Category filter
Configuration profile to disable Siri on macOS devices
Siri is Apple’s voice-activated virtual assistant that simplifies and enhances various tasks on Apple devices through natural language voice commands. However, in a work environment consisting of Macs, privacy and security concerns related to Siri can be significant. Siri, if used in noisy environments or, when permitted interactions with third-party applications that require access to sensitive data sources on your Mac, can pose security risks. This may lead IT administrators to consider disabling or restricting its use.
Disabling Siri individually on a fleet of devices can be cumbersome. That’s where Hexnode’s Deploy Custom Configuration feature comes in. Learn how to disable Siri efficiently using a configuration profile through Hexnode.
Configuration profile to disable Siri on Macs
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 |
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>PayloadContent</key> <array> <dict> <key>PayloadDescription</key> <string>Configures restrictions</string> <key>PayloadDisplayName</key> <string>Restrictions</string> <key>PayloadIdentifier</key> <string>com.apple.applicationaccess.EC187132-755E-4500-B2EA-8DB072401C74</string> <key>PayloadType</key> <string>com.apple.applicationaccess</string> <key>PayloadUUID</key> <string>EC187132-755E-4500-B2EA-8DB072401C74</string> <key>PayloadVersion</key> <integer>1</integer> <key>allowAssistant</key> <false/> </dict> </array> <key>PayloadDisplayName</key> <string>Untitled</string> <key>PayloadIdentifier</key> <string>1B64A284-C44B-4588-BE57-C2994AA8C611</string> <key>PayloadRemovalDisallowed</key> <false/> <key>PayloadType</key> <string>Configuration</string> <key>PayloadUUID</key> <string>9DF9AAFF-3913-40BE-8638-07E3B0013E9A</string> <key>PayloadVersion</key> <integer>1</integer> </dict> </plist> |
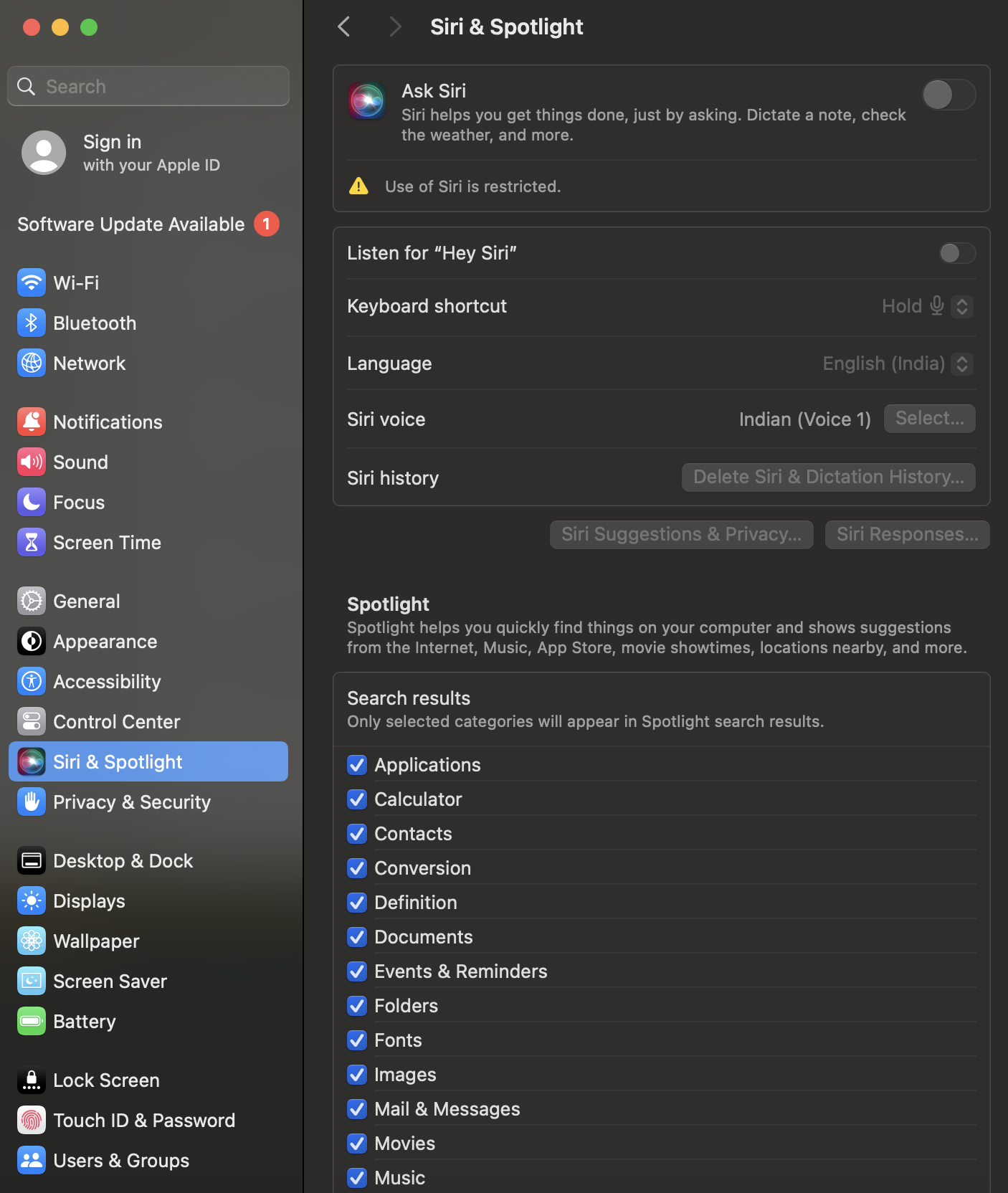
In the above configuration profile, the “allowAssistant” key should be set to false to disable Siri. Once the configuration profile is successfully deployed to the device, the settings related to Siri will be greyed out under System Settings, accompanied by a warning message stating, “Use of Siri is restricted”.
Configuration profile to enable Siri on Macs
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 |
<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>PayloadContent</key> <array> <dict> <key>Assistant Enabled</key> <true/> <key>PayloadDisplayName</key> <string>Assistant</string> <key>PayloadIdentifier</key> <string>com.apple.assistant.support.F0AA5679-B2E3-49E2-BCCC-F3A5A974CFC0</string> <key>PayloadType</key> <string>com.apple.assistant.support</string> <key>PayloadUUID</key> <string>F0AA5679-B2E3-49E2-BCCC-F3A5A974CFC0</string> <key>PayloadVersion</key> <integer>1</integer> </dict> </array> <key>PayloadDisplayName</key> <string>Untitled</string> <key>PayloadIdentifier</key> <string>1234567</string> <key>PayloadType</key> <string>Configuration</string> <key>PayloadUUID</key> <string>780C35E8-A9C0-4030-8CCB-F3C97B8C39A1</string> <key>PayloadVersion</key> <integer>1</integer> </dict> </plist> |
In the provided configuration profile, the “Assistant Enabled” key should be set to true to enable Siri. Once the configuration profile is successfully deployed to the device, the “Ask Siri” option under System Settings > Siri & Spotlight will be enabled, and users will not be able to disable it.