Category filter
Protect Verification Key for BitLocker Encryption
BitLocker drive encryption is a data protection feature available on Windows devices. The data stored on a BitLocker-encrypted device becomes inaccessible even when the device is decommissioned or recycled. Therefore, enabling BitLocker on a device ensures that the data is safe from unauthorized access. When used in conjunction with TPM versions 1.2 and above, BitLocker encryption provides maximum protection.
When a drive is encrypted using BitLocker, a BitLocker recovery key (encryption key) that can be used to access encrypted data is also generated. The recovery key is stored as plaintext on the device if no key protector is assigned. A key protector is an authentication method that prevents storing the volume encryption key as plaintext on the device. It can be a PIN or a USB drive containing the key. BitLocker uses this key protector to retrieve the encryption key that reads data from the encrypted drive. This document helps the admin on how to protect the recovery key of a BitLocker-encrypted device.
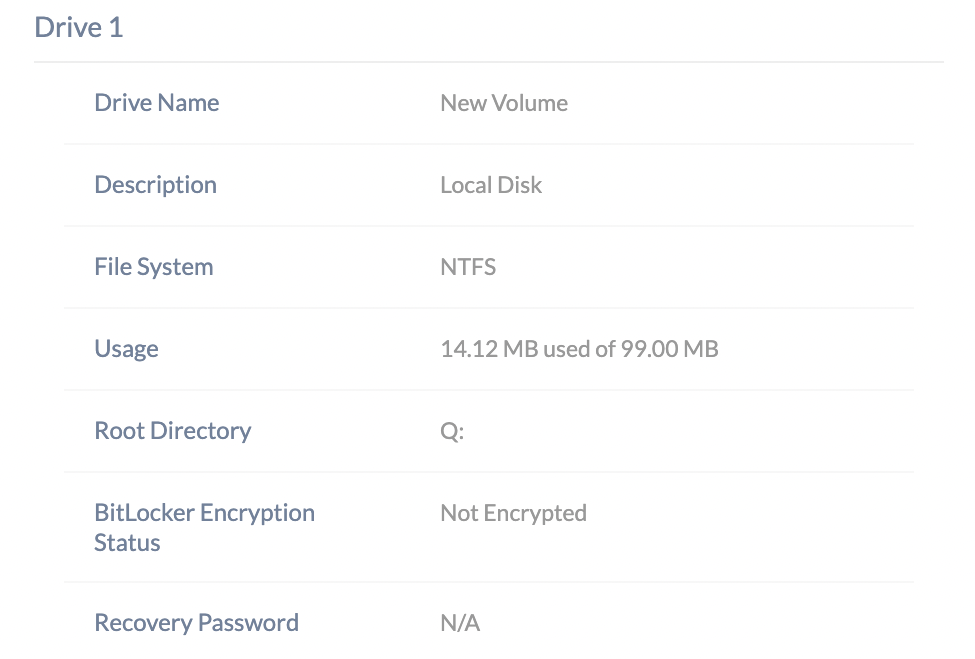
BitLocker Encryption Status
Admins can monitor the encryption status of a remote Windows device through the Device Summary page of the target device on the portal. Note that the BitLocker encryption status can be verified even if the BitLocker is enabled manually. The BitLocker encryption status of a device takes either of the following forms:
- N/A – BitLocker encryption is not supported on this device.
- Encrypted – The encryption of the volume is completed.
- Encryption in progress – BitLocker encryption has started and is ongoing.
- Encryption paused – The encryption of the specified volume is paused.
- Not encrypted – The device is not BitLocker encrypted at the moment.
- Decryption in progress – The decryption of the specified volume is ongoing.
- Decryption paused – The decryption of the specified volume is paused.
- Status unknown – The volume protection status cannot be determined. This can be caused by the volume being in a locked state.
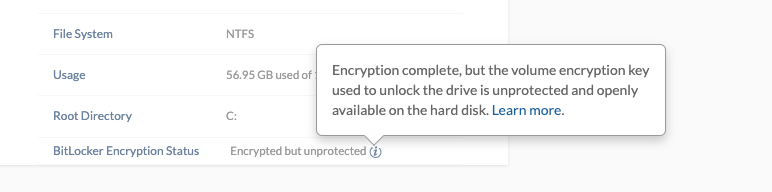
- Encrypted but unprotected – Encryption is complete, but the volume encryption key used to unlock the drive is unprotected and openly available on the hard disk.
Encryption completed but verification key is unprotected
The BitLocker encryption status Encrypted but unprotected denotes that the volume encryption is complete, but the volume encryption key is stored as plain text on the device without any protection. As a result, the encryption key is vulnerable to unauthorized access and can be used to read encrypted data on the drive.
Follow these steps to protect and store the encryption key,
- Setup key protectors using the BitLocker policy from the Hexnode console.
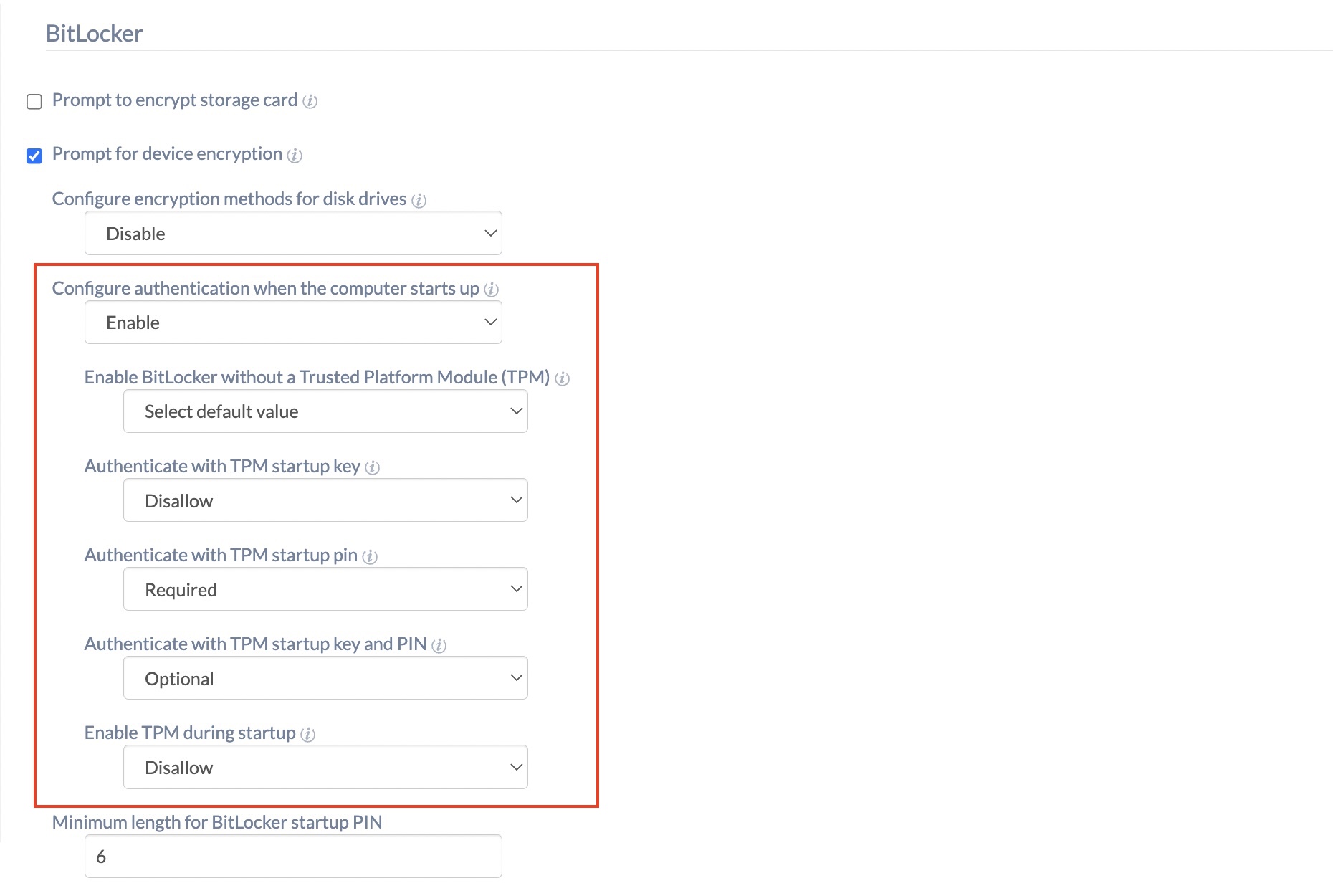
Admins can setup key protectors using the BitLocker policy under Policies > New policy > New Blank Policy > Windows. Select Enable for the option Configure authentication when the computer starts up and configure the required options to act as the key protector for the encryption key. You can use the following authentication methods to protect the encryption key.
- Enable BitLocker without a Trusted Platform Module (TPM)
- Authenticate with TPM startup key
- Authenticate with TPM startup pin
- Authenticate with TPM startup key and PIN
- Enable TPM during startup
- Backup the recovery key from the device.
You can backup up the recovery key on the Windows device by following these steps,
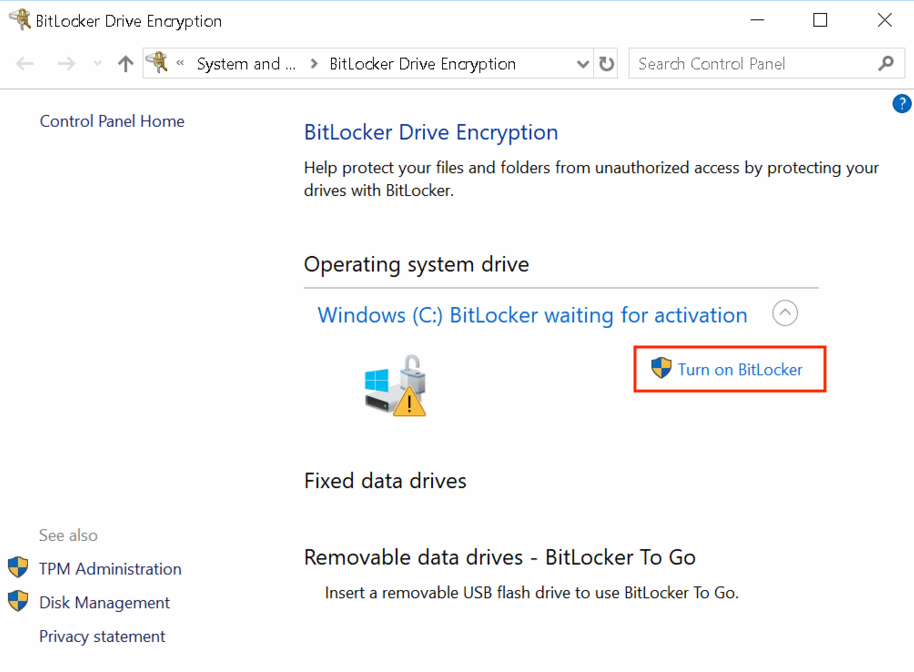
- Type Manage BitLocker in the search box in the Start menu. You can also access the BitLocker settings through Start > Settings > Privacy & security > Device encryption > BitLocker drive encryption.
- Next, scroll down to the encrypted drive section and click on Turn on BitLocker.
- In this step, the user will be prompted to set up a key protector. The user can choose from any of the key protectors that are enabled in the BitLocker policy. The selected key protector containing the recovery key will be used in the future to decrypt the drive.
- Back up the recovery key using any of the methods provided below,
- Save to your Microsoft account – This method requires the user to be signed into a Microsoft account to store the recovery key to the specified account.
- Save to a file – Choosing this option allows you to save the recovery to a drive which is not encrypted or a removable device.
- Print the recovery key – This option allows the user to print the recovery key on paper.
- Complete the setup assistant to back up the recovery key. The BitLocker encryption will be completed after this step, and the encryption status in the portal will be changed to Encrypted.