The concern for endpoint security for Mac devices has often taken a backseat compared to Windows corporate devices. The higher security of Mac devices has been a given ever since the first MacBook was introduced in May 2006. However, while Macs do boast of a relatively secure environment compared to their counterparts, they are not invincible against security threats. For Macs in corporate use, it is necessary to evolve the endpoint security in accordance with the latest trends.
Common mistakes while achieving Endpoint Security for Mac
Relying on end-users for securing their devices
Mac users are often pre-conceived as the more technical users. The task of securing their devices is left to the end-user which can be a risky move. End users cannot be expected to be proactive about device security at all times. Properly monitoring the devices and ensuring that the updates and configurations are properly enabled is the responsibility of the IT admin.
Excessive restrictions on the devices
While it is inadvisable to give the user complete control over the device, it is also not recommended to tightly restrict the devices. Striking the right balance is important to maximize security while not compromising on user experience.
Dependence on legacy applications for protection
macOS is constantly evolving and the tools responsible for securing the Macs need to keep up with the pace. For example, using the Profile Manager tool to manage your Apple devices may work for a few devices but it would backfire in the long run when the business has a growing number of devices. Using a proper MDM solution that stays updated with the latest technology is the optimal option for managing a bulk number of devices.
Security Threats in 2020

1. Phishing: Phishing and credential attacks never go out of fashion in the battle for security. For macOS users, phishing attacks have gone up by 30-40% last year. These attacks could be aimed at stealing the Apple ID of the user or installing adware on the Mac. Using 2-Factor authentication for access to the accounts can give a measure of security against phishing. Watch out for:
- Emails apparently from Apple support claiming to have detected problems in your Mac or claiming that your Apple account is locked with a “Restore” link. Such emails are often used for fooling the user into giving their Apple credentials.
- Bank links in an email. Online bank accounts should be accessed only by manually typing in the URL or your own bookmarks.
- Unauthorized dmg or pkg files. The apps should be installed either from the Mac App Store or a trusted developer. If the Mac is enrolled with Hexnode, the admin can restrict the user to the App Store and remotely install the required applications for higher security
2. Ransomware: While a Windows user has been well aware of the threat ransomware poses, Mac users have enjoyed a relatively calmer experience. However, with the advanced ransomware like ThiefQuest surfacing especially for Macs, the admins can no longer be complacent towards the security threat. With Hexnode, preventive measures such as setting up a VPN, configuring Firewall and blacklisting dangerous websites can be taken with ease.
3. Insider Attacks: With all the corporate data migrating to the cloud, conducting a security attack would not be easy. In such a case, it is possible that the attackers seek to get insider information by providing high compensation. To prevent insider attacks to an extent, the best method is to provide the minimum access possible. The user should have access only to those accounts that are essential for getting the work done. For instance, with Hexnode, you can create user groups according to departments and assign different policies and configurations to each user group as required.
4. Software attacks: No software is perfect. There is always the possibility of discovering a new security weakness in the existing version. The software and OS updates usually patch the weak links in the security. The user may often skip the updates, which would leave the system vulnerable to attacks. Hence, it is recommended to enforce the OS updates for enterprise macOS devices.
Using an MDM for Endpoint Security
A Mobile Device Management solution is a simple and excellent tool for increasing the endpoint security of the macOS devices.
FileVault Encryption
FileVault is Apple’s full-disk encryption program. The disk content is encrypted and the users have to provide a passcode on booting the device to access the data and files. It highly increases device security as it actively prevents unauthorized users from accessing sensitive corporate data. Hexnode provides you with three methods for encrypting your macOS computers:
1. Personal Recovery Key: These are the unique alphanumeric keys that are automatically generated at the time of encryption. The user has to note the key for future decryption of the encrypted disk.
2. Institutional Recovery Key: These are used by institutions or organizations so that a common key is used to decrypt all their devices.
3. Institutional and Personal Recovery Key: As the name suggests, both institutional and personal recovery keys are generated for the user. This is the most recommended method for device encryption. A major advantage is that even if the personal recovery key is lost, you would be able to decrypt the device using the institutional recovery key.
Smart Card Authentication
For devices running macOS 10.12.4 or higher, the IT admins can remotely configure smart card authentication settings with Hexnode. Authentication via smart cards improves the device security by leaps and bounds than a simple device password. Hexnode allows you to enable user login via smart cards, enforce users to pair with a single smart card, verify the authenticity of the certificate, and much more.
Managed software and OS updates
Enforcing OS updates for the business Macs is an effortless task with an MDM like Hexnode. The OS updates can be downloaded and scheduled to install at a later time or be installed directly after downloading.
Network security
Using an MDM to set up the enterprise Wi-Fi would allow the users to connect without prompting for the password. A major benefit of setting up the Wi-Fi via MDM is the additional layer of security for the enterprise network achieved by preventing the knowledge of the network password for the user.
Web Content Filtering
Majority of the security attacks are successful only because of irresponsible surfing of the internet at the endpoints. Using web content filtering, the admin can filter any websites or domains that pose a threat to endpoint security. All the admin needs to do is log in to the Hexnode Web portal and blacklist/whitelist the Web URLs as required while configuring the policy assigned to the Mac devices.
What does 2020 bring or Mac security?
The Apple WWDC event this year brought with it many wonderful features that would increase the endpoint security for Mac devices. We have discussed a few here:
Lights Out Management for Mac Pro
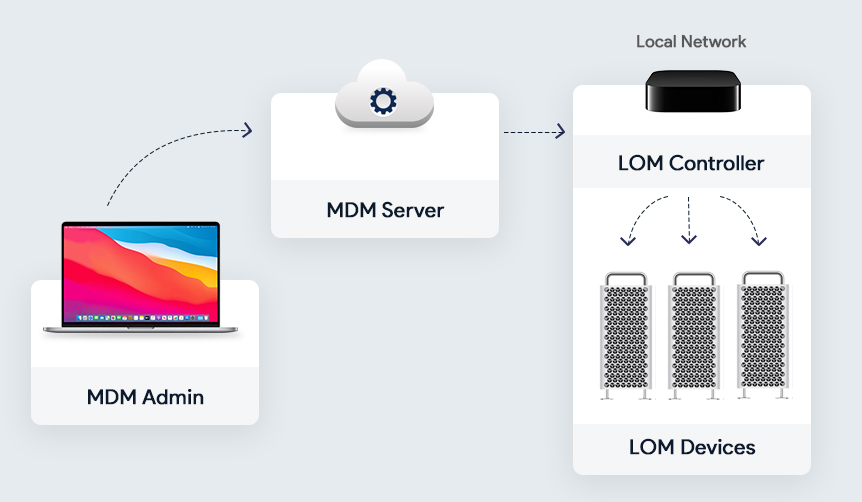
The admins can remotely startup, reboot, or shut down one or more Macs even if they are unresponsive. The task is accomplished by sending a command from the MDM server to the MDM-enrolled controller on the Mac network. Lights Out Management requires macOS Big Sur, the Macbook Pros to be on the same subnet, and the Lights Out Management Payload to be installed. The remote control of the macOS devices given to the admins by LOM helps to secure the devices
Supervision for User Approved MDM
Earlier, only the macOS devices enrolled using the Apple Business Manager account could be supervised. The admins can now query, list, and delete local users, control Activation Lock Bypass, install supervised restrictions profile using MDM, or even schedule software updates in even user-enrolled Macs.
Bootstrap Tokens
Bootstrap tokens are encryption keys provided by the MDM server used to create admin accounts in the macOS devices without using a password for authentication. Instead of using complicated workflows for creating the admin account and user accounts, the bootstrap token enables users to get a secure token and boot a Mac that uses FileVault. This is a coveted feature for network accounts. The admins can take advantage of authorized software updates and kernel extensions once this is implemented. Bootstrap tokens are supported on all the latest Macs with Apple T2 Security Chip.
Preventing accidental installations of downloaded profiles
For protection against the accidental installation of potentially harmful profiles, the downloaded profiles have to be manually installed by the user. To install the downloaded profile, the user has to go to the device System Preferences > Profiles > Downloaded Profiles and install the profile using the user password after previewing it.
Preventing silent profile installs from the command line
For enhanced security, complete silent installation of profile using the terminal would no longer be supported from macOS Big Sur. The profiles to be installed using the terminal would be treated as a downloaded profile. The user would have to go manually to the System Preferences and install the profile just like with a downloaded profile.
Format change for Serial Numbers
Serial numbers of the Mac devices serve not only as unique identifiers but also for automated device enrollment. The existing 12-digit serial numbers contain bits of identifiable information such as where and when the device is built. To prevent malicious use of identifiable data, Apple will now use completely random 10-character serial numbers.
The year 2020 has been a golden year for Mac endpoint security. With the realization that Mac is not immune to security threats, measures have been taken to keep Mac devices still the best option when it comes to endpoint security. For business and individual users alike, Mac endpoint security was somewhat of a blind spot due to either lack of knowledge or the lack of proper tools. With Macs steadily making its mark in the business world, it is now time to focus on strengthening the endpoint security using an MDM solution that keeps evolving with updated features.






