Category filter
Troubleshoot Common Issues with BitLocker
BitLocker, the Windows full-disk encryption program, can be enabled on Windows devices with the BitLocker security policy in Hexnode. This encryption helps to secure the integrity of the device even in compromised environments by encrypting the entire OS volume in the hard disk and by verifying the boot process integrity.
1. BitLocker policy association fails as the system cannot find the specified file.
Indication:
When you are associating the Windows BitLocker security policy through Hexnode, it fails and returns the error message:
“Unable to turn on BitLocker as the system cannot find the file specified. Resetting the REAgent.xml file may help in resolving the issue.”
If you are directly turning on BitLocker on such devices without the UEM policy, the OS will throw an error message: System cannot find the file specified.
Solution:
To resolve this issue, you have to reset the REAgent.xml file on the device. To do so,
- Find your target Windows device and open the File Explorer by clicking the keys Windows and E together.
- Head on to C:\Windows\System32\Recovery.
- Find the REAgent.xml file and right-click on it.
- Click on Rename to rename the file REAgent.old.
- Click on Yes in the prompt you receive.
After successfully resetting the REAgent.xml file, reassociate the BitLocker policy with the device.
2. The policy doesn’t reach the target device
Description:
The applied BitLocker policy fails to reach the device end.
Probable Causes:
- The device doesn’t have an active internet connection.
- The device is not listed under the Policy Targets.
Possible Solutions:
- Establish an active network connection on the device for the policy to take effect.
- Check whether the device is listed as a target under the Policy Targets tab of the same BitLocker policy.
3. The policy reaches the device, but BitLocker settings are not getting applied to the device
Description:
The BitLocker policy pushed from the Hexnode portal reaches the device end, but some BitLocker settings are not getting applied to the devices.
Probable Cause:
Some BitLocker settings are not supported on all Windows versions. Also, BitLocker may not work on all hardware.
Possible Solution:
Make sure the devices satisfy the BitLocker software or hardware requirements. Check out BitLocker CSP for details on the supported Windows versions for each BitLocker setting. Also, see the hardware requirements needed for BitLocker encryption.
4. Force BitLocker Encryption remote action fails with an error message
Description:
When Force BitLocker Encryption remote action is applied through Hexnode, it fails and returns the error message:
“The device is either partially or fully encrypted. Please decrypt the device entirely before applying this action.”
Probable Cause:
The BitLocker in the device might have already been configured manually or by BitLocker Windows policy from the Hexnode UEM portal.
Possible Solution:
Please make sure that the BitLocker is not configured nor turned on before executing the action. If it is turned on, turn it off manually to re-configure it from the Hexnode UEM portal.
Here’s the list of some common error messages shown in Windows Event Viewer (Applications and Services logs > Microsoft > Windows > BitLocker API), their causes and possible remedies.
1. A compatible Trusted Platform Module (TPM) Security Device cannot be found on this computer
Description:
The error message indicates that the devices do not possess a compatible TPM chip.
Probable Cause:
The device may not appear to have a TPM chip, or the device BIOS has disabled it.
Possible Solution:
Ensure that the device BIOS has enabled TPM. Run the below PowerShell command to obtain information about the Trusted Platform Module (TPM) on the computer:
|
1 |
Get-Tpm |
Besides, verify that the TPM status in the TPM management console shows the following:
- Ready (TPM 2.0)
- Initialized (TPM 1.2)
2. BitLocker Drive Encryption detected bootable media (CD or DVD) in the computer
Description:
The error message indicates that the device contains bootable media (CD or DVD).
Probable Cause:
The BitLocker Drive Encryption records the device configuration in order to establish a baseline during the provisioning process. If it detects any changes to the device configuration later, it will enter into BitLocker recovery mode. To combat this scenario, the process stops if it finds any removable bootable media on the device.
Possible Solution:
Try removing the bootable media from the device and then restart it. Then verify the encryption status after the device restart.
3. WinRE is not configured
Description:
This error message indicates that the device is incapable of supporting encryption as Windows Recovery Environment (WinRE) is not properly configured.
Probable Cause:
The provisioning process cannot start unless Windows Recovery Environment (WinRE) is available on the device.
Possible Solutions:
Resolve the issue by verifying the following:
- Configuration of the disk partitions
- WinRE status
- Configuration of Windows Boot Loader
4. Contact the computer manufacturer for BIOS upgrade instructions
Description:
Encryption cannot be enabled on the OS drive.
Probable Cause:
The device must have legacy BIOS that is not compatible with BitLocker device encryption.
Possible Solution:
To check the BIOS mode, start with the below steps:
- Click the Start menu and search for msinfo32.
- Check that the BIOS Mode setting is not Legacy. If it is Legacy, switch it to UEFI or EFI mode.
5. BitLocker cannot use Secure Boot for integrity
Description:
Cannot read the Unified Extensible Firmware Interface (UEFI) variable ‘Secureboot’ for integrity.
Probable Cause:
Secure Boot should be turned on for BitLocker device encryption.
Possible Solution:
Verify the Platform Configuration Register (PCR) validation profile of the TPM and the state of Secure Boot.
6. Drive Encryption cannot be applied to this drive
Description:
Cannot enable encryption on OS drives due to conflicting Group Policy settings for recovery options.
Possible Solution:
Check out the possible group policy conflicts to resolve this issue.
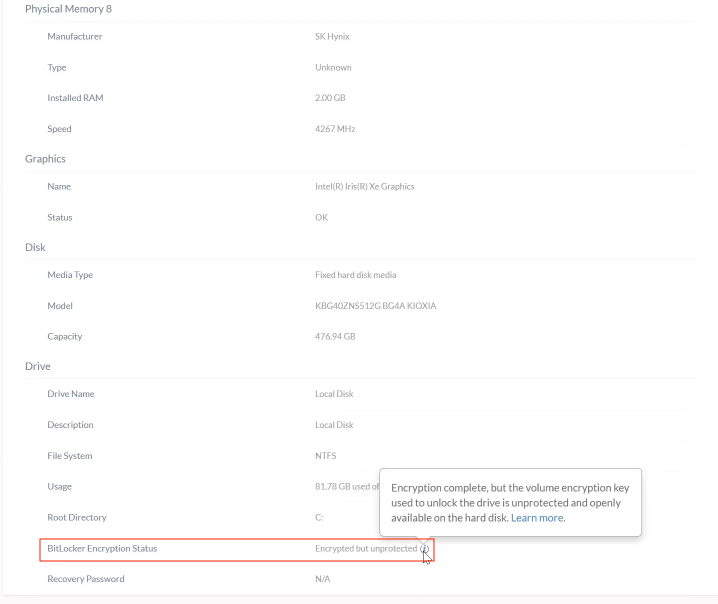
7. Force BitLocker Encryption action fails, status indicates ‘Encrypted but Unprotected’ and volume encryption key is available on hard disk
Description:
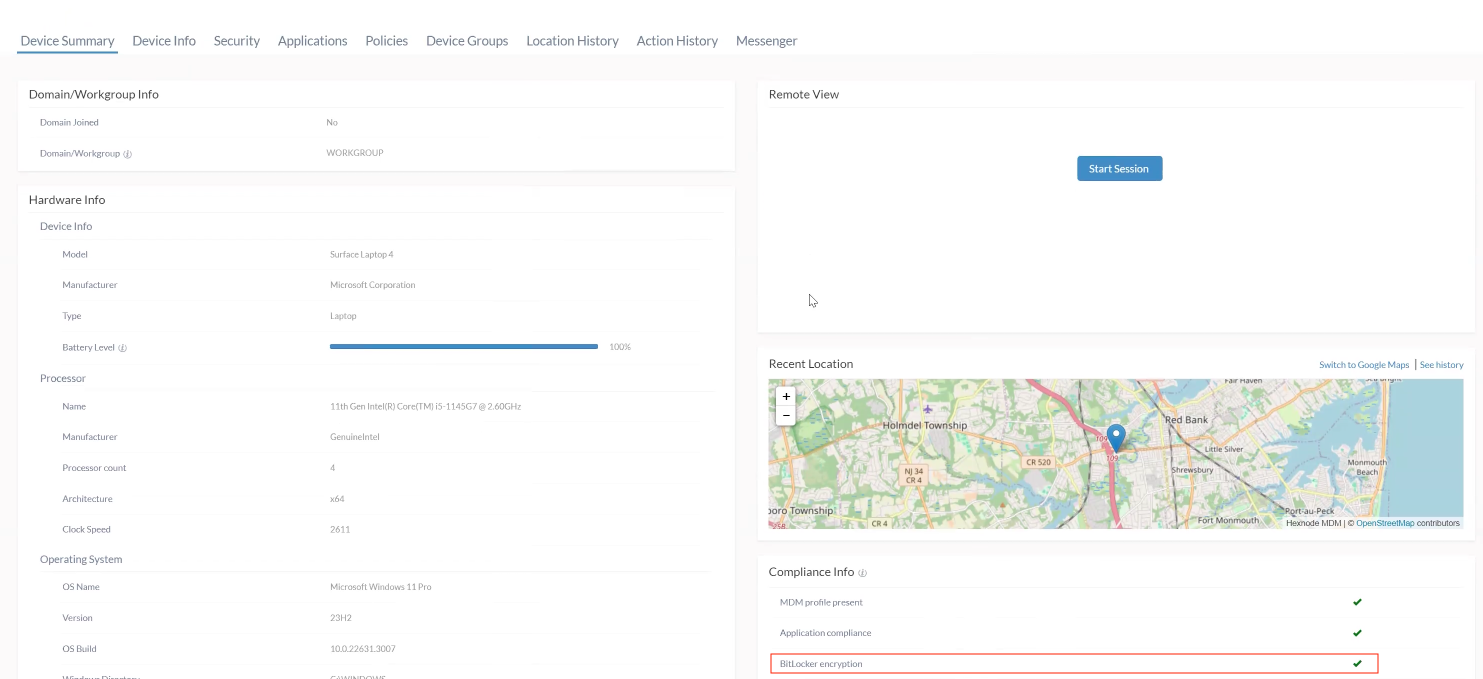
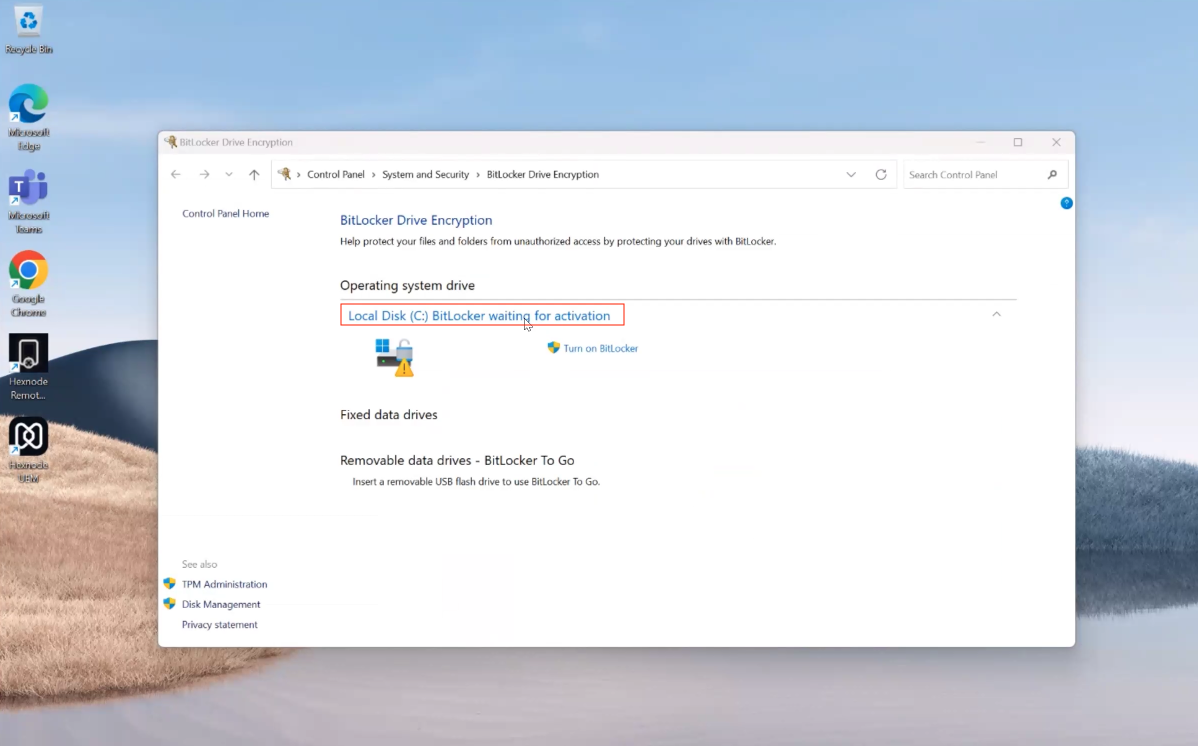
After deploying the BitLocker policy on the device, a prompt related to encryption is encountered on the device. Clicking on the prompt directs to the Device encryption section, where encryption is indicated as “ON,” and the BitLocker setting displays the status as “BitLocker waiting for activation.” Also, attempts to force BitLocker activation via remote actions result in an error. In the Hexnode portal’s device summary, the encryption status indicates “Encrypted but unprotected,” with the volume encryption key being exposed on the hard disk.
Probable Cause:
When a user first signs in to a Windows 10 or later device with a personal Microsoft account or a work/school account, a feature called Device encryption turns on BitLocker automatically. If you apply a BitLocker policy to a device that already has this encryption turned on, it will cause the policy to fail.
Possible Solution:
Disabling the Device encryption option under the Privacy and security section in the device settings will prevent the failure of the BitLocker policy or the Force BitLocker Encryption remote action. This allows the encryption to continue and makes it easy to escrow the BitLocker encryption key to the Hexnode portal.
8. BitLocker policy failure, status indicates ‘Failed to apply the action to the device’
Description:
The BitLocker policy failed, and an error message appeared on the Hexnode UEM portal indicating that the policy could not be applied to the device.
Probable Cause:
This failure occurs if drive decryption on a Windows device is still in progress. Enabling the “Require encryption for OS and fixed data drives” option and applying the BitLocker policy during this time will lead to the encryption process failing, with an error message stating: Failed to apply the action to the device.
Possible Solution:
Wait until the drive decryption process is fully complete, then re-apply the BitLocker policy.