Category filter
Configure Windows LAPS policy from Hexnode
What is Hexnode LAPS?
Hexnode LAPS (Local Administrator Password Solution) automatically generates, manages, and rotates passwords for local administrator accounts on Windows devices. Admins can configure it to manage passwords for multiple admin accounts, including built-in and custom accounts, across all enrolled devices. Hexnode LAPS securely rotates the password and stores them in the UEM console, where they can be accessed only by authorized Hexnode UEM technicians. By assigning unique passwords to specified administrator accounts and rotating them at defined intervals, Hexnode LAPS reduces the risk of Pass-the-Hash or other lateral movement attacks while simplifying password management for IT teams.
How is Hexnode LAPS different from Microsoft’s Windows LAPS?
Microsoft Windows LAPS automatically manages and backs up the password of local administrator accounts on devices joined to Microsoft Entra or Windows Server Active Directory. Access to these passwords is limited to administrators and managing them requires reliance on your organization’s Microsoft Entra or Active Directory setup.
Hexnode LAPS, on the other hand, operates entirely within the Hexnode UEM console. It generates, rotates, and securely stores local admin passwords for each device, accessible only to authorized IT admins. This removes reliance on Microsoft Entra or Active Directory and simplifies password management for organizations of any size.
How to configure Windows LAPS settings?
To configure Hexnode LAPS on Windows devices:
- Log in to your Hexnode UEM portal.
- Navigate to Policies > New Policy. Assign a suitable name and description (optional) for the policy. You can also choose to continue with an existing policy.
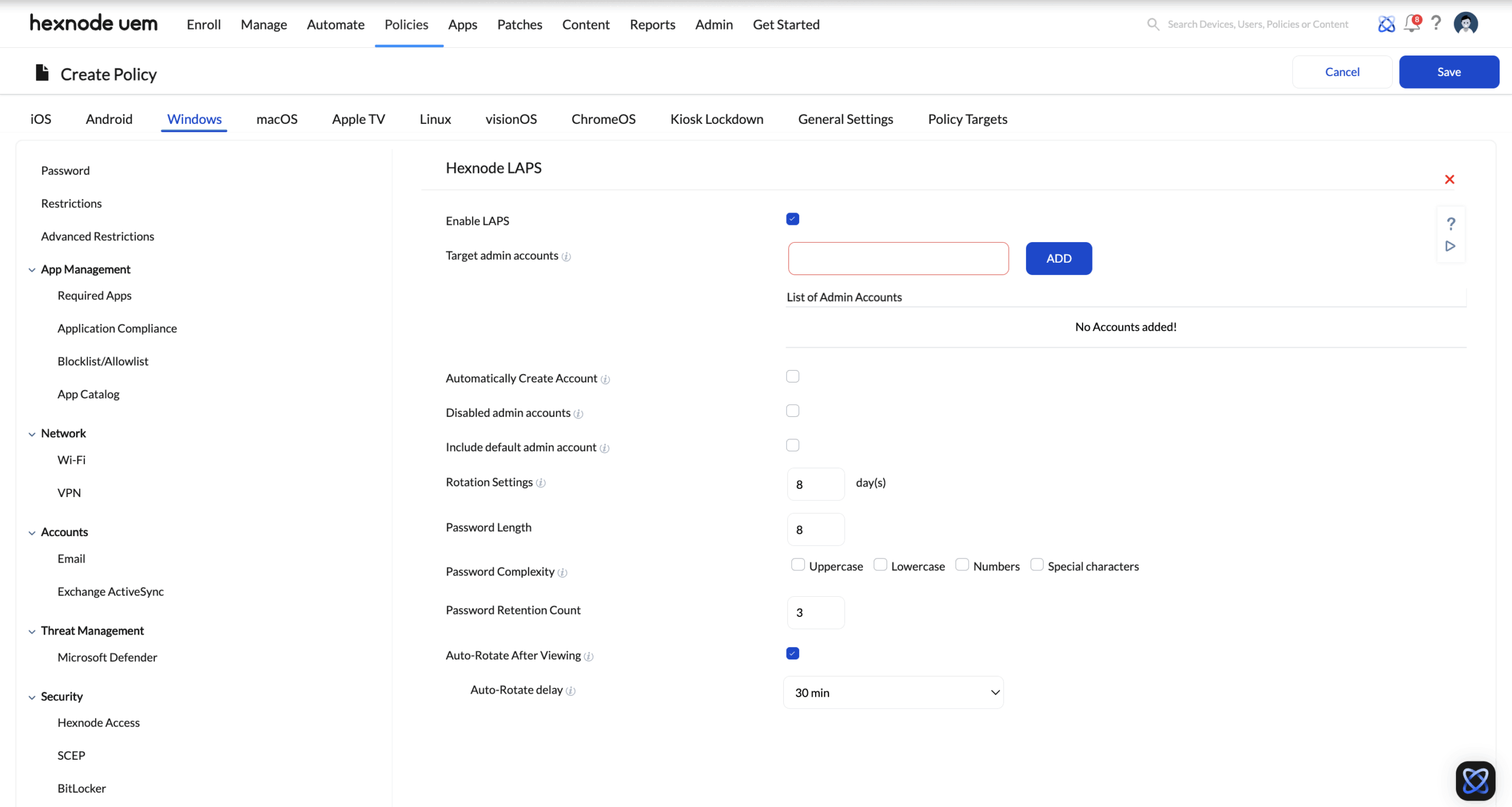
- Navigate to Windows > Security > Hexnode LAPS and click Configure.
-
You will find the following settings:
- Enable LAPS: To turn on the Local Administrator Password Solution. This setting must be enabled before you can configure any of the other LAPS settings.
- Target Admin Accounts: Add the local administrator accounts you want LAPS to manage. Standard or non-admin accounts are ignored during password rotation. Also, the account names you enter aren’t case sensitive, so names like “Admin”, “admin”, and “ADMIN” will all be treated the same.
- Automatically Create Account: If the specified admin account doesn’t exist, Hexnode will create it when the policy is deployed.
- Disabled Admin Accounts: When checked, Hexnode will enable disabled admin accounts and rotate their passwords. If left unchecked, disabled accounts will be ignored.
- Include Default Admin Account: Include the built-in administrator account in password rotation. The default admin account’s password will be rotated even if the account is disabled or renamed.
- Rotation Settings: Define how often the admin password should be automatically rotated. The value is specified in days and can be set anywhere between 1 and 365 days.
- Password Length: Define the length of the new password after each rotation. The value should be between 8 and 64.
- Password Complexity: Choose at least one character type for the password. The options include:
- Uppercase
- Lowercase
- Numbers
- Special characters
- Password Retention Count: Defines how many previously used passwords Hexnode LAPS should remember and block from being reused, preventing password repetition. The value should be between 3 and 10.
- Auto-Rotate After Viewing: IT admins can check the local administrator password for a device from Device Details page > Local Accounts > LAPS in the Hexnode UEM console. Put simply, viewing the password in the console triggers a rotation, ensuring that any exposed password is promptly replaced with a new one.
- Auto-Rotate delay: Define how long Hexnode LAPS waits before rotating the password after it has been viewed. Available options are:
- Immediately – Rotates the password shortly after it’s viewed. A brief 30-second window is provided so administrators can copy and use the password before it changes.
- 5min
- 15min
- 30min
- 1hr
- 3hrs
- 6hrs
- 12hrs
- 24hrs (1day)
- Auto-Rotate delay: Define how long Hexnode LAPS waits before rotating the password after it has been viewed. Available options are:
- Finally, click Save.
Associating the LAPS policy with devices
If the policy has not yet been saved:
- Navigate to Policy Targets.
- Select the target of the policy (Devices, Device Groups, Users, User Groups, Domains/OUs).
- Click on +Add Devices.
- Select the devices you want to apply the policy to and click OK.
- Click Save to apply the policies to the selected devices.
If the policy has already been saved:
- Go to the Policies tab.
- Select the policy you want to associate with devices.
- Click on Manage > Associate Targets.
- Select the devices or device groups to which you want to apply the policy.
- Click Associate to apply the policy to the selected devices.
View the local admin account password managed with Hexnode LAPS
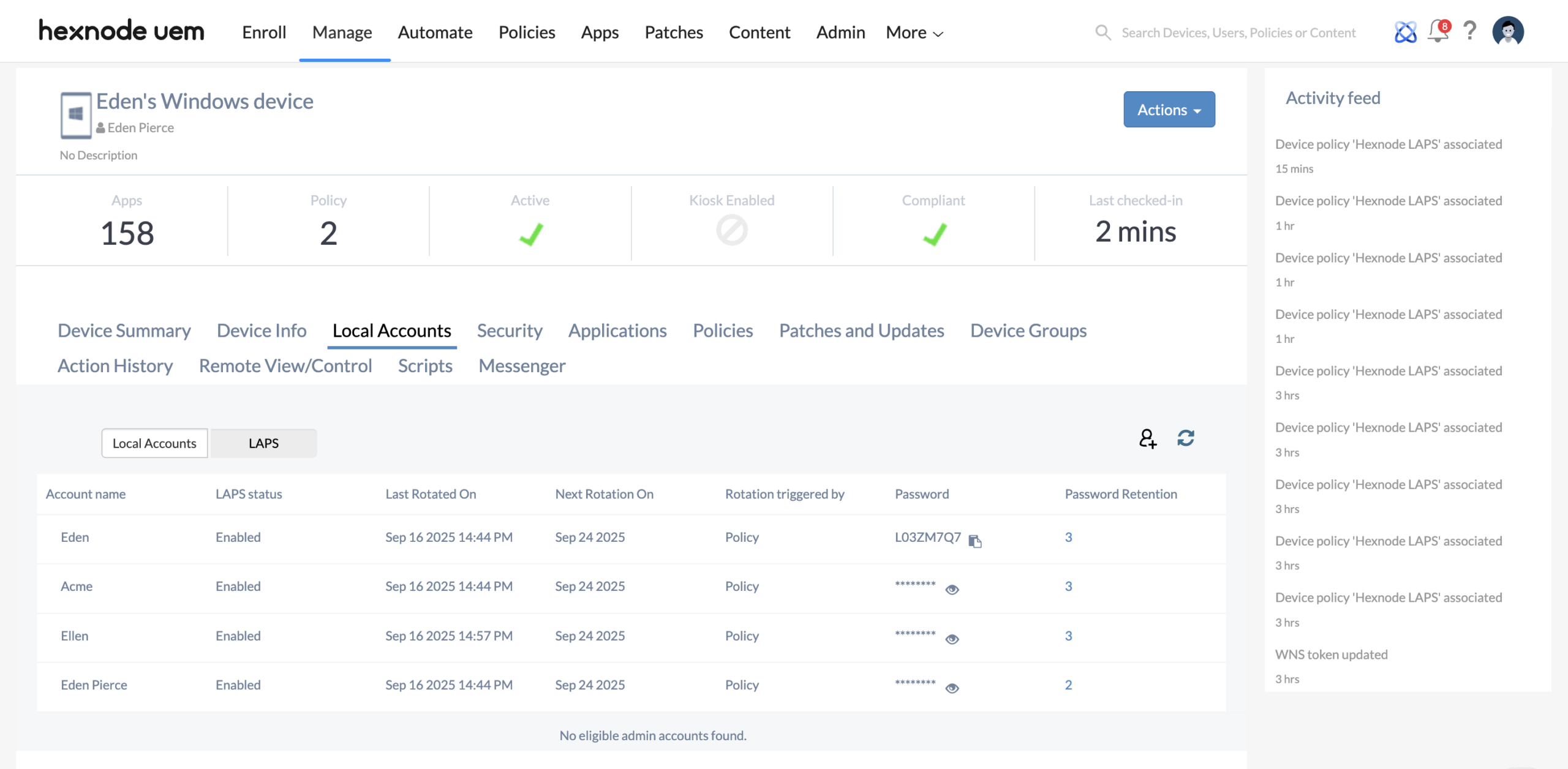
To view the local admin account password on a Windows device managed by Hexnode LAPS,
- Log in to the Hexnode UEM console.
- Go to the Manage tab and select the Windows device you want to check.
- Open the Local Accounts sub-tab and click on LAPS.
- Here, Hexnode displays all the local admin accounts on that device whose passwords are managed by Hexnode LAPS.
- To view the latest password for a local admin account, click the password reveal icon in the Password column corresponding to the specified account.
Find local admin account details associated with the Hexnode LAPS policy
To find the local admin accounts and other details of Windows devices associated with the Hexnode LAPS policy,
- Go to the Device Details page of the required Windows device and open the Local Accounts > LAPS section.
- Hexnode lists all local administrator accounts on the device whose passwords are managed by Hexnode LAPS, along with relevant details such as:
- Account Name: The name of the admin account.
- LAPS Status: Indicates whether LAPS is enabled for this account.
- Last Rotated On: Date and time when the password were last rotated.
- Next Rotation On: Scheduled date and time for the next password rotation.
- Rotation Triggered By: Shows whether the rotation was triggered by the configured Hexnode LAPS policy or via Rotate Local Admin password remote action.
- Password: The current password of the admin account.
- Password Retention: Displays the retention count. Clicking the number shows all previously used passwords stored as per the configured Hexnode LAPS policy.
Frequently Asked Questions
Can IT admins see older, rotated passwords of the admin account managed by Hexnode LAPS?
Yes, but it depends on the Password Retention Count configured in your Hexnode LAPS policy. In the LAPS section of a device’s Device Details page, the Password Retention column shows how many older passwords are stored based on the retention count set in the policy.
For example, if the policy sets the Password Retention Count to 3, the column will display 3. Clicking on it will reveal the last three rotated passwords. Any passwords older than that will not be available.
What is a Pass-the-Hash attack, and how does Hexnode LAPS help prevent it?
A Pass-the-Hash (PtH) attack occurs when an attacker captures a hashed version of a user’s password and reuses it to authenticate on other systems, bypassing the need to know the actual plaintext password. In a network where multiple devices share the same local administrator password, PtH attacks can allow attackers to move laterally across systems easily.
Hexnode LAPS mitigates this risk by assigning a unique, randomly generated password to each local administrator account and automatically rotating it at defined intervals. Since each device has a different password, even if an attacker captures one, it cannot be reused on other devices, preventing lateral movement.
What if the role of the local admin account managed by Hexnode LAPS is changed to standard?
The account will no longer be managed by Hexnode LAPS and will be removed from password rotation during the next scheduled rotation.
Can IT admins use the Change Password action in the Hexnode console to update the password of a local admin account managed by Hexnode LAPS?
Yes, you can change the password of the local admin account from the Hexnode console using the Change Password action if the applied Password policy allows it. During the next LAPS rotation, the password will be updated again based on the policy settings.
If both the Password policy and Hexnode LAPS policy define settings for password complexity and length, which settings are applied during password rotation?
In such cases, Hexnode LAPS applies the most restrictive setting for each attribute individually during password rotation.
Example:
- Password policy: Requires passwords to have at least 12 characters and include digits, uppercase letters and lowercase letters.
- Hexnode LAPS policy: Requires passwords to have at least 16 characters but only lowercase letters and numbers.
Applied settings during password rotation:
- Password complexity: Taken from the Password policy (since it is more restrictive with uppercase letter included).
- Password length: Taken from the Hexnode LAPS policy (since 16 characters is longer than 12, making it more restrictive).