Why is access control important for both IT teams and employees?
Organizations need to set clear boundaries as to who should be allowed to access specific files or data.

Get fresh insights, pro tips, and thought starters–only the best of posts for you.

Modern enterprises can’t afford to rely on static, one-size-fits-all access controls. With users signing in from different devices, locations, and risk contexts, security needs to adapt dynamically.
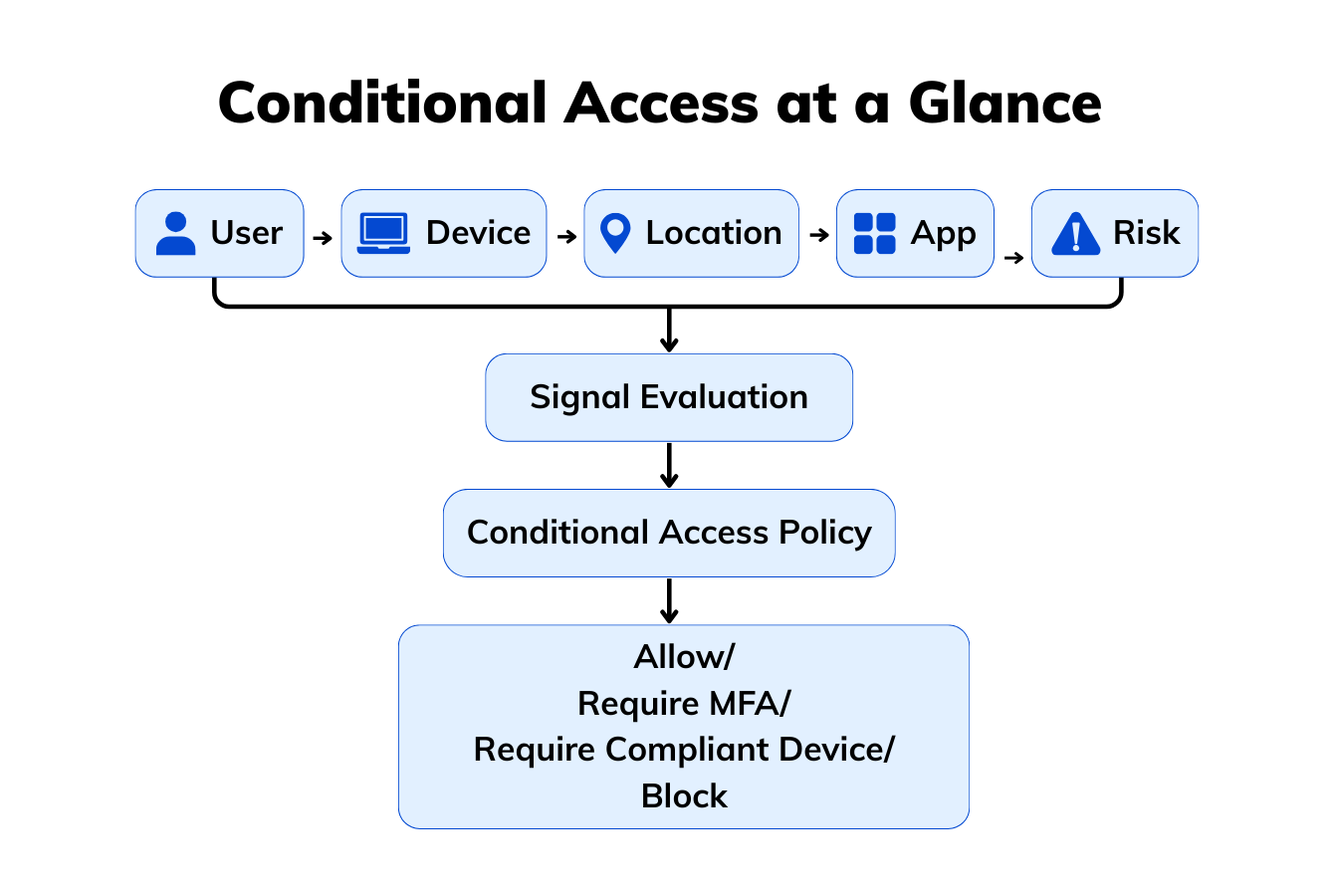
Conditional Access is Microsoft Entra ID’s Zero Trust policy engine that checks who’s signing in, from where, on what device, and under what risk conditions, then decides whether to allow, block, or require extra verification such as multi-factor authentication (MFA) or a compliant device.
In fact, Microsoft’s Digital Defense Report 2024 revealed that 99% of identity attacks still exploit passwords, while only 41% of organizations have adopted strong, phishing-resistant authentication methods.
In 2025, Conditional Access has evolved beyond basic sign-in checks, introducing Continuous Access Evaluation (CAE) and deeper Intune integration for real-time device compliance and session enforcement.
This intelligent, signal-based approach makes Conditional Access the backbone of identity-driven security and a cornerstone of any Zero Trust architecture.
Conditional Access (CA) is an adaptive security framework that governs how and when users can access corporate resources based on predefined conditions. Acting as a gatekeeper, CA evaluates multiple factors before determining whether an access request should be granted, challenged, or denied.
Built on the principle of least privilege access, CA ensures that users receive only the minimum level of access required for their role. This significantly reduces the risk of unauthorized access, insider threats, and credential-based attacks.
Key decision factors in Conditional Access include:
Access is granted only when all specified conditions are met, preventing unauthorized or risky attempts from reaching critical data.
By enforcing context-aware authentication, Conditional Access helps organizations protect data, prevent unauthorized access, and enhance security without disrupting productivity.
This impact is amplified when integrated with Unified Endpoint Management (UEM), which ensures that only compliant and secure devices can connect to corporate networks, adding an extra layer of enforcement to access decisions.
Traditional access controls assume that once a user logs in, they’re safe. Conditional Access takes a Zero Trust approach, treating every sign-in as untrusted until verified.
Conditional Access evaluates multiple signals at every sign-in attempt and, with Continuous Access Evaluation (CAE) enabled, even mid-session:
Based on these signals, Conditional Access enforces contextual controls, such as:
Conditional Access policies follow a structured process inside Microsoft Entra ID, guiding how you assign users, define conditions, and apply access or session controls.
Each layer narrows who, what, and how the policy applies.
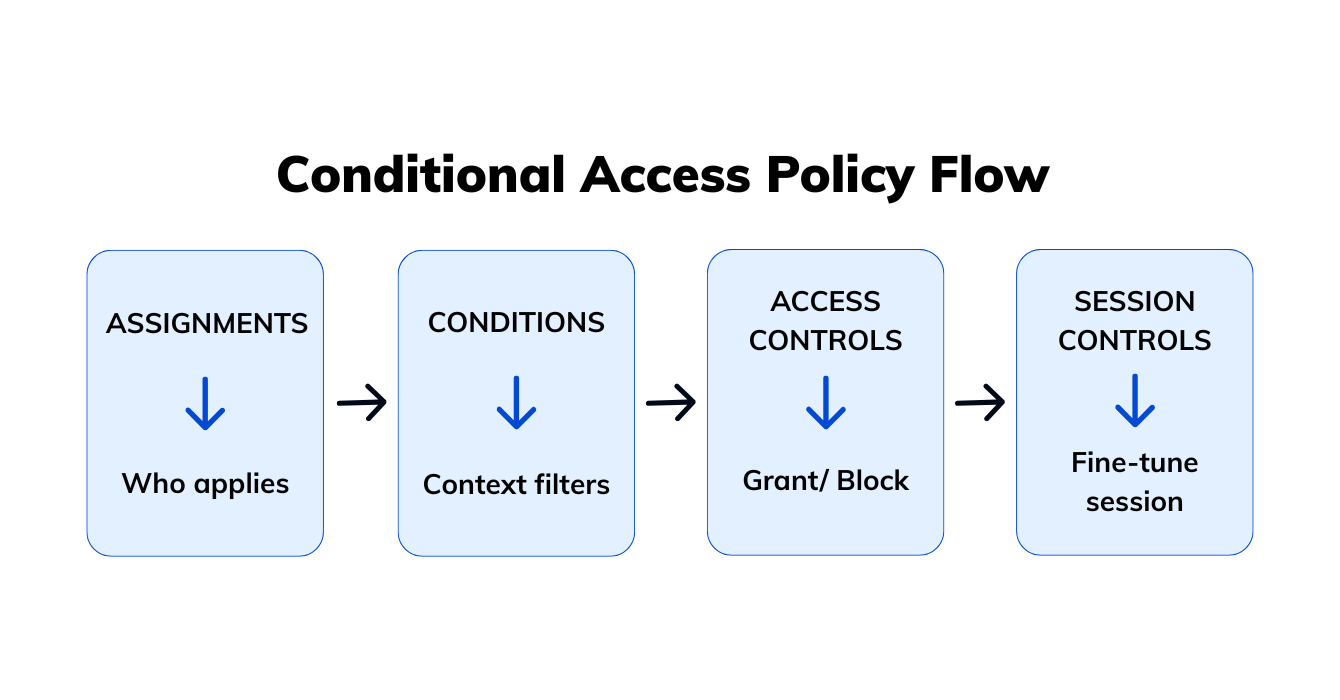
Define who and what the policy targets:
Add contextual filters such as:
Define what happens when conditions are met:
Manage risk during active sessions:
Once you understand the Conditional Access flow, you can start building policies that enforce identity and device security in the real world.
Here are a few tried-and-tested examples you can copy and adapt for your organization.
Goal: Protect high-privilege accounts from credential compromise.
Setup:
✅ Best for: Preventing lateral movement in attacks targeting admin accounts.
Reinforcing cybersecurity with Multi-Factor Authentication (MFA)
Goal: Eliminate insecure protocols that bypass modern Conditional Access.
Setup:
✅ Best for: Closing password-only authentication gaps in Exchange, POP, IMAP.
Goal: Allow access only from devices that meet your organization’s security baseline.
Setup:
✅ Best for: Enforcing device hygiene and data protection on mobile and desktop endpoints.
Goal: Add adaptive authentication based on sign-in risk.
Setup:
✅ Best for: Balancing user experience and security with adaptive friction.
Goal: Control access for non-user identities like Service Principals, which can be just as powerful as admin accounts.
Setup:
✅ Best for: Preventing compromise of service accounts used by automation or backend services. (Requires Entra ID P1/P2)
| Policy name | Trigger / Condition | Primary control | Ideal use case |
| Admin MFA enforcement | Role-based (Privileged roles) | Require MFA + compliant device | Protect high-impact accounts |
| Block legacy Auth | Legacy protocols (POP/IMAP/SMTP) | Block access | Eliminate password-only logins |
| Compliant device only | App = Microsoft 365 | Require device compliance | Enforce endpoint hygiene |
| Risk-based MFA | Medium/high sign-in risk | Require MFA or block | Adaptive protection for users |
| Workload identities protection | Non-user (service principal) | Block access from untrusted locations | Secure backend automation accounts |
Conditional Access brings clarity and control to identity-driven security, balancing protection, compliance, and usability.
Key Benefits
Multi-Factor Authentication (MFA) and Conditional Access are closely related, but they serve very different purposes within Microsoft Entra ID’s Zero Trust framework.
MFA is an authentication method, it verifies a user’s identity using multiple factors (something they know, have, or are).
Conditional Access, on the other hand, is a policy engine that decides when MFA or other access requirements should apply, based on contextual signals like risk level, device compliance, and location.
| Feature | MFA | Conditional Access |
| Function | Authentication method | Policy engine that controls when and how MFA applies |
| Triggers | Every login (static enforcement) | Context-based – adjusts based on user, device, location, and risk |
| Flexibility | Limited | High – combines multiple signals and enforcement controls |
| User Experience | Can cause over-prompting | Reduces friction by requiring MFA only when risk conditions are met |
| Scope | User-level configuration | Organization-wide adaptive access layer |
| Example Use Case | Always require MFA for admin accounts | Require MFA only if sign-in risk is medium or device is noncompliant |
Conditional Access depends heavily on device compliance data to make risk-based decisions.
That’s where Intune and UEM platforms like Hexnode come in.
Conditional Access policies can require that a device be “marked as compliant” before a user can access Microsoft 365 or other cloud apps.
This compliance state is determined by the UEM platform, which evaluates factors such as:
If a device meets the defined baseline, Intune (or the integrated UEM) reports it as compliant, allowing Conditional Access to grant access seamlessly. Noncompliant or unmanaged devices can be prompted for remediation or blocked entirely.
While Microsoft Intune handles compliance for enrolled Windows and mobile devices, Hexnode UEM extends that control to a broader range of endpoints across the enterprise.
It can:
By combining Hexnode’s endpoint intelligence with Microsoft Entra Conditional Access, organizations achieve a truly device-aware Zero Trust framework – one that adapts dynamically to both user identity and device health.
When possible, pair “Require device to be marked as compliant” with risk-based access. Trusted users enjoy frictionless access, while high-risk endpoints trigger MFA or blocking.
Implementing Conditional Access across your organization is a phased process. Start simple, validate policies, and expand gradually to avoid lockouts or user friction.
Here’s a best-practice rollout sequence to help you deploy with confidence.
This single step removes one of the biggest identity attack surfaces.
Keeps data protected on endpoints that meet your security baseline.
Introduces adaptive access without increasing user friction.
| Example | Purpose |
| CA-Admins-MFA-Compliant | Admins, Require MFA + Compliant Device |
| CA-Finance-TrustedLocation-MFA | Finance Users, Trusted Location, Require MFA |
PIM ensures that users only receive their privileged roles (like Global Administrator) on a time-bound, “just-in-time” basis.
Your CA policy can then be configured to only apply when a user has an active PIM role assignment, eliminating standing access and enforcing a true least-privilege model.
| Phase | Focus Area | Goal |
| Phase 1 | MFA for Admins | Protect privileged accounts |
| Phase 2 | Block Legacy Auth | Eliminate insecure protocols |
| Phase 3 | Device Compliance | Enforce trusted endpoints |
| Phase 4 | Risk-Based Policies | Adapt access dynamically |
| Phase 5 | Report-Only Pilot | Validate before enforcing |
| Phase 6 | CAE Rollout | Achieve real-time policy response |
| Phase 7 | Governance & PIM integration | Improve visibility, eliminate standing privilege |
Even well-planned Conditional Access deployments can stumble if key configurations are overlooked.
Here are some of the most common mistakes and how to sidestep them.
Result: User X must complete MFA and sign in from a compliant device.
Solution: Use the “What If” tool in the Microsoft Entra admin center to simulate combined effects and preview the final grant controls before enforcing policies.
This helps prevent unexpected blocks and redundant authentication prompts.
? Conditional Access is Microsoft Entra ID’s zero trust policy engine.
It evaluates signals like user identity, device compliance, location, and sign-in risk to decide whether to allow, block, or require additional verification (like MFA).
? How is Conditional Access different from MFA?
MFA is a verification method – it checks who you are.
Conditional Access is a policy layer – it decides when and under what conditions MFA (or other controls) should apply.
? What is Continuous Access Evaluation (CAE)?
Continuous Access Evaluation (CAE) reassesses access in real time.
If a user’s location, risk, or device state changes, CAE can revoke or limit access instantly, reducing the window for compromised sessions.
? Can Conditional Access require a compliant device?
Yes. Conditional Access integrates with Intune and UEM tools like Hexnode to enforce the “Require device to be marked as compliant” control before granting access to Microsoft 365 or SaaS applications.
? Should I still use per-user MFA?
No, Microsoft recommends migrating from per-user MFA to Conditional Access-based MFA policies.
This approach is more flexible, context-aware, and consistent with the Zero Trust model.
Conditional Access sits at the core of modern identity security, the decision engine that ensures only the right users, on trusted devices, under the right conditions, can reach corporate resources.
By combining Microsoft Entra ID’s adaptive policy framework with device compliance signals from management platforms like Intune and Hexnode UEM, organizations can achieve true Zero Trust enforcement across users, apps, and endpoints.
Hexnode UEM strengthens this ecosystem by extending Conditional Access coverage to every device platform – Windows, macOS, iOS, Android, and beyond.
It simplifies compliance verification, unifies device posture data, and helps security teams implement Conditional Access confidently, without friction.
Sign up for Hexnode's 14-day free trial and redefine your access control strategy
JOIN NOW!