EDR Explained: A Complete Guide to Modern Endpoint Security
Want to take a closer look at how Endpoint Detection and Response works in practice? Check out our in-depth guide

Get fresh insights, pro tips, and thought starters–only the best of posts for you.

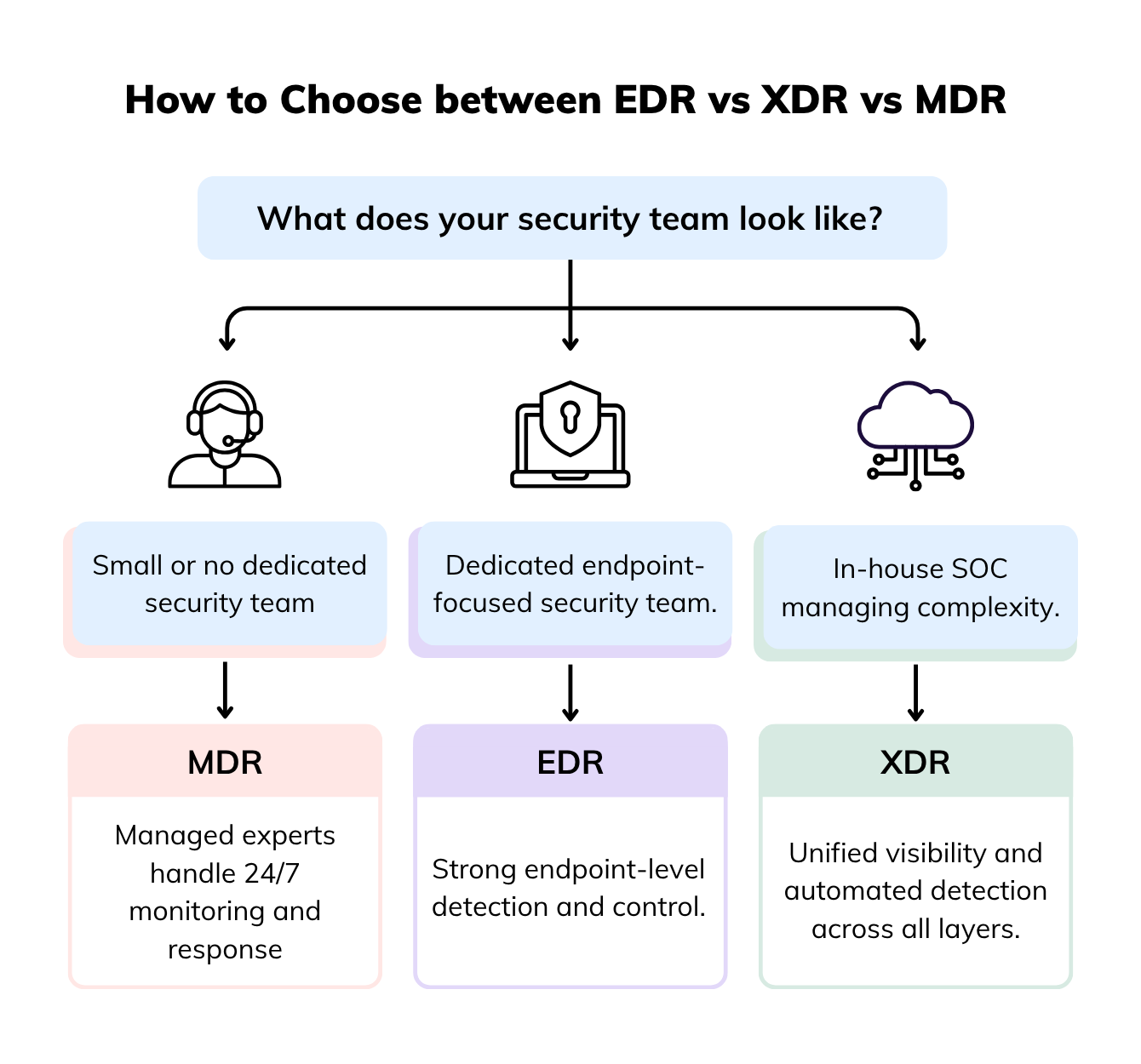
EDR, XDR, and MDR represent three layers of modern cyber defense. EDR secures endpoints, XDR expands visibility across systems, and MDR adds 24/7 human expertise. Understanding how they differ helps you pick a solution that fits your team’s size, resources, and security goals – without overcomplicating your defense.
Modern attacks move quicker than the tools built to stop them, pushing security teams to rethink their approach. From ransomware and phishing to complex supply chain breaches, the threat surface keeps expanding — and so do the risks.
To stay ahead, security can’t just react; it has to think. That’s where EDR, XDR, and MDR come in.
These modern detection and response models mark a major shift in how organizations find, analyze, and contain threats. Each has its strengths — and knowing the difference helps you choose the protection that actually fits your environment.
Endpoint Detection and Response (EDR) focuses on one mission — protecting devices like laptops, desktops, and mobile endpoints from advanced threats that slip past traditional defence. These are the endpoints attackers often target first, and once breached, they can open the door to your entire environment.
EDR focuses on spotting those attacks early. It continuously tracks what’s happening on each device — from process executions to file changes and user behavior — looking for patterns that suggest something’s off. When it finds one, it gives security teams the data and tools they need to investigate, contain, and remediate before the threat spreads.
What EDR does:
Why it matters:
EDR is most effective for organizations with a dedicated IT or security team — people who can analyze alerts, fine-tune detection rules, and act quickly when something suspicious shows up. It’s not just about finding threats, but understanding how they got in and how to stop them next time.
Extended Detection and Response (XDR) builds on what EDR started — but instead of stopping at endpoints, it brings the bigger picture into focus. XDR connects data from endpoints, networks, cloud workloads, email systems, and user identities, giving security teams a single, cohesive view of what’s happening across their environment.
Traditional tools often work in silos, forcing analysts to jump between dashboards to piece together what happened. XDR breaks that wall. It correlates signals from every layer — endpoint activity, network traffic, authentication logs, and cloud telemetry — to uncover the full story behind an attack.
What XDR delivers:
By merging all these data points, XDR helps analysts focus on high-fidelity alerts — the real threats — instead of chasing false positives or sifting through disconnected signals.
Modern attacks rarely stay confined to one system. A single phishing email can compromise credentials, move laterally across the network, and infiltrate cloud storage within hours. XDR connects these dots automatically, showing how each event relates to the bigger attack chain.
It’s this contextual insight that makes XDR so valuable. Instead of reacting to isolated alerts, security teams can see the entire attack path — and shut it down before it escalates.
While Endpoint Detection and Response (EDR) and Extended Detection and Response (XDR) equip organizations with powerful tools to detect and contain threats, they still rely on skilled security teams to manage and interpret them effectively. Analysts need to investigate alerts, fine-tune detections, and perform proactive threat hunting – tasks that demand both time and expertise. Not every organization has the resources or personnel to maintain that level of focus internally.
MDR is a fully managed security service that pairs advanced detection technology with a dedicated team of cybersecurity experts. Instead of relying solely on automation, MDR brings in the human element — professionals who monitor your environment 24/7, investigate suspicious activity, and respond to threats in real time. MDR often integrates with existing EDR or XDR platforms to deliver these capabilities as a managed service, allowing businesses to strengthen their defenses without expanding internal security teams.
What MDR covers:
With MDR, you’re essentially extending your security team — without having to build one from scratch.
MDR is ideal for small to mid-sized organizations that don’t have an in-house SOC or prefer to offload the operational heavy lifting of threat management. It’s also a strong fit for enterprises that want expert oversight on top of their existing tools, ensuring no critical alert slips through the cracks.
For SMBs, this blend of automation and human expertise is especially valuable. Automated detection tools handle the heavy lifting — scanning logs, correlating data, and flagging suspicious behavior in real time. Meanwhile, human analysts step in to validate alerts, investigate anomalies, and apply context that automation alone can’t provide. This partnership ensures smaller teams get enterprise-grade protection without needing to scale headcount or infrastructure.
By combining the scale of technology with the precision of human judgment, MDR helps organizations stay protected even when resources are limited — offering peace of mind that someone’s always watching your back.
Here’s a quick snapshot comparing EDR, XDR, and MDR by their focus, scope, and management style. Each takes a different approach to strengthening threat detection and response.
| Feature | EDR | XDR | MDR |
| Focus | Endpoint detection | Extended visibility across layers | Managed detection and response |
| Scope | Endpoint only | Endpoint, network, cloud, identity | Varies by provider’s tools |
| Management | In-house | In-house or hybrid | Fully managed service |
| Response type | Automated or manual | Automated + Correlated | Human + Automated |
| Visibility | Endpoint-level | Multi-layered | Depends on MDR provider |
| Ideal for | Security teams with resources | Enterprises seeking unified visibility | Businesses needing outsourced SOC |
| Goal | Detect and remediate endpoint threats | Provide holistic, AI-driven defense | Deliver expertise and 24/7 monitoring |
Choosing between EDR, XDR, and MDR isn’t about which one sounds more advanced — it’s about finding what fits your team, your infrastructure, and the level of visibility you actually need. The right choice depends on your organization’s size, security maturity, and resources.
Key things to consider
XDR sits in between, offering scalability with flexibility for hybrid teams.
Each model has its strengths. For smaller teams, MDR brings peace of mind. For mature setups, XDR delivers efficiency and insight. And for endpoint-heavy environments, EDR keeps defenses focused and responsive.
Ready to lock down your mobile devices? Grab this essential checklist to immediately start fortifying your mobile fleet, protecting sensitive data, and tackling those evolving threats head-on.
Download the Checklist Now!At Hexnode, we’ve always believed that security and endpoint management shouldn’t live in separate silos. They’re two sides of the same story — control and protection working hand in hand. Our Unified Endpoint Management (UEM) platform already gives IT teams the visibility, context, and control they need to secure their device ecosystem. The next step is expanding that visibility beyond endpoints.
That’s where Hexnode XDR comes in.
We’re building an integrated, data-driven defense layer that connects endpoint insights with network telemetry, cloud intelligence, and behavioral analytics. The goal is simple: help IT and security teams detect threats earlier, respond faster, and make smarter security decisions — all from a single, unified platform.
By merging UEM and XDR, we’re creating a security ecosystem where every signal matters. Device activity, user behavior, and network patterns work together to tell the full story of an incident — not isolated fragments. It’s visibility and control, elevated into active defense.
The future we’re building at Hexnode is one where:
From managing endpoints to mastering threats, Hexnode’s evolution into XDR marks the next step in unified cybersecurity — where operational simplicity meets deep, intelligent defense.
Hexnode Expands Product Line to Include XDR and DEX Solutions at HexCon25
?Can EDR, XDR, and MDR work together?
Yes, and they often do. Many organizations use EDR or XDR as their core defense, paired with MDR services for 24/7 monitoring and expert response. It’s the balance of strong tools and human insight.
?Which solution is best for small businesses with limited IT resources?
For smaller teams, MDR is usually the most practical option. It provides access to experienced security professionals who handle monitoring, investigation, and response on your behalf. That means you get enterprise-level protection without needing to build an in-house SOC or hire around-the-clock analysts.
? Is XDR just a marketing term for EDR?
Not quite. While XDR builds on EDR’s foundation, it goes well beyond endpoints. XDR pulls in telemetry from networks, cloud platforms, identity systems, and even email — connecting the dots between isolated events. The result is a broader, more contextual view of your entire attack surface.
? What threats can EDR detect that traditional antivirus might miss?
Traditional antivirus tools rely on known malware signatures, which means new or evolving threats can slip through. EDR, on the other hand, tracks behavior — not just files. It can detect zero-day exploits, fileless malware, lateral movement, and insider threats that static antivirus software often overlooks.
? Does EDR require a dedicated security team to manage?
In most cases, yes. EDR solutions generate detailed telemetry and alerts that require skilled analysts to review and act on. Without a trained team to interpret the data, you risk alert fatigue or missed signals — which is why many organizations combine EDR with MDR for expert support.
? Can EDR be used in cloud environments?
Absolutely. Modern EDR tools are built to monitor endpoints regardless of where they sit — on-premises, in the cloud, or remote. Cloud-native EDR agents provide consistent visibility and protection across distributed environments, which is essential for hybrid or remote-first workforces.
? Is XDR suitable for organizations with existing security tools?
Yes. XDR is designed to integrate, not replace. It can pull data from tools you already use — like SIEMs, firewalls, and identity providers — and correlate that information to create a unified threat picture. This helps reduce tool sprawl and makes your existing stack more effective.
? What does a typical MDR service include?
MDR usually covers 24/7 monitoring, threat detection, incident response, and proactive hunting — all handled by a dedicated security team, often with regular reporting and recommendations.
EDR, XDR, and MDR each tackle the same challenge from different angles — detecting and responding to threats before they cause damage.
The right choice depends on your team’s maturity, tools, and goals — but the endgame is the same: stronger, faster, smarter defense.
At Hexnode, we’re bridging that gap. By bringing Unified Endpoint Management (UEM) and Extended Detection and Response (XDR) together, we’re building a platform where protection and control work as one — giving IT and security teams the intelligence to stay ahead of every threat.
Explore how Hexnode’s upcoming XDR redefines unified cybersecurity.
Start your 14-day free trial today!