What is Windows kiosk mode?
Windows Kiosk Mode: Learn its benefits, features, and how it secures single-purpose devices for business.

Get fresh insights, pro tips, and thought starters–only the best of posts for you.
Estella Pocket
Nov 14, 2025
10 min read

Windows kiosk security hardens public or shared devices by strictly locking them into single or multi-app mode, restricting unauthorized user access, and enforcing strict security policies. Native controls can be effective but are insufficient; true enterprise protection requires a UEM solution to prevent keyboard shortcuts and secure hardware.
Hexnode UEM simplifies enterprise-grade windows kiosk security. It ensures deep device lockdown, prevents hotkey breakouts, and allows remote management for compliance. The actionable step is deploying a UEM to block all non-kiosk applications.
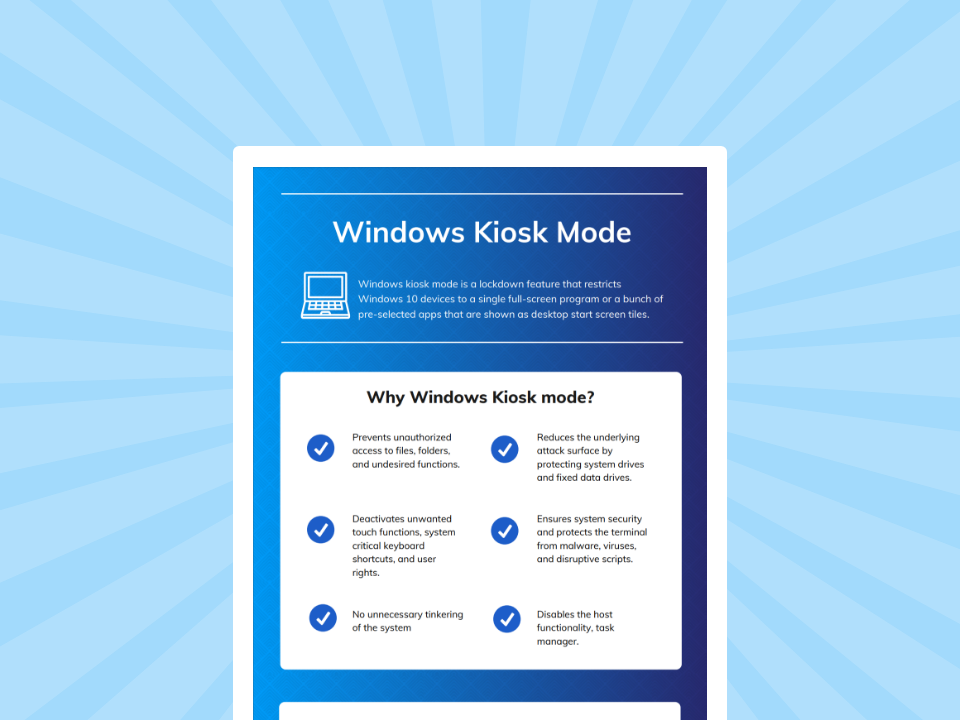
Increasing the security of our devices is critical to prevent unauthorized access and maintain operational integrity in shared settings. This is why we need Windows kiosk mode security. It makes sure that the environment is locked down by restricting user interaction to a predefined set of applications or functions.
Locking down the device to a predefined set of functions is the main concept of Windows kiosk mode. A specific configuration managed through Windows Assigned Access or Shell Launcher strictly limits a device to one specific app or set of functions.
From being used for digital signage in retail and in hospitality for patient information systems and in logistics, kiosk devices are essential in modern enterprise operations.
The usability of a kiosk device is equal to its security risk. So, an unsecured kiosk is the prime target for security breaches. While Windows provides top-notch native features, some gaps persist. Common risks due to these gaps could be unauthorized access, data theft, malware injection.
Over 60% of organizations’ surveys reported an insider incident involving unsecured shared devices in the past year, underscoring the urgency.
To resolve this, the essential step for every IT admin is to utilize an effective UEM solution to suppress OS-level shortcuts and lock physical ports.
With Hexnode UEM, you can swiftly deploy multi-layered security profiles like HIPAA and PCI-DSS, blocking all shortcut attempts and securing peripherals from a single console, simplifying enterprise-wide deployments drastically.
The built-in risks in a Windows kiosk deployment come from the device’s public accessibility, which hackers can exploit to get through the restricted environment. These vulnerabilities basically fall into three categories – unauthorized access, network threats, and critical policy misconfigurations.
The single most threatening thing to windows kiosk security is the risk of a “breakout.”
Ready to secure your Windows devices? Lock them down instantly with Hexnode UEM's Kiosk Mode, preventing unauthorized access and data breaches.
Download InfographicMany security failures that we know of are by preventable configuration errors:
With Hexnode UEM, you can manage the entire risk surface, centrally. The platform simplifies the deployment of granular controls to instantly block hotkeys, enforce strict USB port restrictions, and policy compliance across thousands of devices.
Hardening Windows kiosk security requires a multi-layered strategy that focuses on minimizing the attack surface, controlling user permissions.
Adopting industry-standard best practices like the below topics and using a solid UEM solution ensures that kiosks in public remain locked down, compliant, and protected against unauthorized usage.

Windows laptop in kiosk mode
Hexnode UEM elevates Windows kiosk security beyond native OS limitations by providing a dedicated, centralized management console to implement deep-level lockdown policies and maintain uninterrupted compliance.
Here we’re going to see some of Hexnode’s specialized tools:
The huge scale of enterprise deployments makes manual configuration an impossible security risk.
Hexnode UEM provides the power to configure kiosk mode remotely for your entire fleet of devices. From the centralized Hexnode console, you can easily choose single- or multi-app kiosk settings, defining exactly what users can access and launch. This allows for immediate deployment of granular, location-specific policies.
While the native Windows kiosk features are functional they mostly lack the granular security required in public settings.
Advanced security management features of Hexnode allows the user to completely restrict unauthorized access by enforcing deep-level lockdown profiles that disable the taskbar and start menu, and most critically, suppress all breakout keyboard shortcuts (e.g., the Windows key or the ALT+TAB).
To ensure operational continuity, the watchdog policies monitor the kiosk app and automatically relaunches it instantly in the event of a crash or intentional exit attempt.
The essential actionable step is to deploy an app whitelisting policy through the Hexnode console to lock down the devices, ensuring only the primary kiosk application to be executable.

Windows kiosk laptops used in management
Security requires continuous vigilance and Hexnode provides comprehensive remote monitoring and compliance tools.
By centrally hardening your Windows kiosk fleet, you go from reactive troubleshooting to proactive security management, ensuring reliability and a positive customer experience.
Hardened kiosks deliver immediate and measurable improvements:
Relying on native Windows kiosk features as is can be risky down to the fundamental level. Absolute windows kiosk security hardening requires a unified tool like Hexnode UEM to implement granular registry-level and hardware-level policies remotely, a complexity that is also visible when managing devices in a browser lockdown scenario.
Ready to prevent Windows kiosk breakouts?
What is the best way to secure Windows kiosk mode?
Use a UEM like Hexnode to enforce kiosk mode policies remotely. Restrict access to authorized apps, disable hotkeys, limit network and USB usage, and ensure regular OS patching for airtight protection.
Can I manage multiple Windows kiosks remotely?
Yes. With Hexnode UEM, IT admins can configure, monitor, and update kiosk devices from a single dashboard. It allows policy grouping, automated patching, and real-time device tracking across large deployments.
Give your Windows device unbreakable security. Start your 14-day free trial now.
Signup now!