Category filter
How to force BitLocker decryption on drives?
The Force BitLocker Decryption remote action disables BitLocker protection and initiates the decryption process for OS, fixed, or removable drives on managed Windows devices, rendering data accessible without encryption.
What is BitLocker Decryption?
BitLocker Decryption is the process of removing BitLocker protection from a drive, reverting it from an encrypted state to its original, unprotected state. This removes the requirement for a password or recovery key to access the data.
- Purpose: Essential for device reassignment, repurposing, or decommissioning.
- Benefits: Prevents BitLocker from interfering with operating system reinstallations or hardware changes that might otherwise trigger recovery key prompts.
- Scope: Can be applied to the Operating System (OS) drive, fixed data drives, or removable storage media.
Prerequisites and Constraints
Before initiating the decryption process, ensure the following conditions are met:
| Prerequisite | Description |
|---|---|
| Drive State | The target drive(s) must be in an unlocked state for the action to work. |
| OS Drive Keys | If auto-unlock is enabled, the Clear auto-unlock option must be used to decrypt the OS drive. |
| Device Platform | Supported on managed Windows devices. |
Step-by-Step Guide: How to Force BitLocker Decryption
Administrators can remotely trigger decryption for all drives or specific partitions using the Hexnode UEM console.
- Log in to the Hexnode UEM portal.
- Navigate to the Manage tab and select the target Windows device.
- Click on Actions > Security > Force BitLocker Decryption.
- In the Force BitLocker Decryption dialog box, configure the following settings:
- Decrypt all drives: Select this to decrypt all fixed and removable drives.
- Decrypt fixed drives: Select to target only internal data drives.
- Decrypt removable drives: Select to target external storage (e.g., USB drives).
- Decrypt specific drives: Manually enter drive names (e.g., D:, E:) separated by commas.
- Clear auto-unlock: Required for OS drive decryption if auto-unlock is active. This removes automatic unlocking keys from the OS drive to allow the decryption process to proceed.
- Click Proceed.
Monitoring the Decryption Process
Once the action is executed, BitLocker is immediately disabled, and key protectors (passwords/recovery keys) are removed.
Viewing Status in Hexnode UEM
- Go to the Device Summary page of the specific device.
- Locate the Hardware Info section.
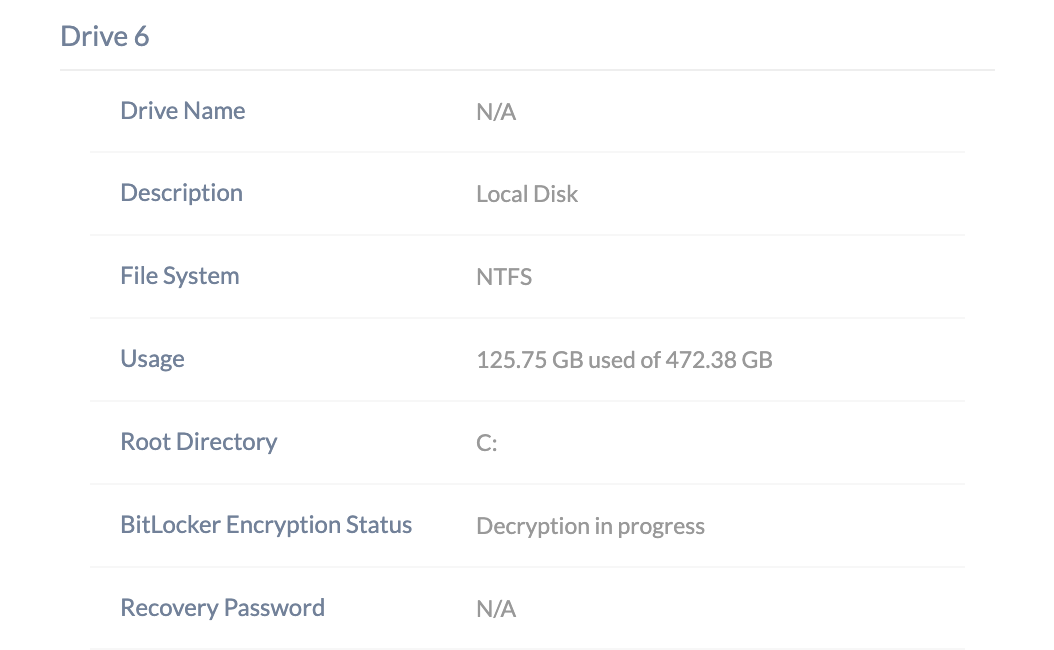
- Check BitLocker Encryption Status:
- Decrypting: The process is currently in progress.
- Not Encrypted: The decryption process is complete.
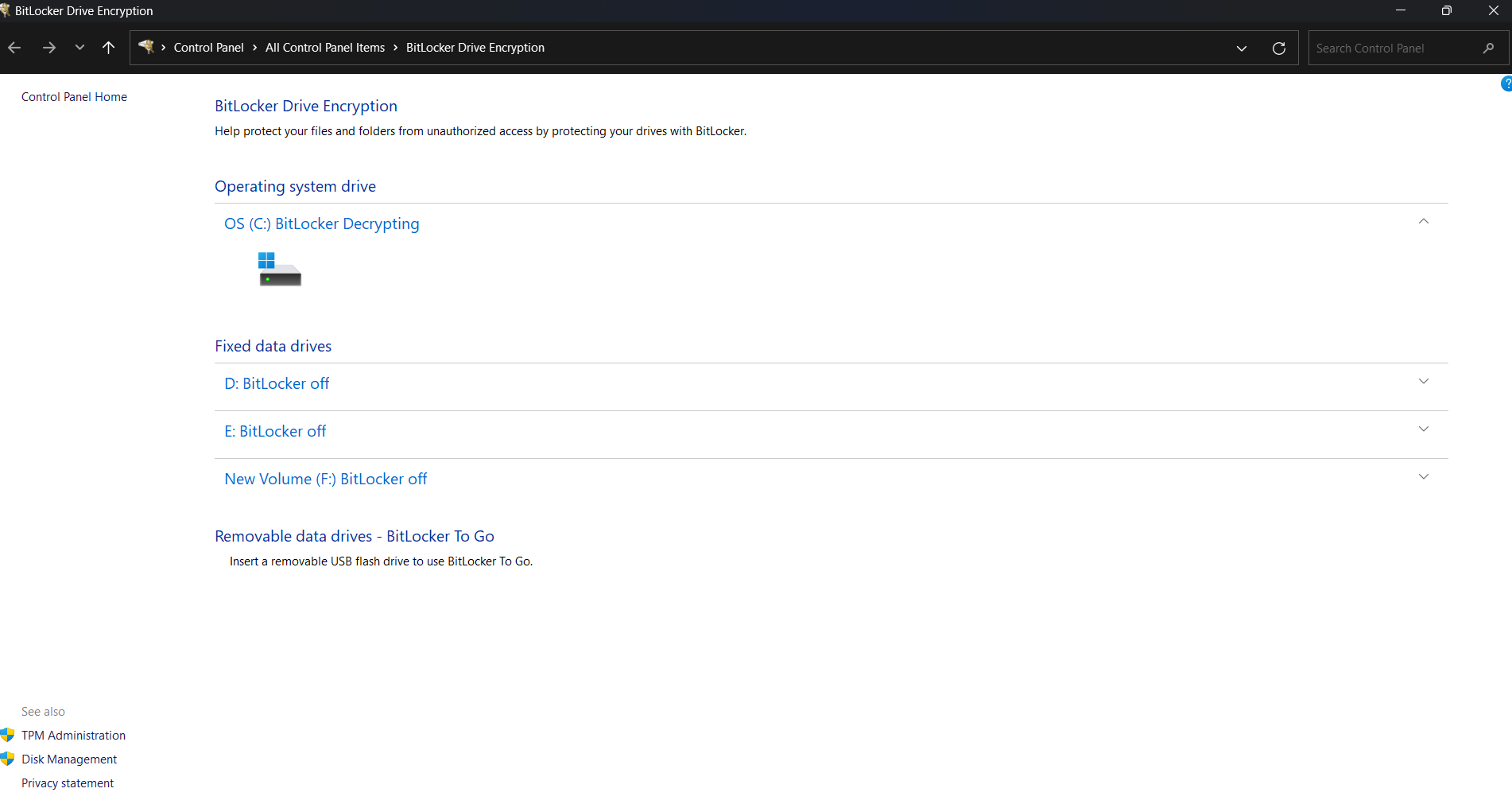
Viewing Status on the Local Device
Navigate to Control Panel > System and Security > BitLocker Drive Encryption to verify the status directly on the Windows endpoint.
Frequently Asked Questions (FAQ)
Why is “Clear auto-unlock” required to decrypt the OS drive?
The BitLocker auto-unlock feature stores decryption keys on the Operating System (OS) drive to allow data drives to open automatically upon startup. Decryption of the OS drive is prohibited while these keys remain active. Selecting Clear auto-unlock removes these keys, allowing the OS drive to revert to an unprotected state.
Can a drive be decrypted while currently locked?
No. The Force BitLocker Decryption action functions only if the drive is in an unlocked state. If a drive is locked, it must be accessed via a recovery key or password before decryption can be initiated.
Does this action result in data loss?
No. Decryption solely removes the encryption layer protecting the information. Files remain on the drive but will no longer be secured by BitLocker encryption.