Category filter
Set Firmware/Recovery lock password on macOS devices
What is a Firmware or Recovery lock password?
A firmware password protects macOS devices with Intel processors at the hardware level. When enabled, it prevents unauthorized users from starting up the device from any storage device other than the default startup disk, accessing macOS Recovery, or using startup key combinations. This ensures that only authorized users can modify system-level configurations or reinstall macOS.
With Apple silicon (M1, M2, and later), the traditional firmware password has been replaced with Recovery Lock. Recovery Lock performs a similar role by restricting access to macOS Recovery and ensuring only authorized users can erase the device or change security settings.
Both firmware and recovery lock passwords can be configured through a Unified Endpoint Management (UEM) solution like Hexnode. For Apple silicon devices, UEM is the only supported method for setting up the Recovery Lock password, whereas the firmware password can also be set directly on the device.
Why use firmware/recovery lock passwords?
Firmware/recovery lock passwords serve a critical role beyond simply protecting against unauthorized access. In enterprise environments, where macOS devices often store all the confidential data, these passwords prevent attackers from bypassing security mechanisms, booting from external drives, or reinstalling macOS to gain access. They also help devices meet compliance standards which require physical and firmware-level protections for devices handling sensitive data. During device reassignment or decommissioning, firmware and recovery locks ensure that stored information remains inaccessible until the IT team clears it with the correct password. In sectors such as education and government, these locks prevent users from modifying the boot process or installing unapproved software, ensuring devices remain aligned with organizational policies.
Setting Firmware/Recovery lock password via Hexnode
While a firmware password can be set directly on Intel-based macOS devices, managing passwords individually across multiple devices can be inconsistent and time-consuming. Hexnode lets IT admins set or update a common firmware or recovery lock password across multiple devices using the Set Firmware/Recovery Lock Password action. Applying a uniform firmware or recovery lock password across multiple devices simplifies administration, provided administrators rotate it regularly and store it securely. When the action is executed, the password is securely escrowed in the portal under each device’s Security Info section.
Steps to set up Firmware/Recovery lock password
Follow the below steps to configure Firmware/Recovery lock password on macOS devices,
- Login to your Hexnode portal.
- Navigate to Manage > Devices.
- Select a device(s) or you can click on the name of device if you want to set it for a single device.
- Go to Actions > Security > Set Firmware/Recovery Lock Password.
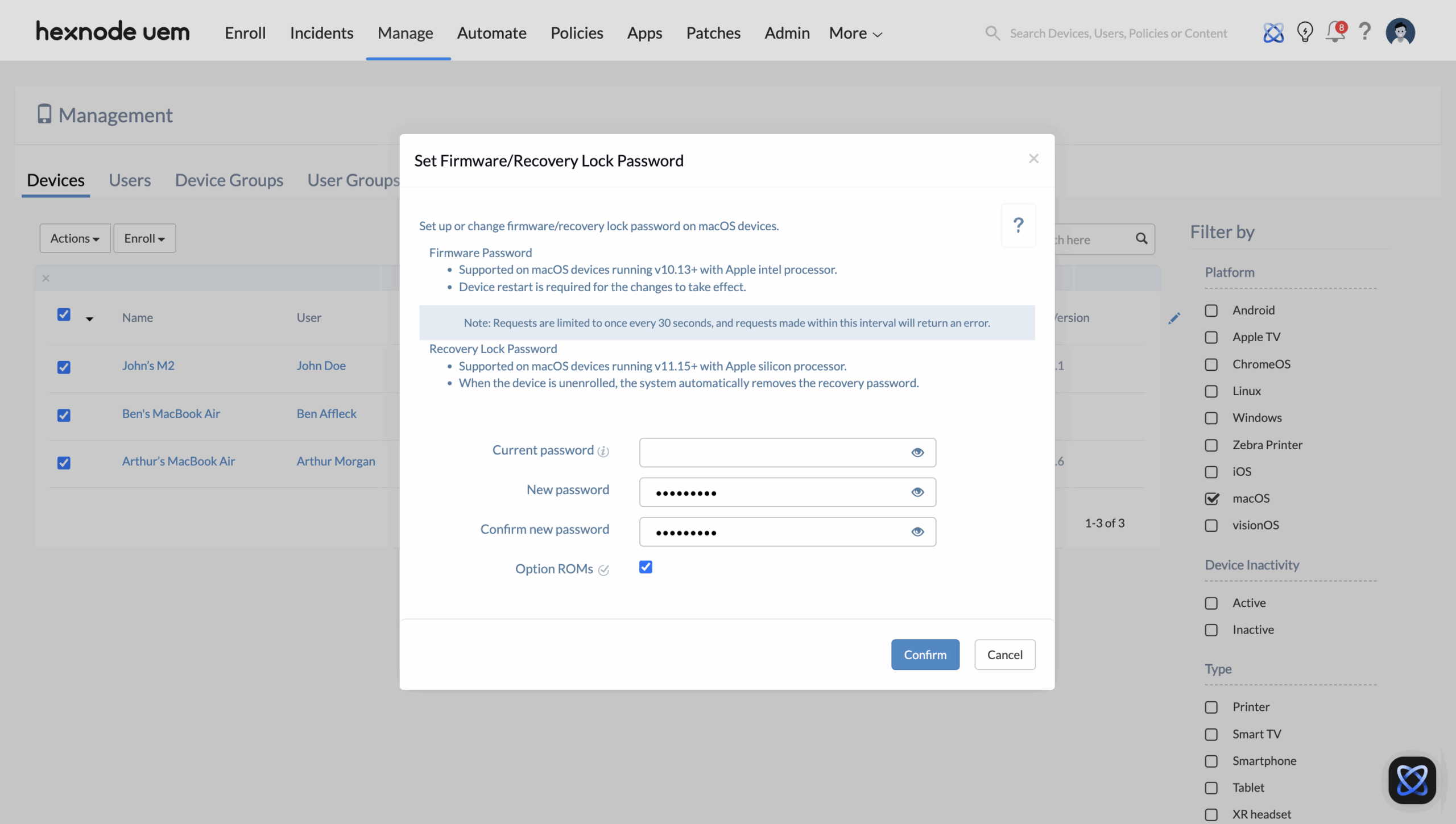
- You can configure the following account set-up options.
- Current password: Enter the existing firmware or recovery lock password if one is already set. Leave this blank if you are configuring the password for the first time.
- New password: Specify the new firmware or recovery lock password. This password will be required when attempting to access recovery mode or boot from external media.
- Confirm new password: Re-enter the new password to confirm accuracy.
- Option ROMs: Lets you decide whether to allow external hardware firmware to run at startup on Intel-based macOS devices (v10.13+). Check to allow external hardware firmware to run at startup or uncheck to block it.
- Click Confirm.
How to view the Firmware/Recovery password?
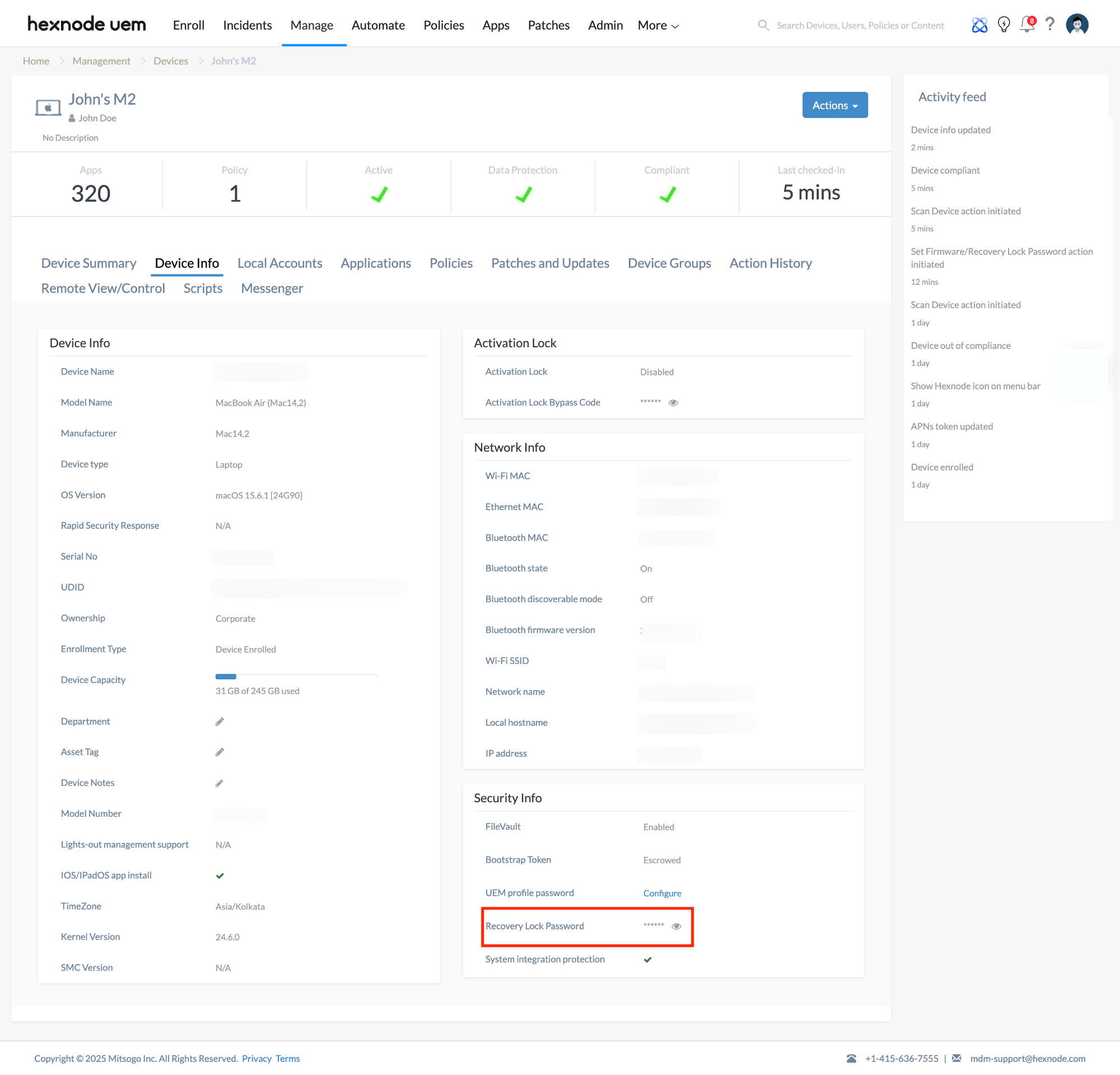
Once the firmware or recovery lock password is set, it is escrowed to the Hexnode portal under the device info of each device. To view the escrowed password:
- Log in to your Hexnode portal.
- Navigate to Manage > Devices.
- Click the device name and go to Device Info > Security Info > Firmware/Recovery password to view the escrowed password.
If the firmware or recovery password is neither set nor changed from the Hexnode portal, the status under Device Info > Security Info > Firmware/Recovery password will display either Yes or No.
What happens at the device end?
After setting up the firmware or recovery lock password, the macOS device enforces authentication during specific startup operations.
On macOS devices running with Apple Intel processor, the firmware password prompt appears when attempting to start the device from a disk other than the default startup disk or when entering recovery mode. For macOS devices running with Apple silicon processor, the recovery lock password prompt appears when the device is booted into recoveryOS.
Frequently Asked Question’s (FAQs)
1. What is the difference between a firmware password and a recovery lock?
A firmware password on Intel processor based devices can be set by the end user or via a UEM. It prevents unauthorized startup from non-default disks and recovery mode. A recovery lock on Apple silicon-based devices can only be configured through a UEM like Hexnode and protects access to recoveryOS.
2. What are Option ROMs, and how does enabling or disabling them affect Intel-based Macs?
Option ROMs are small programs stored in the firmware of external hardware devices, such as graphics cards or network adapters. These programs load during startup to initialize the connected hardware.
On Intel-based macOS devices running version 10.13 or later, enabling Option ROMs allows such external firmware to load at startup, which may be necessary for specific peripherals. Disabling them prevents any external firmware from loading, improving device security by blocking unauthorized boot attempts or potentially malicious firmware.
What if the firmware password on an Intel-based macOS device is changed directly on the device after being set via Hexnode?
Administrators can verify whether the password on the device matches the one set via Hexnode using the remote action Verify Firmware Password.