Category filter
Hexnode Cloud Infrastructure & Security
Hexnode UEM is a Unified Endpoint Management solution that lets you set up, administer, and manage endpoints across all major device platforms. As a UEM, security and data privacy has always been an integral part of our product. Hexnode ensures at-most security to your devices and their data at rest, in transit, and in use. We are keen on finding our points of vulnerability and mitigating them to strengthen the security posture across the cloud environment. We employ the most modern technologies and strategies for creating, operating, and supporting our product.
Architecture
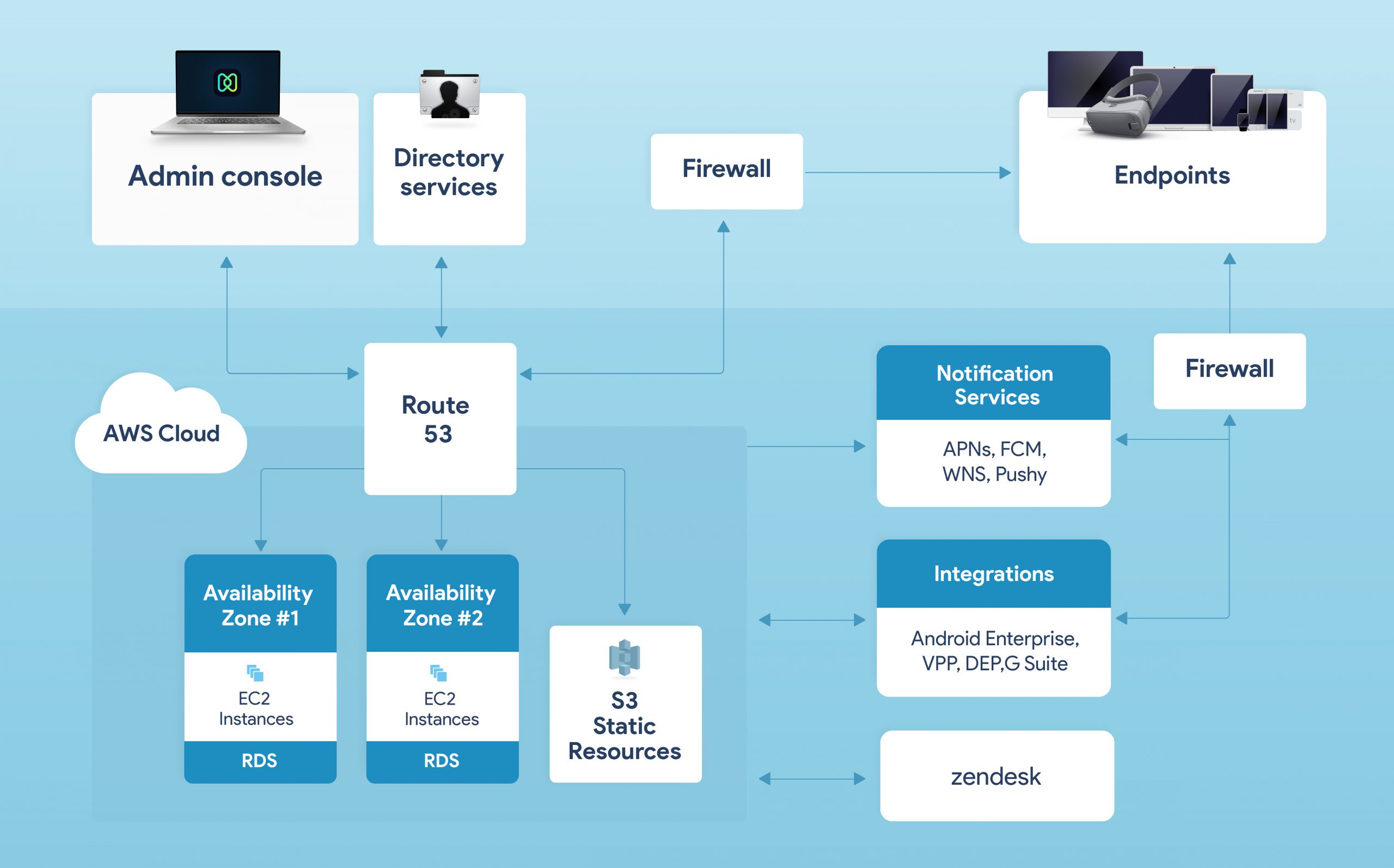
To remotely administer the device and let the organization manage it, you must enroll it in Hexnode. We support the enrollment of both personal and corporate devices that are used for work. The unified device management console lets you centrally manage and seamlessly secure the entire device fleet.
Hexnode employs different encryption methodologies to secure the communication between devices and the server. Managed Android devices communicate with the server using standard HTTPS protocol with strict certificate validation. The digital certificates are signed using strong hash algorithms and are thus highly immune to fraudulency. iOS and Windows devices use TLS based authentication to connect to the server.
Hexnode cloud server stores files and other client configurations in the AWS S3 and uses the EC2 instances for executing secure cloud computational tasks. The relational database services (RDS) in the AWS are used for managing scalable CRUD operations in the cloud.
Hexnode cloud supports the connectivity to the directory services like ADFS, Microsoft Entra ID, Google Workspace (G Suite), and Okta for federated authentication and directory sync.
Hexnode server uses cloud notification services (APNs, FCM, or WNS) to initiate communication with the managed endpoints. The configuration data may be sent to the device either through these notification channels for iOS and Windows devices. Android devices ping the Hexnode server on receiving the notification from FCM. The server then directly sends the configurations to the devices. This configuration data is parsed and processed by the Hexnode client application (for Android and Windows) or the OS in case of iOS devices to take effect on the device.
To learn more about Hexnode’s cloud architecture, visit Hexnode – Architecture.
Data Protection
Hexnode has set forth a well-defined set of policies, stringent rules, and encryption methodologies on the transmission, processing, and storage of data we collect from our customers and their devices. Hexnode periodically backs up the data across multiple servers, with security matching that of production, for high availability and to avoid potential downtime caused by hardware failures or crashes.
Data is collected from customers and their devices with the intention of providing personalized services and enhanced troubleshooting. Hexnode does not use this data for marketing or advertising the product. The data collected from the devices include device identifiers, hardware and software details of the device, files and content shared by the administering organization, and data requested through policies (For instance: location tracking data, data usage reports, etc.).
Only a selected team of employees at Hexnode is privileged to access the full data of customers. Moreover, access to these data is granted only if it is of the at-most necessity for troubleshooting purposes. The access is automatically logged, and the authorizations and entitlements are handled automatically via dedicated tools. Any confidential information in this data is automatically redacted before sharing it with the team. Hexnode has a multi-level privilege system regarding the sharing of non-confidential customer data between its employees. The technical support team is allowed to access the basic customer details (the details you provide during the sign-up, excluding the password). The engineering team can access the server logs and so on.
We have robust processes in place to facilitate a coordinated response to security incidents if one were to occur. A security event may refer to (but not limited to) loss of availability, unauthorized access resulting in loss, disclosure or alteration of data. In such a situation, we follow a well-drafted set of procedures: Identification and declaration of a potential event; Assignment of incident severity; Investigation and diagnosis; Containment; Eradication; Recovery; Collection of evidence; Communication with the clients; Formulate strategies to mitigate such future events.
To ensure your data doesn’t end up in the wrong hands, thorough background checks are conducted on the employees who handle the client data during the hiring process in accordance with the law. Hexnode may sometimes engage external third-party data subprocessors in delivering services, as stated in the SaaS agreement. Visit this article to learn more.
Hexnode has a strict two-factor authentication program that enforces portal login through two different authorization techniques to eliminate possible unauthorized access. The technicians will so be granted access only if both the logins are successful. Protected audit trails and action history reports of all the CRUD activities performed on the enrolled devices are also created and maintained in the MDM portal and are accessible to the authorized technicians anytime.
Physical Data Security
Hexnode’s data servers are hosted on Amazon Web Services (AWS) across multiple EU and US locations. The customer server instances and associated data storage are automatically assigned based on the location or as per request. AWS architecture incorporates core infrastructural and foundational technologies like data encryptions, DDoS mitigation techniques, and network management policies. This ensures privacy and industry-standard security.
The strategic positioning of Hexnode’s data centers across different secure locations ensures maximized protection from natural and direct attacks. AWS data centers are strictly monitored and are well secured against physical attacks. At Hexnode, we have a dedicated team of fully-fledged employees working to ensure infrastructure security through proprietary processes and security models. For more information about AWS cloud server security, visit Amazon cloud security.
Network Security
The security team at Hexnode is working around the clock to create safe network traffic and is fully prepared to detect, prevent, and mitigate intrusions and security threats.
Hexnode’s network security system incorporates a dedicated security team and the most modern technologies to defend the cloud, client devices, and the data managed by them from unauthorized activities and attacks. We employ the most modern tools, battle-tested strategies, and processes to counter threats like malware and hacker attacks proactively.
The first step in securing any cloud network is to control access to resources. Hexnode’s firewalls segregate the untrusted network traffic from the safer ones.
Hexnode follows the standard security practices to mitigate impersonation attacks, cross-origin requests, and more. We use Advanced Encryption Standard (AES 256) based encryption for all devices and web-based applications in the corporate network. The security team and automated tools periodically monitor the network traffic for malware and suspicious activities. They use file integrity (host files) detection, intrusion detection and prevention, risk identification and breach management systems to analyze, identify and manage the threats. The logs are then forwarded to our SIEM. Hexnode uses multiple identity and access management systems to enable the employees both role-based and context-based entitlement to network, data and applications.
We use dedicated tools to perform automated vulnerability/exploit scans of our service, applications, and application dependencies on an ongoing basis, and we do manual scans to investigate any vulnerabilities reported. We have a process to review any reported vulnerabilities and formally track and remediate them on priority and in the mission-critical time frame.
Hexnode uses AIDL for intercommunication between its apps (Remote view, Hexnode browser, etc.). Android OS secures all communications through AIDL by validating the certificate of the communicating apps. This disallows any third-party applications from eavesdropping on confidential information shared among the apps.
Hexnode offers a well-structured set of APIs for letting organizations automate their repetitive tasks. A private API key (available at Hexnode portal) is used to ensure the authenticity of API requests. Therefore, only approved technicians of your organization will be able to use Hexnode’s APIs. Moreover, Hexnode’s API requests are well secured using SSL to avoid all kinds of man-in-the-middle attacks.
All applications from Hexnode are signed using a private certificate. This lets the host OS ensure the authenticity of the updates being installed to the system. Any attempt to install a reverse-engineered or modified version of these applications will be blocked by the host OS.
Privacy Policy
All data that are given to Hexnode by the organization or on behalf of the organization will be used by Hexnode to provide and improve the services only. The organization’s IT administrator can access and request to delete the provided data anytime, no questions asked.
In case if you have created user accounts by syncing with the directory services, Hexnode will not access your directory credentials. We use the OAuth authentication method to grant access to the information and approve actions. Hexnode uses one-way hashing to securely store local user credentials in the server. As data controllers, Hexnode is fully compatible with the GDPR and Privacy Sheild Framework and exercises extreme caution while utilizing the data to provide and troubleshoot services. Hexnode has also achieved certificates and standards, including PCI DSS, and others. Hexnode is currently pursuing ISO 27001 certification and is expected to be compliant by the last quarter of 2021. For more information about data privacy, visit Hexnode’s Privacy Policy and GDPR statement.
Data Retention
People are the owners of their own data. Hexnode provides data portability to all individuals. If you decide to leave Hexnode, no data of yours will be retained after the time specified in the GDPR laws.
If the organization ends the Hexnode subscription or does not subscribe after the trial period, the data will be purged. However, the data back-up will be retained for 28 days complying with the Right to erasure of the GDPR.
Endpoint security
Endpoint devices managed by Hexnode are encrypted and password-protected if the end-user grants his/her consent to ensure maximum protection for sensitive corporate data.
With Hexnode, you can restrict corporate devices to only connect to networks with WPA2 or higher security standards. You can also filter the network traffic by only allowing corporate devices to connect to the company network.
The top priority of Hexnode is to provide quality and secure services to its users. To update the employees about the latest security trends and best practices in cloud security, Hexnode hosts an annual security meet for all the employees.
Development cycle
At Hexnode, the engineers follow a strict procedure during the development cycle. Each line of the source code is carefully drafted and is hosted in version-controlled software repositories. This code is peer-reviewed and is manually and automatically tested for security threats and software bugs prior to its distribution.
Attestation
Hexnode UEM does not have any inherent constraints that would intercept in meeting any future scalability requirements of the Government or your organization. Hexnode is always keen at finding possible chances of security breaches even before any potential exposure, reducing the risk of liabilities. However, in case of an infringement, Hexnode is accountable in explaining the incident history and the mitigation methods implemented to the client.