Category filter
Manage login to Macs using cloud identity providers with Hexnode Access
Hexnode Access is a feature that allows users to log in to their macOS devices using cloud IdP (identity provider) credentials. We’ve all experienced the ease of using cloud credentials when asked to sign up/log in to websites or apps instead of creating new credentials for each of them. Similarly, logging into macOS devices is made smoother with Hexnode UEM’s integration with IdPs Microsoft Azure AD and Google Workspace. In addition, IT admins can remotely customize how the login window will look, provide users access to help links, and enable them to connect to a network, all from the login screen itself.
Configure Hexnode Access:
To configure Hexnode Access on macOS devices:
- Login to Hexnode UEM portal.
- Go to Policies, select an existing policy or click on New Policy to create a new one.
- Navigate to macOS > Security > Hexnode Access and click Configure.
Basic settings:
Identity provider – Select an IdP of your preference from the drop-down. Azure AD and Google Workspace are supported by Hexnode Access.
Azure AD
Configure authentication by – Admins can choose to move forward either using the IdP domains already added to the Hexnode UEM portal or by creating a new app registration in the IdP portal. Select the preferred method from the drop-down.
- Azure AD domains added to Hexnode portal – Admins can select the domains listed under Admin > Azure AD in the Hexnode UEM portal to configure the authentication.
- Domains – Select one or more domains from the drop-down.
- Allow access for all users – Mark the checkbox if all the user groups in the above-selected domains should be given access to the device.
- Allow access only for – If all the user groups in the selected domains shouldn’t be given access to the device, specify the ones that should be given access.
- Creating a new app registration in Azure Portal – A new app registration has to be created for the Hexnode Access app in the Microsoft Azure portal.
How to register Hexnode Access with Azure AD?
Create a new app registration:
- Login to the Microsoft Azure portal.
- Click on the Show portal menu icon at the left top corner of the page and navigate to Microsoft Entra ID > Manage > App registrations > New registration.
- Enter Hexnode Access in the Name field.
- Under the Supported account types field, select Accounts in this organizational directory only (company name only – Single tenant).
- Under the Redirect URI field, select Web from the Select a platform drop down and enter a valid URI in the adjacent field. The URI will be of the format https://portalname.hexnodemdm.com/azure_devicelogin_callback . Replace
portalnamewith the name of the corresponding Hexnode UEM portal’s name. - Click Register.
Once you have registered the app in the Microsoft Azure portal, navigate back to the Hexnode UEM portal to further configure the authentication settings.
Client ID – Enter the Application/Client ID of the registered app from the Azure AD portal. It is used to authenticate the user.
Tenant ID – Enter the Directory/Tenant ID of your Azure AD portal.
Client secret – Enter the client secret of the registered app, which is known only by the app and your IdP.
Google Workspace
Configure authentication by – Select a configuration method to move forward with from the drop-down.
- Google Workspace domains added to Hexnode portal – Admins can choose domains listed under Admin > G Suite in the Hexnode UEM portal to configure the authentication.
- Domains – Select one or more domains from the drop-down.
- Allow access for all users – Mark the checkbox if all the user groups in the above-selected domains should be given access to the device.
- Allow access only for – If all the user groups in the selected domains aren’t given access, specify the ones that should be given access to the device.
- Creating OAuth credentials in Google Cloud – OAuth credentials has to be created for the Hexnode Access app in Google Cloud.
How to create OAuth credentials for Hexnode Access?
- Login to Google Cloud.
- Click on the Navigation menu icon at the left top corner of the page and navigate to APIs and Services > Credentials.
- Click Create Credentials and select OAuth Client ID.
- Select Web Application from the Application type drop-down.
- Enter Hexnode Access in the Name field.
- Click Add URI under Authorized Redirect URIs and enter a valid URI. The URI will be of the format https://portalname.hexnodemdm.com/gsuite_devicelogin_callback . Replace
portalnamewith the corresponding Hexnode UEM portal’s name. - Click Create.
Once you have registered the app and generated OAuth credentials in Google Cloud, navigate back to the Hexnode UEM portal to further configure the authentication settings.
Client ID – Enter the Client ID provided once the credentials are created. It is used to authenticate the user.
Client secret – Enter the Client secret provided once the credentials are created. This value is confidential and is known only by the app and the IdP.
Account settings:
When choosing domains added to Hexnode portal:
Set user type of newly created user to Admin – Select the checkbox to set the user types of the newly created users as admin users.
Set admin user type only for – Incase all users need not be given admin privileges, specify the users that should be created as admin users.
When creating app registration with IdP:
Set user type of newly created user to Admin – Mark the checkbox to set the newly added users as admin users.
Ignore app roles – Mark the checkbox if the app roles assigned in the IdP portal have to be ignored.
Login settings:
Limit offline access – Mark the checkbox if the users should be required to re-authenticate themselves online using their cloud IdP credentials after a specific period of time.
Require authentication every – If the Limit offline access checkbox is marked, select the frequency for re-authentication from the drop-down:
- Every login
- Every 15 days
- Every 30 days
- Every 45 days
- Every 60 days
- Every 90 days
- Every 120 days
- Every 180 days
Set login page background – Upload an image to set as the login page background.
Blur background image – Adjust the slider to blur the background image.
Login page logo – Upload an image to set as the login page logo.
Click the Preview login screen button to view how the login window would look when the above-configured settings are applied.
Advanced settings:
Allow access to network settings – Mark the checkbox to allow users to connect to a network from the login window. If enabled, click Network Settings on the login page and select a network to connect to.
Help URL – Add a link that may be resourceful to the users when logging into the device or during enrollment and onboarding.
Backup help file – Upload a file that the users can access in case they cannot connect to a network and are unable to open the help URL.
Login scripts
You can choose a script that should be executed on logging into the device. The supported file formats include Perl (.pl), Bash (.sh), Shell (.sh), C Shell (.csh), Zsh (.zsh), Korn Shell (.ksh), Hypertext Preprocessor (.php), Ruby (.rb), and Python (.py).
Choose script file source – The script can be either uploaded directly from the device or selected from the Hexnode repository if the file is already added to My Files under the Content tab in the Hexnode UEM portal.
File name – On uploading files, the file name field will be auto-populated. If Hexnode repository is chosen as the file source, select a file from the File name drop-down.
Binary path – Binary path will be auto-populated depending on the type of the selected file.
Arguments – If necessary, specify the arguments that would be required in the script.
Please go through our detailed document on how to execute custom scripts on macOS devices for better insight.
Associate policies with macOS devices
If the policy has not been saved:
- Navigate to Policy Targets.
- Click on Devices/ Device Groups/ Users/ User Groups/ Domains.
- Choose the targets and click OK and then Save.
If you have the policy saved already:
- Go to the Policies tab and choose the desired policy.
- Click on the Manage drop-down and select Associate Targets.
- Choose the target entities and click Associate. You can choose devices, users, groups, and domains as the policy targets.
What happens at the device end?
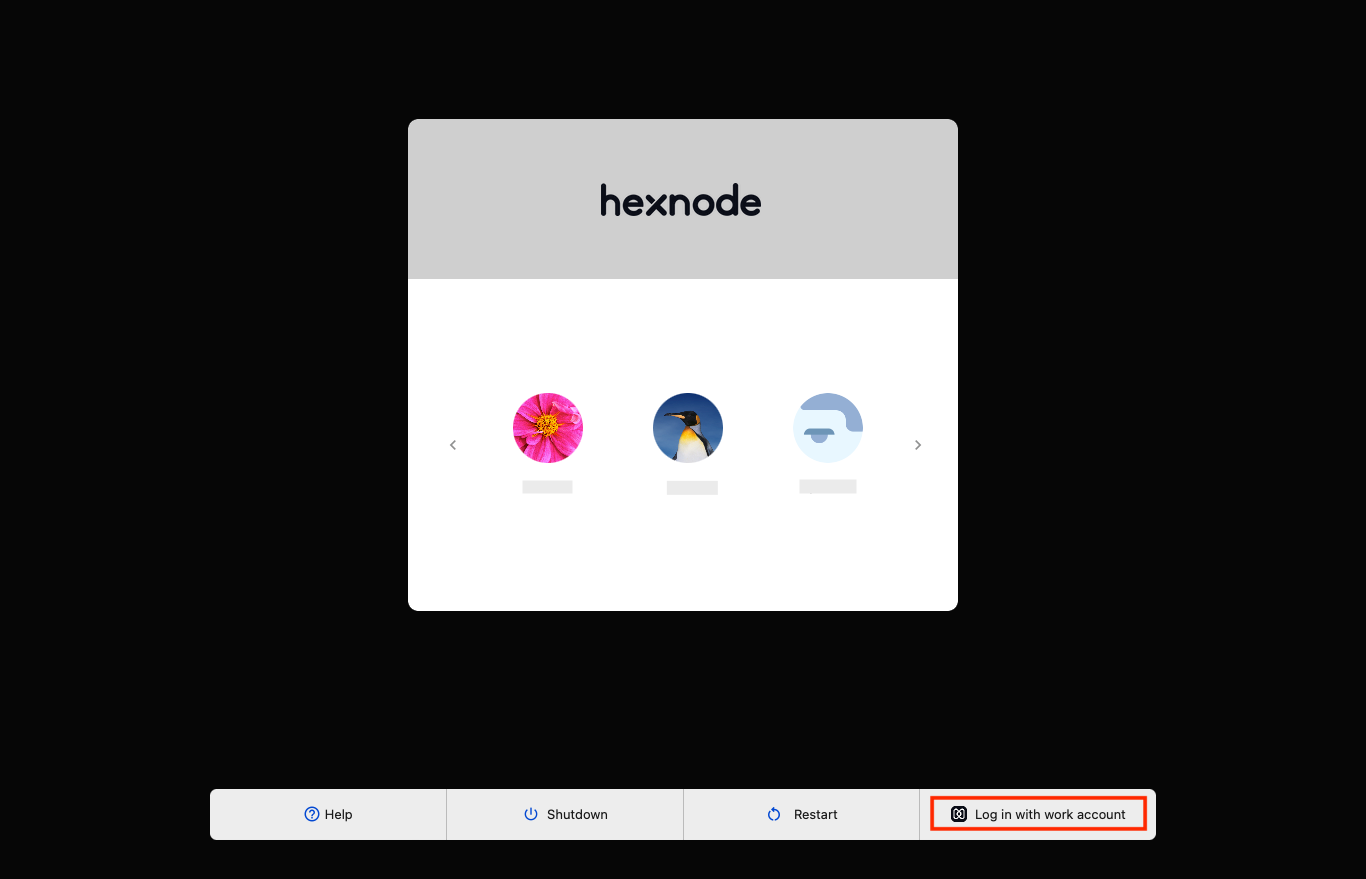
Once the policy is associated with the device, the user can either log in as usual to the local accounts or choose the Log in with work account option.
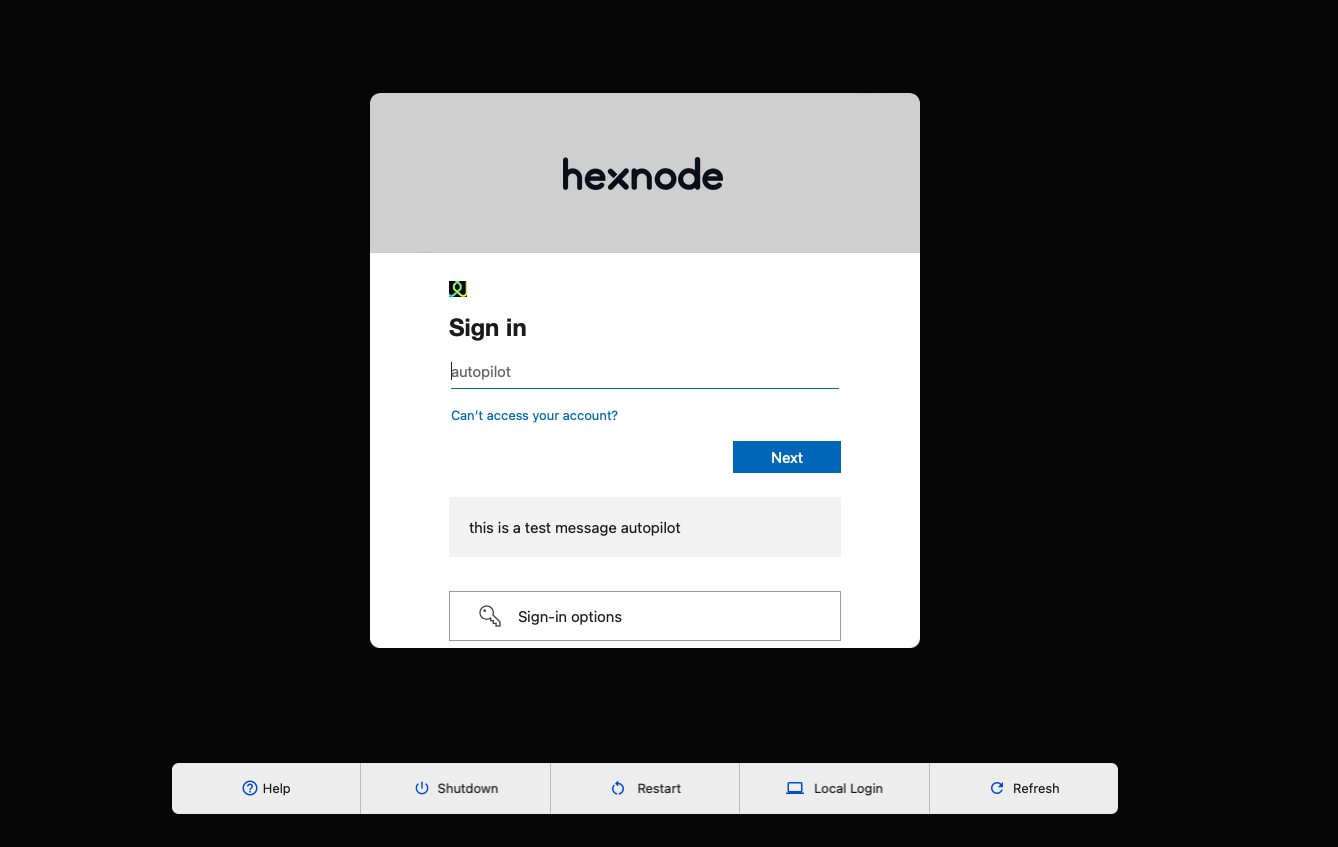
On clicking Log in with work account, the user can log in using their IdP credentials.
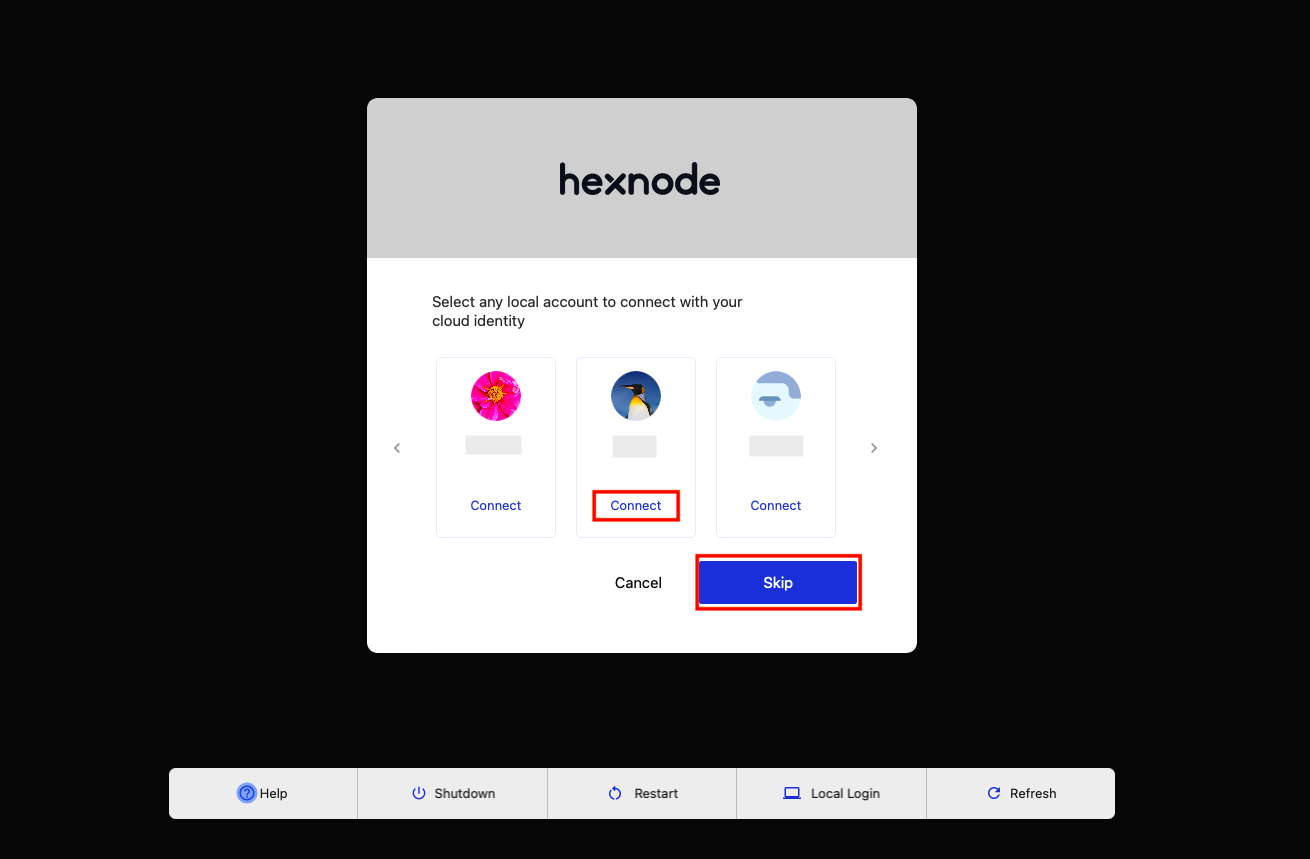
Once authentication is complete, the user will have the option to connect to an already existing local account or to create a new one.
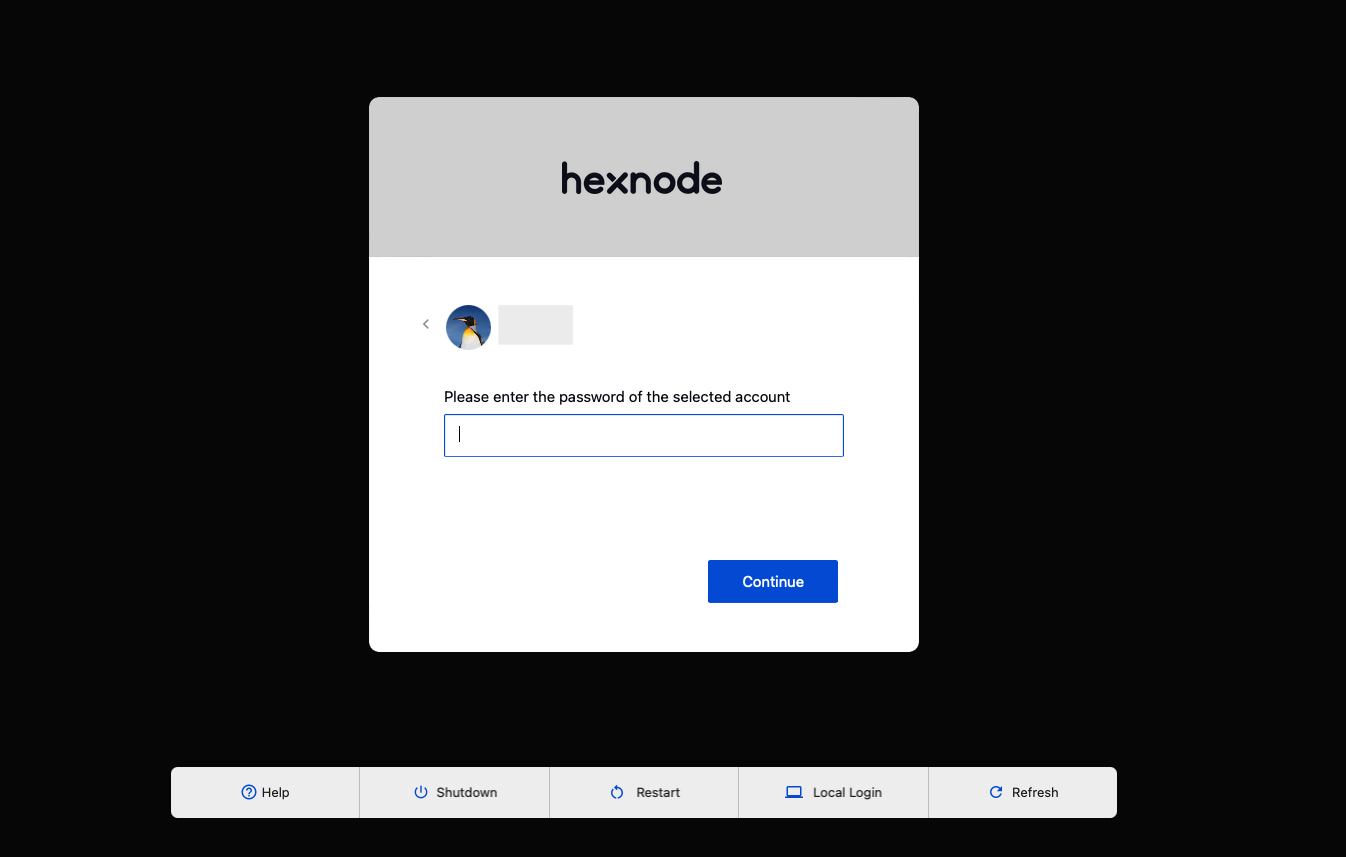
On clicking Connect, the user will be prompted to enter the password of the corresponding local account.
On clicking Skip, the user will be prompted to set a password for the new local account that is being created. Once it is done, the user will be logged into the device.