Category filter
Configure security and hardware settings in managed guest sessions
Security and hardware settings in managed guest sessions on ChromeOS devices define how much access and control users are permitted during each session. Security settings focus on browser-level safeguards. They control features such as incognito mode, TLS configurations, data retention, and remote debugging. These settings determine how Chrome handles user privacy, encryption standards, and interactions with web content. Hardware settings manage access to the device’s physical components, like audio input, or external storage. They also control how websites interact with these components.
Although managed guest sessions do not retain any user data or activity after logout, applying these settings ensures a secure and controlled environment while the session is active. For example, a public library might block access to external storage and disable pop-ups to prevent misuse.
Together, security and hardware settings help administrators enforce a consistent, controlled, and secure experience for every guest user.
Security and Hardware settings
To configure security and hardware settings in managed guest sessions on ChromeOS devices,
- Login to the Hexnode UEM portal.
- Go to the Policies tab. Click on New Policy to create a new policy or modify an existing one.
- Provide the name and description (optional) for the policy.
- Navigate to ChromeOS > Managed Guest Session > Security & Hardware.
- Click on Configure.
- Default: Uses the system’s default hash algorithm.
- Allow: Permits the use of insecure hash algorithms.
- Deny: Blocks all insecure hashes during TLS handshakes.
- Default: Follows the system’s default configuration.
- Allow: Enables post-quantum key agreement.
- Deny: Disables post-quantum key agreement.
- Allow users to use incognito mode in Chrome
- Block users from using incognito mode in Chrome
- Force incognito mode in Chrome
- Browsing history
- Download history
- Cookies and other site data
- Cached images and files
- Passwords and other sign-in data
- Autofill form data
- Site settings
- Hosted app data
- Allow user to choose: Users can choose the task scheduler mode.
- Optimize for stability: Uses a conservative Hyper-Threading configuration to prioritize system stability.
- Optimize for performance: Uses an aggressive Hyper-Threading configuration to maximize performance.
- Ignore: No action is taken when the security token is removed.
- Logout: Logs the user out after the security token is removed. A notification that blocks the screen appears, alerting the user about the upcoming logout. You can define how many seconds this notification remains visible. If the security token is reinserted within that time, the logout is cancelled.
- Lock: Locks the session after the security token is removed. A notification that blocks the screen appears, alerting the user that the session will be locked. You can define how long this message stays on screen. If the security token is reinserted during this time, the lock action is cancelled.
- Screen brightness on battery
- Screen brightness on AC power
- Allow external storage (default)
- Allow external storage with read only access
- Do not allow external storage
- User can choose (default)
- Allow sites to request user for access
- Do not allow sites to request for access
- URLs field: Specify the website URL patterns that should be granted access.
- Devices field: Enter USB device IDs in the format vendor_id:product_id, separated by commas.
- URLs field: Specify the website URL patterns that should be granted access.
- Devices field: Enter HID device IDs in the format vendor_id:product_id, separated by commas.
The following settings are available to configure,
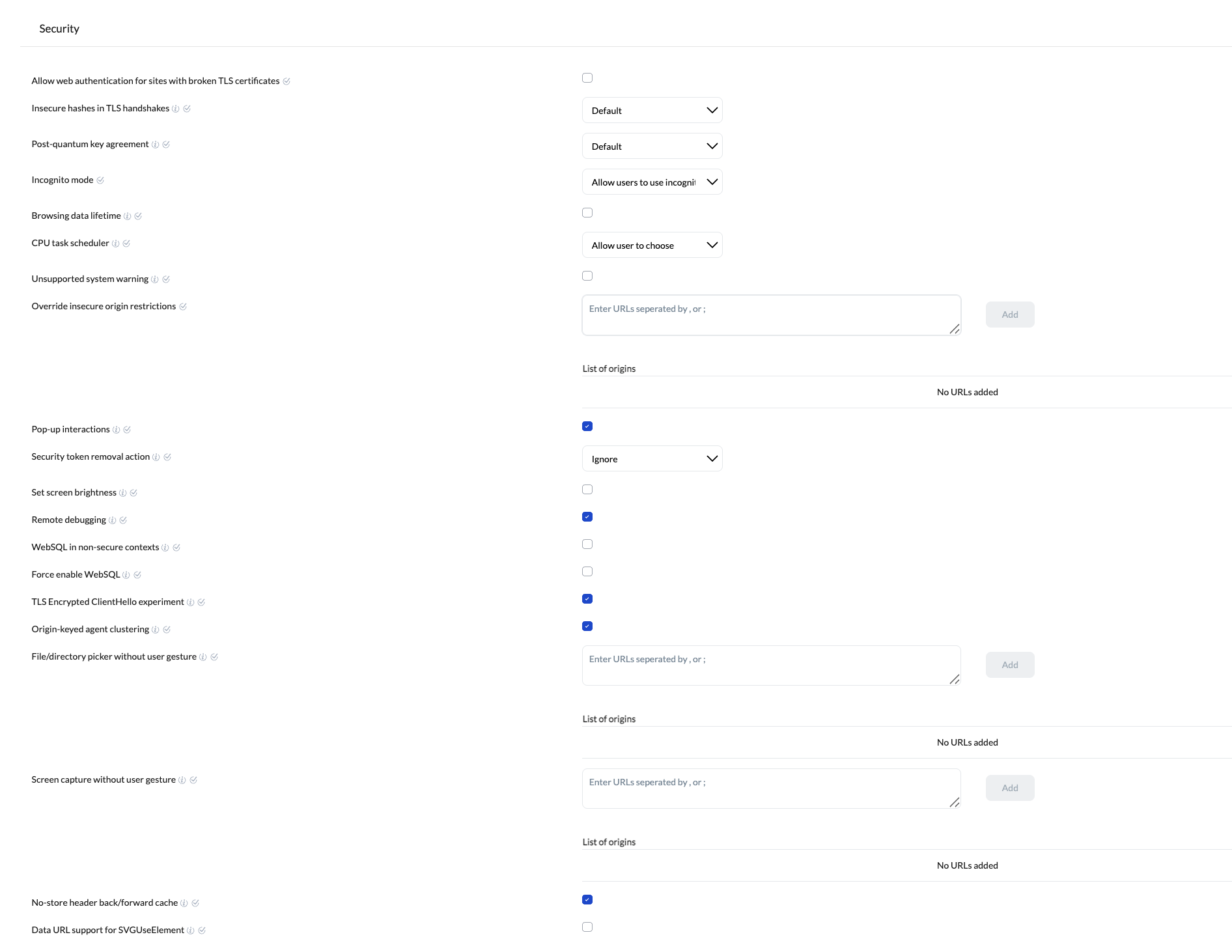
Security settings
| Restriction | Description | Supported OS |
|---|---|---|
| Allow web authentication for sites with broken TLS certificates | When enabled, Chrome permits Web Authentication requests on websites with TLS (Transport Layer Security) certificate errors i.e., sites flagged as insecure. | ChromeOS 110+ |
| Insecure hashes in TLS handshakes | Controls whether Chrome can use legacy, insecure hash algorithms during TLS handshakes. You can choose from the following options:
|
ChromeOS 114–123 |
| Post-quantum key agreement | Determines support for post-quantum key agreement algorithms in TLS connections. You can choose from the following options:
|
ChromeOS 116+ |
| Incognito mode | Manages access to Chrome’s Incognito mode. You can choose from the following options:
|
ChromeOS 14+ |
| Browsing data lifetime | Allows administrators to control how long Chrome retains user’s browsing data before it is automatically cleared.
When enabled, you can set a specific retention period (in hours) for the following data types: After the configured duration, the specified data is automatically removed from the browser. |
ChromeOS 89+ |
| CPU task scheduler | Optimizes the system for either stability or performance by selecting the appropriate Intel Hyper-Threading Technology mode. You can choose from the following options:
|
ChromeOS 74+ |
| Unsupported system warning | Suppresses warning messages when Chrome is running on unsupported hardware or operating systems. | ChromeOS 49+ |
| Override insecure origin restrictions | Specify a list of origins or hostname patterns that are exempt from Chrome’s insecure origin restrictions. | ChromeOS 69 |
| Pop-up interactions | When enabled, it prevents pop-up windows from interacting with the page that opened them. | ChromeOS 88–102 |
| Security token removal | Controls the behaviour of user sessions when the security token (e.g., smart card) is removed. You can choose from the following options:
|
ChromeOS 90+ |
| Set screen brightness | Sets the screen brightness level for the managed guest session. While users can manually adjust brightness, the setting will revert to the configured value after a device reboot or when the policy is re-applied.
You can configure separate brightness levels for: |
ChromeOS 72+ |
| Remote debugging | Prevents users from using remote debugging, even when attempting to enable it via command-line switches. | ChromeOS 93+ |
| WebSQL in non-secure contexts | Disables WebSQL on non-secure contexts unless explicitly enabled using a Chrome flag. | ChromeOS 105–112 |
| Force enable WebSQL | Keeps WebSQL enabled and prevents users from disabling it through Chrome flags. | ChromeOS 101–123 |
| TLS Encrypted ClientHello experiment | Enables the TLS Encrypted ClientHello experiment to encrypt sensitive fields and improve security. | ChromeOS 105 |
| Origin-keyed agent clustering | When unchecked, site-keyed agent clusters are allowed instead of origin-keyed ones. | ChromeOS 100+ |
| File/directory picker without user gesture | Specify the list of URLs where websites can access file or directory picker APIs without requiring user interaction on the webpage. | ChromeOS 100+ |
| Screen capture without user gesture | Specify the list of URLs where websites can initiate media picker (e.g., screen capture) without user interaction on the webpage. | ChromeOS 113+ |
| No-store header back/forward cache | When checked, it enables caching even for pages with the Cache-Control: no-store header. | ChromeOS 116+ |
| Data URL support for SVGUseElement | Starting with ChromeOS M119, data URLs are blocked by default. Enable this option to allow data URLs to continue working in SVGUseElement. | ChromeOS 120+ |
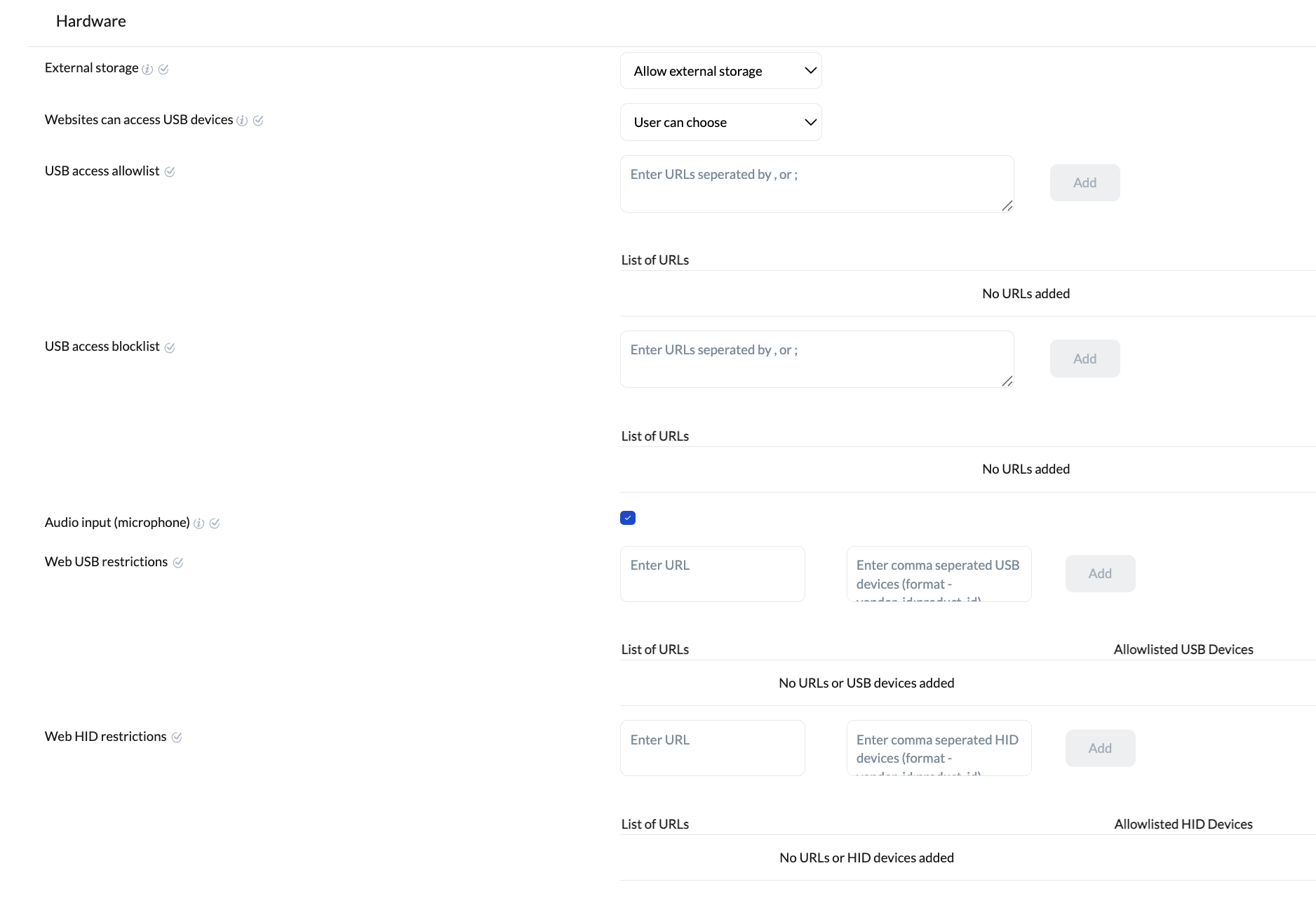
Hardware settings
| Setting | Description | Supported Versions |
|---|---|---|
| External storage | Manage user access to external storage devices like SD cards, USB flash drives, and MTP devices. You can choose from the following options:
|
ChromeOS 54+ |
| Websites can access USB devices | Control how websites can access connected USB devices. You can choose from the following options:
|
ChromeOS 67+ |
| USB access allowlist | Specify the list of websites allowed to prompt users for access to USB devices. Only these sites can make such requests, while all others will be blocked. | ChromeOS 68+ |
| USB access blocklist | Specify the list of websites that are not allowed to prompt users for USB device access. These sites will be blocked from requesting access. | ChromeOS 68+ |
| Audio input (microphone) | Prompts users for permission when a website tries to access the microphone. | ChromeOS 23+ |
| Web USB restrictions | Automatically grant access to specified USB devices for selected websites.
|
ChromeOS 79+ |
| Web HID restrictions | Automatically grant access to specific HID (Human Interface Devices) for listed websites.
|
ChromeOS 116+ |
Associate the policy with target entities
If you haven’t saved the policy,
- Navigate to Policy Targets.
- Select Domains/OUs.
- Click on +Add Domains/OUs.
- The Browse Domain/OU window will appear.
- From here, select the Google Workspace account that is integrated with Hexnode, (eg: example.kmanaged.com(Google))
- Next, locate the Parent OU, which is represented by a briefcase icon. Select the Parent OU to associate the policy with it, or
- Click the dropdown icon beside the Parent OU to expand and select the required Child OU(s).
- Once selected, click OK, then Save to apply the changes.
If you have already saved the policy,
- Navigate to Policies > My Policies and select the required policy.
- Click on Manage > Associate Targets.
- Select Domains/OUs.
- From here, select the Google Workspace account that is integrated with Hexnode, (eg: example.kmanaged.com(Google)).
- Next, locate the Parent OU, which is represented by a briefcase icon. Select the Parent OU to associate the policy with it, or
- Click the dropdown icon beside the Parent OU to expand and select the required Child OU(s).
- Click on Associate.