In 2026, the password is dead. We just haven’t finished burying it yet.
For decades, we relied on “shared secrets” (passwords) to prove identity. But today, where 81% of data breaches involve stolen or weak credentials, the shared secret is a liability. If a user knows it, a hacker can phish it.
The future of authentication is Asymmetric Cryptography, specifically, Public Key Infrastructure (PKI). Instead of a user typing a password, their device presents a Digital Certificate. It is un-phishable, unique to the hardware, and invisible to the user.
However, for enterprises, the challenge isn’t why to use certificates; it’s how to deploy 50,000 of them to a fleet of iPhones, Androids, and Windows laptops without the help of a team of 20 manual administrators.
This guide decodes SCEP vs NDES, explains the architecture of automated certificate delivery via Hexnode UEM, and looks at the future of ACME (Automated Certificate Management Environment) and Device Attestation.
- Core Components of MDM Certificate-Based Authentication
- The Architecture: How SCEP & NDES Work Together
- The Technical Handshake:
- Why NDES Often Fails (And How to Fix It)
- The Over-Privilege Pitfall
- The “Too Much Info” Error
- The “Name” Mix-up
- The Hexnode Solution: Automating the Pipeline
- Data Protection with Hexnode
- 5 ways to enhance data protection with Hexnode
- Beyond SCEP: The Future of PKI
- The ROI of SCEP
- Conclusion: Identity is the New Perimeter
- Try Hexnode free for 14 days
- Frequently Asked Questions (FAQ)
Core Components of MDM Certificate-Based Authentication
Let’s define the components of the PKI framework.
- PKI (Public Key Infrastructure): The total system of hardware, software, and policies that manages digital certificates.
- CA (Certificate Authority): The “Bank” that issues the identity documents. In most Microsoft shops, this is AD CS (Active Directory Certificate Services). The CA acts as the “Root of Trust”; if the CA signs a certificate, every other device in your organization automatically trusts it.
- SCEP (Simple Certificate Enrollment Protocol): The language devices use to ask for a certificate. Think of it as the “application form” the device fills out.
- NDES (Network Device Enrollment Service): The “Receptionist.” It sits between the dangerous public internet (where your mobile devices are) and your secure internal CA. It validates the request and passes it to the Bank.
The Architecture: How SCEP & NDES Work Together
The goal is simple: Get a unique, trusted security certificate from your internal, air-gapped Server onto a remote device, like an iPad in a coffee shop, without the user doing a thing.
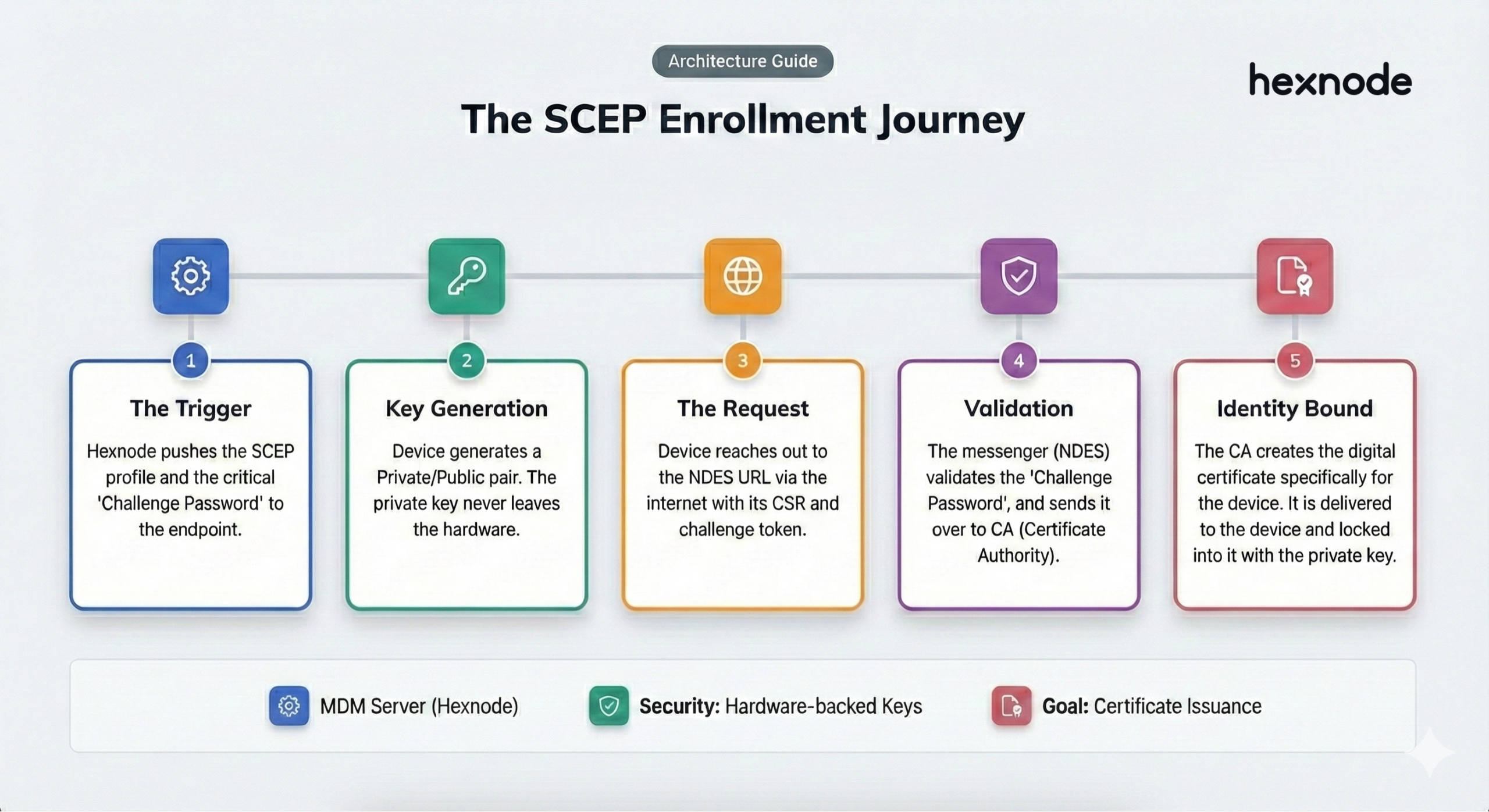
The Technical Handshake:
- The Trigger: Hexnode pushes a SCEP Profile to the device. This is the “instruction manual.” It tells the device exactly where your NDES server is located and gives it a Challenge Password, a one-time-use secret code that proves the request is coming from a managed, authorized device.
- The Key Generation: Before sending anything, the device creates its own Private Key and Public Key. The Private Key stays hidden deep in the device’s secure hardware (it never travels over the internet). The device then prepares a request containing the Public Key and that secret Challenge Password.
- The Request: The device “calls” the NDES Server over the internet and submits its request.
- The Validation: NDES acts as the Gatekeeper. It looks at the Challenge Password. If the password matches what the MDM expected, NDES knows the request is legitimate. It then passes this request over to your internal Certificate Authority (CA).
- The Issuance: The CA (the “Bank”) verifies that the NDES server is allowed to make requests. It then “mints” (creates) the digital certificate specifically for that device.
- The Delivery: The CA hands the certificate back to NDES, which then passes it back across the internet to the device.
- The Final Bind: The device receives the certificate and mathematically “locks” it to the Private Key it created in step two.
The Result: The device is now “ID-verified.” When the user tries to join the Office Wi-Fi or a VPN, the device simply shows this certificate. No passwords, no prompts, just instant, secure access.
Why NDES Often Fails (And How to Fix It)
Setting up NDES is tricky. Most failures come down to three specific problems. Here is how to avoid them.
-
The Over-Privilege Pitfall
Admins often get frustrated when the connection fails and give the NDES service account Domain Admin rights just to “make it work.”
- The Mistake: Over-privileging the account.
- The Risk: Since the NDES server is open to the internet, a single hack could give an attacker the keys to your entire kingdom.
- The Fix: Stay disciplined. Use a dedicated account that has only three specific “VIP” passes: Logon as a Service, Read/Enroll on your template, and Request Certificates on the CA.
-
The “Too Much Info” Error
SCEP requests could be very long and complicated. By default, the NDES (IIS) isn’t allowed to read orders that are too long.
- The Symptom: You see a 404.15 error (URL Too Long).
- The Secret: The default limit is 2,048 characters, but SCEP needs way more.
- The Fix: Go into your IIS settings and “widen the pipe.” Set the character limit to 65,534. This gives the long SCEP messages plenty of room to pass through.
-
The “Name” Mix-up
NDES is a stickler for names. It has a specific “address book” (the Windows Registry) where it looks for the name of your certificate.
- The Symptom: Everything looks right, but you get a 500 Error or an “Incorrect Password” message.
- The Catch: There is a difference between a template’s Display Name (e.g., Hexnode Wi-Fi) and its Actual Name (e.g., HexnodeWiFi).
- The Fix: Go to your Registry settings and make the MSCEP keys match the Actual Name exactly. If there is a space or a typo, the whole thing breaks.
The Hexnode Solution: Automating the Pipeline
In a manual SCEP setup, you have to generate a static challenge password and manually input it. That is insecure and a nightmare to scale. Hexnode uses Dynamic SCEP to handle the heavy lifting.
How We Integrate:
- Hexnode AD CS Connector (aka Hexnode Cloud Broker): You install the lightweight Hexnode Cloud Broker on a Windows Server within your network. This creates a secure, outbound-only bridge between the Hexnode Cloud and your Certificate Authority.
- Dynamic Challenge: When a device requests a certificate, Hexnode doesn’t use a “forever” password. It communicates through the connector to your AD CS to generate a unique, one-time challenge password specifically for that one request.
- Zero Touch: The user does nothing. The policy lands on the device, the certificate negotiation happens in the background via the connector, and the certificate is installed silently.

Data Protection with Hexnode
5 ways to enhance data protection with Hexnode
Security solutions are often viewed as an expensive add-on. Check out the highlighted features Hexnode implements to keep your data secure.
Download the InfographicBeyond SCEP: The Future of PKI
While SCEP is an industry standard now widely used, the future of Enterprise PKI is moving toward more robust, automated protocols.
- ACME (Automated Certificate Management Environment)
Popularized by Let’s Encrypt, ACME is superior to SCEP because it handles Revocation and Renewal much better.- The Shift: While SCEP is great for “getting” a cert, ACME is better at “managing” the lifecycle. We are seeing a trend where modern servers and IoT devices prefer ACME for its lightweight verification challenges.
- EST (Enrollment over Secure Transport)
Think of EST as “SCEP 2.0.” It uses TLS for the transport layer, making it more secure and firewall-friendly than the messy HTTP GET requests of SCEP. It also supports ECC (Elliptic Curve Cryptography) certs more natively, which are faster and stronger than legacy RSA keys. - Apple’s Managed Device Attestation
This is the game-changer. Instead of just asking “Does this device have a certificate?”, Apple’s new ACME-based service allows the device to prove “I am a genuine Apple device, and I have not been modified.“- The Impact: The private key is generated in the Secure Enclave (hardware) and attested by Apple’s servers. This effectively kills “Identity Cloning” attacks where hackers steal certs to put on unauthorized laptops.
The ROI of SCEP
You are not just deploying certificates; you are deploying Velocity.
- Eliminate Password Reset Tickets: 30% of Helpdesk volume is password resets. Cert-based auth (CBA) removes the password entirely.
- Kill the Phish: You cannot phish a private key stored in a TPM chip. Moving to CBA instantly neutralizes the #1 attack vector for ransomware.
- Invisible Security: Security usually adds friction. PKI removes it. The user opens their laptop, and the VPN is just “Connected.” No prompts, no friction, no complaints.
Conclusion: Identity is the New Perimeter
In a Zero Trust world, the network firewall is irrelevant. The only thing that matters is: “Can I trust this device?“
By integrating Hexnode with your Enterprise PKI (via SCEP/NDES today, and ACME tomorrow), you are building the only perimeter that holds up in a cloud-first world. You are turning every device into its own fortress, authenticated by math, not memory.
Try Hexnode free for 14 days
Ready to Go Passwordless? Learn how to configure the Hexnode Cloud Broker and deploy your first SCEP profile today.
Sign Up TodayFrequently Asked Questions (FAQ)
Q: What is the difference between SCEP and NDES?
A: SCEP (Simple Certificate Enrollment Protocol) is the language/protocol devices use to request a digital certificate. NDES (Network Device Enrollment Service) is the Microsoft server role that acts as the gateway/proxy, receiving the SCEP request from the device and forwarding it to the internal Certificate Authority (CA) for fulfillment.
Q: Why use Certificate-Based Authentication (CBA) over passwords?
A: CBA offers superior security and user experience. Unlike passwords, certificates cannot be guessed, shared, or phished. They enable “Zero Touch” access to Wi-Fi and VPNs, eliminating password reset tickets and preventing credential theft attacks, which account for 81% of breaches.
Q: What is the future of SCEP in Enterprise PKI?
A: While SCEP is the current standard, the industry is moving toward ACME (Automated Certificate Management Environment) and Device Attestation. These newer protocols offer better lifecycle management (automated revocation/renewal) and hardware-backed proof of identity (attesting that keys are stored in the Secure Enclave), offering higher trust assurance than SCEP.

