HexCon23 Opening Keynote: Championing Growth
Unveil the 4th edition, HexCon23 with our board of directors as they outline Hexnode’s roadmap for the future.

Get fresh insights, pro tips, and thought starters–only the best of posts for you.

HexCon23 kicked off with a bang, featuring a lineup of distinguished industry leaders who delved into pressing topics in the cybersecurity and tech field. Our speakers shared their insights and expertise on themes such as the transformative power of artificial intelligence and fortifying endpoint security.
In case you missed it, here’s a brief rundown of HexCon23 Day 1:
HexCon returns for an exciting three-day cybersecurity event, packed with informative discussions and insights on the latest trends in cybersecurity. The event commenced with an impactful keynote address delivered by the founders. Apu Pavithran, the CEO, touched on the increasing significance of Unified Endpoint Management (UEM).

He underscored the pivotal role it plays in shaping modern business strategies and emphasized its growing relevance in today’s rapidly evolving digital landscape. This year, HexCon has chosen the theme of “Championing Growth”. Rachana Vijayan, the Chief Marketing Officer, proudly unveiled “Hexnode Connect,” an innovative forum aimed at assembling a community of cybersecurity experts and IT administrators.
Hexnode Connect represents a dedicated platform designed to facilitate knowledge sharing, problem-solving, and meaningful connections within the cybersecurity and IT admin community. Bijo Paulose, the COO, addressed the audience on the topic of enhancing digital employee experience. During his presentation, he unveiled an exciting development at Hexnode Access – the introduction of a cutting-edge feature that offers a secure method for logging into macOS devices.
This feature enables users to sign in using cloud-based identities such as Microsoft Azure AD and Google Workspace, ensuring a streamlined and secure authentication process for Hexnode users. Sahad, the CTO, also mentioned that macOS administrators can now seamlessly synchronize and manage all local user accounts. This includes the ability to access comprehensive and detailed information about each user account, as well as the capability to execute remote actions on them. More developments are on the horizon! Hexnode is set to introduce Windows Autopilot, a zero-touch enrollment experience for Windows device fleets. In addition, Hexnode is coming up with its own suite of applications to access work email, calendar & contacts! Much more; Automated scripts for Mac administrators, and integrations with Drata, Vanta, and Check Point were also announced! With these updates in place, HexCon23 officially commenced, promising an engaging and informative experience for attendees!
Christopher Sherman, Principal Analyst at Coherent Strategies, emphasized the critical importance of aligning endpoint security with device management to mitigate internal IT friction and enhance overall cybersecurity. He began by highlighting how employee devices can serve as vulnerable entry points for cyber attackers, and the challenges posed by security tools only intensify the urgency for alignment.
Sherman stressed that effective device security and management are two inseparable aspects of the same coin. Poor alignment between IT operations and security teams, combined with the proliferation of technologies in less controlled environments, creates vulnerabilities that must be addressed. The reasons for aligning device security and management are multifaceted. This alignment serves as a potent defense against malware propagation, enhances data awareness, reduces security agent fatigue, improves network visibility, and accelerates breach detection.
Sherman reinforced his insights with real-world case studies, illustrating the tangible benefits of this alignment. He recommended three key strategies:
In conclusion, Christopher Sherman’s presentation highlights the paramount importance of harmonizing endpoint security and device management to strengthen organizational cybersecurity defenses, ultimately ensuring a more resilient and proactive approach to cyber threats.
The session commenced with Scott Giordano highlighting the positive aspect of competition within the AI field, a sentiment that was echoed by Megha Khalsi. Mark emphasized that tech giants leverage their resources, such as cloud services and GPUs, to drive innovation internally.
Taimur raised a crucial point about the security risks associated with generative AI tools like Chat GPT, as they can inadvertently expose sensitive information like meeting minutes and source codes. He advocated for privacy options that allow users to opt out of using their data for training such tools.
Megha expressed support for AI-powered data loss prevention tools, while Mark discussed the potential of feeding decision algorithms to automate tasks, like enhancing firewall protection.
Scott shifted the conversation to the impending EU AI regulations, set to take effect in the next six months, which carry penalties of up to 7% of annual gross revenue for violations. There will be a two-year grace period for compliance.
Megha emphasized the importance of embedding security throughout the AI/ML model development process, conducting regular privacy and security audits, and performing risk assessments for AI products.
Scott highlighted that in the USA, the FTC will oversee AI-related administration, with the SEC responsible for public companies. Additionally, individual states are also expected to enact AI-related laws.
Megha raised concerns about the use of AI, particularly GPT, by cybercriminals to create malware. Worm GPT poses a significant threat in this regard.
The session concluded with all speakers sharing their positive experiences with AI, underlining its utility and potential benefits in various contexts.
Securing digital services is of paramount importance in today’s interconnected world, as these services underpin our daily lives, from online banking and healthcare to communication and commerce. Mike Nelson, Global VP of Digital Trust at Digicert, kicked off the session by shedding light on how to ensure the integrity, availability, and privacy of digital assets.
As our lives increasingly migrate online, concerns about safeguarding our digital assets grow. The frequency of data breaches and cyberattacks in the headlines raises anxiety about the theft of our personal information. Mike also cited several cyber incidents that have wrought havoc in the digital world, such as the Equifax data breach in 2017. Nonetheless, all these cybersecurity breaches can be averted with the right security approaches.
Trust in the digital realm is incredibly important in today’s highly interconnected world. Without it, utilizing services like online shopping, social media, or healthcare apps could become risky and uncertain. On the other hand, a robust digital trust architecture can fuel real-world innovation across various sectors, including infrastructure, healthcare, and government.
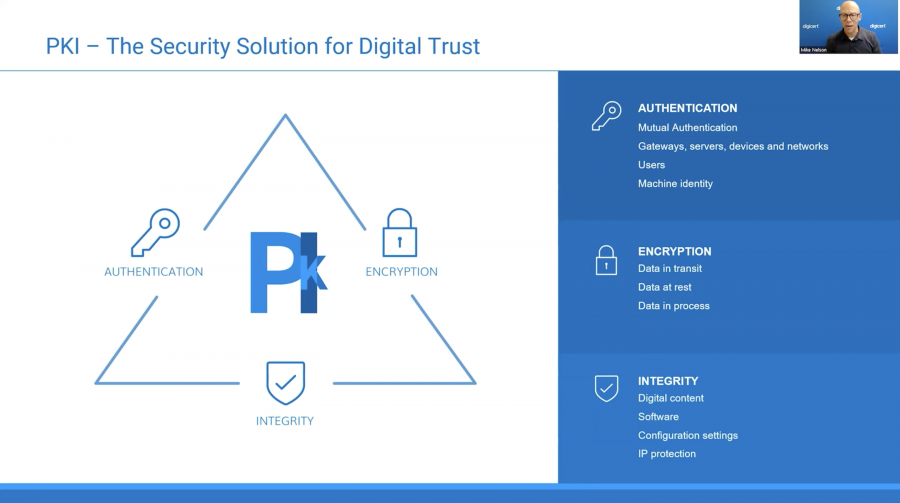
The outcomes of digital trust are far-reaching. They grant us greater visibility and control over data breaches, ensuring that another Equifax incident does not occur. Additionally, they furnish us with authenticated and tamper-proof content, along with secure software supply chains.
Bradley Chambers predicts that Apple will ascend to the top position in the endpoint market by 2030. To prepare for this shift, he advocates for IT professionals to become experts in using Apple devices, emphasizing that CTOs and CISOs should invest in training programs. He points to Apple’s game-changing move in 2020 with the introduction of silicon, which sig.nificantly impacted the industry. Chambers states that Apple has already acquired a substantial market share and anticipates its domination by 2030. He explains the synergy between security and productivity, highlighting an example of passkeys on Mac login pages. He encourages IT administrators not to confine Macs to kiosk-like setups but rather to explore their full potential, as Mac devices often offer 1-2 years of additional usability compared to other devices.
In the context of a booming Software as a Service (SaaS) landscape, Chambers suggests building solutions around zero-touch deployment. He concludes by recommending the utilization of passkeys as a foundation for bolstering security measures. In essence, Bradley Chambers envisions a future where Apple’s endpoint dominance is imminent, and IT professionals should proactively adapt, embrace, and harness the unique advantages offered by Apple devices while emphasizing the integration of security and user experience.
James Potter outlines a three-step process for understanding how compromises occur within an organization’s network. First, there’s the potential for a domain controller breach, which can serve as the initial entry point for attackers. Following this, attackers often seek to move from a child domain to the root domain, gaining access to higher levels of control and sensitive data. Finally, the compromise of a child domain can occur, which can further exacerbate the security breach.
To mitigate these risks, Potter recommends implementing a tiered approach for account and device isolation. This involves categorizing users and devices into different tiers based on their roles and privileges. By doing so, organizations gain a clear understanding of who occupies each tier, facilitating better control and management of access rights. Potter also introduces the concept of grouping Role-Based Access Control (RBAC) role groups into Universal Role Assignment (URA). This approach ensures that even if an account is compromised, it won’t possess the ability to elevate its own privileges, adding an extra layer of security. Furthermore, Potter advocates for the adoption of a bastion forest, which can establish a Zero Trust security model without requiring additional subscriptions.
Interestingly, having a bastion environment can also lead to lower premiums from cyber insurance providers, as it demonstrates a commitment to robust security measures, reducing the overall risk profile for the organization. In essence, James Potter’s insights emphasize the importance of a strategic and layered approach to security, which includes understanding the stages of compromise, implementing role-based access control, and considering bastion forest environments to enhance cybersecurity and potentially reduce insurance costs.
Mark A. Houpt, the Chief Information Security Officer at DataBank, is an IT security expert with over three decades of experience in the field. In this session, he delved deeply into the intricate relationship between Artificial Intelligence and cyber threat protection.
He began by discussing the history of both ransomware and AI. Ransomware, which first emerged in the 1980s, has evolved into numerous lethal forms, such as Cryptowall and Double Extortion attacks.
Security functions and services solely reliant on AI can be helpful but should not be considered our ultimate solution.
Mark explained that Artificial Intelligence cannot generate ransomware or other malware attacks; its role is primarily that of a threat amplifier. Threat actors may leverage AI to devise new deceptive techniques, employ complex encryptions, and utilize sophisticated attack vectors. AI can also shift attacks to different servers by automatically detecting their vulnerabilities.
However, when used responsibly, AI can prove to be invaluable for rapidly identifying ransomware infections and isolating them within containers. Here are some ways in which AI can help mitigate security risks:
Mark also shared insights on how to use AI responsibly and concluded the session by providing instructions for viewers on where to seek help if they fall victim to a ransomware attack.
Rinki Sethi, a prominent figure in the world of cybersecurity, has offered valuable insights into the evolution of cybersecurity over the last two decades. She started off by discussing the concept of a Security Champions Program, an approach includes investing in training for employees within various departments, with the security team identifying individuals who exhibit a strong passion for cybersecurity, and subsequently providing them with specialized training. Rinki spoke of the importance of executives to champion the program. She emphasized the importance of a Chief Information Security Officer (CISO), noting that this role is frequently underestimated or absent in many organizations.
Drawing from her experience at eBay, she highlighted how it exposed her to the intricate and sometimes malicious work of hackers. Furthermore, Rinki pointed out that a proficient CISO should excel in articulating cybersecurity risks, possess strong communication skills, and have a unique combination of technical and business expertise. The big organizations have always placed huge importance on championing security, but Rinki says that of late, it is common for even the small organizations to have Security Champions Programs in place. Nation-state cyberattacks are occurring more often in today’s digital age. Rinki has emphasized that third-party vendors can play a crucial role in fortifying defenses against such attacks. These cyber intrusions often stem from successful phishing scams that unsuspecting employees fall prey to. To address this issue, organizations must:
She mentioned how it is advantageous to work with multiple vendors since each vendor possesses a unique and specialized skill set. Rinki’s concluded by mentioning her staunch support for promoting diversity within the industry. She actively championed the cause of inclusivity and worked diligently to ensure that people from various backgrounds and underrepresented groups were given equal opportunities and recognition in the field.
Enterprises often overlook the critical aspect of comprehensive Software as a Service (SaaS) management. In this regard, Jiby Joseph, Product Analyst at Hexnode, provided valuable insights into what enterprises should consider within the SaaSOps domain.
Inefficient management of SaaS apps can result in efficiency losses and increased expenditures for organizations. However, if you have a capable SaaS management tool, it can help enhance the employee experience while also safeguarding your app data.
Generative AI refers to a type of artificial intelligence with the capability to generate new content, such as text, images, or other data, by learning from existing examples and producing novel outputs based on learned patterns and information. However, it raises concerns regarding potential breaches of privacy regulations.
During their session, Kara Larson, Assistant General Counsel at 6sense, and Mae Beth, Deputy Chief Privacy Officer at Northrop Grumman, discussed how to navigate the risks associated with Generative AI and how to ensure a secure future with this technology. They began by addressing privacy risks linked to Generative AI, acknowledging that it is still in its early stages, with instances of model memorization (repeating examples from training data) observed in poorly regulated models. Additionally, the deletion of subject data used for training Generative AI poses significant challenges.
However, the mitigation methods available today closely resemble existing frameworks for privacy protection:
In addition to these measures, organizations must establish a governing policy regarding the use of AI and educate personnel on its acceptable use. Utilizing a closed model trained with first or zero-party data is another crucial step in minimizing privacy risks.
Kara and Mae concluded the session by emphasizing the necessity of a uniform regulatory framework. They stressed that meaningful regulation should strike a balance between risks and the benefits to individuals or companies.
Samuel Mbonu, President of ISC2 Nigeria Chapter, delivered an insightful session on the current challenges in the cybersecurity space and the significance of AI and ML in addressing these challenges.
Cybersecurity can be defined as the protection of internet-connected systems, including hardware, software, and data, from cyberthreats.
Samuel highlighted the escalating frequency and complexity of cyber threats in recent times, which is propelling the growth of AI in the cybersecurity market. He emphasized the necessity for more than just human intervention to analyze and enhance an organization’s cybersecurity posture.
According to Samuel, AI-based cybersecurity systems can play a pivotal role in threat exposure and incident response. AI can also facilitate an understanding of the strengths and weaknesses of an organization’s information security programs. However, it’s crucial to acknowledge that AI cannot be rendered unconditionally safe. It can be exploited and misused by cybercriminals. Just as AI serves defensive purposes, hackers can leverage AI to penetrate defenses and create mutating malware that alters its structure to evade detection.
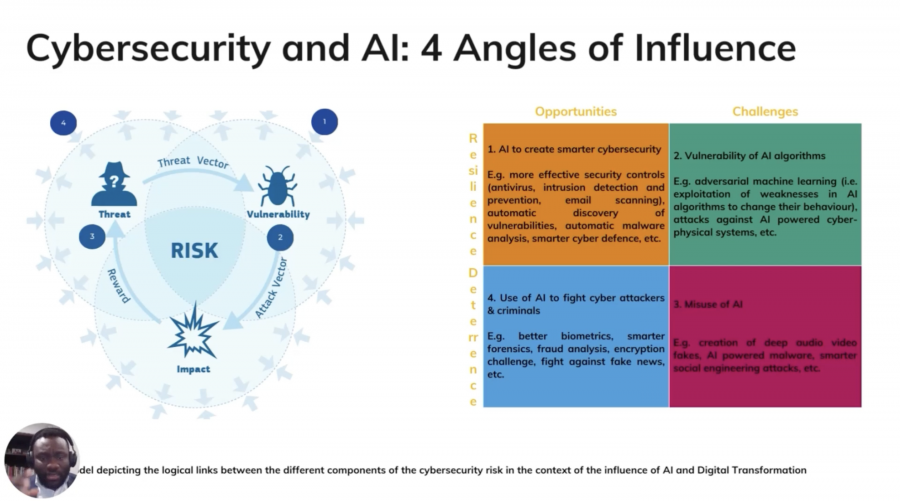
Samuel summarized the session by emphasizing the importance of establishing safeguards to prevent AI from working against us. Regularly assessing the configurations of devices and applications, as well as monitoring other aspects of an organization’s cybersecurity infrastructure not directly related to artificial intelligence tools, is essential.
The session started off with Danni reflecting on her wonderful experience at last year’s HexCon. She then delved into her career journey, which initially led her to the elite cover unit of the police force. In this role, she became well-acquainted with the world of cyberattacks and their techniques. Danni emphasized a startling statistic: 98% of all cyberattacks rely on social engineering tactics. She stressed that confidence is the key to tricking and deceiving individuals into divulging sensitive information. Furthermore, she highlighted the alarming scale of cybercrime, noting that if it were measured as a country, it would constitute the world’s largest economy. This stark reality translates into the average business facing as many as 700 social engineering attacks.
She explained the tactics hackers use, which mostly involves blackmailing people through potential exposure of their secrets. Danni explained how hackers manipulate, influence, and deceive users to achieve their goals.
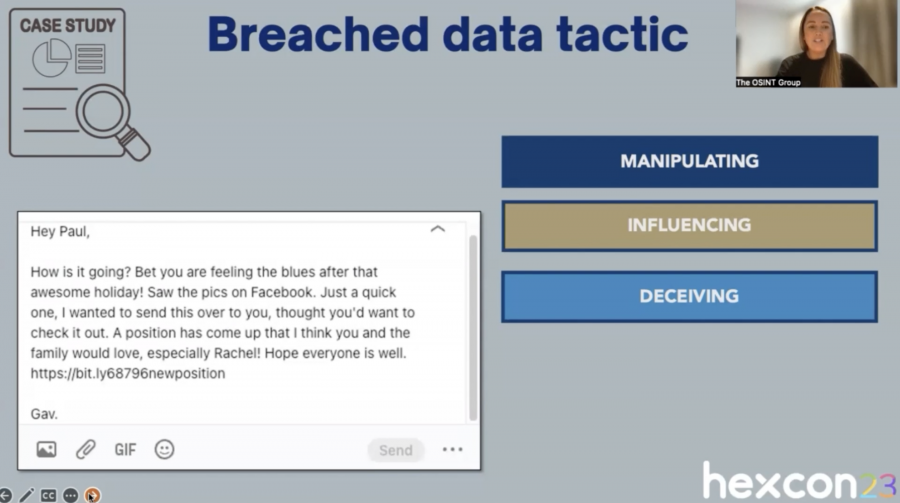
In conclusion, Danni’s presentation underscored the pervasive threat of social engineering in the world of cybercrime and provided actionable steps for individuals and businesses to bolster their cybersecurity defenses.
Ever heard of OSINT? Open Source Intelligence, commonly known as OSINT, refers to gathering information from publicly available sources. It encompasses a wide range of data, from social media posts and news articles to satellite imagery and public records. Now imagine sifting through this ocean of data to find that one teeny-tiny thing you want! This, right here, is where AI, artificial intelligence, steps in.
The CEO of SecPro Security Professionals, David Pereira, helmed an insightful session on the applications of AI in OSINT (Open Source Intelligence). The man had us all intrigued and hanging on to every single one of his words from the get-go. From kick-starting the session with a bold statement…
AI is not as precise as people think. It makes mistakes.
…to dropping hints on how to handle prompt engineering, the session was, indeed, the right mix of information overload and curiosity piquing.
Pereira mentioned that the key to using AI for specific purposes with precision is to ‘ask gently.’ Here’s a quick rundown of the pointers
There are, at least, some of us who think that the field of AI has only gained traction in the last couple of years, what with the popularity of ChatGPT and all. Well, we couldn’t have been further from the truth. Remember how reverse image search first astounded us almost a decade ago? AI has been on the center stage for quite some time now. Just as David mentioned in his session, the application of AI for OSINT is far-reaching. Here are some of the applications that the expert mentioned.
In the discussion about Endpoint Detection and Response (EDR), Partha introduces the four key steps involved in EDR processes.
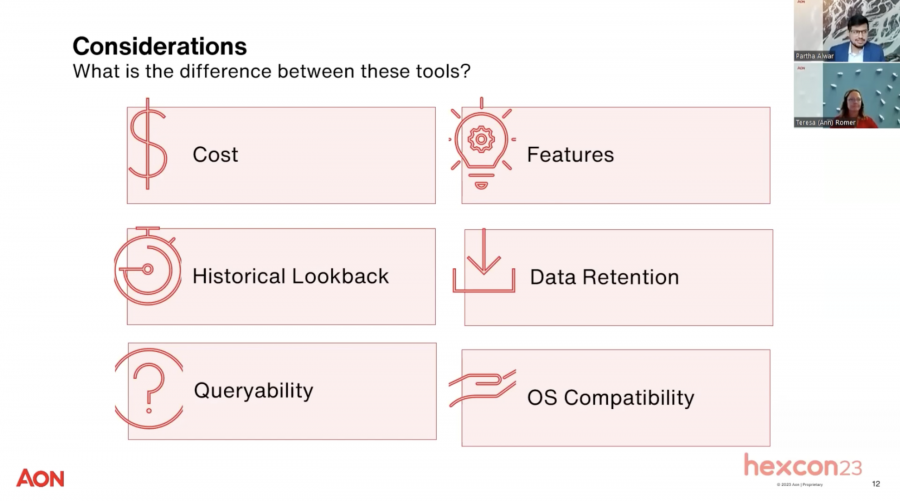
Ann highlights some common missteps in EDR configuration. First, there is often an issue with not installing the EDR console widely enough, which can limit its effectiveness. Second, failing to enable Multi-Factor Authentication (MFA) on the EDR console can leave it vulnerable. Third, not implementing access limits on who can use the console can lead to security concerns. Finally, inadequate staff training can result in inefficient EDR operation.
In conclusion, Partha and Ann stress the importance of auditing user roles granted within the EDR console. They emphasize the need for fine-tuning EDR systems to ensure they operate optimally. Proper training for EDR console operators is also essential to make the most of the EDR capabilities and enhance overall cybersecurity posture. Ultimately, their message underscores the critical role that proper configuration and training play in the effective utilization of EDR for threat detection and response.
That concludes our agenda for today. But don’t worry! Day 2 is coming up, bringing you more insightful and engaging sessions.
Stay tuned!