Category filter
How to force BitLocker encryption on Windows with Hexnode UEM?
BitLocker is Microsoft’s native device encryption software, developed to protect data by enforcing encryption of OS drives, fixed data drives, and removable drives on Windows devices. With Hexnode’s BitLocker encryption policy, administrators can configure encryption and recovery settings for the devices. However, the policy only prompts the user to encrypt the device. By executing the Force BitLocker Encryption action, admins can encrypt drives with a PIN or password remotely, ensuring the system drive is safe and secure.
Force BitLocker Encryption on Windows drives
You can follow the steps given below to force BitLocker encryption on drives on a Windows device.
- From your Hexnode portal, navigate to the Manage tab and select your device.
- Click on Actions > Security > Force BitLocker Encryption.
- You can choose whether to encrypt the entire drive or just the used space.
- Encrypt used disk space: This option is recommended when setting up BitLocker on a new drive or new PC, as this encrypts the part of the drive currently being used. BitLocker will encrypt any new data automatically added thereafter.
- Encrypt entire drive: This option is recommended when setting up BitLocker on a drive that is already in use, as encrypting the entire drive ensures that all data is protected, i.e., even the data that has been deleted. This offers more security as the drive might hold info that can be used to retrieve the deleted data using third-party tools.
- Encrypt all drives: Encrypts all fixed and removable drives on the device. If not enabled, you can choose from:
- Encrypt fixed drives
- Encrypt removable drives
- Encrypt specific drives – Specify the drive names, separated by commas.
- Enable auto unlock: Automatically unlocks BitLocker-protected drives when the OS drive is unlocked. If disabled, each drive must be unlocked manually using a password or BitLocker recovery key.
- TPM Startup PIN: Provide a PIN to be used to unlock the drive every time the system is rebooted. You must provide a 6-20 digit PIN as per the Minimum PIN length set in the BitLocker policy.
- Fallback Password: Provide a password to be used to unlock the drive on devices that do not have a supported TPM. In such cases, the drive will be encrypted with the Fallback Password instead of the TPM Startup PIN. You must provide a password with at least 8 characters to proceed with the action.
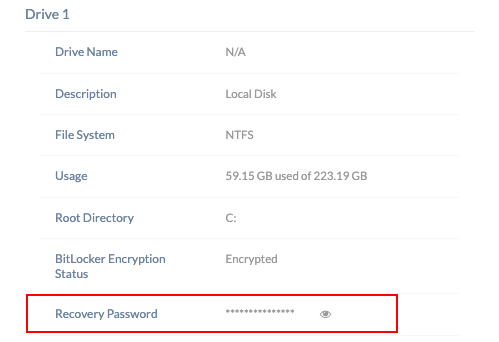
- Mandate and escrow a recovery password: Check this option to ensure that a recovery password is generated and escrowed to your portal. The recovery password can then be viewed on the portal under the details for the encrypted system drive at Device Summary > Hardware Info tab for the device.
- Click on Proceed.
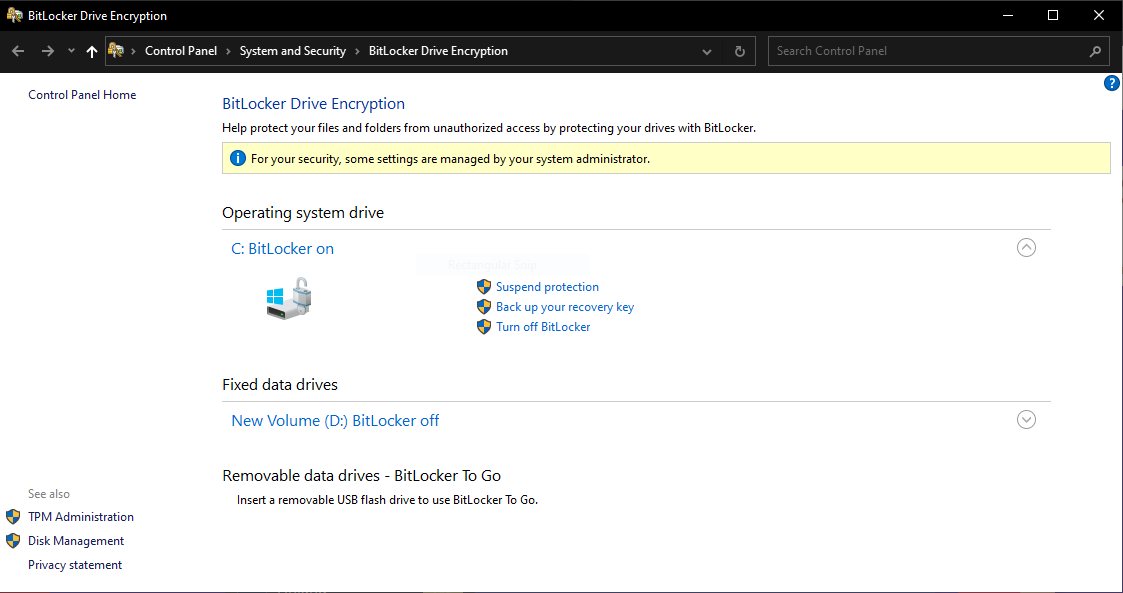
What happens at the device end?
BitLocker is enabled for the device’s drive on the device based on the configurations set in the BitLocker policy. If no BitLocker policy is associated with the device, the drive is encrypted using the device’s default BitLocker configurations. The user can check the same on the device by navigating to Control Panel > System and Security > BitLocker Drive Encryption.