Today, businesses rely on a vast network of devices to operate. From laptops and smartphones to tablets, wearables, and even internet-connected devices, these endpoints hold sensitive data and require robust security measures. Unified Endpoint Management (UEM) offers a comprehensive solution for managing and securing this diverse device landscape on a single platform. In fact, UEM has become a cornerstone in the landscape of enterprise IT management. And so, let’s explore the ins and outs of UEM.
What is UEM?
UEM goes beyond traditional mobile device management (MDM) solutions. It provides a centralized approach to managing all endpoints within an organization, regardless of device type or operating system. This includes desktops, laptops, smartphones, tablets, wearables, rugged devices used in field operations, and even internet-of-things (IoT) devices like smart sensors. In today’s interconnected world, driven by the Industry 4.0 revolution and the surge in remote work, UEM solutions are more critical than ever. They offer a unified view of users across multiple devices, enhance data protection, streamline device configuration, and enforce usage policies. UEM solutions are not just about managing devices, but also about smoothly handling related endpoint technologies such as identity services, client management tools, and so on.
Unified endpoint management elements:
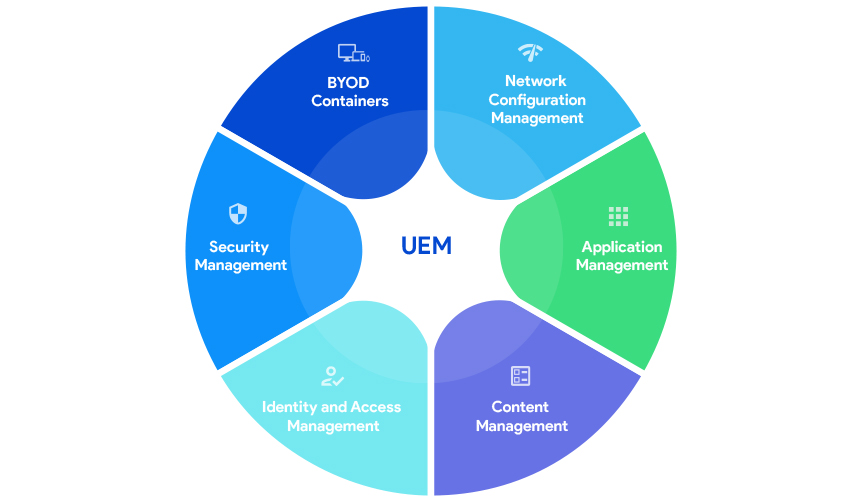
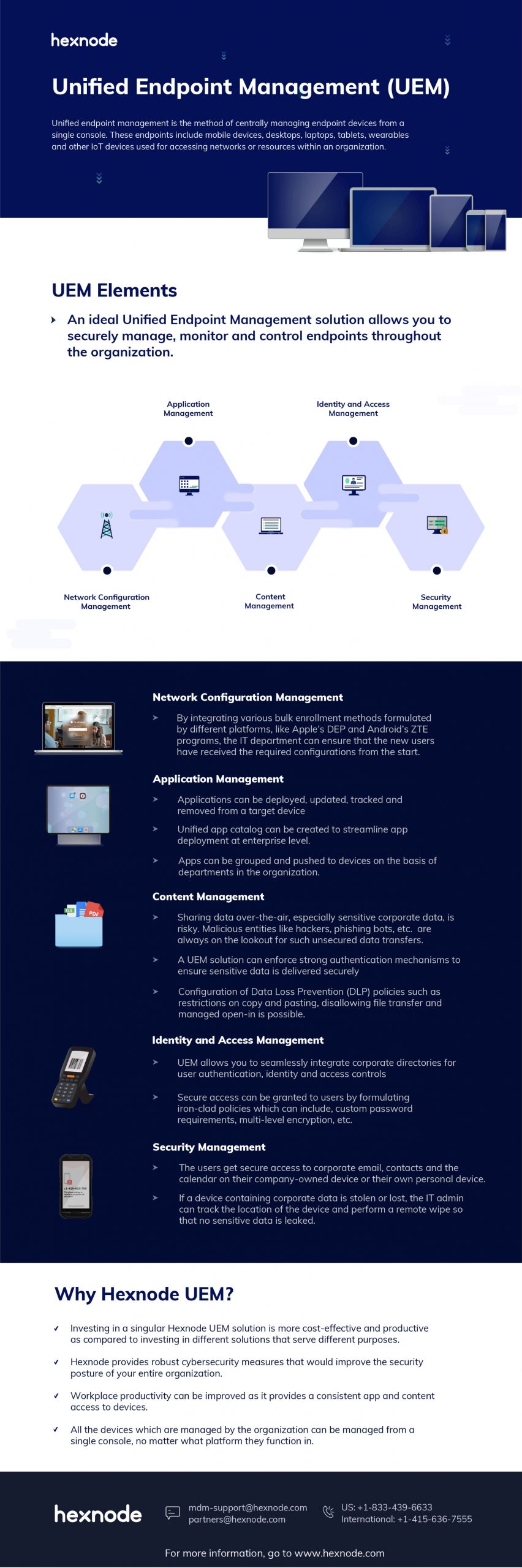
Network configuration management (NCM)
NCM acts as the bedrock for a robust unified endpoint management solution. By managing configurations for network devices like routers, switches, and access points, NCM ensures a smooth foundation for UEM functionality. This translates to seamless data flow for UEM-managed devices, allowing them to effectively communicate and receive updates. Additionally, NCM strengthens UEM’s security posture by setting firewall policies and controlling network access. Finally, NCM manages Wi-Fi networks, ensuring reliable device connectivity crucial for UEM’s remote management capabilities.
An ideal UEM solution allows IT departments to securely manage, monitor, and control endpoints throughout the organization. With advancements in automation, bulk enrollment methods such as Apple’s DEP and Android’s ZTE programs ensure that new users receive the required configurations promptly. UEM also streamlines the lifecycle management of enrolled devices, enabling IT to enroll, provision, remotely control, and decommission devices from a single console.
Application management
UEM solutions facilitate the deployment, updating, tracking, and removal of applications across devices. A unified app catalog can streamline app deployment at an enterprise level, ensuring that only relevant apps are available to users based on their roles. Modern UEM solutions also offer enhanced app security features like sandboxing and threat detection, and they integrate seamlessly with popular enterprise app stores.

Content management
It is quite risky to share sensitive corporate data over-the-air. UEM solutions enforce strong authentication mechanisms to secure data transfers. Advanced Data Loss Prevention (DLP) policies, such as copy-paste restrictions and managed open-in, ensure data security. UEM enables users to access corporate data securely from anywhere, significantly enhancing remote work capabilities.
Identity and access management (IAM)
UEM solutions integrate seamlessly with corporate directories for user authentication and access control. They enforce robust security policies, including custom password requirements and multi-level encryption, to ensure secure access to corporate resources. Modern UEM solutions support advanced identity management features like biometric authentication and adaptive access control based on user behavior analytics.
Security management
UEM solutions implement sturdy security controls to protect sensitive corporate data across various endpoints. They support Endpoint Detection and Response (EDR) for real-time monitoring and threat response. IT departments can manage and secure both corporate-owned and BYOD endpoints, ensuring secure access to corporate resources. If a device is lost or stolen, UEM solutions can track its location and perform a remote wipe to prevent data breaches.
BYOD containers
Supporting BYOD (Bring Your Own Device) is essential for modern enterprises. Bringing personal devices to work can increase employee productivity and decrease operational costs. UEM solutions can deploy secure containers (containerization) within personal devices, ensuring that corporate data remains protected. These containers allow for selective wiping of corporate data if a device is lost or the employee leaves the organization, addressing privacy concerns and enhancing security.
Unified endpoint management use cases
Unlike MDM and EMM solutions, UEM aims to integrate all the endpoints coming under an organization’s purview. This greatly increases the scope for UEMs. Here’s a look at a few of the UEM use cases:
Hybrid work environment
The rise of hybrid work models, combining in-office and remote work, has highlighted the need for robust endpoint management solutions. UEM solutions are essential in this context as they:
- Ensure consistent security: UEM provides consistent security policies across all endpoints, regardless of location. This includes enforcing encryption, multi-factor authentication (MFA), and compliance with corporate security standards.
- Streamline device management: With UEM, IT departments can manage and support remote devices just as efficiently as those within the office network. This includes remote troubleshooting, software updates, and policy enforcement.
- Enhance productivity: UEM solutions enable seamless access to corporate resources and applications, ensuring that employees remain productive whether they are working from home or in the office.
- Facilitate compliance: UEM ensures that all devices adhere to organizational and regulatory compliance requirements, protecting sensitive data across all environments.
Rugged device management
Industries such as construction, transportation, logistics, healthcare, and the military heavily rely on rugged devices designed to withstand harsh conditions. UEM solutions offer significant advantages in managing these devices:
- Simplified enrollment: UEM provides multiple enrollment methods, making it easy to onboard rugged devices, whether they are new or replacements.
- Remote provisioning: IT admins can remotely push mandatory applications, configurations, and updates to devices in the field, reducing downtime and maintaining productivity.
- Enhanced security: Rugged devices often operate in challenging environments, making security a critical concern. UEM solutions offer features like remote wipe, location tracking, and device lockdown to protect sensitive data if a device is lost or stolen.
- Monitoring and analytics: UEM enables continuous monitoring of device health and performance, allowing proactive maintenance and reducing the risk of device failure in critical situations.
CMT integration
Client management tools (CMT) have historically been used for managing desktop configurations and software. However, with the advent of mobile devices and the need for unified management, UEM solutions have integrated CMT capabilities.
- Comprehensive device management: Modern UEM solutions provide a unified platform that includes traditional CMT features such as device imaging, software distribution, and patch management alongside mobile device management capabilities.
- Seamless integration: Organizations can leverage their existing CMT infrastructure while benefiting from the advanced features of UEM, such as mobile device management, IoT device management, and enhanced security protocols.
- Streamlined processes: UEM integration with CMT allows for streamlined processes, reducing the complexity and time required for device enrollment, provisioning, and auditing.
- Improved visibility: A unified UEM solution provides comprehensive visibility into all endpoints, facilitating better decision-making and more efficient IT operations.
IoT management
The Internet of Things (IoT) has introduced a vast array of connected devices that need to be managed and secured. UEM solutions are expanding to address the unique challenges posed by IoT devices.
- Centralized management: UEM solutions offer a centralized platform to manage a diverse range of IoT devices, from smart TVs and scanners to wearables and industrial sensors.
- Enhanced security: IoT devices often lack built-in security features, making them vulnerable to cyber threats. UEM solutions implement strong security measures, such as network segmentation, secure communication protocols, and regular firmware updates.
- Operational efficiency: By managing IoT endpoints through a UEM platform, organizations can improve operational efficiency, ensuring that their endpoints are functioning correctly and are promptly updated.
- Data insights: UEM solutions provide analytics and reporting on IoT device usage, performance, and security, enabling organizations to make informed decisions and optimize their IoT deployments.
Why does your organization need a UEM solution?
UEM offers a multitude of benefits that can significantly improve your organization’s security posture, operational efficiency, and user experience. Here are some key advantages:
- Enhanced security: UEM enforces strong authentication protocols, application whitelisting, and data encryption to safeguard sensitive information across all devices. This centralized approach minimizes the risk of data breaches and ensures compliance with industry regulations.
- Simplified device management: UEM eliminates the need for multiple management consoles for different device types. IT administrators can remotely provision, configure, and troubleshoot devices from a single, unified platform, streamlining workflows and saving valuable time and resources.
- Improved user experience: UEM ensures consistent application and content access across all devices. This allows users to work seamlessly from any authorized device, enhancing productivity and satisfaction.
- Platform-agnostic management: UEM solutions manage a diverse fleet of devices in a platform-agnostic manner, accommodating the needs of a modern, device-diverse workforce.
- Increased flexibility: UEM facilitates Bring Your Own Device (BYOD) initiatives by creating secure workspaces on personal devices. This empowers employees with their preferred devices while maintaining strict data security measures within the organization.
- Reduced costs: UEM eliminates the need for multiple device management solutions, reducing licensing fees and simplifying IT infrastructure. Additionally, the streamlined management process lowers the IT team’s workload, leading to potential cost savings.
UEM in action
UEM solutions are implemented across various industries to streamline device management and bolster security. Here are some examples:
- Healthcare: UEM secures access to patient data on doctors’ laptops and tablets, ensuring HIPAA compliance and safeguarding sensitive medical information.
- Retail: UEM manages inventory scanners and mobile point-of-sale devices in stores, protecting financial data and streamlining checkout processes.
- Manufacturing: UEM secures access to control systems and monitors on the factory floor, preventing unauthorized access and protecting critical industrial operations.
The future of unified endpoint management (UEM)
As technology evolves, UEM solutions will continue to adapt and integrate with emerging trends. Here are some potential areas of growth:
- Artificial intelligence (AI): UEM powered by AI can offer real-time threat detection, automated remediation, and self-healing capabilities for a proactive approach to security.
- Virtual and augmented reality (VR/AR): As VR and AR devices become more prevalent, UEM will expand to manage and secure these new endpoints within the work environment.
- Enhanced IoT security: UEM will play a crucial role in securing the ever-growing number of IoT devices deployed within organizations.
Conclusion
UEM is no longer a luxury but a necessity for organizations of all sizes. By adopting a unified approach to endpoint management, businesses can ensure robust security, streamline operations, and empower their workforce with the flexibility to work productively from any authorized device.