Explore Resources Hexnode UEM for Education

Hexnode UEM for Education
7 min read
Get started with Hexnode’s device management solution for the education industry that helps in remotely securing all learning apps, resources and devices from a central console.

Hexnode Windows Management Solution
7 min read
Hexnode Windows Management Solution helps improve efficiency, increase productivity, save time and overhead costs of managing your corporate devices.
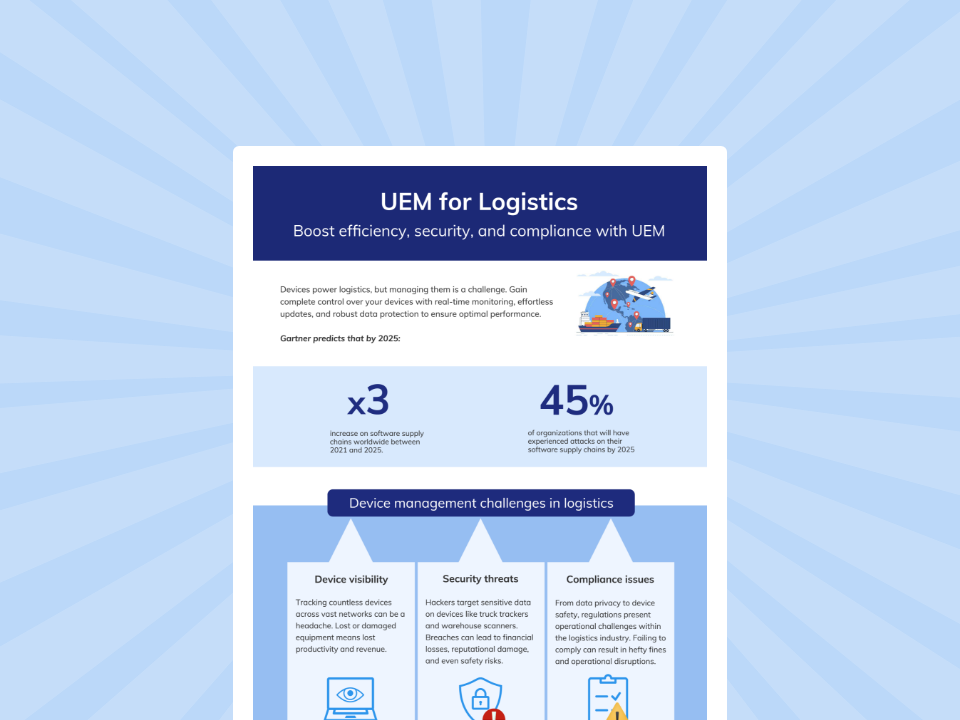
Boost efficiency, security and compliance in logistics with UEM
3 MINS
Learn how Hexnode UEM is beneficial in the logistics industry.

Hexnode Mac Management
8 min read
Get started with Hexnode’s Mac Management solution to save your time and the associated IT operational costs of managing your Mac devices.

Hexnode App Management Solution
8 min read
App Management helps businesses deploy work apps seamlessly to managed devices.

Hexnode UEM for Healthcare
8 min read
Hexnode UEM supports the healthcare industry to manage medical devices.

Android Enterprise Management Solution
9 min read
Get started with Hexnode’s Android Enterprise management solution for IT admins.

Hexnode Asset management solution
8 min read
Get started with the Hexnode Asset management solution & manage all your endpoints.

UEM migration kit
zip, 18.94 MB
The UEM migration kit will help you adopt the right strategy for a successful migration.
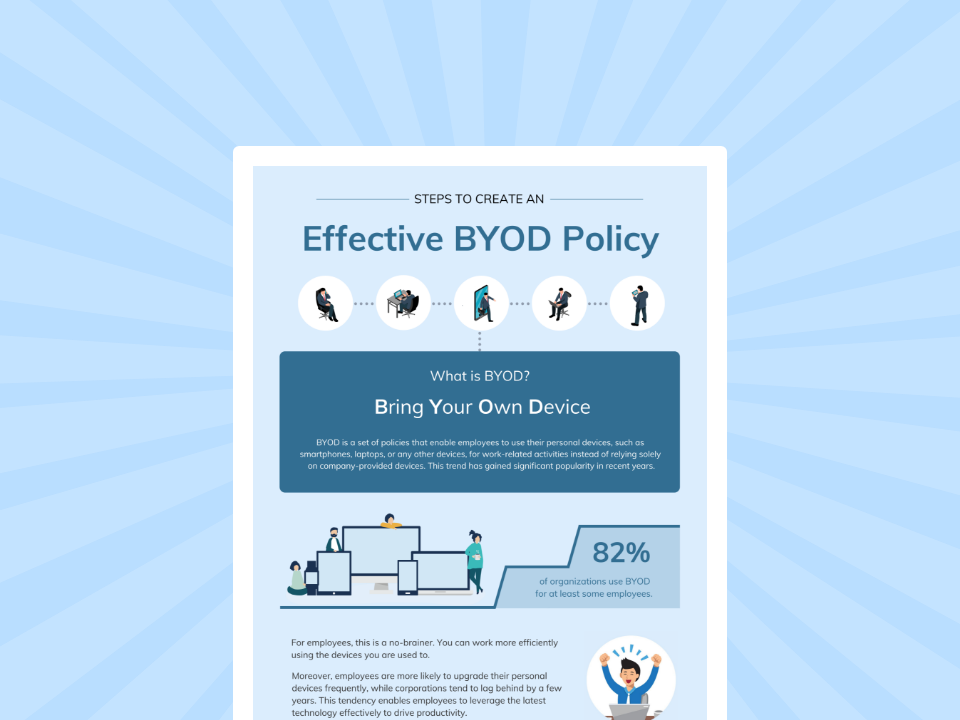
Steps to create an effective BYOD policy
3 min
Have a look at the 8-step plan on creating an effective BYOD policy.

