Category filter
Configuration profile to enable/disable AirDrop on macOS devices
Using AirDrop on a macOS device allows users to share files wirelessly with nearby Macs, iPhones, and iPads via Bluetooth and Wi-Fi connectivity. It enables easy transfer of files like photos, videos, documents, websites, etc. However, this convenience raises significant security concerns about potential data leakage. Disabling AirDrop tentatively or permanently can act as a proactive measure to prevent inadvertent sharing of sensitive data and ensure compliance with regulations. If you want to disable AirDrop to address security concerns, you can utilize the configuration profile described below. The custom configuration profile can be executed using Hexnode’s Deploy Custom Configuration feature.
Disable AirDrop
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 |
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>PayloadContent</key> <array> <dict> <key>DisableAirDrop</key> <true/> <key>PayloadDisplayName</key> <string>AirDrop</string> <key>PayloadIdentifier</key> <string>com.apple.NetworkBrowser.8246AC79-53F4-411A-AC6E-8C94F9218F99</string> <key>PayloadType</key> <string>com.apple.NetworkBrowser</string> <key>PayloadUUID</key> <string>8246AC79-53F4-411A-AC6E-8C94F9218F99</string> <key>PayloadVersion</key> <integer>1</integer> </dict> </array> <key>PayloadDisplayName</key> <string>Untitled</string> <key>PayloadIdentifier</key> <string>MacBook-Air.2E925F64-08BC-46E0-AF8C-0EA95B9D2849</string> <key>PayloadType</key> <string>Configuration</string> <key>PayloadUUID</key> <string>2E925F64-08BC-46E0-AF8C-0EA95B9D2849</string> <key>PayloadVersion</key> <integer>1</integer> </dict> </plist> |
In the provided configuration profile, the key DisableAirDrop is set to true, which instructs macOS to disable the AirDrop feature, thereby preventing users from using it to share files wirelessly between devices.
Re-enable AirDrop
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 |
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>PayloadContent</key> <array> <dict> <key>DisableAirDrop</key> <false/> <key>PayloadDisplayName</key> <string>AirDrop</string> <key>PayloadIdentifier</key> <string>com.apple.NetworkBrowser.CA1B720D-8B9B-486C-967D-7C86B1841E85</string> <key>PayloadType</key> <string>com.apple.NetworkBrowser</string> <key>PayloadUUID</key> <string>6D5C0292-7025-47BE-9A01-53513B56BD1A</string> <key>PayloadVersion</key> <integer>1</integer> </dict> </array> <key>PayloadDisplayName</key> <string>Untitled</string> <key>PayloadIdentifier</key> <string>MacBook-Air-M2.279FE351-8DAC-4DC6-A633-121683841845</string> <key>PayloadType</key> <string>Configuration</string> <key>PayloadUUID</key> <string>8F80ACFF-2AD0-4FB1-8D1C-153D3333E63E</string> <key>PayloadVersion</key> <integer>1</integer> </dict> </plist> |
In the provided configuration profile, the key DisableAirDrop is set to false, which instructs macOS to re-enable the AirDrop feature if it has been disabled or blocked.
What happens at the device end?
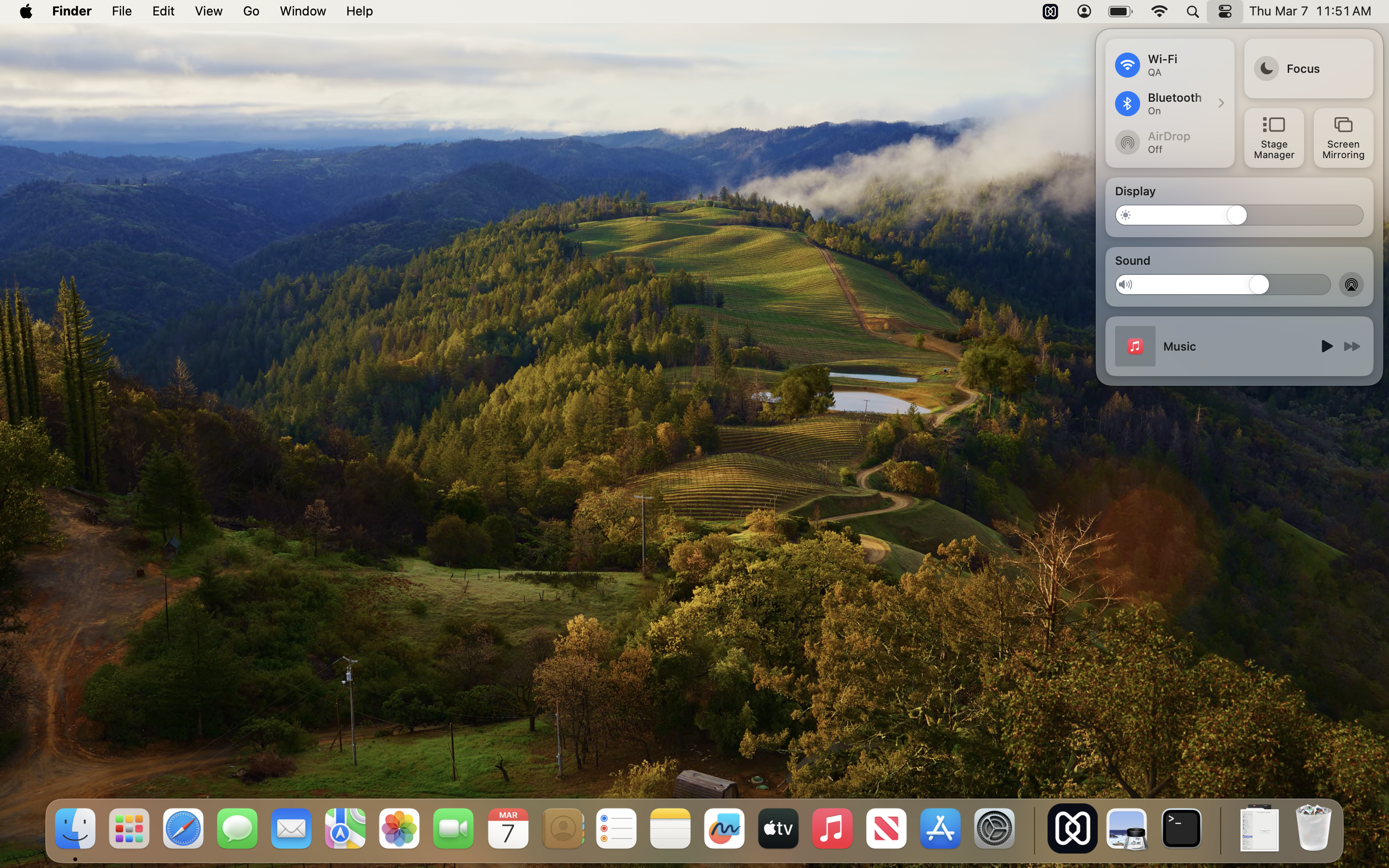
After deploying the “Disable AirDrop” configuration profile to the macOS devices, the AirDrop option in the Control Center becomes completely greyed out and toggled off, preventing users from accessing it.
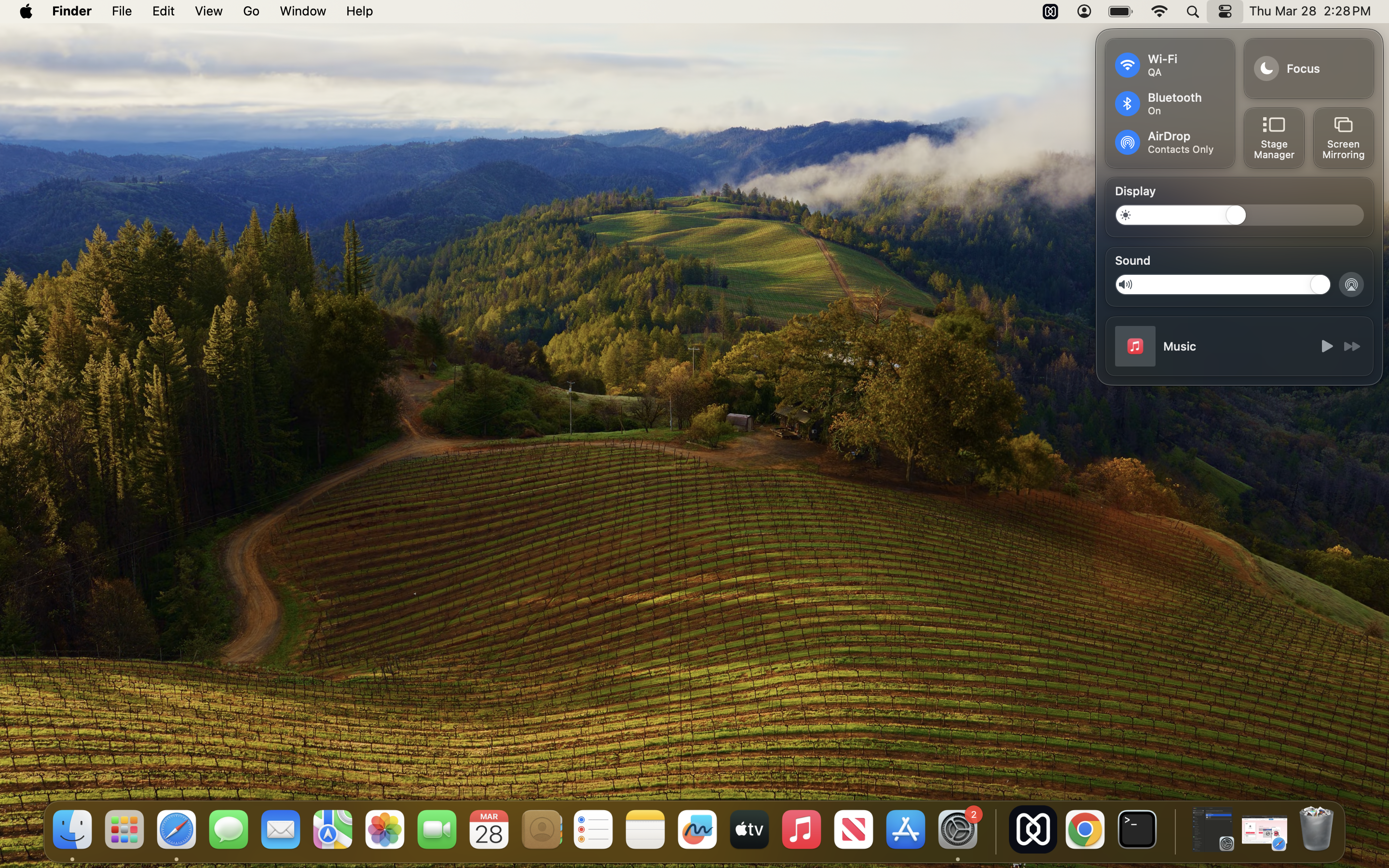
The feature can be re-enabled by deploying the “Re-enable AirDrop” configuration profile. This will restore the feature to its normal state, allowing users to access it again.