Category filter
PowerShell script to verify the file hash of a file on Windows devices
Hashing is a cryptographic technique used to generate a unique hash value for a file using a specified hash function. The generated hash value of a file depends on the file’s content (not including name or extension) at the time of generation. Any modification to the file’s content produces a different hash value from its original hash value when it is first generated. The widely-used hash functions include MD5, SHA-1, and SHA-256, providing hash values of different lengths and different cryptographic properties. With the help of custom scripts, IT admins can verify the file hash of a file by comparing its original hash value with the one obtained after executing the script. IT admins can use custom scripts to verify the file hash of a file on Windows devices with the help of Hexnode’s Execute Custom Script action.
PowerShell scripts to get the hash of a file
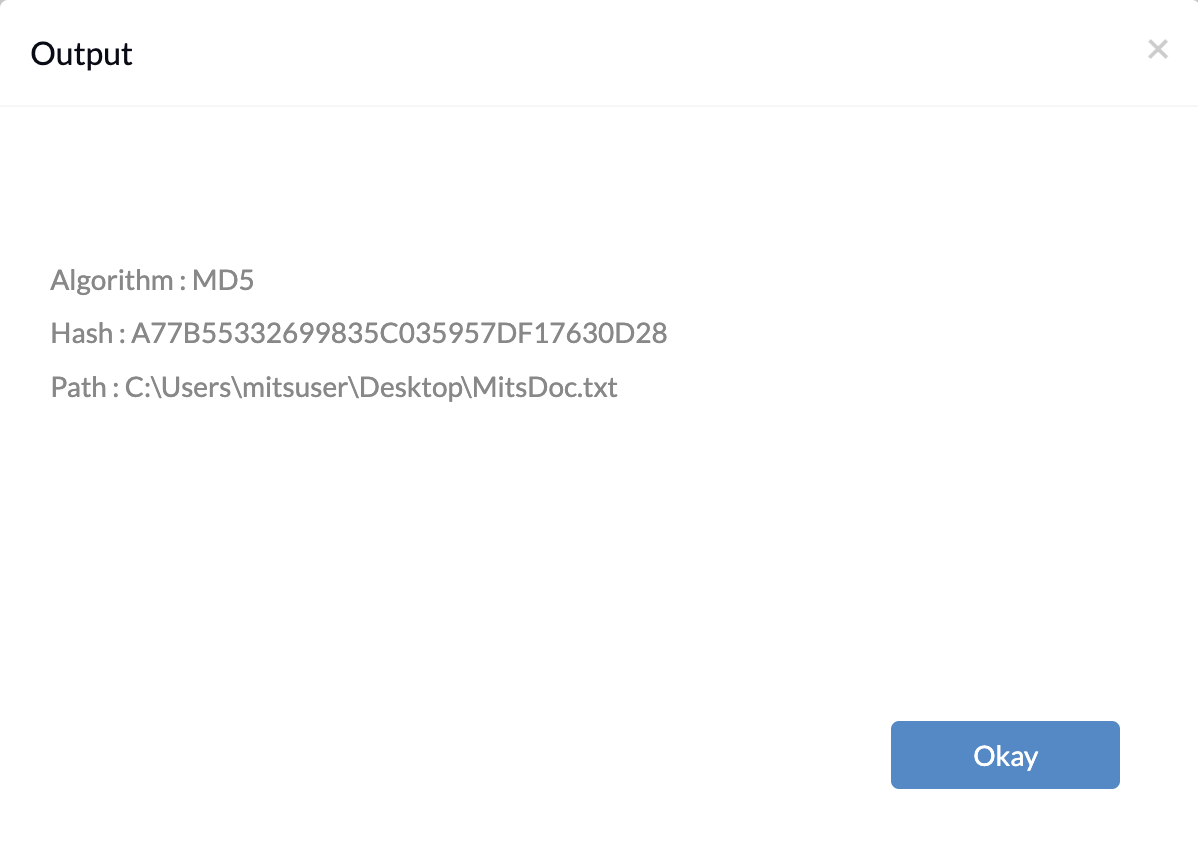
Administrators should generate and store the original hash value of the file before executing the scripts for verifying the hash of a file. This ensures that the comparison accurately detects any tampering. IT admins can use these PowerShell scripts to generate hash values for files on Windows devices. Specify the file path and choose a hash function (MD5, SHA1, or SHA256).
|
1 |
Get-FileHash "C:\Path\to\the\file" -Algorithm Function | Format-List |
PowerShell script to verify the file hash
For MD5, SHA1, and SHA256 methods, given PowerShell scripts can be used on Windows devices to verify file authenticity using file hash. These scripts require administrators to input the file path and the original hash value of the file for each method.
For MD5 method
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
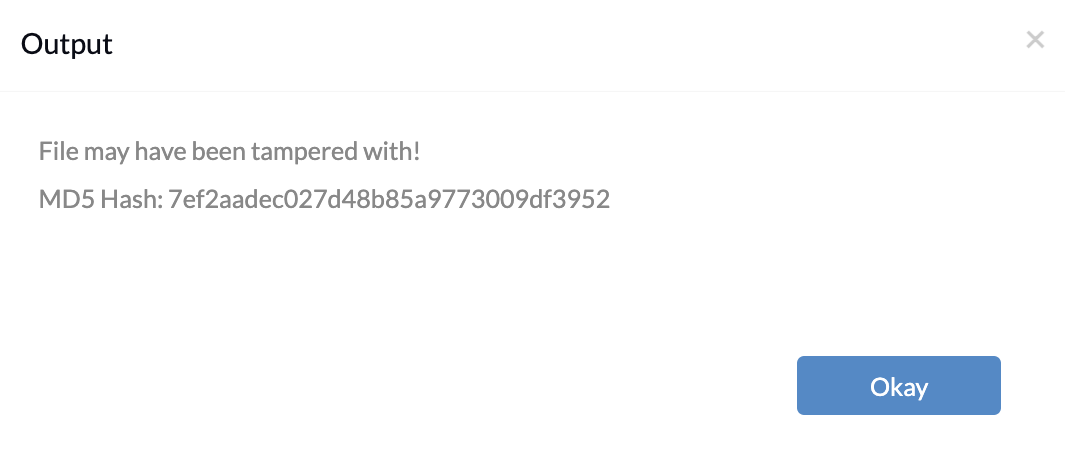
$filePath = "C:\Path\to\the\file" $expectedMD5 = "<Enterthehashvalue>" function Get-MD5Hash($file) { $md5 = [System.Security.Cryptography.MD5]::Create() $stream = [System.IO.File]::OpenRead($file) $hash = [BitConverter]::ToString($md5.ComputeHash($stream)).Replace("-", "").ToLower() $stream.Close() return $hash } $md5Hash = Get-MD5Hash $filePath if ($md5Hash -eq $expectedMD5) { Write-Host "File is authentic." } else { Write-Host "File may have been tampered with!" Write-Host "MD5 Hash: $md5Hash" } |
function Get-MD5Hash($file) {….}: This function calculates the MD5 hash of a given file. It opens the file, computes the MD5 hash, and returns it as a formatted string.
$md5Hash = Get-MD5Hash $filePath: This line calls the ‘Get-MD5Hash’ function with file path parameter stored in ‘$filepath’ and stores the resulting MD5 hash value in the variable ‘$MD5Hash’.
if ($md5Hash -eq $expectedMD5) {…}else{…}: This conditional statement verifies if the computed MD5 hash value of the file matches the expected hash value stored in the variable ‘$expectedMD5’. The output will show as ‘File is authentic’ if both the calculated and expected hash values match. The output will show ‘File may have been tampered with!’ along with the new MD5 hash value if the computed hash value does not match the expected hash value.
For SHA1 method
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
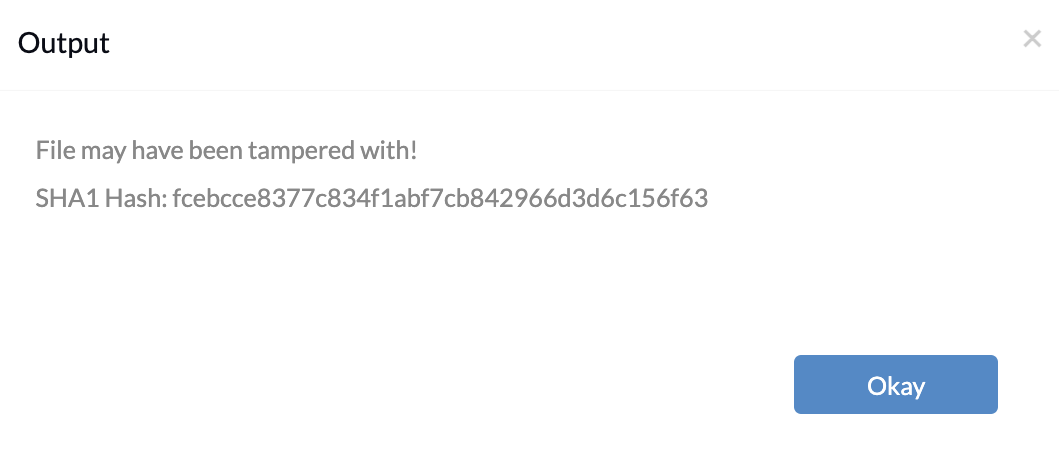
$filePath = "C:\Path\to\the\file " $expectedSHA1 = "<Enterthehashvalue>" function Get-SHA1Hash($file) { $sha1 = [System.Security.Cryptography.SHA1]::Create() $stream = [System.IO.File]::OpenRead($file) $hash = [BitConverter]::ToString($sha1.ComputeHash($stream)).Replace("-", "").ToLower() $stream.Close() return $hash } $sha1Hash = Get-SHA1Hash $filePath if ($sha1Hash -eq $expectedSHA1) { Write-Host "File is authentic." } else { Write-Host "File may have been tampered with!" Write-Host "SHA1 Hash: $sha1Hash" } |
For SHA256 method
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 |
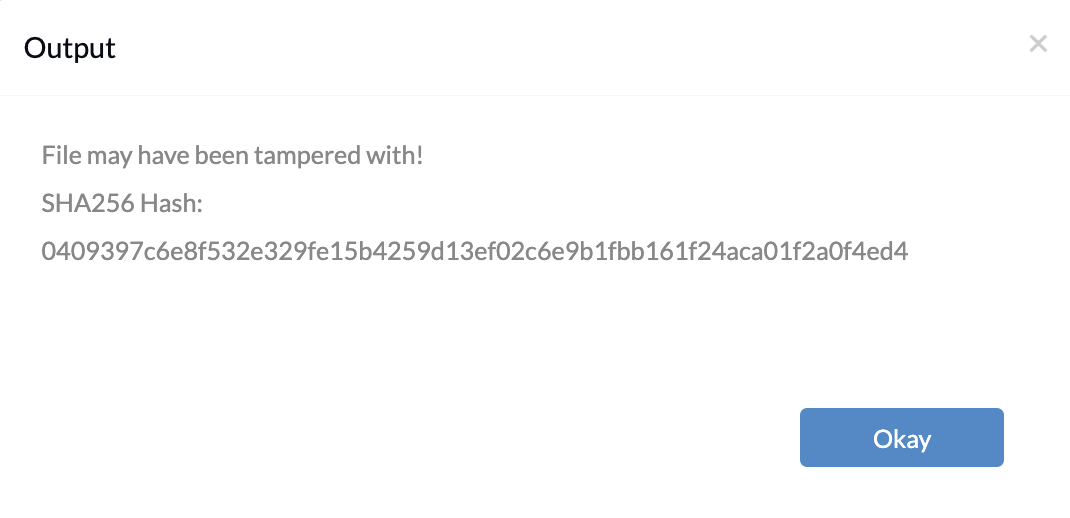
$filePath = "C:\Path\to\the\file" $expectedSHA256 = "<Enterthehashvalue> " function Get-SHA256Hash($file) { $sha256 = [System.Security.Cryptography.SHA256]::Create() $stream = [System.IO.File]::OpenRead($file) $hash = [BitConverter]::ToString($sha256.ComputeHash($stream)).Replace("-", "").ToLower() $stream.Close() return $hash } $sha256Hash = Get-SHA256Hash $filePath if ($sha256Hash -eq $expectedSHA256) { Write-Host "File is authentic." } else { Write-Host "File may have been tampered with!" Write-Host "SHA256 Hash: $sha256Hash" } |
If the hash value matches the expected value, the file is considered authentic as shown. Otherwise, it suggests potential tampering, displaying the computed hash value for comparison.