Almost every one of us is pretty sure that nobody or nothing knows more about us than we do. Well, think again. Mobile phones probably know way too much about us, probably even more so than us. Have you ever been in a situation where ads about things you dream of pop up on your phone? If yes, you are not alone.
If you are a person who uses smartphones regularly, then all your details, from your browsing history to your password and banking details, are accessed from mobiles. It can be dangerous if someone with ill intentions gets hold of your phone.
Keeping your phone and the data in it safe should always be a priority. Just as you keep your most valuable possessions under lock and key, you should always take care of your phone.
- iPhone’s rise to popularity
- Do not allow iPhones to automatically connect to a Wi-Fi
- Disable or restrict notifications and Siri on lock screen
- Always keep your OS and apps updated
- Enable and configure Find My iPhone
- Do not jailbreak your iPhone
- Some bonus tips to ensure iPhone security
- Enable Erase Data on your iPhone
- Enable Two-Factor Authentication whenever possible
- Use a USB data blocker
- How can Hexnode help you ensure corporate iPhone security
- Hexnode iOS Management Solution
- Passcode policy
- Disable Siri when screen is locked
- Disable Autofill
- Disable notification history on locked screen
- Remote lock, locate and wipe
- In conclusion
iPhone’s rise to popularity
Almost all of the mobiles used today are either Android phones or iPhones. Android’s influence over the smartphone market made it a monopoly but now it has to share the market with Apple’s iPhone.
If you ask me why people prefer iPhone over Android one of the first things that pop up would be security. Apple does not allow any third-party apps to be installed on an iPhone and every application has to be downloaded from the Apple App Store.
Apple conducts a very strict background check on all apps before they can be published on the App Store. This is the main reason why Apple App Store has much less apps compared to other app stores.
Although Apple takes strict precautions to keep your device safe, it cannot be 100% secure. When it comes to iPhone security, the user also has to take some measures.
Common security concerns regarding Apple devices for enterprises
Some of the very common but effective practices commonly followed by people to ensure iPhone security are: using a strong passcode instead of a four-digit pin, refraining from using public Wi-Fi, using a trustworthy VPN while using the internet, and not letting others use your phone.

Apart from these common practices, a few others that can help you ensure iPhone security are:
-
Do not allow iPhones to automatically connect to a Wi-Fi
Everyone lets their mobile connect to a known Wi-Fi, office Wi-Fi, or their Wi-Fi at home. People do it because it is extremely convenient. Entering your Wi-Fi password every time you get back from work might be a bit frustrating.
There is a small problem with this habit. If someone creates a Wi-Fi with the same name as a known connection then your device might get connected to the fake Wi-Fi. This type of cyberattack is called the evil twin attack.
Evil twin attack tricks device users into connecting to fake Wi-Fi access points posing to be nearby known Wi-Fi. Once the device is connected to this Wi-Fi, the attacker can gain access to all information like passwords and ids entered by the user in non-secure or non-HTTPS websites.
Attackers can also intercept transactions done through insecure channels since the traffic passes through their device.
So, to keep your device from getting connected to a fake Wi-Fi with the same name as a known Wi-Fi, never let your iPhone connect to a Wi-Fi automatically.
-
Disable or restrict notifications and Siri on lock screen
How many times have you read a message without even unlocking your phone? From private messages to OTPs and authentication codes everything gets displayed as lock screen notifications.

Notification on a locked iPhone data This creates a chance for unwanted eyes to snoop and gather valuable information about your phone even if the device is locked. To avoid it, try to disable lock screen notifications or at least set it in preview mode so that details aren’t displayed.
Siri is the virtual assistant on your iPhones and it can help you with daily chores like booking a ticket, making reservations, or even setting alarms. Siri is an extremely useful feature introduced by Apple.
Even though Siri is a very helpful feature, there is a possibility that personal information is accessible through Siri. If Siri is enabled on lock screen, then literally anyone can activate Siri to make a call, send a text message or even know your name, without unlocking your iPhone. So, try to disable Siri on the lock screen.
-
Always keep your OS and apps updated
With most OS updates Apple tries to resolve security issues that might be present in the previous version. The same goes for apps too.
Hackers are always on the lookout for vulnerabilities with apps and OS as it can provide an easy way for them into devices. With each update, these entry passages are closed making it harder for hackers.
-
Enable and configure Find My iPhone
Ever thought about what you would do if you lost your iPhone? Find My iPhone is a safety feature introduced by Apple so that iPhone users can use their Apple ID to track and lock their iPhones if it is lost.
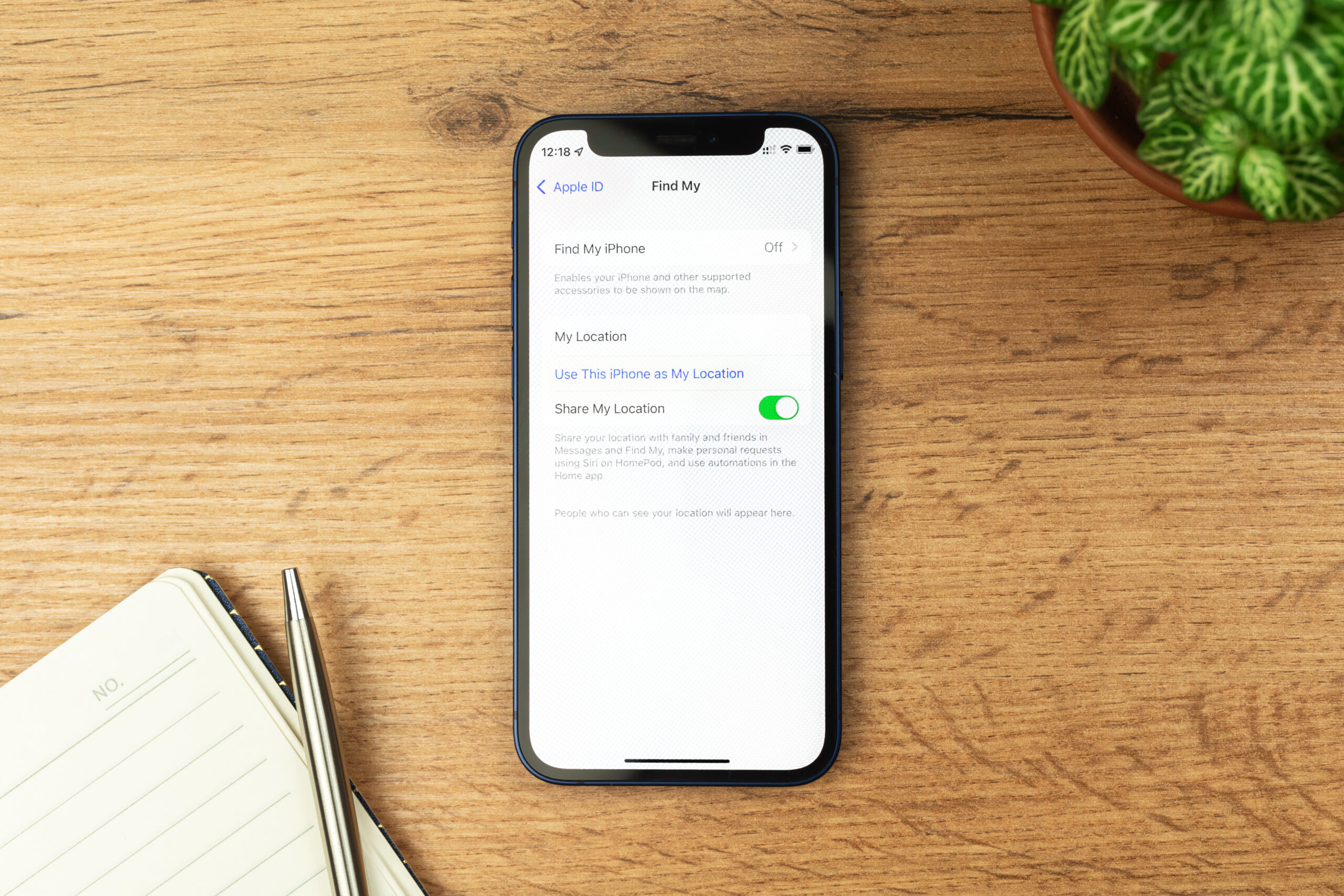
Find My iPhone settings Find My iPhone enabled devices can be tracked, locked, or even wiped clean using just your Apple ID. Just log in to your Apple ID on another device and then you can use Find My iPhone to remotely do all the previously mentioned actions on the lost device.
Activation Lock is a feature associated with Find My iPhone and it helps lock iPhones. Once Activation lock is enabled, the iPhone can’t be unlocked without the original Apple ID credentials. Without the original Apple ID, the device can’t be reused or even reset.
-
Do not jailbreak your iPhone
Before seeing why jailbreaking is dangerous, let’s see what it is and why many people do it. So, jailbreaking is sort of like hacking your iPhone. Through jailbreaking, you can unlock a world of new possibilities with your iPhone.
From sideloading applications to completely customizing your phone’s theme, jailbreaking can make your iPhone experience much more customizable.
The main drawback of jailbreaking your phone is that it bypasses all the security measures implemented by Apple. There are multiple threats out there that target jailbroken iPhones. Apart from this jailbreaking can make your warranty null and void.
So, even though jailbreaking your iPhone lets you do much more with your phone, it is safer not to do it. The same goes with sideloading of apps. One of the main reasons why people jailbreak iPhones is to sideload apps. It is always recommended to refrain from both.
Some bonus tips to ensure iPhone security
Enable Erase Data on your iPhone
There is an option “Erase Data” in the Settings of your iPhone. If this option is enabled, then the device data gets wiped after a wrong passcode is entered 10 times.
Even after the device is reset, only the original owner of the phone can access the device, because, the device is locked even after the reset and can be unlocked only on entering the owner’s Apple ID credentials.
Enable Two-Factor Authentication whenever possible
It is advisable to use Two-Factor Authentication (TFA) to secure accounts such as email, bank accounts, social media accounts, and so on. This adds an extra degree of security to your account.
Apart from the account password, an additional key is sent to the registered mobile number or email which has to be entered while logging in. This way, even if someone gets your account ID and password, they won’t be able to access it.
Use a USB data blocker
We have all used public charging ports to charge our phones. There is a slight chance that these charging points might have devices hidden inside them that can inject your device with malware.
So, while using public charging points or unknown charging points in general, try to use a USB data blocker. This is a device that is placed between your device and the charging cable, which makes sure that only charging happens and no data transfer occurs.
How can Hexnode help you ensure corporate iPhone security
Businesses and other organizations have found the importance of Unified Endpoint Management (UEM) solutions and many have started implementing UEMs in their organizations for device management. Managing devices is just one use of UEMs, they can also help organizations secure endpoints, streamline deployment, automate tasks, and more.
Featured resource
Hexnode iOS Management Solution
Hexnode UEM enables you to setup, deploy, manage, and secure iOS devices in your enterprise by simply unifying all management functionalities.
Download datasheetA lot of organizations use iPhones as work devices these days, mainly because they are much more secure compared to other mobiles. As mentioned earlier, even iPhones can be compromised. Hexnode can help you secure your corporate iPhones.
Passcode policy
IT admins can specify certain rules for passcodes used in iOS devices, like the passcode complexity, passcode length, minimum complex characters, and so on.
Some other interesting passcode restrictions that can be applied using Hexnode are:
- Maximum passcode age – Number of days after which the passcode becomes invalid and has to be reset.
- Auto lock – IT admins can set a period after which the device automatically gets locked.
- Passcode history – This can be used to make sure that previously used passcodes are not used again for some time.
- Grace period – This can help specify a period up to which a user can unlock a phone without the passcode
- Failed attempts – This lets you specify the number of failed attempts at entering the correct passcode after which the device is automatically wiped. It is similar to the Erase Data feature.
Disable Siri when screen is locked
Using this feature, you can make sure that Siri is not activated by voice when an iPhone is locked.
Disable Autofill
Using Hexnode, IT admins can not only restrict auto-filling of passwords in browsers and other apps but also disable auto-filling of user data like name, address, phone number, etc. in web forms in Safari.
Disable notification history on locked screen
Notification history can be switched off on iPhones using Hexnode. This means that the notifications will only be visible for a limited time on the lock screen.
Remote lock, locate and wipe
Hexnode can help you remotely lock iPhones into a kiosk screen in case the device is stolen. The screen can be exited only using the password mentioned by the IT admin or if the IT admin manually disables it.
iPhones can also be located using Hexnode. Remote actions like enabling Activation Lock and initiating device wipe are also possible using Hexnode.
In conclusion
Just because you use an iPhone doesn’t mean that you don’t have to worry about its security. iPhone security should always be ensured even though Apple provides a level of security of its own.
Following every tip mentioned here might greatly diminish your convenience while using your iPhone. However, in the wake of rising data breaches and attacks, it is crucial to focus more on security over convenience.
Sign up for a free trial
Sign up for a 14-day free trial with Hexnode and explore iOS security features offered by Hexnode.
Sign up




