Category filter
Manage Incidents from Hexnode: A complete guide
Understanding incidents in Hexnode UEM
Incidents serve as real-time alerts that help administrators quickly identify, investigate, and resolve issues across their managed environment.
Unlike compliance violations, which are tied to predefined policy rules, incidents are dynamically generated whenever potential risks, configuration errors, or endpoint-level failures are detected. These can include issues such as failed policy deployments, recurring agent errors, expired certificates, or configuration errors between Hexnode and integrated third-party service providers.
Each recorded incident includes detailed contextual information – such as the affected entity (device or user), time of occurrence, severity level, and resolution status, giving administrators the visibility needed to maintain security and compliance.
A centralized incident visibility framework in Hexnode enables organizations to track these events efficiently. Administrators can monitor incidents, assess the impact across their devices, and take corrective actions directly from the Hexnode UEM console. This unified visibility ensures faster response times, reduced risk exposure, and consistent management across all enrolled devices and users.
How does tracking incidents benefits organizations?
Tracking incidents allows administrators to:
- Maintain visibility over the entire managed environment.
- Detect misconfigurations and system errors early.
- Investigate recurring issues.
- Improve response and remediation workflows.
Incident management roles in Hexnode
Effective incident response in Hexnode relies on clear administrative roles and permissions. Depending on their assigned roles, technicians can view, investigate, or manage incidents within the UEM console.
Super Admins and Admins have the authority to perform key incident-related actions such as assigning incidents, changing statuses, or marking resolutions.
Can roles other than Admin or Super Admin manage incidents?
To delegate incident-handling responsibilities, administrators can create a dedicated Incident Manager custom technician role within Hexnode. While Admins and Super Admins can manage and assign incidents by default, creating an Incident Manager role allows organizations to assign incidents to a dedicated technician for better ownership and accountability.
To create an Incident Manager:
- Navigate to Admin > Technicians and Roles > Add Technician.
- Enter the technician’s account information, including name, email, and phone number.
- Configure SSO, CAPTCHA, 2FA, and logout settings, then click Next.
- Under the Roles section, click Assign Role and select Incident Manager.
- Click Assign to create the technician.
Why assign a dedicated Incident Manager?
Assigning a dedicated Incident Manager helps ensure that every incident is tracked and resolved efficiently. It gives clear ownership of investigations and actions, reducing confusion or overlap between teams. This approach works best in larger organizations where incidents occur often. For example:
- A security team can focus on alerts such as failed logins or compromised devices.
- A helpdesk team can manage user errors or device sync failures.
Incident prioritization in Hexnode
Each incident in Hexnode is automatically assigned a severity level based on its impact.
- Critical level incidents represent the most severe issues – such as license expiration or failed integrations – and are treated as top priority requiring immediate action.
- The remaining levels – High, Medium, Low, and Info – follow in descending order of urgency. These levels help administrators address issues according to their importance and the level of attention they require.
These severity levels are predefined by Hexnode based on internal evaluation criteria to ensure that incidents with the highest potential risk are prioritized appropriately.
Incident categories in Hexnode
In Hexnode UEM, incidents are categorized into four types to help administrators identify and act on critical issues faster. These categories group similar incident types based on their impact, source, or scope – ensuring better visibility and prioritization within the Hexnode UEM console.
All incident data is accessible under the Incidents tab in the Hexnode UEM portal. From here, admins can view the categorized incidents, track severity, assign technicians, download reports, and take corrective actions.
The Incidents tab in Hexnode is categorized into seven:
| Category | Purpose |
|---|---|
| Critical | Displays high-severity incidents that demand immediate attention, such as licensing, certificate, or integration failures. |
| Endpoints | Tracks incidents detected on managed devices, including configuration errors, security risks, or connectivity issues. |
| Users | Lists incidents related to user accounts, such as failed logins, policy violations, or suspicious credential changes. |
| Apps | Displays incidents associated with application management, including vulnerable applications, VPP license issues, Apple VPP failures, failed app installations, and app update failures. |
| Patches | Lists incidents related to patch management, such as detected vulnerabilities, failed patch deployments, and devices missing critical updates. |
| Identity Providers | Shows incidents associated with identity provider integrations, including failed directory syncs and recently deleted identity connections. |
| Exports | Provides a record of all incident report export requests (PDF/CSV) initiated within the last 24 hours. |
The Critical, Endpoints, and Users categories have its own dashboard that provides an overview of corresponding incidents and includes a real-time Incident Feed showing all incidents with their occurrence times for quick monitoring.
Incident sources
The Critical, Endpoints, and Users categories includes Incident Sources – predefined groups that help narrow down the root cause of an issue. Grouping incidents this way gives administrators better visibility into where problems originate, making it easier to investigate and resolve them.
Why is incident categorization important?
Incident categorization allows administrators to:
- Quickly identify the scope and urgency of an issue.
- Assign incidents to the right technicians based on type.
- Prevent critical disruptions by addressing high-severity events first.
- Maintain compliance by tracking user- and device-level incidents separately.
For example, a certificate nearing expiry (under Critical) needs faster remediation than a single device falling out of compliance (under Endpoints).
Critical incidents
The Critical section in the Incidents tab highlights high-severity issues that require immediate administrative attention. These incidents typically indicate a disruption in essential operations or integrations that could directly impact device management or organizational compliance.
What makes an incident critical?
An incident is classified as Critical when its severity level, as determined by Hexnode’s internal monitoring and policy-based rules, meets predefined high-impact thresholds.
This means the issue poses a direct or imminent threat to UEM functionality or security. For example:
- Expired or invalid Apple Push Certificates or Android Enterprise tokens.
- License-related errors that prevent device management.
- Agent communication failures that block policy or command updates.
- Integration or service disruptions that affect connected platforms.
Critical incidents are automatically surfaced under the Critical category in the Incidents tab, allowing administrators to prioritize them before lower-severity issues.
The following are the available incident sources under the Critical subtab:
Apple Services
Flags incidents related to Hexnode UEM’s integration with Apple device management services. These include configuration or certificate errors in Apple Business/School Manager, APNs certificates, or VPP tokens. These incidents are critical for admins, as they directly affect the organization’s ability to manage Apple devices and should be monitored and addressed by admins only.
Android Enterprise
Shows failures in Android Enterprise integration, such as enrollment profile deletion or organization disenrollment. When this happens, device syncing stops, and affected devices can no longer be managed from Hexnode. As a result, you cannot apply policies, perform remote actions, or trigger automated actions on these devices.
UEM License
Indicates issues with the Hexnode UEM license, such as upcoming license expiration, expired license, exceeding the device count, or exceeding the technician account limit for that license, which may affect device management.
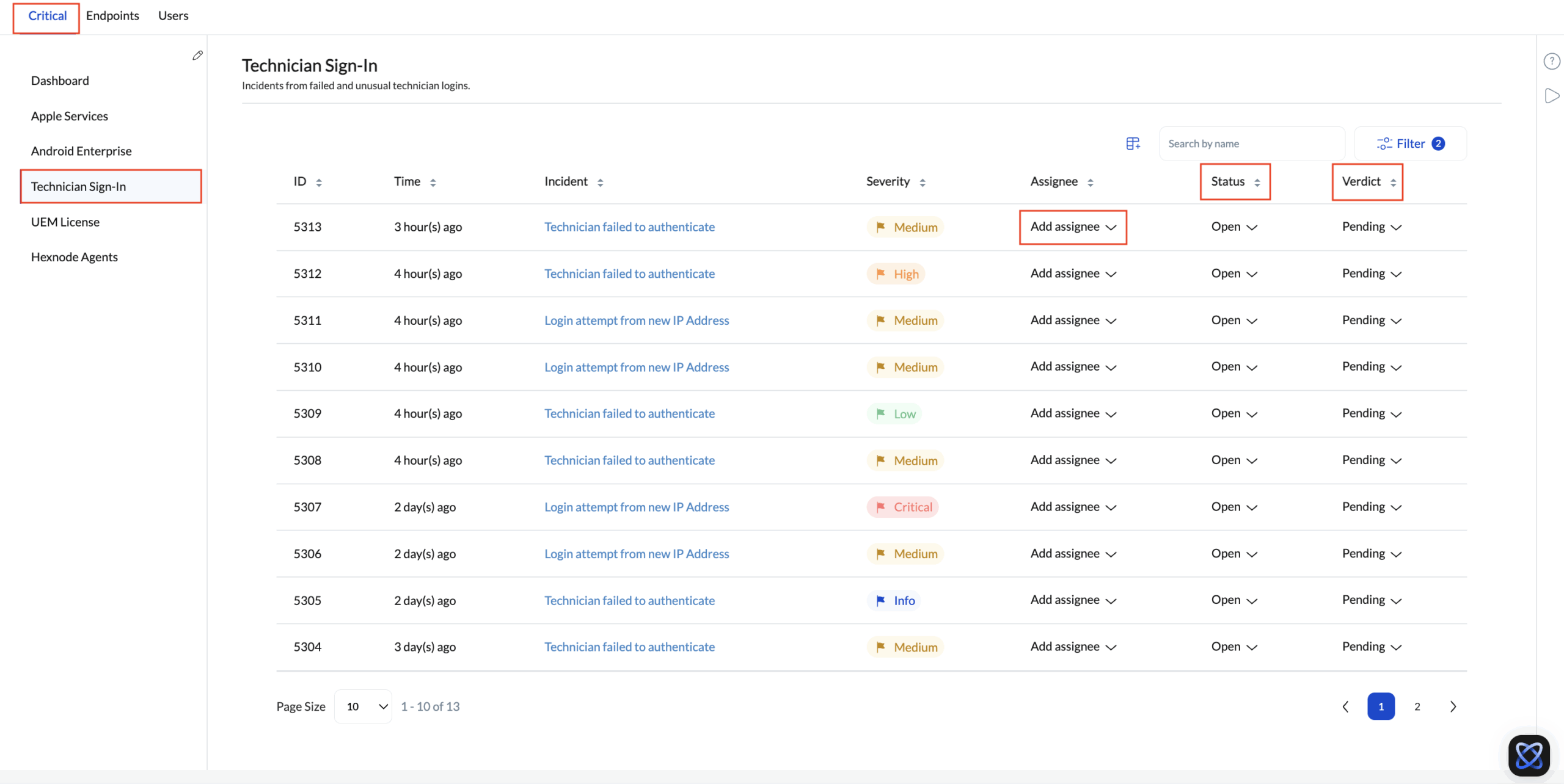
Technician Sign-In
Tracks technician login activity in the Hexnode UEM portal to detect unauthorized access. This includes failed authentication attempts, such as entering incorrect credentials, and unusual logins, such as accessing the portal from a new or unrecognized IP address.
Hexnode Agents
Tracks incidents reported by the Active Directory agent and DAFS agent, helping administrators identify connection issues, synchronization failures, or agent/server removals. Examples of incidents include failed connections to the Active Directory agent, portal or server synchronization failures with DAFS, and removal of DAFS servers or sites.
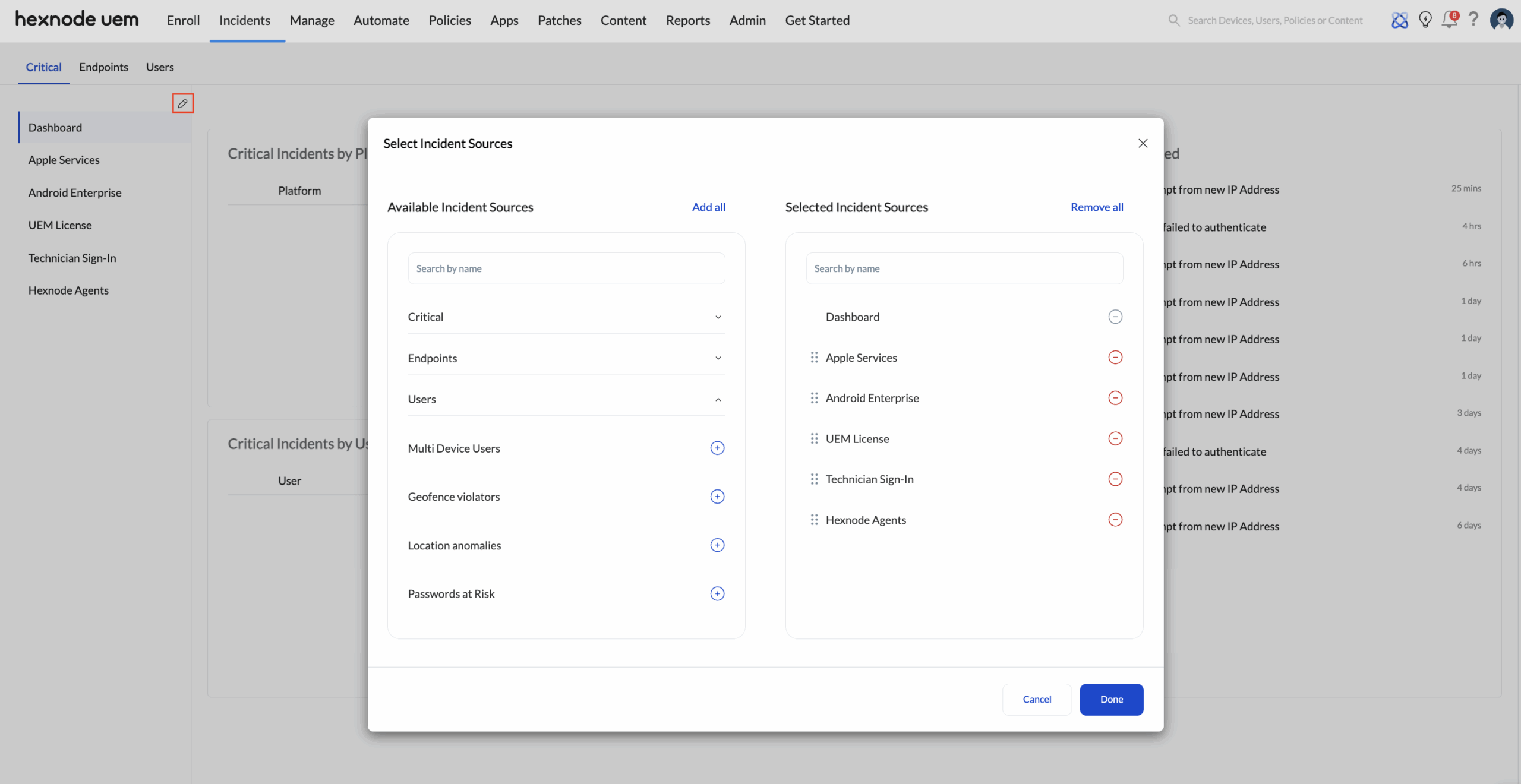
Configuring the Critical incidents dashboard
Administrators can tailor the Critical dashboard to suit their priorities.
Each incident source like Apple Services, Android Enterprise, UEM License, Technician Sign-In, or Hexnode Agents can be rearranged or filtered for better visibility.
To configure the dashboard:
- Navigate to Incidents > Critical.
- Click the Pen icon.
- Use the customization options to add, remove, or reorder incident sources.
- Save your configuration to instantly reflect changes in the dashboard.
This feature helps admins to control which incident sources from the Critical, Endpoints, and Users sections appear prominently displayed on the dashboard, ensuring the most important issues are always prioritized.
For example, organizations heavily managing Apple devices may prioritize Apple Services at the top of their dashboard.
Example: Prioritizing critical issues
Consider an organization managing iOS devices via Hexnode.
The admin receives a Critical alert indicating an expired Apple Push Certificate.
Without renewal, Apple devices would fail to sync policies or commands.
By immediately reviewing the Apple Services source within the Critical dashboard, the admin can renew the certificate and restore uninterrupted device management.
Importance of critical incident tracking
Tracking critical incidents in Hexnode provides:
- Centralized visibility over key integrations and services.
- Early warnings for license, token, or certificate expirations.
- Faster isolation of high-impact issues.
- Reduced downtime through quick remediation.
Endpoint incidents
The Endpoints section in the Incidents tab provides a consolidated view of all device-level issues detected across your managed fleet.
These incidents help administrators monitor the health of devices, detect non-compliance, and ensure that Hexnode’s configurations and policies are functioning on devices as intended.
What are endpoint incidents?
Endpoint incidents are events generated when Hexnode detects abnormal or failed configurations, missing security parameters, or communication breakdowns on managed devices.
They reflect the state of enrolled endpoints and indicate whether those devices continue to meet the organization’s security and compliance standards.
The following are the available incident sources under the Endpoints subtab:
Endpoint Compliance
This incident section highlights security and compliance deviations on devices, helping admins quickly identify risky device states.
- Rooted/Jailbroken devices – Detects devices that have been rooted or jailbroken, as these modifications bypass built-in security controls.
- Geofence violations – Flags devices that move outside predefined geographical boundaries, which could signal loss or misuse.
- Compliance policy violations – Identifies devices that fail to adhere to the compliance policies set by the administrator.
Command Failures
Tracks incidents where Hexnode policies and certificate configurations fail to run on devices, allowing admins to detect and address the issues promptly.
- Policy – Reports when a policy fails to apply to a device, which may leave it non-compliant.
- Certificates – Alerts admins when a device fails to install a required certificate, potentially blocking secure communications.
High Usage Detected
This incident section shows devices exhibiting unusually high memory and CPU usage, which could indicate device performance related issues.
- High memory usage – Detects devices where memory usage exceeds 90%.
- High processor usage – Identifies devices with CPU usage above 90%.
Devices with Recent Owner Updates
This incident section shows endpoints flagged for administrator alert due to changes in device ownership, helping maintain visibility and accountability for asset transfers.
- Recent owner changes – Detects when ownership of a device is updated.
- Recent owner change upon re-enrollment – Detects changes in device ownership that occur after re-enrollment.
Cellular
Shows endpoints flagged for administrator alert due to issues with cellular connectivity, such as SIM removal or SIM changes, helping administrators quickly identify devices that require attention.
Kiosk Exits
This section captures incidents where devices exit kiosk mode, either by user action or administrative intervention.
- Kiosk exit from device – Logs when a user manually exits kiosk mode.
- Kiosk exit by admin – Logs admin-initiated kiosk exits.
Encryption
When an administrator enables BitLocker or FileVault encryption from the Hexnode portal, the incident is reported here. This helps administrators confirm that device encryption is successfully applied and meets the organization’s security requirements.
Disenrollments
If you remove Hexnode device management from a device, it’s reported as a disenrollment incident. This section also lists devices that have been disconnected from the internet for a long time and become inactive, helping administrators monitor and address potential security risks.
- Inactive devices – Identifies devices that have gone inactive.
- Disenrollments by user – Lists devices that users have removed from management.
- Disenrollments by admin – Lists devices disenrolled by administrators to track intentional removals.
Battery Health
If a device repeatedly reports poor battery performance, such as holding less than 50% charge after a full cycle, it is flagged as a battery health incident. This allows administrators to identify potential battery issues early on and take actions like replacing or servicing the device.
How does Hexnode detect endpoint incidents?
Whenever a configuration, restriction, or compliance rule fails to apply, or if the device fails to communicate with Hexnode servers, the corresponding incident is automatically generated.
Example: Tracking device encryption incidents
Suppose your organization enforces mandatory disk encryption on all corporate Windows laptops.
If encryption fails to apply on a set of devices – perhaps due to some configuration errors – Hexnode logs an encryption failure incident under the Endpoints section.
Importance of endpoint incident tracking
Tracking endpoint incidents helps organizations:
- Maintain device compliance and security posture.
- Identify misconfigurations before they escalate.
- Ensure policy enforcement across all managed devices.
User incidents
The Users section in the Incidents tab lists all issues related to users managed in the Hexnode UEM console.
These incidents help administrators detect suspicious activities, authentication errors, and policy violations tied to user behavior, ensuring that access and security remain consistent across the organization.
What are user incidents?
User incidents are alerts generated when Hexnode detects abnormal or policy-violating activities associated with users managed in the Hexnode UEM console.
They primarily focus on user credential updates, sign-in patterns, or actions that may indicate potential user account misuse or compromise.
The following are the available incident sources under the Users subtab:
Multi device users
Flags users who have more than three devices assigned to them. For instance, if a user is provisioned with more than three devices, administrators are alerted to prevent resource over-allocation and ensure compliance with organizational policies.
Geofence violators
Lists users whose devices consistently cross configured geofence boundaries. For example, if a user’s device leaves a geofence multiple times a day, it may indicate potential misuse or non-compliance with location-based policies.
Location anomalies
Detects location discrepancies that may suggest suspicious activity. For instance, if a user’s device logs locations from two distant regions within a short period, it could point to GPS spoofing or a compromised user account.
Importance of user incident tracking
Monitoring user incidents helps organizations:
- Identify compromised or misused accounts early.
- Enforce consistent authentication policies.
- Ensure compliance by controlling device assignments.
- Maintain auditability for user-driven actions within Hexnode.
App incidents
The Apps subtab in the Incidents section provides visibility into application-related issues across devices.
These incidents help administrators track app security posture, deployment reliability, and license integrity. Unlike endpoint compliance issues, App incidents focus specifically on application lifecycle events, from deployment to updates and vulnerability detection.
What are App incidents?
App incidents are alerts generated when Hexnode detects failures, risks, or inconsistencies related to application management across devices. These may include unsuccessful application installations or updates, identification of vulnerable or outdated app versions, volume licensing issues such as VPP license exhaustion or assignment failures, and changes within the app catalog such as newly added applications.
The following are the available incident sources under the Apps subtab:
Vulnerable Apps
Displays incidents related to applications that are identified as vulnerable or running outdated versions. For instance, if a device continues to run an older version of an application with known security risks, administrators are alerted to update or remediate the app before it exposes the organization to potential threats.
VPP Licenses
Lists incidents related to Apple Volume Purchase Program (VPP) licensing utilization and availability. This includes alerts when 50%, 75%, and 90% of VPP licenses are used for a specific app, when VPP licenses are fully depleted, and when a VPP license is revoked for an app. These incidents help administrators proactively monitor license consumption and prevent deployment interruptions.
Failed App Installations
Displays incidents where application installation or uninstallation does not complete successfully on a device. For example, if a required application repeatedly fails to install on a device, administrators are alerted to investigate the configuration issues.
App update failure
Lists incidents related to issues and changes in application update deployments and update automation workflows. This includes incidents such as app update installation failed, app update approval revoked, app update automation failed, app update automation deleted, app update automation archived, and app update automation paused, helping administrators ensure version consistency across the fleet.
Recently added
Displays incidents generated when new applications are added to the Apps tab within the Hexnode UEM console. For example, if a new application is introduced into the organization’s app catalog, administrators can track and review the addition to maintain visibility and governance over app deployments.
Apple VPP Failures
Lists incidents related to failures in Apple VPP integration and configuration. This includes incidents such as T&C not accepted by user and VPP setup failed. These incidents help administrators identify issues that may block app distribution through VPP and ensure that licensing and deployment processes function without disruption.
Patch incidents
The Patches subtab in the Incidents section provides centralized visibility into patch management–related issues across devices. It highlights detected vulnerabilities, identifies devices that remain unpatched, and tracks failed patch deployments that may expose the organization to risk.
By consolidating these events into a single view, the Patches subtab enables administrators to prioritize remediation efforts, ensure timely update enforcement, and maintain a consistent security posture across both operating systems and applications.
The following are the available incident sources under the Patches subtab:
Vulnerabilities Detected
Flags incidents where vulnerabilities are identified in device operating systems or installed applications. For instance, if a device is running an outdated OS version with known security flaws, administrators are alerted to assess the risk and initiate remediation through patch deployment.
Failed Patch Installations
Lists incidents related to unsuccessful patch deployments on managed devices. This includes incidents where an OS patch installation fails on a device, or an app update does not install successfully on a device. These incidents help administrators quickly identify devices where patching has not been successfully completed and take corrective action to maintain security and compliance.
Vulnerable Devices
Lists devices that are identified as having application-level or operating system vulnerabilities. For example, if multiple devices remain unpatched against a critical security update, the incident helps administrators quickly isolate affected endpoints and prioritize corrective action.
Identity provider incidents
The Identity Providers subtab in the Incidents section provides visibility into directory integration and synchronization events between Hexnode and connected identity services. These incidents help administrators monitor authentication reliability, directory consistency, and structural changes that may impact user provisioning or access management.
The following are the available incident sources under the Identity Providers subtab:
Failed Syncs
Lists incidents of failed synchronization with identity providers and are typically categorized as High severity. These incidents cover domain synchronization failures, Active Directory synchronization failures, Okta domain synchronization failures, and Google Workspace synchronization failures.
Recently Deleted
Lists incidents generated from the deletion of directory objects within connected identity providers. These incidents cover deletion of users, groups, organizational units (OUs), and domains, helping administrators maintain visibility over critical structural changes.
Exports
The Exports section in the Incidents tab provides a centralized record of all incident data export requests initiated by technicians within the last 24 hours. It serves as a management hub for monitoring and retrieving generated reports. These reports can be downloaded and shared for auditing, compliance reviews, or external documentation.
What are tracked in Exports?
The Exports section displays a comprehensive list of all recent export requests. Each entry provides key details, including the Incident Name, Category, and the exact time it was Initiated on. It also identifies the technician who Initiated the request, the chosen Format (PDF or CSV), and the current Status (In Progress, Success, or Failed).
- Download icon is provided to download the successfully exported file.
- Re-initiate icon is provided for reports that have failed to export, allowing a retry of the process.
Incident details overview
When you select any incident category, Hexnode displays a detailed table listing all incidents within that category. This helps administrators quickly assess the nature of each incident and take appropriate actions as needed.
After selecting one or more incidents from the list, administrators can click the Export button to generate a report of those specific incidents.
The following fields are displayed for each incident entry, offering a clear breakdown of its attributes and current state:
| Field | Description |
|---|---|
| ID | A unique identifier is assigned to every incident for easy reference and tracking. |
| Incident | The name or type of incident (for example, APNs Certificate Expiry or Policy Deployment Failure). |
| Severity | The importance level of the incident, such as Critical, High, Medium, Low, or Info. |
| Time | The time when the incident was created. |
| User | The user account associated with the event (Available only in the Users subtab incident). |
| Assignee | The technician responsible for investigating and resolving the incident. Incidents are initially unassigned by default and can be assigned to a technician later by an administrator. |
| Status | Indicates progress in handling the incident – Open, In Progress, or Resolved. |
| Verdict | Represents the final assessment after investigation – Pending, False Positive, or Fixed. |
Assigning and managing incidents in Hexnode
Each recorded incident in Hexnode must be assigned to a technician who will investigate and resolve it.
By assigning ownership, administrators can ensure that incidents are actively monitored and resolved in a timely manner.
To assign or export an incident:
- Navigate to the Incidents tab and open the relevant sub-tab (Critical, Endpoints, or Users).
- Locate the required incident in the table.
- To assign an incident, click Add Assignee and select the technician from the drop-down menu. From the same window, you can update the Status and Verdict of the incident.
- To export an incident, select the checkbox next to the incident(s) and click the Export button at the top of the list.
What happens after assigning?
The assigned technician becomes responsible for resolving the issue – whether that involves troubleshooting a device, reconfiguring a failed policy, renewing an integration certificate, or contacting an end user for corrective action.
What happens after exporting?
The exported incident report will be listed in Exports tab, and the file can be downloaded for future analysis.
Viewing and managing incidents
Clicking on any incident listed under the different sub-tabs expands it into a detailed management view. This view generates a unique URL for the selected incident, allowing administrators to share direct links for collaboration or bookmark specific records for future reference.
Within this workspace, administrators can review and update the following incident attributes:
- Incident Details: Modify key incident parameters such as Assignee, Severity, Status, and Verdict to reflect the current state of the incident.
- Tags: Add custom tags to categorize incidents and improve filtering and search capabilities across the dashboard.
- Notes: Attach brief updates or technical remarks as notes directly to the incident. Notes are limited to a maximum of 50 characters.
- Custom Fields: Select Add Custom fields to include additional, organization-specific data points. Each custom field requires a Field Name and supports an optional Description.
The following data types are available:
- Long Text
- Checkbox
- Dropdown
- Date
- Numeric
- Text
- Link
Incident History and Collaboration
- Comments: Track progress and communicate with team members using the Comments section. Use the @mention feature within the comment text box to direct a message to a specific technician. Technicians can also participate in threaded discussions by selecting Reply on individual comments.
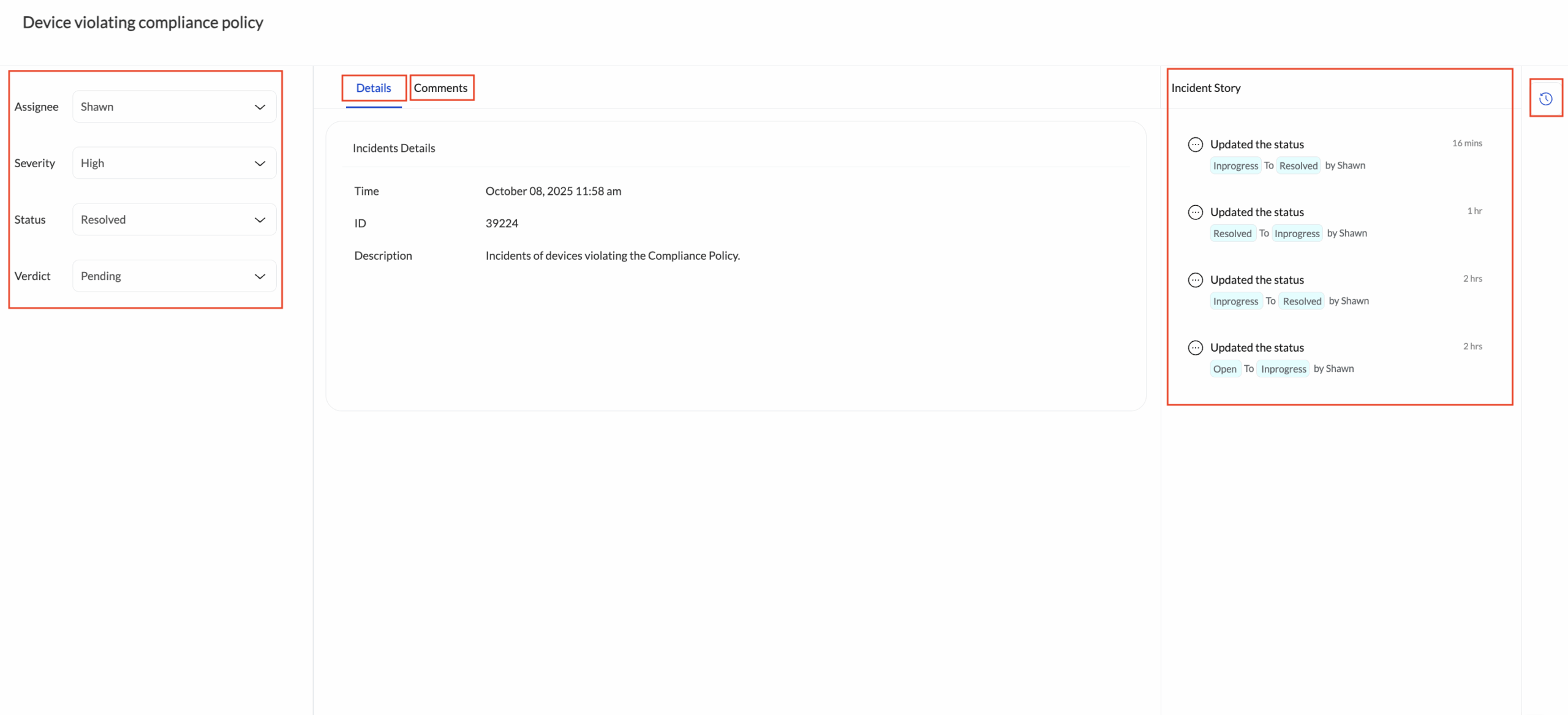
- Incident Story: Click on History icon from the right-hand sidebar to view the Incident Story. This section presents a complete chronological log of all actions, updates, and state changes associated with the incident.
Tracking incident progress
Administrators can track incident progress through two indicators:
- Status: shows where the incident stands in its lifecycle.
- Open – newly detected and unassigned or pending investigation.
- In Progress – currently being reviewed or resolved by a technician.
- Resolved – the issue has been addressed, and no further action is required.
- Verdict: Indicates the final result or evaluation of the incident and is updated by the assigned technician.
- Pending – investigation or validation is still ongoing.
- False Positive – Hexnode detected an event that did not represent an actual issue.
- Fixed – the root cause has been corrected successfully.
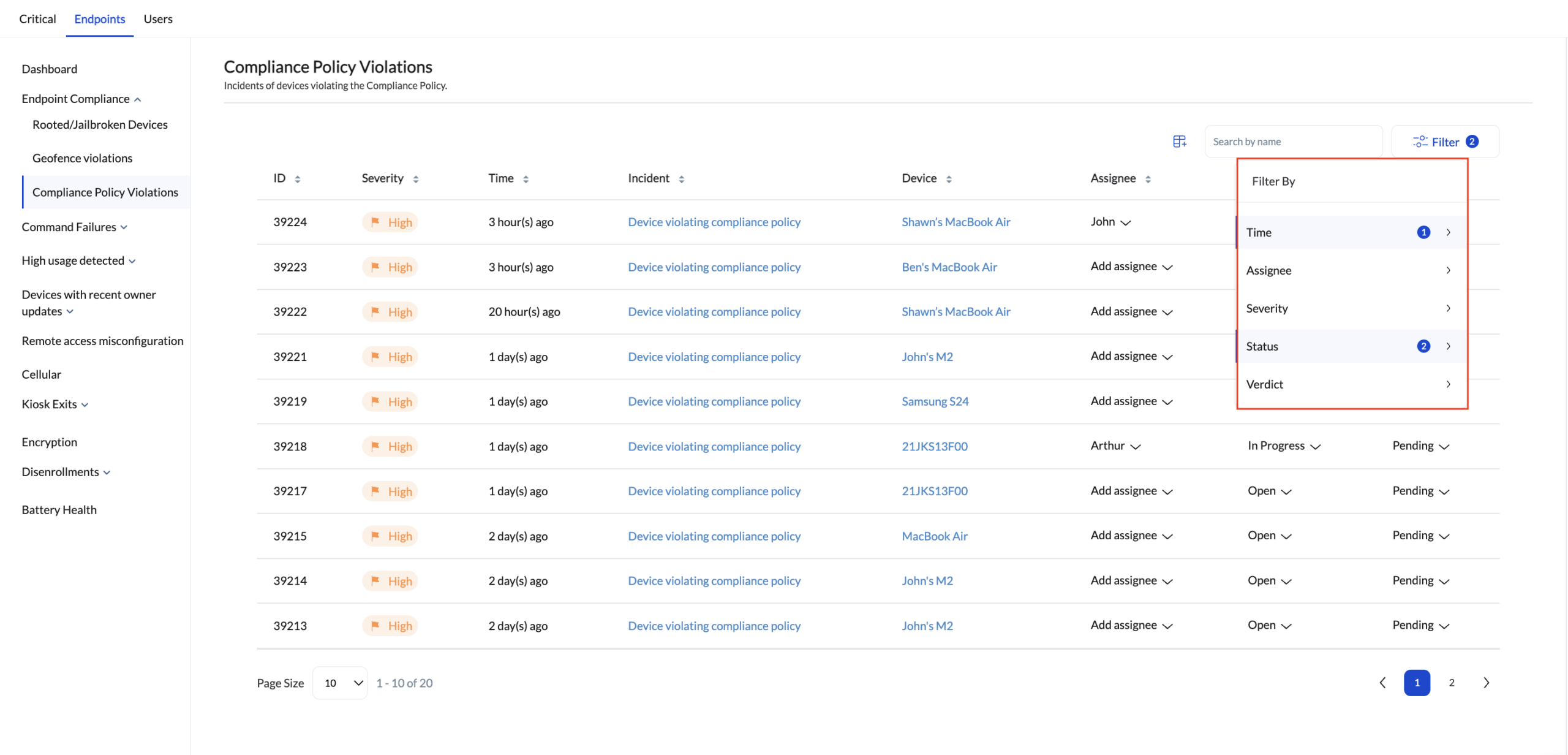
Filter and locate incidents efficiently
The incident filtering options in Hexnode allow administrators to narrow down results and focus on the most relevant events for review.
| Filter | Description |
|---|---|
| Time | Filter incidents based on their creation date. Options include All, Today, Yesterday, Last 7 Days, Last 30 Days, or Custom for a specific date range. |
| Assignee | Filter incidents assigned to a particular technician by searching for their name. |
| Severity | Select incidents based on automatically assigned severity levels: Critical, High, Medium, Low, or Info. Admins may manually adjust severity if needed. |
| Status | Filter by status of the incident: Open, In-Progress, or Resolved. | Verdict | Filter incidents based on the verdict – Pending, False Positive, or Fixed. |
Filtering is particularly useful when prioritizing incidents that remain unresolved or require immediate attention.
Viewing incident timelines, comments, and activity logs
Once an incident is detected and listed in the Hexnode UEM console, administrators can open its detailed view to track how the issue evolved from detection to resolution.
The Incident details page consolidates all relevant contexts – such as descriptions, updates, technician actions, and comments into a single interface, ensuring complete visibility and traceability.
Clicking on an incident opens a detailed view containing the following elements:
- Details section: Displays core information such as the incident occurrence time, ID, and a brief description. These details are automatically generated when the incident is first detected.
- Comments section: Enables technicians and administrators to record investigation notes, progress updates, or remediation steps.
- Incident Story section: Accessible by clicking the history button in the top-right corner. This panel lists every change made to the incident – such as incident occurrence time, comments, status updates, severity changes, verdict changes, and technician reassignments.
Administrators can modify fields such as Assignee, Severity, Status, and Verdict directly from the incident details section when needed.