Category filter
How to fix issues with enabling FileVault on Mac
FileVault is a complete disk encryption program on macOS 10.3 or higher versions for securing data. Hexnode UEM provides an effective mechanism to associate policies from the MDM console to enable FileVault on the devices. However, in some instances, the users might face problems turning it on. This documentation assists the users in fixing issues associated with enabling FileVault.
Problems while enabling FileVault:
After associating the FileVault policy, the device might fail to enable FileVault due to various reasons. Sometimes an error message is displayed stating the reason for failure as the device is restarted or during the next user login.
Common errors
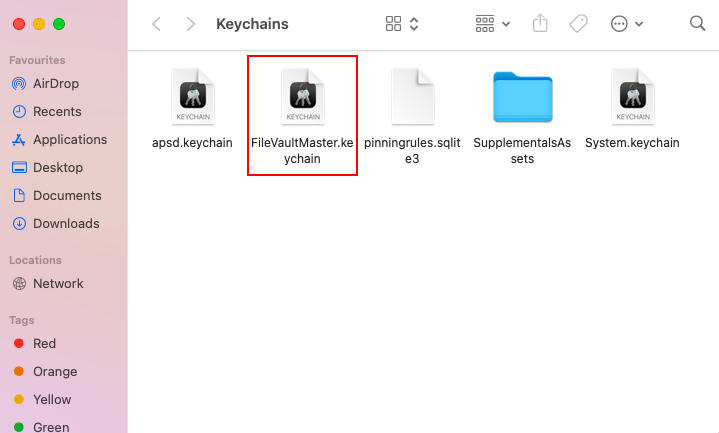
- “An unexpected master password keychain was found.”
Description: When FileVault encryption is enabled with the help of a Personal Recovery key, sometimes it generates this error message as the user restarts or logs out of the device to turn on FileVault.
Solution: The error can be rectified by removing the master password keychain file FileVaultMaster.keychain found in the path /Library/Keychains. Further restarting the device helps to resolve the issue.
Other issues and methods to resolve them
- The given user account that enables FileVault requires a security token to be enabled.
Solution: Add a valid secure token to the user account
On devices running macOS 10.13 and higher, the user (mobile account or user account) needs to have a secure token to activate FileVault. Active Directory users (mobile user accounts) do not have a secure token enabled on them automatically. On the contrary, the server token is enabled on local accounts when such accounts are created. Hence, in the case of an Active Directory user, he/she might experience issues with enabling FileVault. Follow the steps to add a server token to a local user account:
- Log in to the given user account.
- Open Terminal.
- Execute the following command:
1sysadminctl interactive -adminUser [admin_username] -adminPassword [adminpassword] -secureTokenOn [username_that_needs_token] -password [userspassword]
- Log out from the Mac. Log in once again to the given account for the command to take effect.
- Disk problems associated with formatting or directory structure of the device.
Solution: Use Disk Utility to repair the formatting information.
If the users find difficulty in enabling FileVault even when the policy is applied on the devices, you can go for repairing the formatting information on the storage devices. You can make use of the Disk Utility app to repair the disk’s formatting information.
- Open the Disk Utility app on the device that faces the issue.
- Select the volume/container on the storage device.
- Click on First Aid.
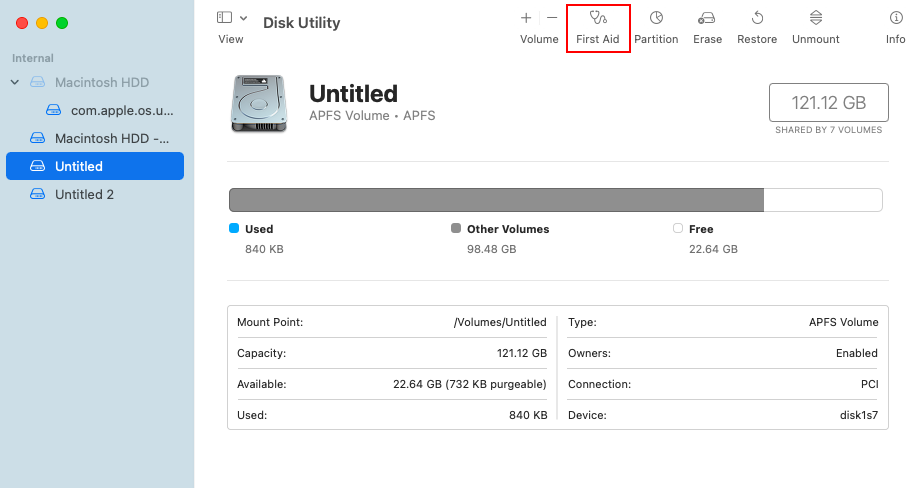
- The device prompts you to confirm the repairing process. Click on the Run button.
- The First Aid checks the given volume/container for errors and repairs it if any corruptions are found. You have to repeat the procedure separately on each volume/container to check them.
-
The device is outdated.
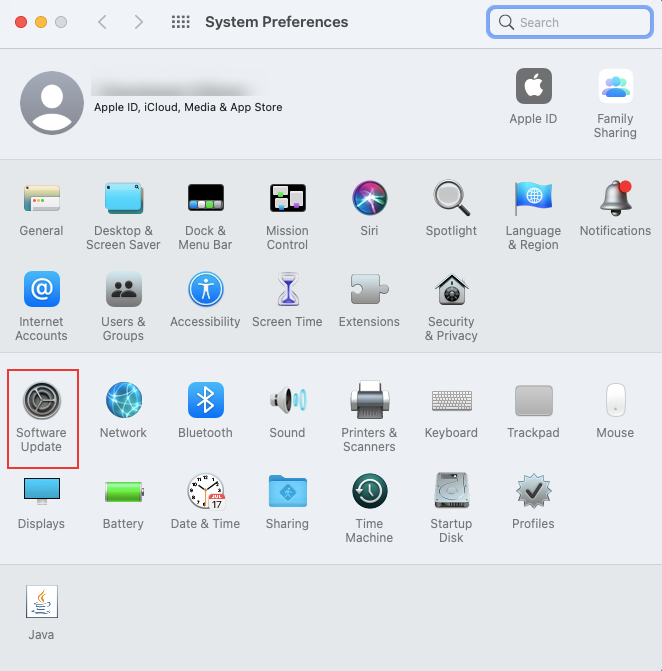
Solution: Update the device
The error might be because of a software bug. The best way to recover the software bugs is to update the software by navigating to System Preferences > Software Update.
FileVault decryption on an already encrypted Mac
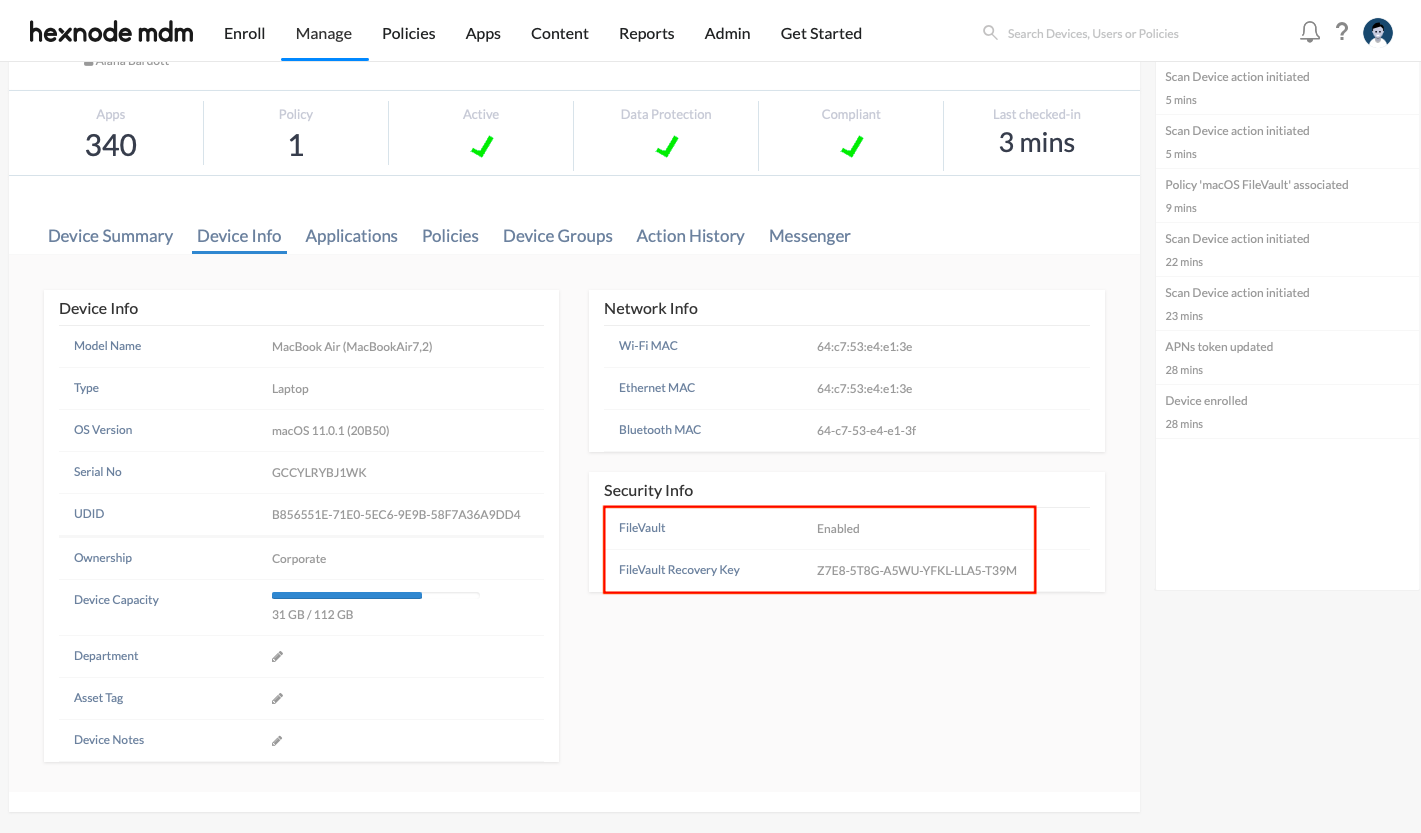
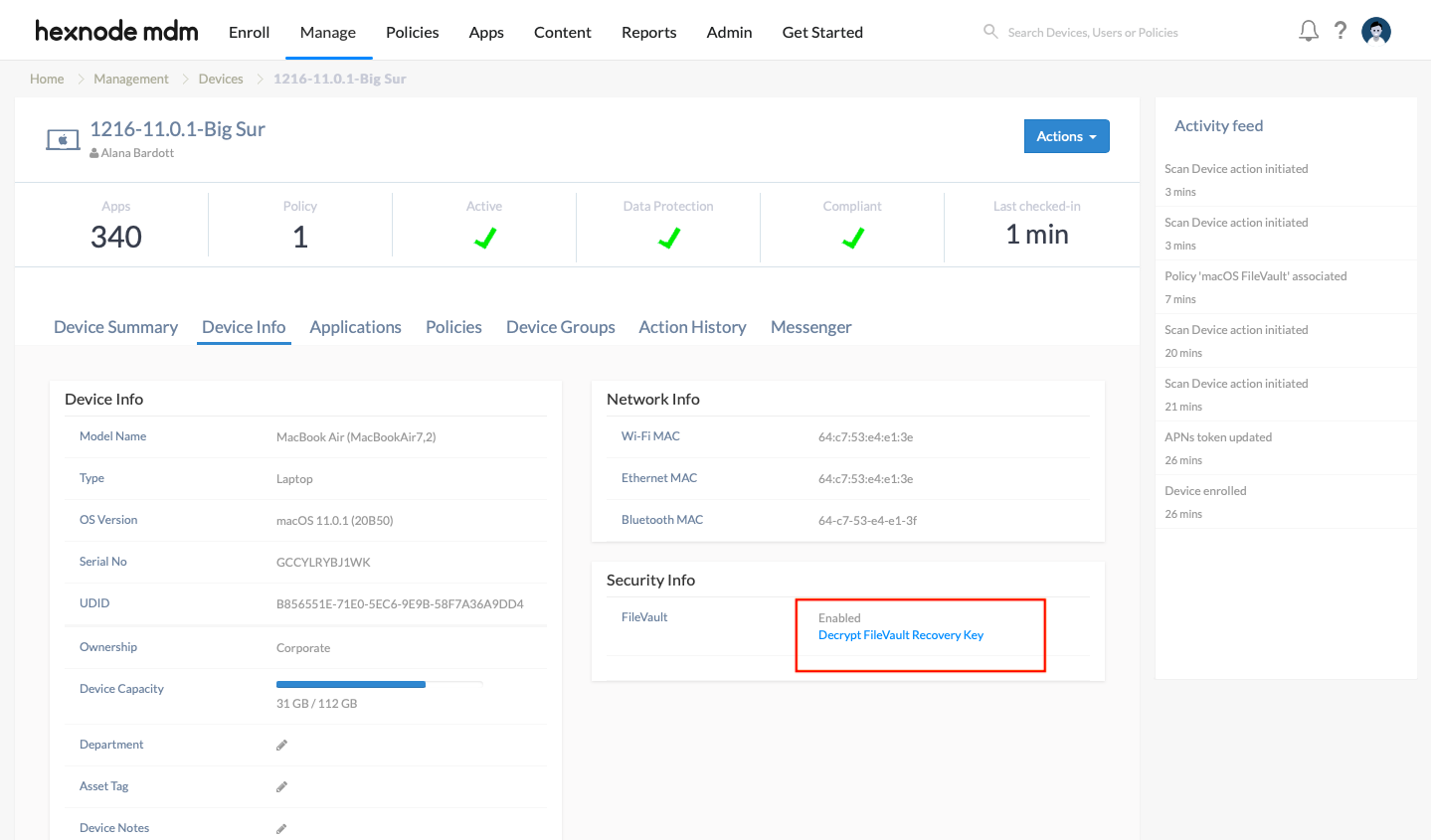
Once the FileVault policy is associated, you can retrieve the personal recovery key of a device that gets automatically escrowed to the Hexnode UEM console. The Decrypt button displayed under Device Summary > Device Info > Security Info > FileVault Recovery Key helps to recover the personal recovery key that you can use to decrypt the macOS disk.
But, the decryption key cannot be retrieved from the portal if the device is encrypted before enrollment or before a FileVault policy is associated.
You may encounter issues retrieving the FileVault Recovery Key in the following cases:
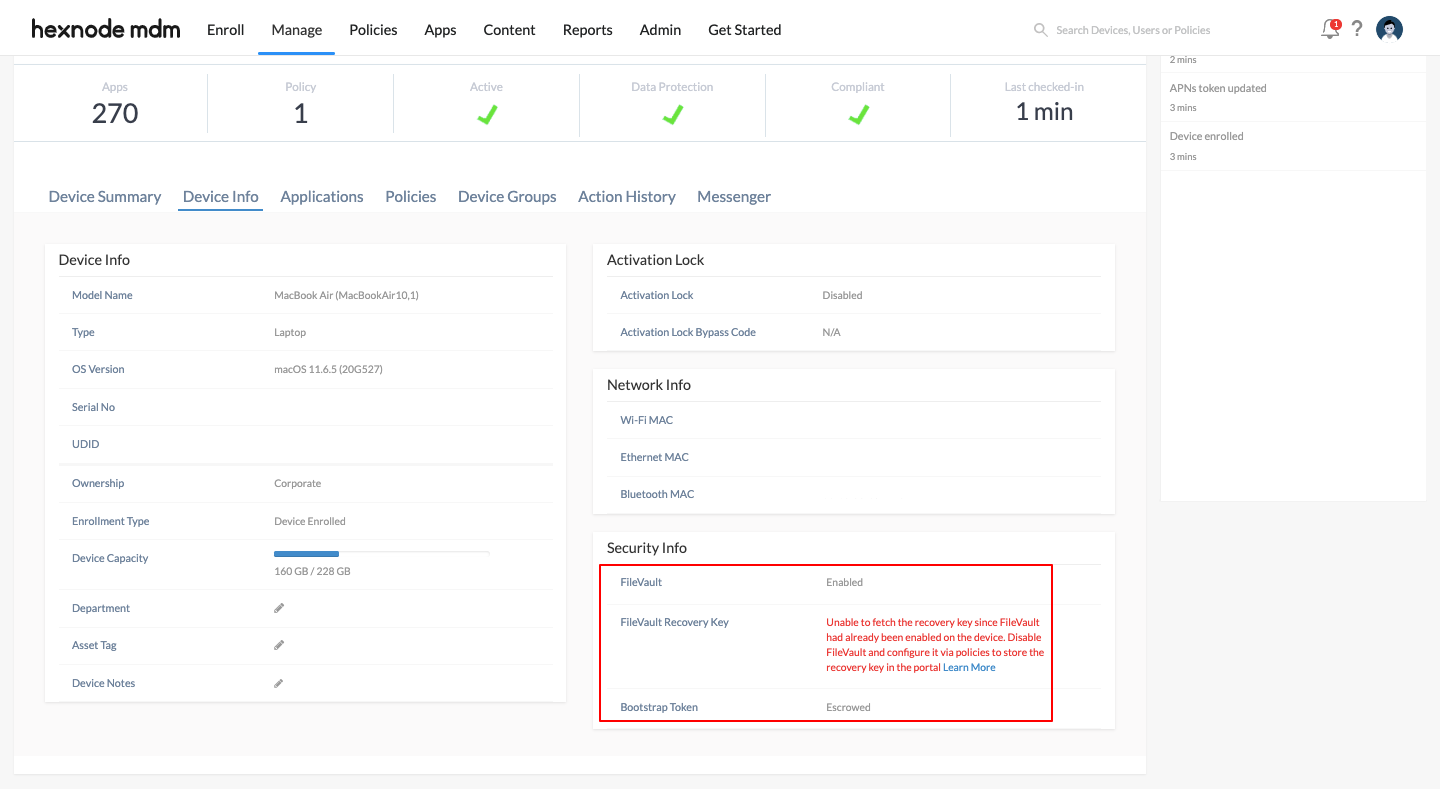
Case 1: “Unable to fetch the recovery key since FileVault had already been enabled on the device. Disable FileVault and configure it via policies to store the recovery key in the portal”
Description:
If a FileVault policy with the Escrow Personal Recovery Key option enabled, is applied to an already encrypted device, you’ll get the above message instead of the FileVault Recovery Key.
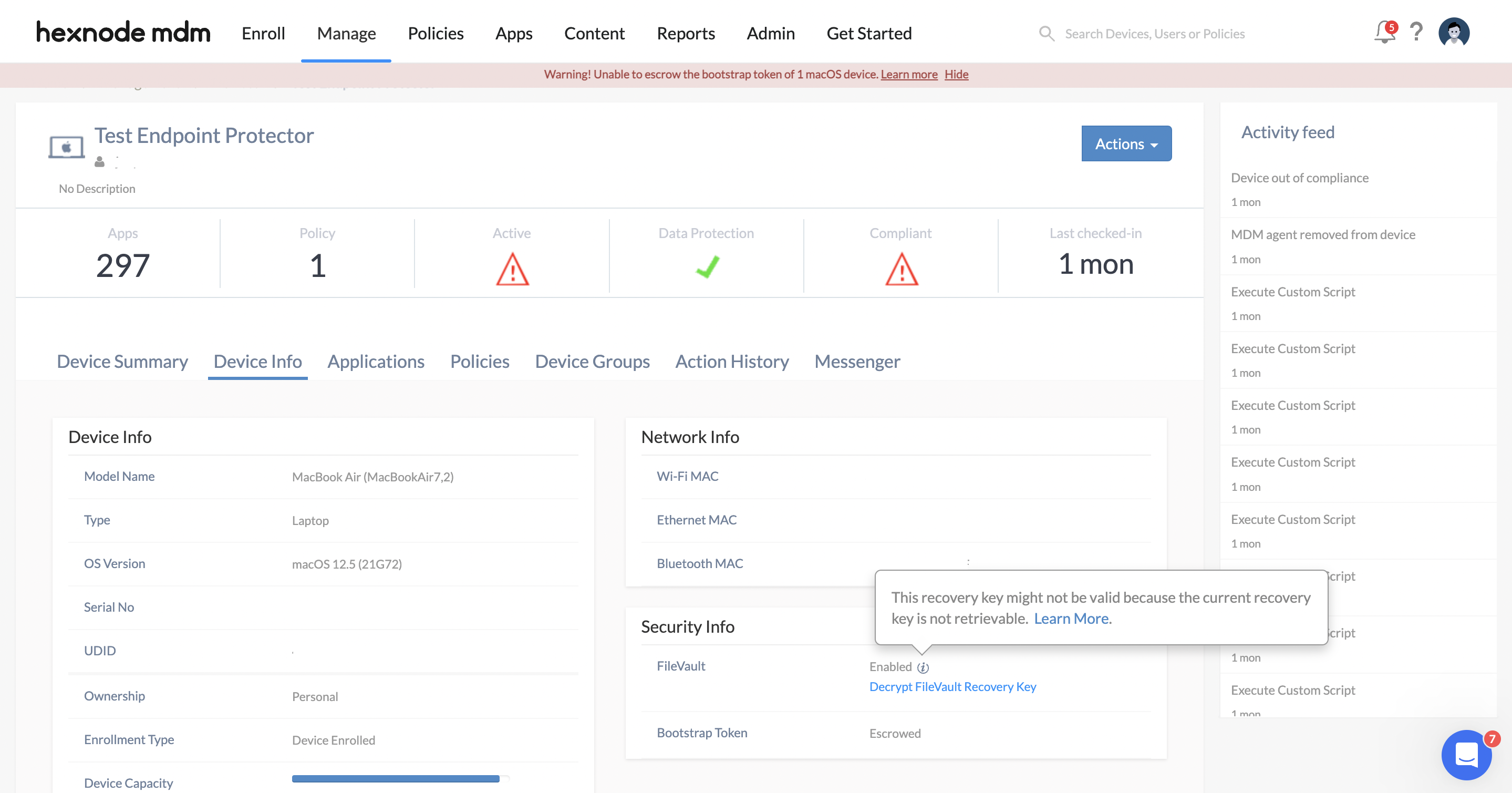
Case 2: “This recovery key might not be valid because the current recovery key is not retrievable.”
Description:
The recovery key displayed on the portal might be invalid if:
- the Hexnode MDM profile is removed from a device that has a FileVault policy associated (with the Escrow Personal Recovery Key option enabled), and
- the device is re-enrolled, and the FileVault policy remains associated.
In the above circumstance, the current recovery key is not retrievable.
In such cases, you have the option to either disable the FileVault from device end before implementing the policy or set up a new personal recovery key from the Terminal.
Here’s how you can set up a new personal recovery from the device’s Terminal:
- Open the Terminal on the Mac.
- Run the following command:
1sudo fdesetup changerecovery -personal
- A new recovery key will be displayed in the Terminal.
- Log in to the Hexnode portal.
- Execute the
Scan Device action on the device. - The option to decrypt the FileVault recovery key will be displayed under Security Info.
- Select the option ‘Decrypt FileVault Recovery Key’.
- Choose the method of encryption used.
- Click Decrypt.
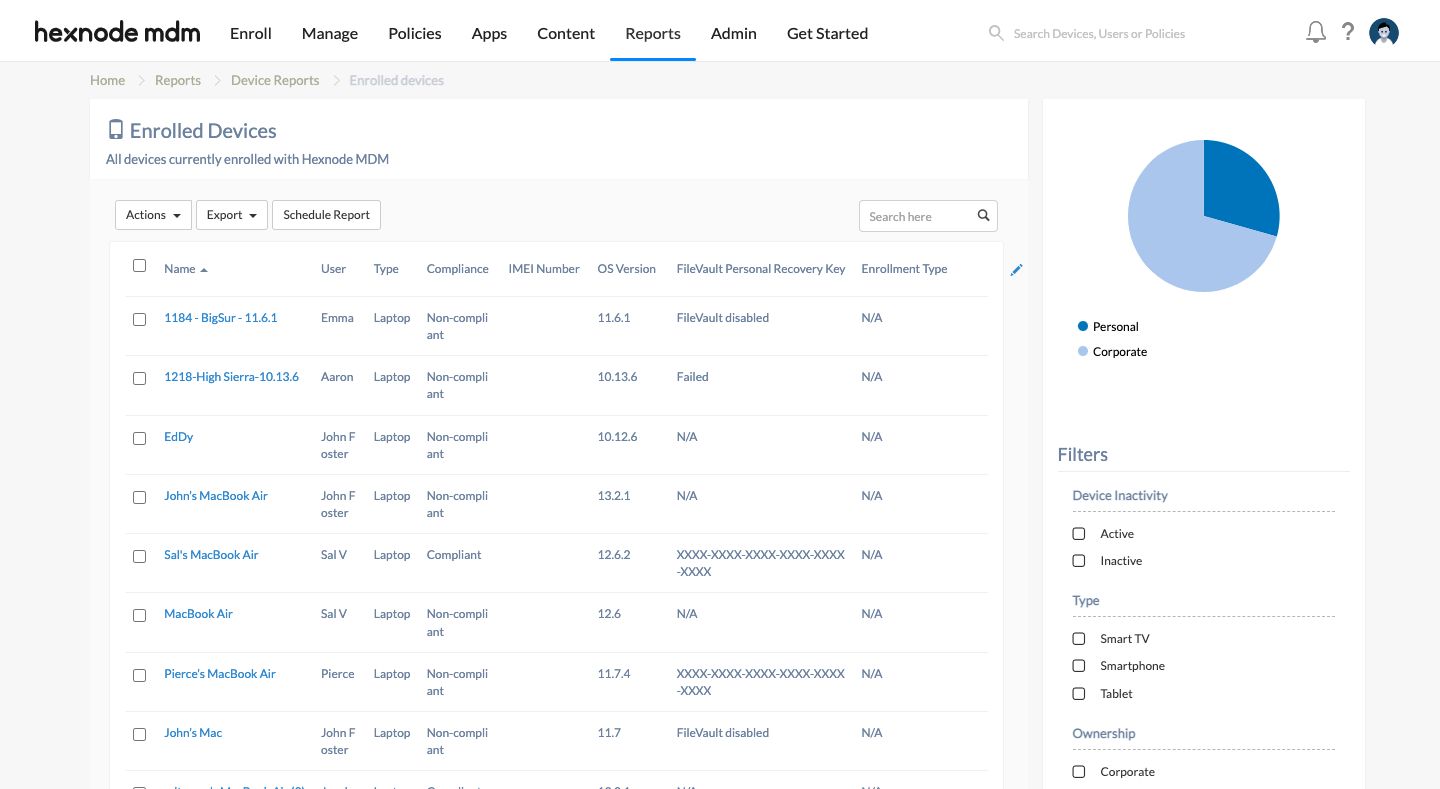
The valid FileVault recovery key will be displayed next to the FileVault option under the Security Info of the device on the Hexnode portal. Alternatively, you can verify the FileVault recovery key info and the device’s encryption status using the Reports tab. Navigate to Reports > Device Reports > Enrolled Devices and search for the device. The FileVault Personal Recovery key column displays either the decrypted recovery key or any of the following statuses:
- Failed: It is shown when the recovery key is not fetched despite enabling the Escrow Personal Recovery Key option on the FileVault policy associated with the device.
- N/A: It indicates that the FileVault is enabled and the recovery key has been fetched but is not decrypted.
- FileVault disabled: The FileVault is disabled in the device.