Category filter
Script to enable BitLocker encryption on Windows
BitLocker prevents unauthorized access to data on devices by encrypting a specified volume. BitLocker encryption renders that data inaccessible on a device unless decrypted using the relevant authenticating parameters. Hence, even if the device is lost or stolen, decommissioned or recycled, the data remains safe. With Hexnode UEM, deploy commands using Execute Custom Script action to set up and manage BitLocker for OS and non-OS drives on Windows devices.
PowerShell scripts to provision TPM
BitLocker uses three keys to encrypt a hard drive.
- A key protector – Protects the volume key of the volume encrypted using BitLocker.
- Volume master key – Encrypted by one or more key protectors. It is stored on an encrypted drive.
- A full volume encryption key – Encrypted by the volume master key and stored on an encrypted drive. It is used to encrypt data.
| Key | Encrypted by | Encrypts | Stored |
|---|---|---|---|
| Key protector | Volume Master Key | TPM or other | |
| Volume Master key (VMK) | Key protector | Full volume encryption key | Encrypted drive |
| Full volume encryption key (FVEK) | Volume Master key | Data | Encrypted drive |
BitLocker requests the key protector as the user tries to access a drive encrypted using BitLocker. The user can, for example, enter a PIN or give a USB disc containing the key. BitLocker uses this key to read data from the drive. You can use key protectors for both OS and non-OS drives. For a key protector, you can use one of the following combinations of methods:
- TPM
- TPM and PIN
- TPM, PIN and startup key
- TPM and startup key
- Startup key
- Password
- Recovery key
- Recovery password
- AD DS
Before using TPM as a key protector
The TPM chip is used as a hardware key protector to unlock the encrypted OS drive alone or in combination with a pin, password or USB key. The TPM must be enabled before it is used for encryption, so before using TPM as a key protector, you must check the status of the TPM chip prior to enabling BitLocker. BitLocker requires TPM version 1.2 or higher for encryption.
First, check the version and then the status of the TPM chip remotely using Execute Custom Script action. Run this command to check your TPM version.
|
1 |
wmic /namespace:\\root\CIMV2\Security\MicrosoftTpm path Win32_Tpm get /value |
Next, you can view the output of the commands by navigating to the Action History tab and clicking on the Show Output option for the corresponding command run.
The output of the command will be as follows:
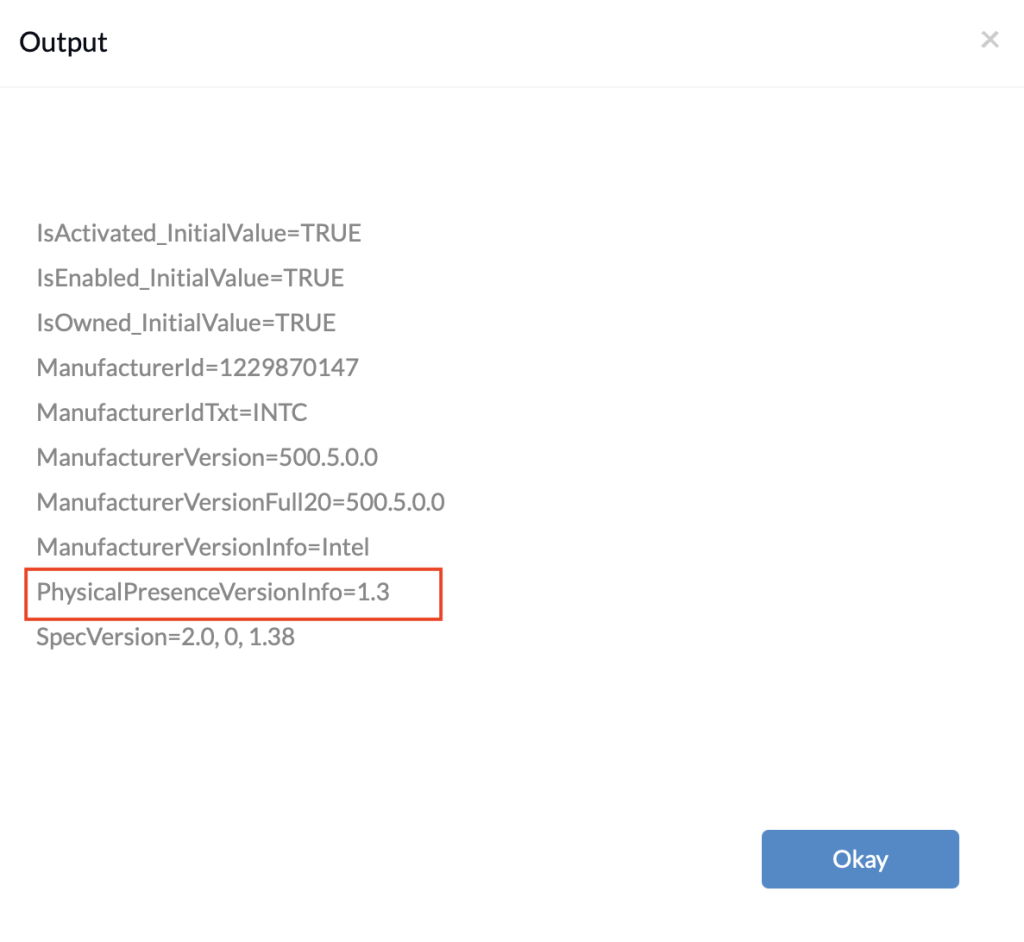
If the TPM version is 1.2 or higher, you can enable the TPM chip before starting encryption. But first, see if the chip is already enabled by checking your TPM status using the following command:
|
1 |
Get-tpm |
The output of the command will be as follows:
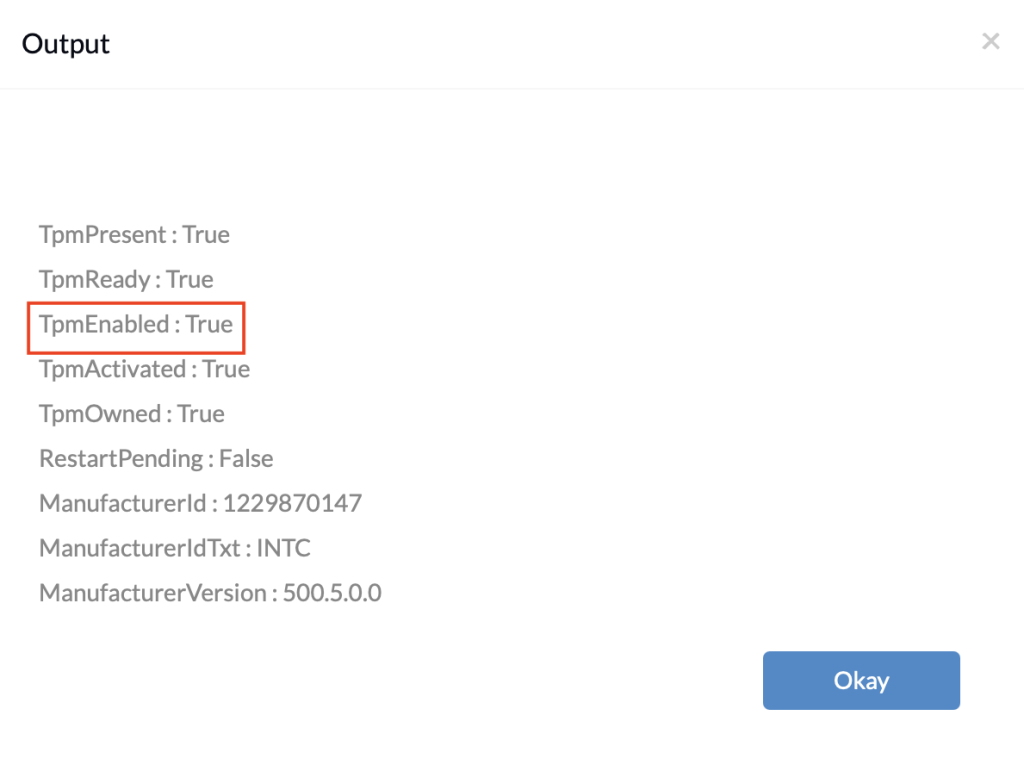
If TPMEnabled is not True, you can use the following script to enable it:
|
1 |
Initialize-tpm |
When this command is executed, it returns the following statuses and their respective values: TpmReady, RestartRequired, ShutdownRequired, ClearRequired and PhysicalPresenceRequired.
- Restart your device remotely using the custom script if RestartRequired returns status as True.
- Shutdown your device if ShutdownRequired is returned as True.
- If ClearRequired is True, you must import an owner authorization value or remove the owner authorization value.
- For PhysicalPresenceRequired equals True, a user must be at the computer during restart to continue the provisioning process.
TPM will be enabled once the provisioning is completed.
PowerShell scripts to set up BitLocker Encryption
Check BitLocker status
Use the following command to fetch information about all the drives in the devices and identify if they are already BitLocker-protected.
|
1 |
manage-bde -status |
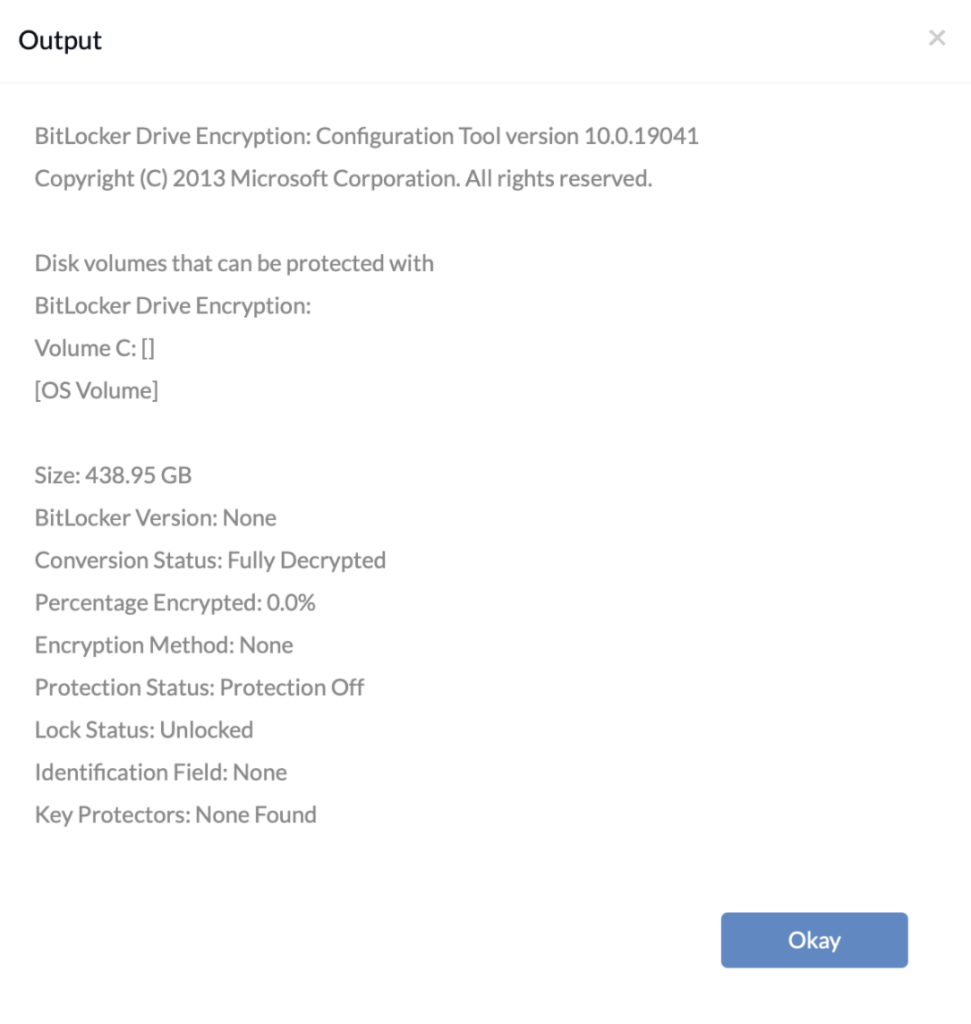
To initiate BitLocker encryption
Manage-bde is a command-line tool that offers additional options not displayed in the BitLocker control panel, like specifying unlock mechanisms, updating recovery methods, and unlocking BitLocker-protected data drives.
Users can use manage-bde command to turn on or off BitLocker and other related functions. Here is the syntax:
|
1 2 |
manage-bde [-status] [–on] [–off] [–pause] [–resume] [–lock] [–unlock] [–autounlock] [–protectors] [–tpm] [–setidentifier] [-forcerecovery] [–changepassword] [–changepin] [–changekey] [-keypackage] [–upgrade] [-wipefreespace] [{-?|/?}] [{-help|-h}] |
If you wish to add TPM as a key protector, you can run the previous commands to check the status of the TPM chip and then add it as a key protector. Then, encrypt your disk drives using the commands:
|
1 2 3 4 5 6 7 |
manage-bde -protectors -delete -type password C: manage-bde -protectors -add -tpm C: manage-bde -on C: -recoverykey D:\ -usedspaceonly -encryptionmethod aes128 |
-protectors-delete: Deletes existing protection methods, if any, used by BitLocker.
-protectors-add: Adds key protection methods. Here it is a TPM protector.
manage-bde-on encrypts the drive and turns on BitLocker. It has various parameters:
-recoverykey: Adds external key protector for recovery. In the example, the recovery key generated is saved in D: drive in .txt or .bek extension files.
-usedspaceonly: Encrypts only used space of the drive to avoid encrypting the entire drive to save time.
-encryptionmethod: Configures encryption algorithm and key size. Valid encryption methods include aes128, aes256, xts_aes128 and xts_aes256.
Finally, reboot the device and view the BitLocker status using the following command:
manage-bde -status.
It may take several hours to encrypt the drive completely. Once encryption is completed, run the following command to see the list of all key protectors for the given drive.
|
1 |
manage-bde -protectors -get C: |



