Overcoming Modern Enterprise Security Crises with Hexnode IdP
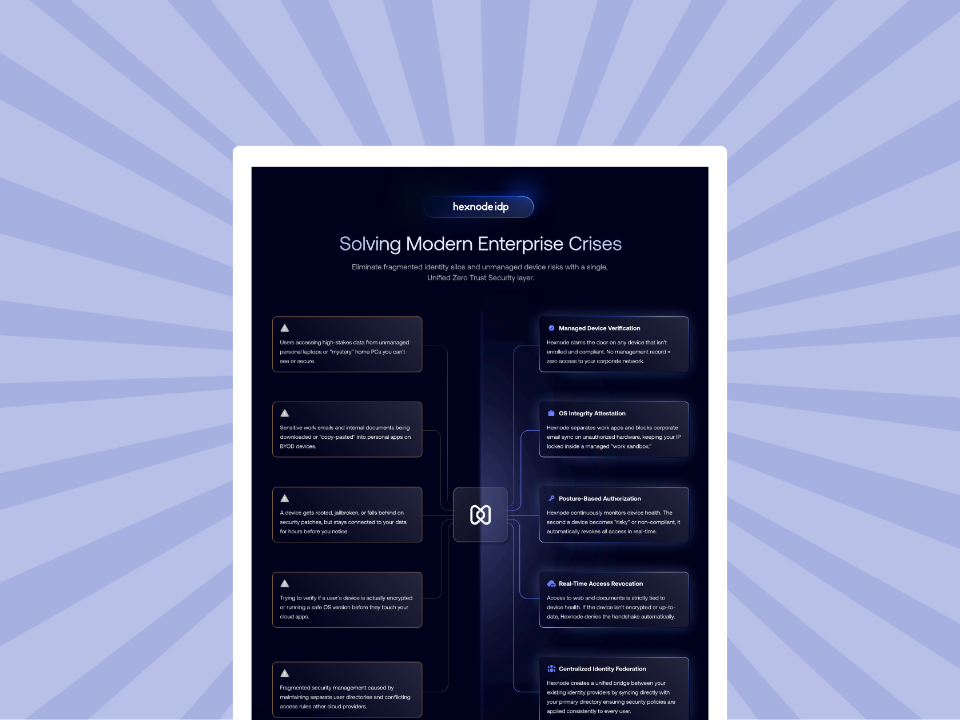
Addressing fragmented identity silos and unmanaged device risks requires a single, unified security layer. Hexnode IdP mitigates enterprise crises by ensuring that any device lacking a management record is strictly denied access to the corporate network. Through posture-based authorization, the platform continuously monitors health to automatically revoke access if a device becomes rooted, jailbroken, or non-compliant.
Whether preventing intellectual property leaks on BYOD hardware via work sandboxing or verifying encryption status before granting cloud access, Hexnode provides real-time enforcement tied to OS integrity. By utilizing centralized identity federation, organizations maintain consistent security policies across every user and directory, ensuring mystery home PCs no longer compromise high-stakes data.