Category filter
Configure device restrictions for visionOS
Hexnode enables admins to enforce tailored UEM restrictions on visionOS devices, ensuring secure and efficient usage. Admins can determine how users interact with their devices, ensuring a controlled and optimized environment. This article will guide you through some key restrictions to manage visionOS devices effectively.
With Hexnode’s UEM, admins have the flexibility to enforce a range of security restrictions to ensure secure device usage. These restrictions allow admins to control various aspects of device behavior, such as network access, app permissions, and data security. By implementing these restrictions, organizations can reduce potential vulnerabilities, ensuring a safer and more controlled digital environment.
Configure device restrictions for visionOS
To configure Restrictions in your visionOS devices:
- Login to your Hexnode portal and navigate to Policies.
- Click on New Policy to create a new one by providing a policy name and description (optional) or click on any existing policy to edit it.
- Navigate to visionOS > Basic/Advanced Restrictions. Click on Configure.
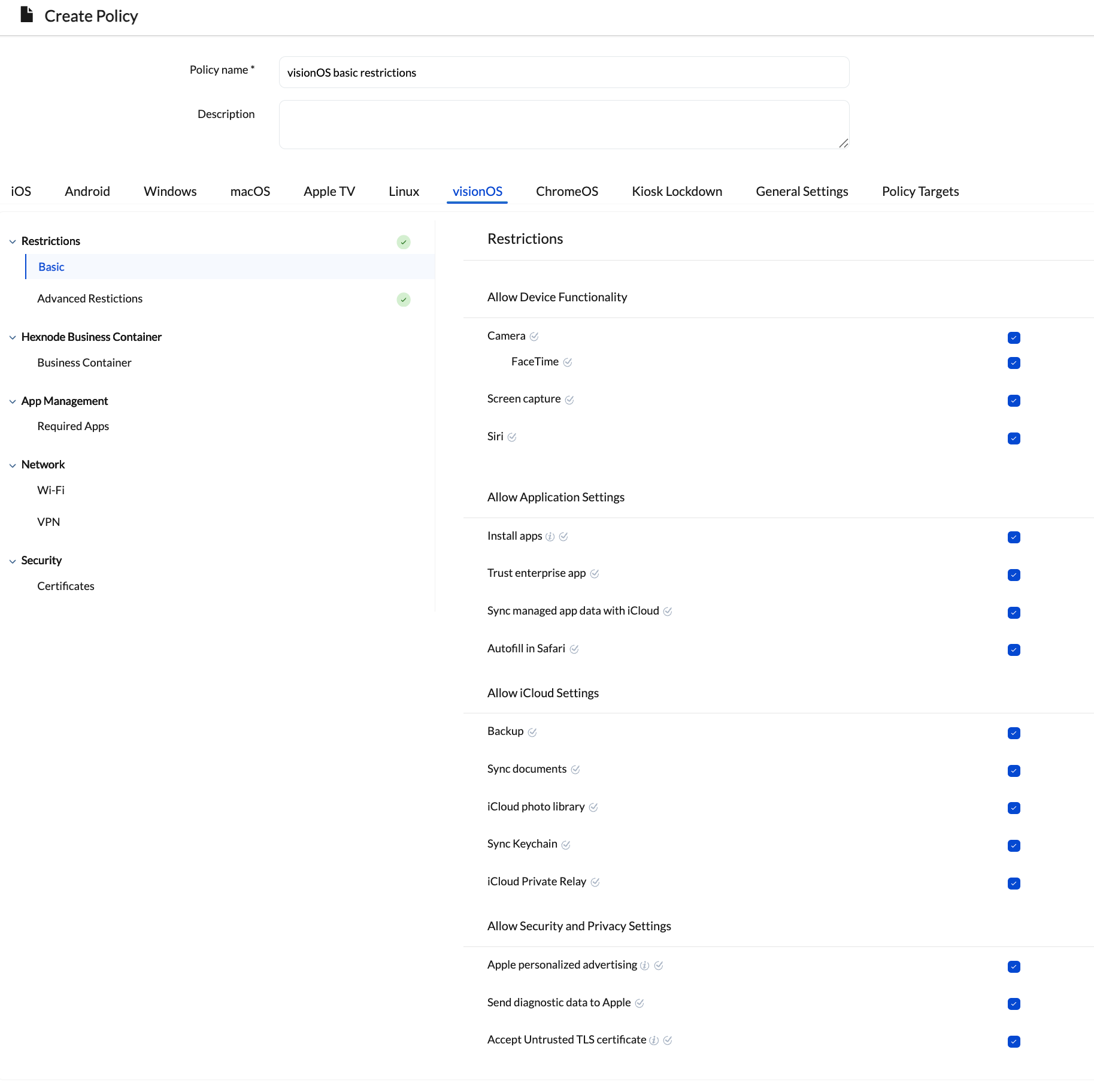
Basic Restrictions
The basic restrictions have been grouped into the following sections:
| Restriction | Description | Supported OS version |
|---|---|---|
| Camera | Allow users to access the device camera. If this setting is turned off, the Camera icon will be hidden, and users won’t be able to take photos or record videos. | visionOS 2.0+ |
| FaceTime | Disabling this setting will prevent users from making or receiving FaceTime audio or video calls. | Supervised visionOS 2.0+ |
| Screen capture | Disabling this setting will restrict users from capturing screenshots or recording the screen. | visionOS 2.0+ |
| Siri | Unchecking this setting will disable Siri functionality for users. | visionOS 2.0+ |
| Restriction | Description | Supported OS version |
|---|---|---|
| Install apps | If left unchecked, the App Store will be disabled and its icon removed from the device home screen, preventing access to App Store apps, marketplace apps, and locally installed apps. | Supervised visionOS 2.0+ |
| Trust enterprise app | Disabling this setting prevents users from trusting new enterprise (in-house) app developers, thereby blocking the launch of those apps. | visionOS 2.0+ |
| Sync managed app data with iCloud | Disabling this setting prevents managed app data from syncing with iCloud. | visionOS 2.0+ |
| Autofill in Safari | If left unchecked, the system disables Safari AutoFill for passwords, contact information, and credit cards, and also blocks the use of Keychain for AutoFill. | Supervised visionOS 2.0+ |
| Restriction | Description | Supported OS version |
|---|---|---|
| Backup | Disabling this setting will turn off iCloud backups for the device. | visionOS 2.0+ |
| Sync documents | Unchecking this setting will disable document and key-value syncing to iCloud. | Supervised visionOS 2.0+ |
| iCloud photo library | Unchecking this setting will disable iCloud Photo Library. The system removes any photos from local storage that aren’t fully downloaded from iCloud Photo Library to the device | visionOS 2.0+ |
| Sync Keychain | Disabling this setting will turn off iCloud Keychain synchronization. | visionOS 2.0+ |
| iCloud Private Relay | Unchecking this setting will disable iCloud Private Relay. | Supervised visionOS 2.0+ |
| Restriction | Description | Supported OS version |
|---|---|---|
| Apple personalized advertising | Disabling this setting will limit Apple’s personalized advertising on your device. | visionOS 2.0+ |
| Send diagnostic data to Apple | Unchecking setting will prevent the device from automatically sending diagnostic reports to Apple. | visionOS 2.0+ |
| Accept Untrusted TLS certificate | If this setting is enabled, devices can accept untrusted certificates through a prompt. | visionOS 1.1+ |
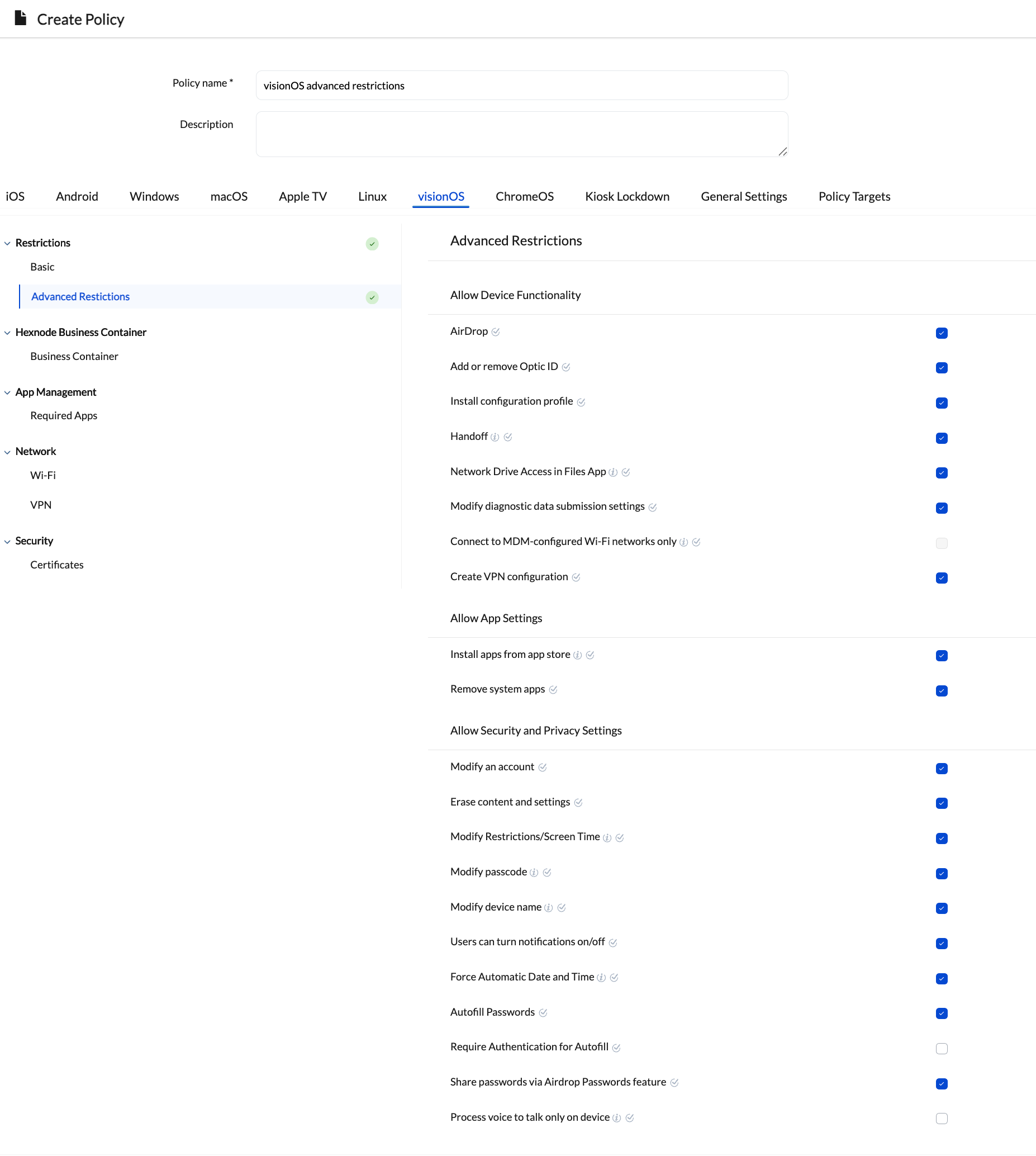
Advanced Restrictions
The advanced restrictions have been grouped into the following sections:
| Restriction | Description | Supported OS version |
|---|---|---|
| AirDrop | Disabling this setting will turn off AirDrop on the devices. | Supervised visionOS 2.0+ |
| Add or remove Optic ID | Disabling this setting will prevent the device from being unlocked using Touch ID or Face ID. | Supervised visionOS 2.0+ |
| Install configuration profile | Disabling this setting will prevent the user from interactively installing configuration profiles and certificates on the device. | Supervised visionOS 2.0+ |
| Handoff | Disabling this setting will turn off activity continuation (starting tasks on one Apple device and continue working on it from another Apple device) across devices. | visionOS 2.0+ |
| Network Drive Access in Files App | Disabling this setting will prevent the system from connecting to network drives in the Files app. | Supervised visionOS 2.0+ |
| Modify diagnostic data submission settings | Disabling this setting prevents changes to the diagnostic submission and app analytics options in the Diagnostics & Usage section of device settings. | Supervised visionOS 2.0+ |
| Connect to MDM-configured Wi-Fi networks only | The system limits the device to connecting only to Wi-Fi networks configured via a configuration profile. Enabling this restriction requires Wi-Fi to be configured within the policy. | Supervised visionOS 2.0+ |
| Create VPN configuration | Enable this setting to restrict VPN configuration creation to managed apps only. | Supervised visionOS 2.0+ |
| Restriction | Description | Supported OS version |
|---|---|---|
| Install apps from app store | Unchecking this option will disable the App Store and remove its icon from the Home Screen. However, users can still install or update apps using iTunes or Apple Configurator. | Supervised visionOS 2.0+ |
| Remove system apps | When this option is unchecked, the system prevents the removal of system apps from the device. | Supervised visionOS 2.0+ |
| Restriction | Description | Supported OS version |
|---|---|---|
| Modify an account | Enabling this setting allows users to modify accounts, including Apple Accounts and internet-based accounts like Mail, Contacts, and Calendar. | Supervised visionOS 2.0+ |
| Erase content and settings | Disabling this setting prevents users from accessing the Erase All Content and Settings option in the Reset UI. | Supervised visionOS 2.0+ |
| Modify Restrictions/Screen Time | Enabling this setting allows users to turn on restrictions or parental controls on the device. | Supervised visionOS 2.0+ |
| Modify passcode | Disabling this setting prevents users from adding, changing, or removing the device passcode. | Supervised visionOS 2.0+ |
| Modify device name | Disabling this setting prevents the user from changing the device name. | Supervised visionOS 2.0+ |
| Users can turn notifications on/off | Disabling this setting prevents the user from modifying the device’s notification settings. | Supervised visionOS 2.0+ |
| Force Automatic Date and Time | Enabling this setting enables the Set Automatically feature in Date & Time and the user can’t disable it. The device’s time zone will be updated only if location services are enabled on the device. | Supervised visionOS 2.0+ |
| Autofill Passwords | Disabling this feature will block the use of password autofill on the device. | Supervised visionOS 2.0+ |
| Require Authentication for Autofill | Enabling this setting prompts the user to authenticate before the system autofill password or credit card information in Safari and apps. | Supervised visionOS 2.0+ |
| Share passwords via Airdrop Passwords feature | Enabling this setting allows the user to share passwords using the AirDrop Passwords feature. | Supervised visionOS 2.0+ |
| Process voice to talk only on device | Enable this setting to block the device’s dictation services from connecting to Siri servers. | visionOS 2.0+ |
Associate the Policies with Device/Groups
You can associate restrictions with devices in bulk through two methods. The first option is directly from the policy configuration page.
This approach is recommended if the policy hasn’t been saved yet.
- Navigate to Policy Targets.
- Click on +Add Devices, search for and select the desired device(s) to apply the policy to, then click OK.
- Click Save to finish associating the policy to the device.
If the policy is already saved,
- Navigate to Policies.
- Search and select the desired policy from the list.
- Click on Manage > Associate Targets.
- Choose the device you wish to associate the policy to.
- Click on Associate for immediate application of the policy to the device.
To associate policies with a device group, select Device Groups from the left pane under Policy Targets, and follow the same steps. You can also associate the policy with users, user groups, or domains from this pane.