Category filter
Common Issues in Google Workspace Integration
1. While integrating Google Workspace with the Hexnode console, an error message Invalid Input appears.
Possible Cause
- This could happen if any of the steps went wrong while configuring Google Workspace.
Solution
Go through the steps and ensure that the below-mentioned ones are carried out properly.
- JSON file is downloaded from the corresponding Service account in Google Developers Console.
- Service Account Admin is chosen as the Service Account role.
- Enable Google Workspace Domain-wide Delegation option under the created Service Account is checked.
- Ensure that APIs and services are enabled.
- In the Google Admin Console, ensure that API clients are correctly authorized. (Syncing the users and user groups)
While integrating with Hexnode console,
- Ensure that the Google Workspace account’s Admin email is provided.
- A proper Domain name is provided.
- The correct JSON file is uploaded.
- The correct Token is provided.
Once these details are provided, the integration will be completed automatically.
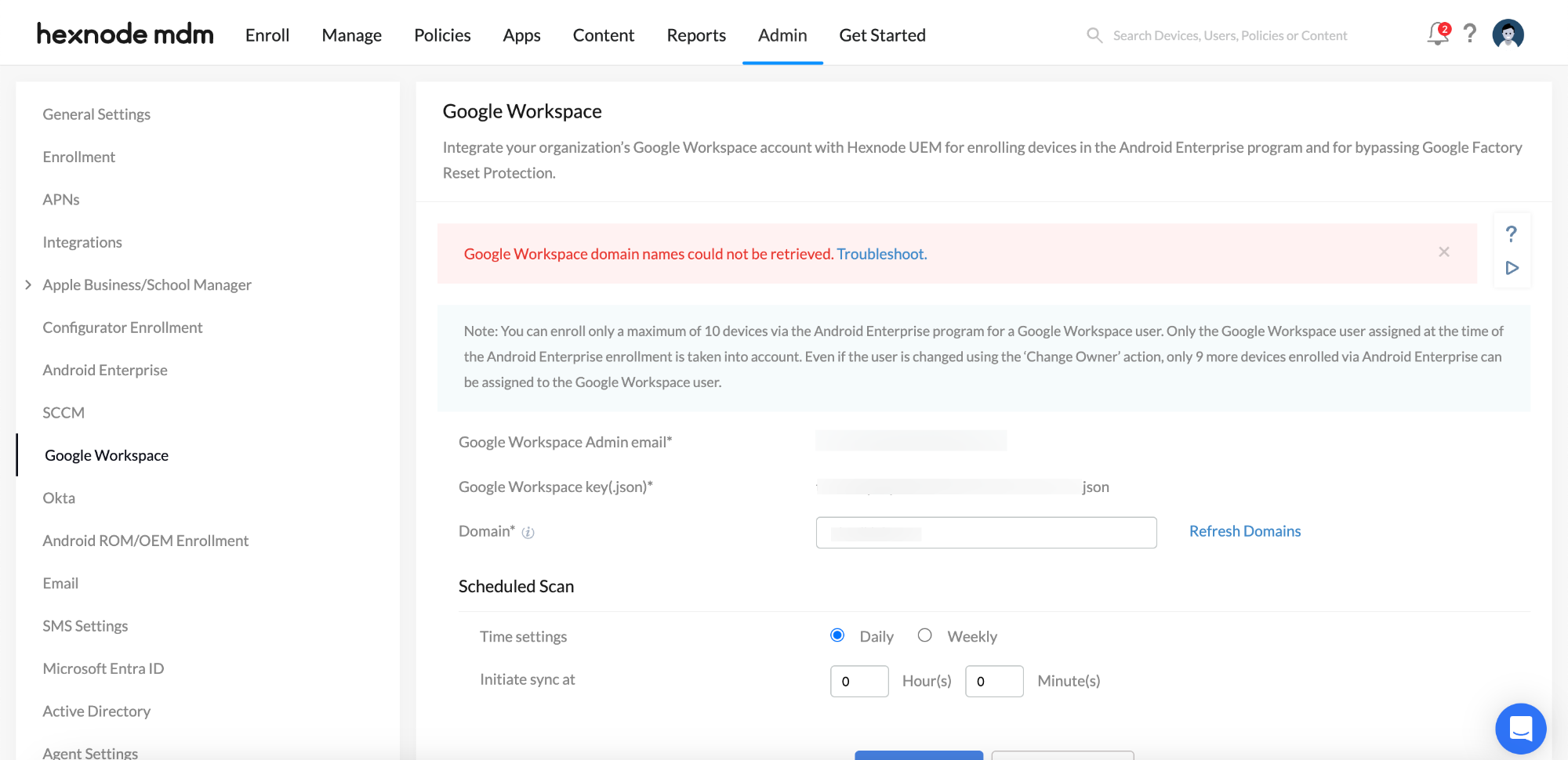
2. On integrating Google Workspace with Hexnode console, an error stating Google Workspace domain names could not be retrieved appears
Cause
Except for the primary domain, the sub-domains and users in the sub-domains are unable to synchronize with the Hexnode UEM portal.
Reason
The error indicating that Google Workspace domain names could not be retrieved may occur due to two possible reasons:
- The OAuth scopes for the API client do not include domain specification.
Since a Google Workspace account can have multiple domains, the users belonging to all the different domains are synchronized only if the domain scope is specified while managing access to the API client. - If the added Google Workspace account does not have the necessary admin privileges to retrieve domain details.
Solution
Include the domain scope for the API client from the Google Admin Console.
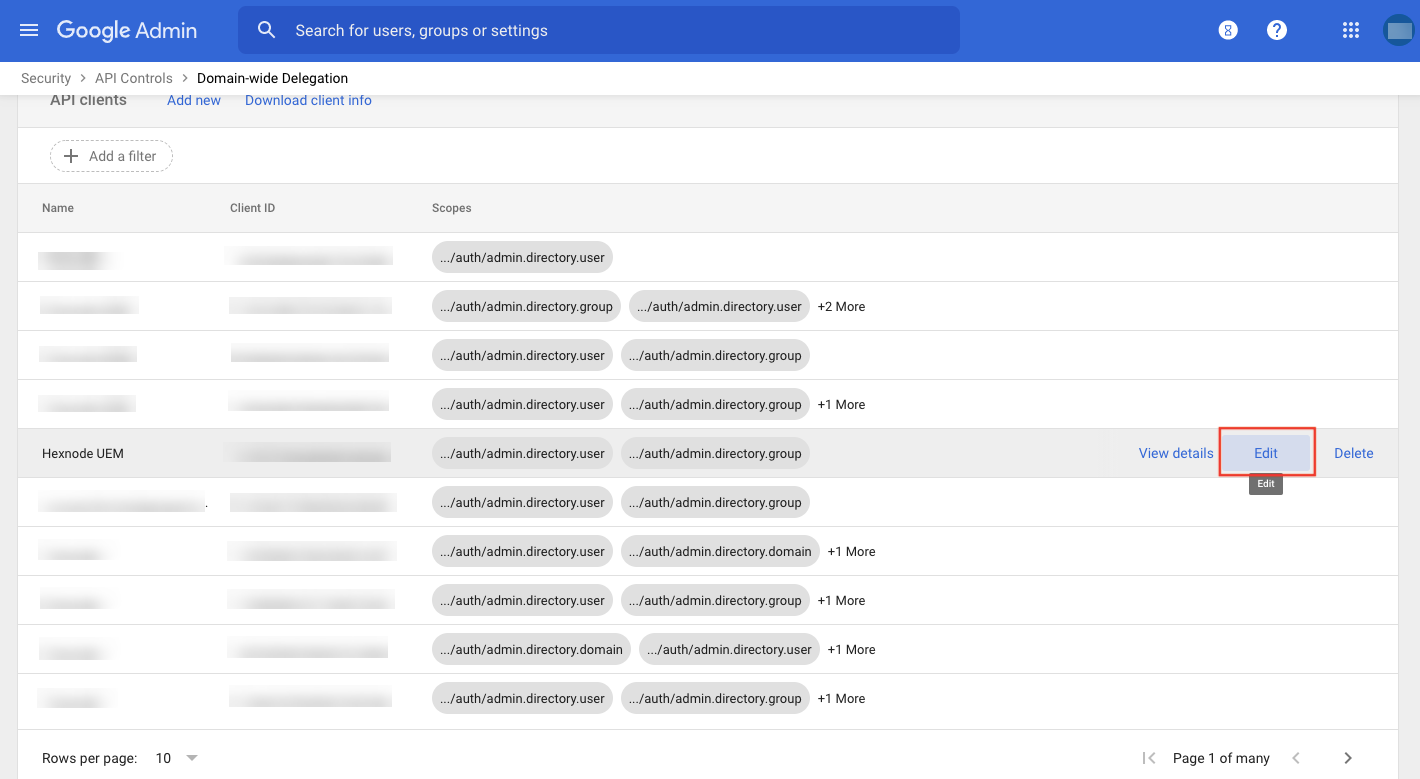
- Log in to Google Admin Console.
- Navigate to Security > API Controls > MANAGE DOMAIN WIDE DELEGATION > Domain wide delegation .
- Identify your API client from the list. Click Edit.
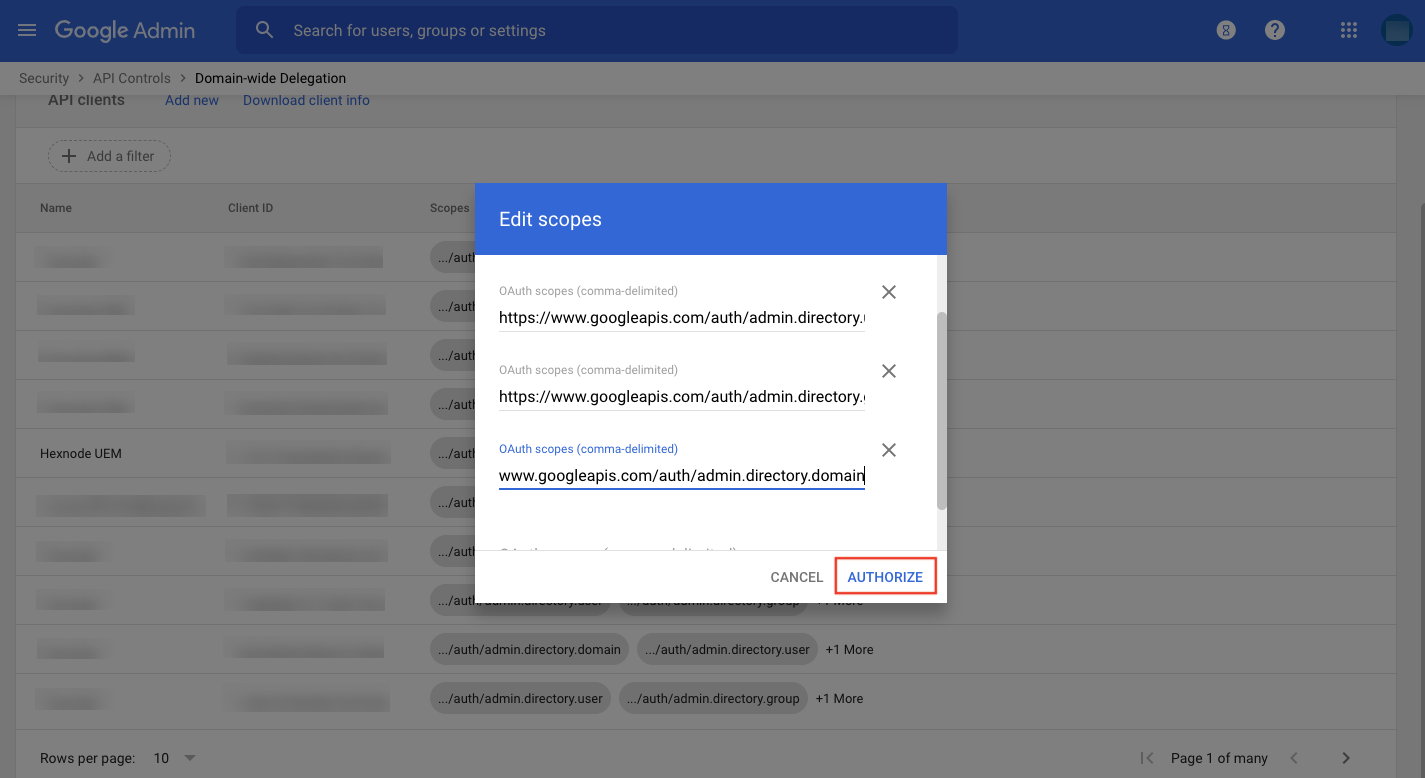
- Copy and paste the following link in the field OAuth scopes:
https://www.googleapis.com/auth/admin.directory.domain
- Click Authorize.
- Next, log in to the Hexnode UEM console.
- Navigate to Admin > Google Workspace.
- Click on the Refresh Domain button and click Save.
It refreshes the domain and syncs the user information from the sub-domains also.
The required admin privileges for the Google Workspace account can be granted using two methods:
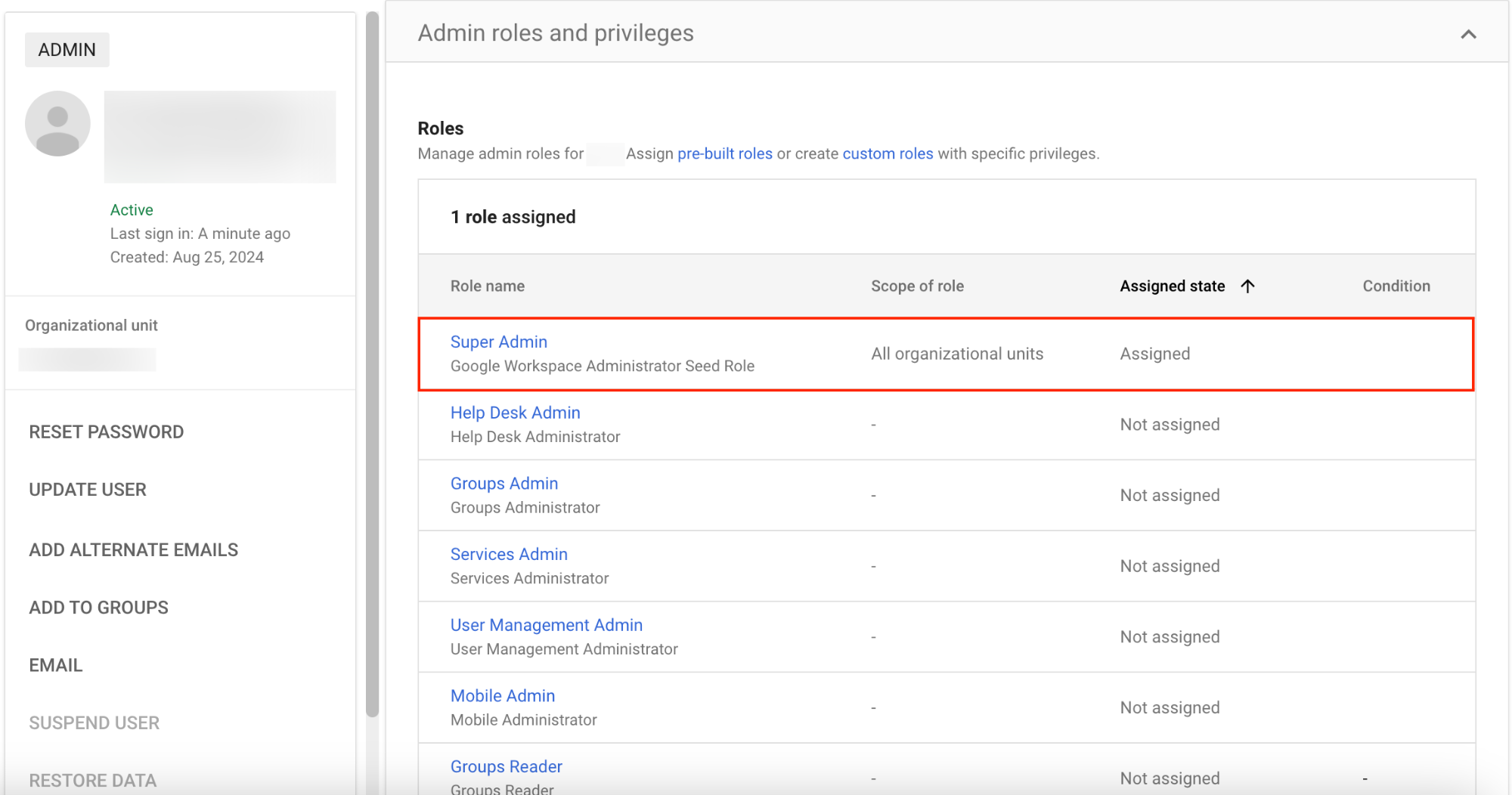
- Assign super admin role
- Log in to Google Admin Console.
- Navigate to the Users section.
- Click on the user’s name from the list of users.
- Go to Admin roles and privileges.
- Toggle the Super Admin role to Assigned by clicking the slider.
- Click Save to apply the changes.
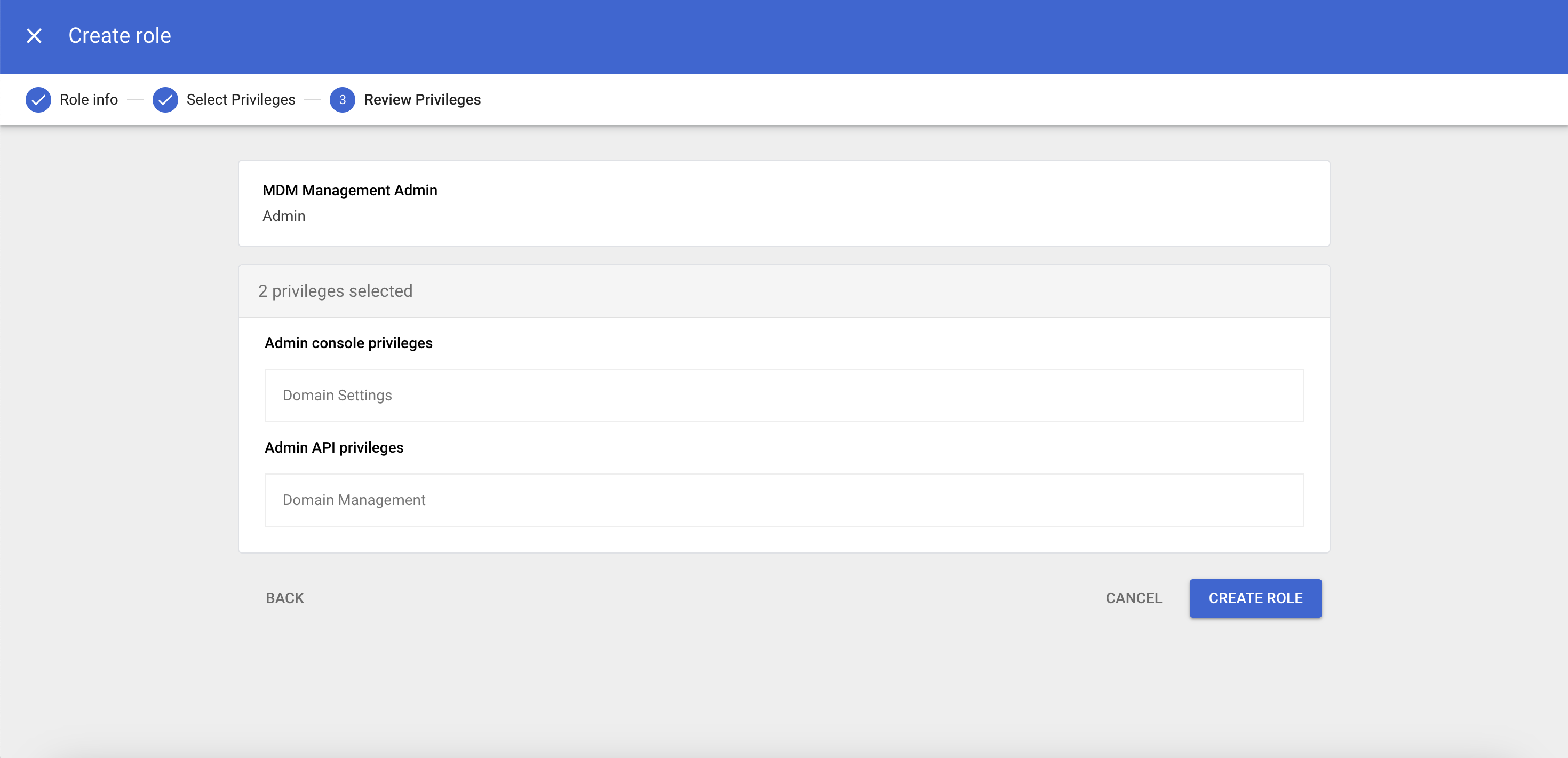
- Create a custom admin role with the required admin privileges
- Log in to Google Admin Console.
- On the Google Admin console, navigate to Menu > Account > Admin roles.
- Click on Create new role.
- Enter a name and, optionally, a description for the role and click Continue.
- Select the desired privileges, such as Domain Settings and Domain Management, from the Privilege Name list by checking the appropriate boxes.
- Click Continue to proceed.
- Review the selected privileges and click Create Role.
- Assign the custom role to the user.
3. ChromeOS devices listed under the Manage tab shows “N/A” with an error “Could not fetch the user from Google. To find out why, click on Learn more.”
Cause
The annotated user of the ChromeOS device has not been synced with Hexnode UEM.
Reason
During the initial enrollment process, each ChromeOS device is assigned to a user in Google Workspace. In Google Workspace, users are organized under specific domains. When integrating Google Workspace with Hexnode UEM, you have the option to sync only selected domains. If the domain that includes the user associated with a particular ChromeOS device is not included among the synced domains from Google Workspace, the user field corresponding to that device will display “N/A” in the Manage tab of the Hexnode UEM console.
Solution
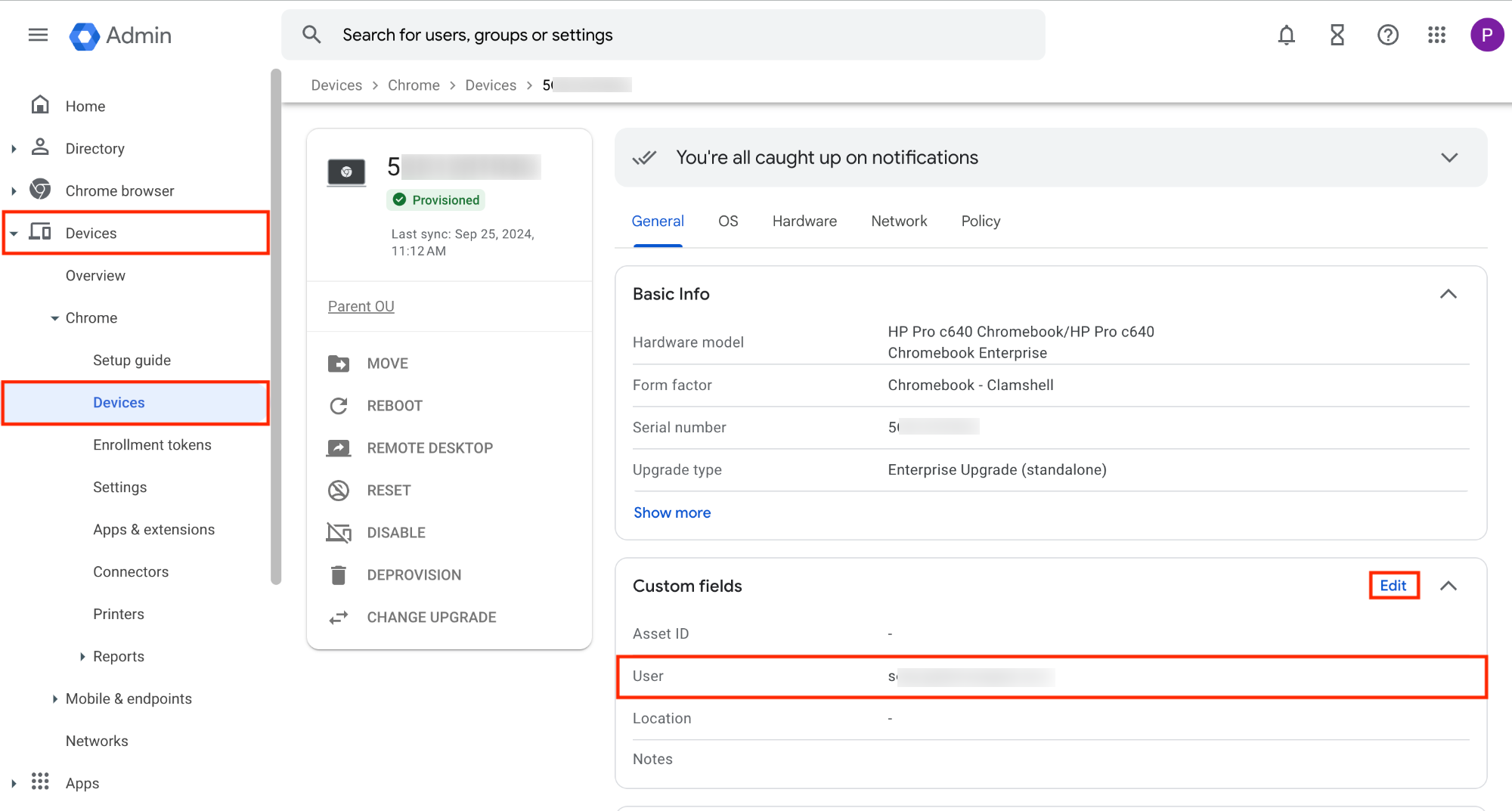
Check the domain of the user assigned to the ChromeOS device.
- Log in to the Google Admin Console.
- Navigate to Devices > Chrome > Devices to view all the devices added to your organization.
- Click on the required device for a detailed overview.
Once the user’s domain is confirmed, you have two options to resolve the issue:
- Change the user associated with the device:
- From the device overview page, Click Edit under General > Custom fields.
- Modify the User field by selecting a user whose domain is synced with the Hexnode UEM console.
- Sync the respective domain of the current user with the Hexnode UEM console:
- Login to the Hexnode UEM console.
- Navigate to Admin > Google Workspace > Actions > Modify.
- Select the required domain from the list of domains. If it’s not listed, click Refresh domains.
- Click Save.
4. While generating token from Google Admin Console, Control Panel Error #1000 appears.
Solution
Following are the two primary solutions:
- Try clearing browser cache.
- Run the website in incognito mode.
If the above solutions don’t work, try with the following secondary solution:
- Login to Google Admin Console.
- From the main menu, navigate to Apps > Additional Google Services.
- Click on Add Services.
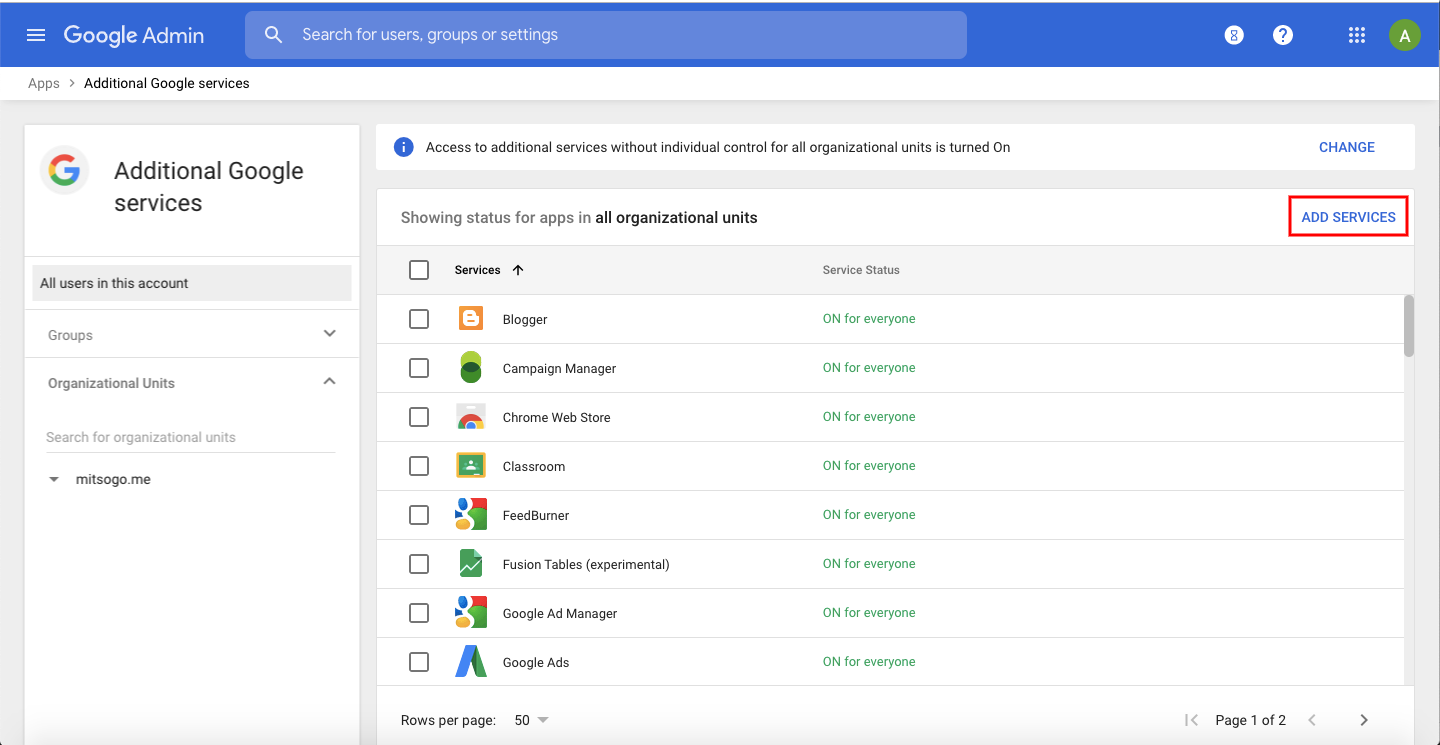
- Click on Add it now under the Android Management services package.
- Once the package is added, you’ll be redirected to Security > Manage EMM provider for Android > Generate Token.
- Token will now be generated successfully.
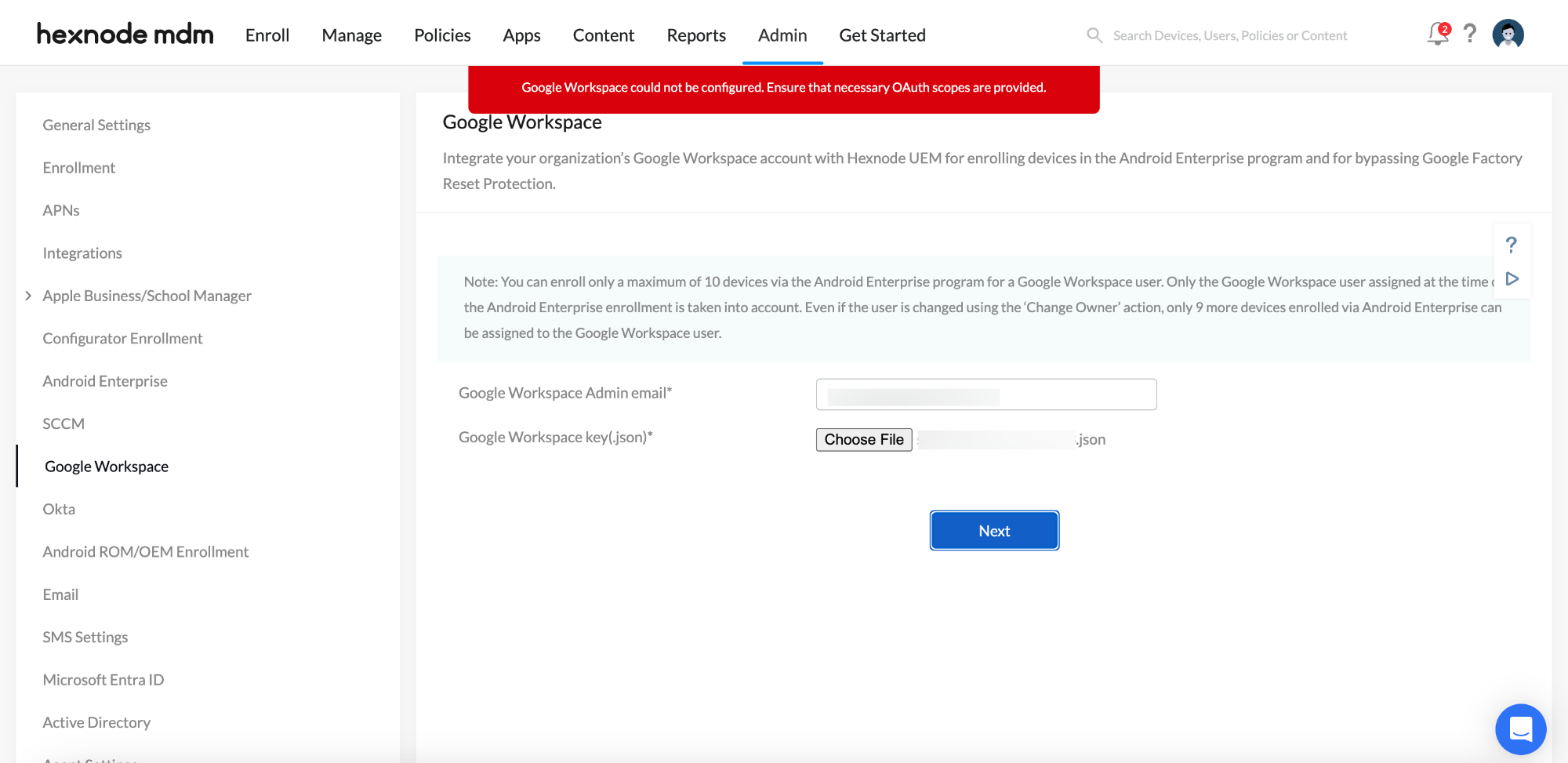
5. After configuring Google Workspace on the Hexnode portal, “Google Workspace could not be configured, ensure that necessary OAuth scopes are provided” error message is shown.
Possible Causes
This could happen if:
- Any of the OAuth scopes are missing while configuring Google Workspace.
- Admin SDK is not enabled.
Solution
Ensure the necessary scopes are added correctly under the SHOW DOMIN-WIDE DELEGATION dropdown menu in your Google Admin account.
- https://www.googleapis.com/auth/admin.directory.user
- https://www.googleapis.com/auth/admin.directory.group
- https://www.googleapis.com/auth/admin.directory.domain
If the issue still persists even after adding the correct OAuth scopes, check if the Admin SDK is enabled for the corresponding account. You can enable the Admin SDK by following the steps below:
- Sign in to your Google Admin Account.
- Head over to Security > API reference.
- Check the Enable API access option.
- Press Save.
6. “Your sign-in settings don’t meet your organization’s 2-Step Verification policy. Contact your admin for more info.” error message during DEP enrollment.
Possible Causes
- 2-Step Verification is enforced on users from the Google Admin console but is not set up in the user account. As a result, such users will be locked out of their accounts when their active sessions expire.
- 2-Step Verification method is set up as Only security key in the Google Admin console, and consequently, the users have configured a built-in security key for verifying their accounts. During DEP enrollment, if the user tries to authenticate using this built-in security, it can lead to an error. Since the DEP enrollment has a Safari-based web view, built-in security keys compatible only with the Chrome browser cannot be used as a method of 2-factor authentication.
Precautions
- Notify the users and ensure that they have set up 2-step verification in their account before enforcing the same from the Google Admin console. Users can activate the 2-step verification by following the steps below:
- Open Google Account.
- Select Security from the navigation menu.
- Select 2-Step verification under Signing in to Google.
- Click on Get started and follow the on-screen instructions.
- Administrators can review Account reports or check 2-Step Verification Settings to find the users who have set up security keys before enforcing the 2-step verification method.
Solutions
- Administrators can recover user accounts by generating backup codes:
- Log in to the Google Admin console.
- Go to Users and select the user account you intend to recover.
- Navigate to Security > 2-step verification.
- Click on Get Backup Verification Codes and copy one of the verification codes.
- Send this code to the user.
- Users can sign in to their account using a password and this backup code.
- Refer to recovering accounts protected by 2-step verification for additional best practices.
7. After configuring Google Workspace on the portal and syncing the domains, user sync stays in ‘In Progress’ for a long time
Possible Causes
-
The issue occurs when there are a lot of users (domains) in the directory.
Solutions
-
User syncing will be completed in 5-10 mins once sync is initiated.
8. After configuring Google Workspace on the Hexnode portal,” Failed Sync” error is shown.
Possible Causes
-
User and/or group scope was not provided.
Solutions
-
Ensure User and group scopes are added before configuring Google Workspace.
If the scope to sync groups is not provided, it shows “Sync failed” in the table after configuration. This sync failure does not mean users are not synced, but groups could not be synced.