Category filter
Configure remote access in managed guest sessions on ChromeOS devices
ChromeOS’s managed guest session allows multiple users to access the same device without signing in with their Google account credentials. During such sessions, IT administrators may require remote access in managed guest session mode for troubleshooting, or end-users may need to connect to another device within the organization for collaboration. Hexnode UEM enables IT admins to configure the settings of the remote session and manage various aspects of communication between host and client devices.
This document provides an overview of the various remote access settings available to configure remote access for managed guest sessions through Hexnode UEM.
Steps to configure Remote Access settings
To configure remote access settings on ChromeOS devices via Hexnode UEM:
- Log in to your Hexnode UEM portal.
- Navigate to Policies > New Policy. Give a suitable name and description (optional) for the policy. You can also choose to continue with an existing policy.
- Navigate to ChromeOS > Managed Guest Session > Remote Access.
- Click Configure.
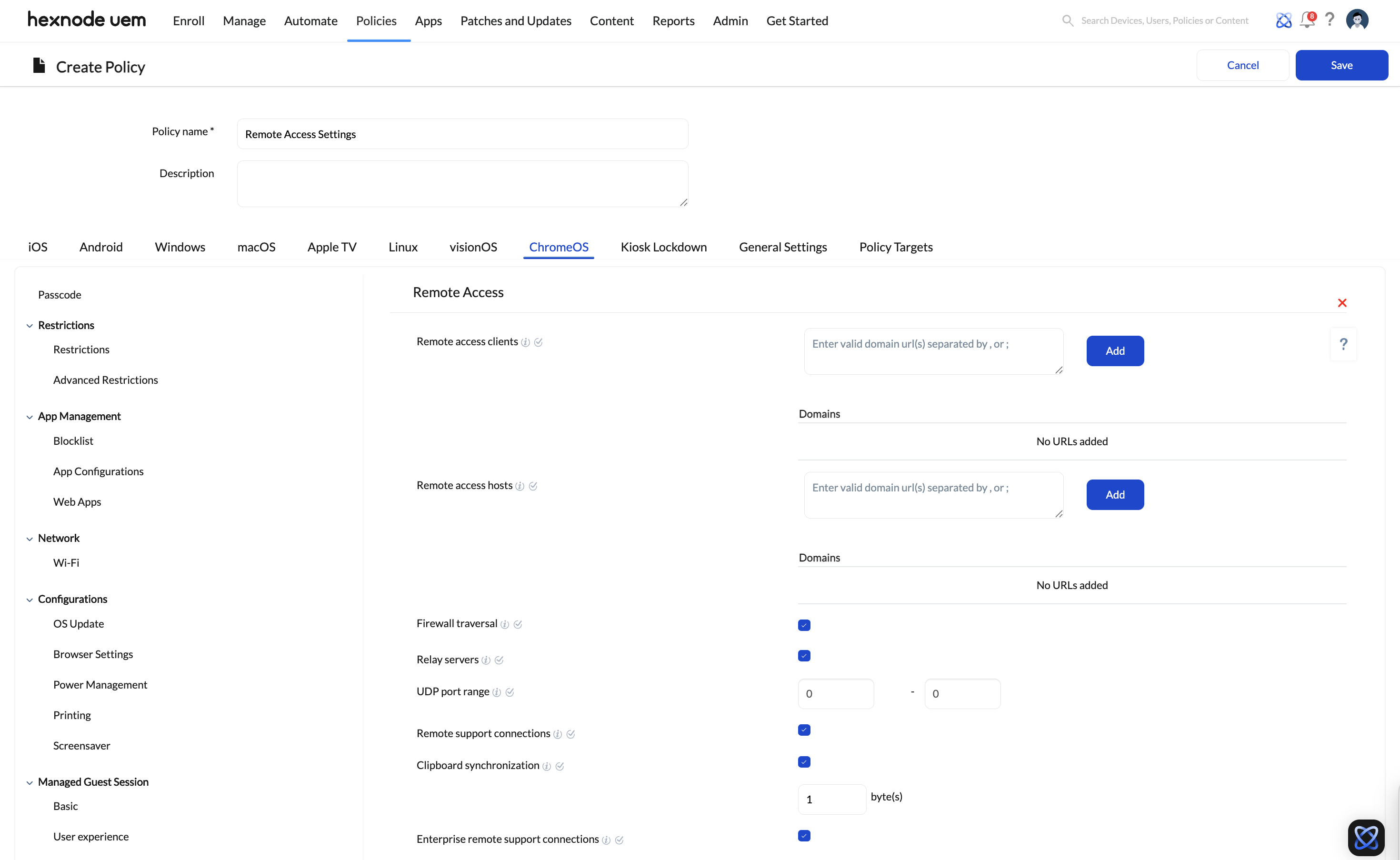
The following options are available to configure:
| Settings | Description | Supported versions |
|---|---|---|
| Remote access clients | Specify the domain URLs that are imposed on remote access clients. |
ChromeOS 60+ |
| Remote access hosts | Specify the host domain URLs that are imposed on remote access hosts. |
ChromeOS 60+ |
| Firewall traversal | If checked, remote access clients can bypass the firewall and establish a connection with the host device by using STUN servers. If disabled, all outgoing UDP connections will be filtered by the firewall. |
ChromeOS 41+ |
| Relay servers | If checked, the usage of relay servers by the remote access host will be enabled. | ChromeOS 86+ |
| UDP port range | Specify the UDP port range to be used by remote access hosts by entering their minimum and maximum range. | ChromeOS 41+ |
| Remote support connections | When enabled, the remote support host cannot be started or configured to accept incoming connections. |
ChromeOS 97+ |
| Clipboard synchronization | If checked, a limit can be set (in bytes) on the clipboard data that can be transferred between the client and host device with clipboard sync. |
ChromeOS 97+ |
| Enterprise remote support connections | When enabled, remote support sessions to a managed ChromeOS device can be started from the Google Admin console. | ChromeOS 113+ |
Associating the policy to Organizational Units (OUs)
Policies cannot be directly associated with ChromeOS devices; they can only be applied through Organizational Units (OUs).
To associate a ChromeOS policy to the devices upon configuration,
- Navigate to Policy Targets > Domains/OUs.
- Click on +Add Domain/OUs. From the list, select the Google Workspace account integrated with Hexnode, indicated by the (Google) tag.
- The parent OU will be listed here and is indicated with a briefcase icon to differentiate it from domains.
- Click the dropdown next to the parent OU to view its child OUs. Select the required Organizational Units and click OK.
- Note that a policy assigned to a parent OU will automatically apply to all its child OUs. Associate the policies to the OUs to which the target devices are assigned.
- Click Save to associate the policy to the devices under the selected Organization Units.