Hi there! Did you miss our webinar on leveraging Mac secure tokens and bootstrap tokens? Well, don’t worry! Here’s your short, sweet, and crisp recap to help you with your FOMO.
The in-house expert, Edwin Jerald, Senior Product Marketing specialist at Mitsogo, steered an information-packed half-hour session while explaining the ins and outs of Mac secure tokens and bootstrap tokens. From introducing the concepts of volume ownership and chain of trust to getting into the nitty-gritty details of generating and assigning the tokens and explaining the potential issues, the session had it all. So, let’s sneak a peek into the highlights and key takeaways of the webinar.
Volume ownership and Chain of trust
In Apple’s terms, volume ownership can be loosely defined as “the user who first claimed a Mac by configuring it for their own use, along with any additional users.”
In simpler terms, Volume ownership is a concept that determines which users are authorized to make changes to the macOS volume. It handles the ‘chain of trust’ on a macOS system. Additionally, it provides a structure for how Macs would recognize a ‘trusted’ account on a user’s device.
Now, the “chain of trust” in Mac security, on the other hand, refers to the process by which secure tokens are associated to macOS user accounts.
What is a secure token?
Apple defines a secure token as…
…a wrapped version of a key encrypted key (KEK) protected by a user’s password.
So, secure tokens are cryptographic identifiers used in macOS systems to determine whether a user has privileges to make system-level changes to the device. They are unique to each user account and are essential for enabling various security features and functions within the macOS ecosystem.
Secure tokens validate a user’s authorization before allowing them to perform privileged actions such as enabling FileVault encryption, managing software updates, or erasing all content and settings on a device. They play a crucial role in maintaining the integrity and security of macOS systems. Essentially, they ensure that only authorized users can access and modify critical system settings. Accordingly, they are responsible for enforcing volume ownership on a user account.
The need for secure tokens
The webinar highlighted a few security features and functions in macOS that absolutely require the use of secure tokens. Here’s a quick rundown.
- macOS drive startup security policy: Determines the booting capabilities of a Mac, ensuring that only trusted volumes are permitted to boot the system.
- macOS software updates and upgrades: Ensures that only authorized users can install system updates and upgrades, mitigating the risk of unauthorized modifications.
- FileVault encryption: Grants users the ability to enable and manage full-disk encryption, safeguarding data against unauthorized access.
- Erase all content and settings: Allows users to securely erase all data from a Mac, protecting sensitive information before recycling or repurposing the device.
Generation of secure tokens
So, when and how are these secure tokens generated? Well, when you set the initial password for the first user on a Mac, that user automatically receives a secure token. Subsequently, any additional user accounts created by this initial user, who has a secure token, will also be automatically granted their own secure tokens.
The process involves cryptographic operations to create unique identifiers linked to user accounts. This establishes a secure foundation for user authentication and authorization.

Featured resource
Apple device management
Apple devices are growing in popularity as enterprise devices. Learn how to be enterprise-ready by managing your Apple fleet.
Download now!Mobile accounts and Secure tokens
Further into the webinar, the question about mobile accounts was addressed. While secure tokens are integral to macOS security, they are not applicable to Active Directory (AD) mobile accounts. These accounts are managed by AD and are not automatically granted a secure token on user login. Essentially, even the user accounts created using command line tools don’t directly receive an associated secure token attribute. And so, these accounts will require the manual assignment of a secure token.
Secure tokens and ADE
In Automated Device Enrollment (ADE) for MDM (Mobile Device Management), secure tokens are vital for device admin privileges and management capabilities. When you’re setting up a Mac using Automated Device Enrollment (ADE) with the assistance of Hexnode (MDM solution), there are two situations regarding how secure tokens are handled:
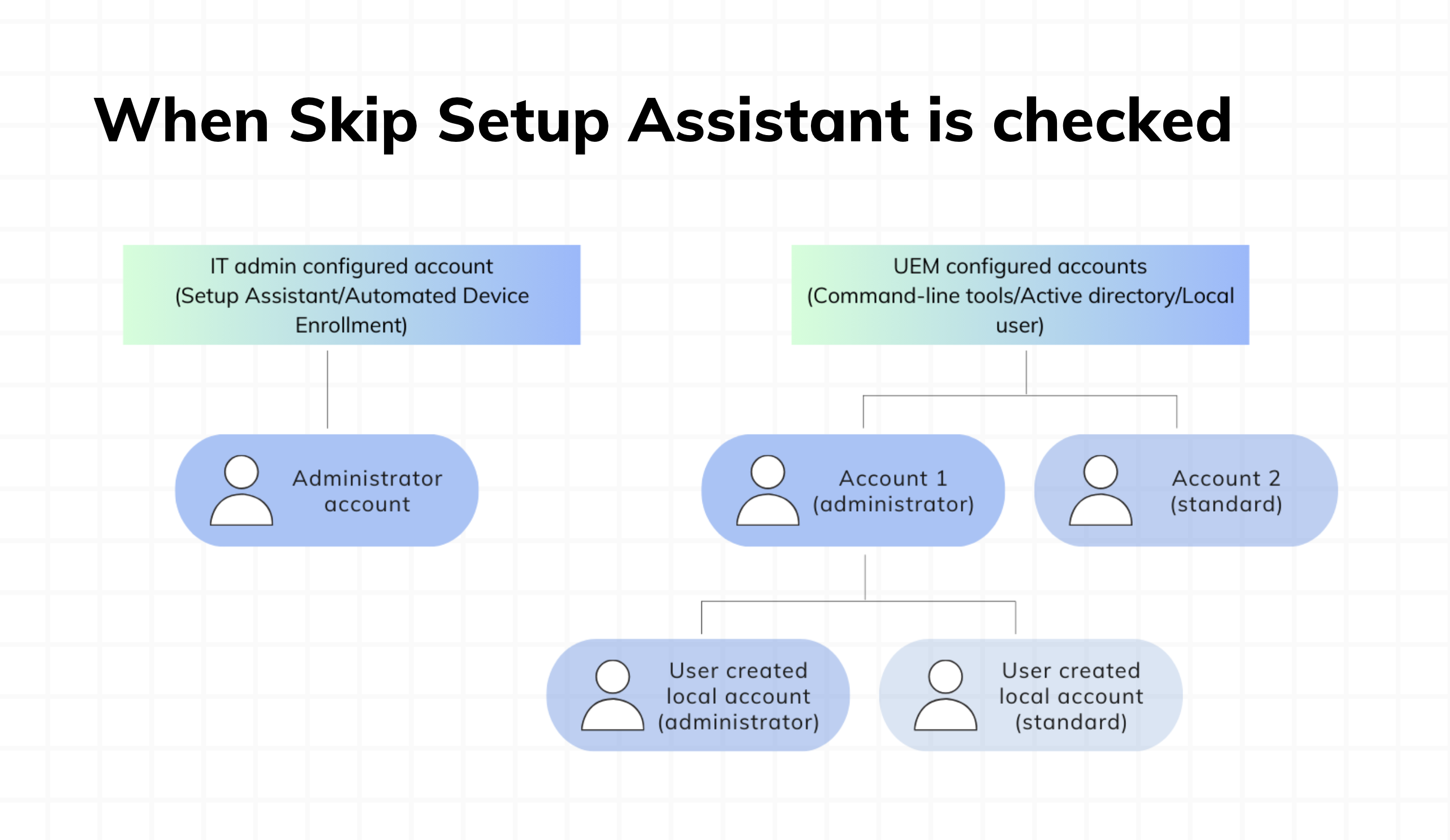
Skip setup assistant checked
- Auto-Admin account: This account is automatically created during the first login after setup.
- End-user account creation: In this case, users won’t see the option to create accounts during the setup process. If additional accounts are needed, they must be created using other methods such as Hexnode Access, Active Directory binding, or remote commands provided by the MDM.
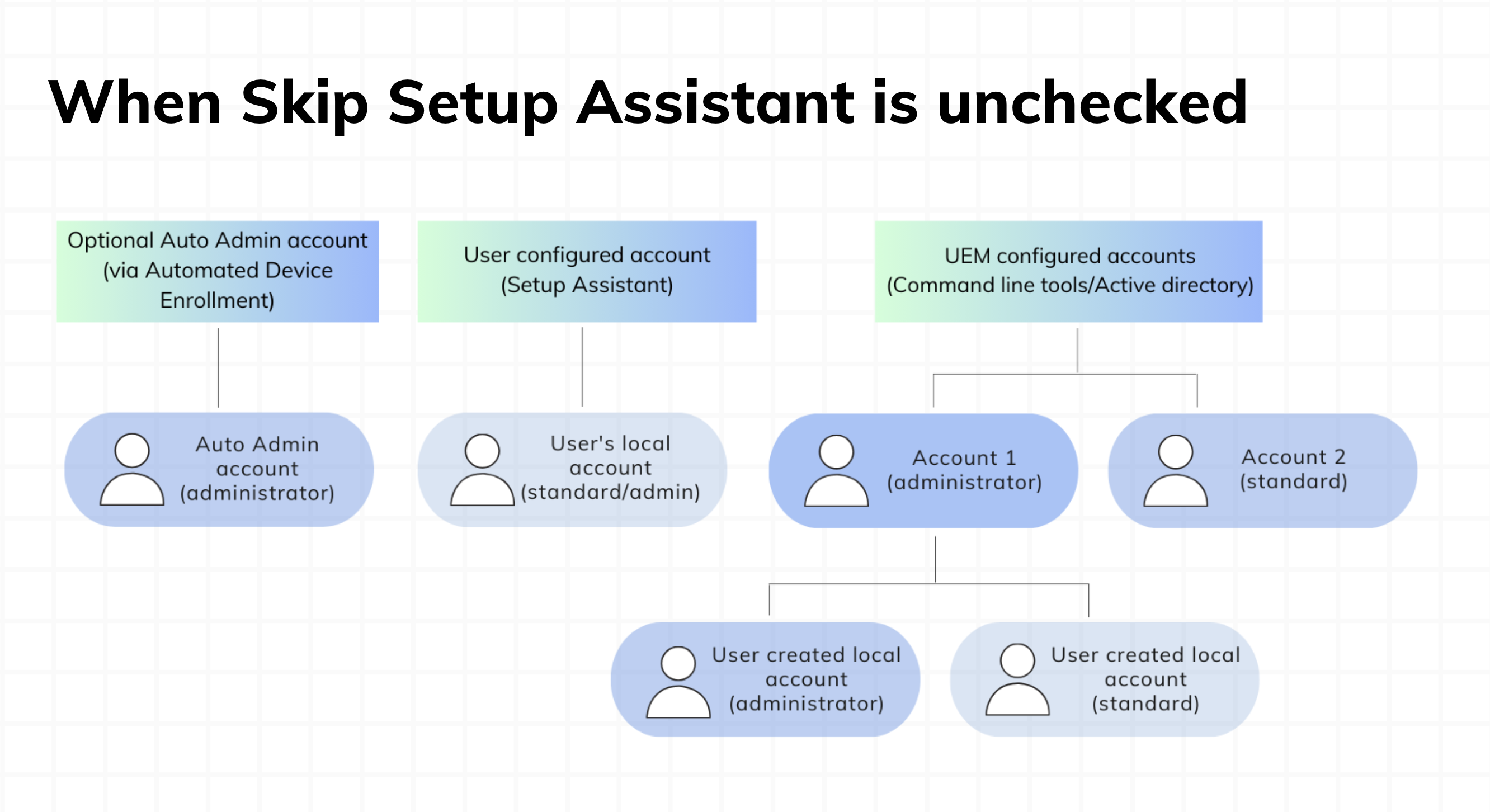
Skip setup assistant unchecked
- Initial accounts: Here, you’ll find two accounts right from the start:
- Auto-admin account: This account is set up automatically through the ADE policy.
- Setup assistant account: This account is created by the end-user during the initial setup process.
- Secure token assignment:
- Auto-admin account: It gets its secure token during the very first login.
- Setup assistant account: A secure token is assigned during the setup process when the user sets up their password.
Manually assigning secure tokens
Moving on, the webinar highlighted the fact that admins can manually assign secure tokens via command-line interface (CLI) or through MDM solutions. The command-line approach offers flexibility and control, allowing administrators to specify user accounts and authentication credentials for token assignment. Alternatively, MDM solutions automate the process, streamlining token assignments based on predefined policies and configurations.
Bootstrap tokens
The later part of the webinar shed light on the bootstrap token feature in macOS 10.15 and later that can help grant secure tokens to macOS accounts. Essentially, bootstrap tokens are cryptographic objects used during the setup and enrollment of macOS devices into a Mobile Device Management (MDM) solution. They serve as initial credentials that establish trust between the device and the MDM server during the enrollment process.
When a secure token-enabled user signs in on a Mac for the first time, the device generates a bootstrap token. This bootstrap token contains cryptographic keys and information necessary for secure communication with the MDM server. The bootstrap token is then securely escrowed to the MDM server.
Escrowing the bootstrap token to the MDM server allows the server to establish trust with the enrolled device. It enables the MDM server to:
- Grant secure tokens to any user logging in to a Mac computer. This includes local user accounts, mobile accounts, and remotely created accounts.
- Approve and load Kernel Extensions (KEXTs) and install Software Updates via MDM.
- Silently authorize an Erase All Content and Settings command via your MDM.
And so…
And that, ladies and gentlemen, is the end. But hey, the learning doesn’t stop here – we’ve got an exciting lineup of more webinars coming your way! Stay tuned for more opportunities to connect, grow, and explore together. Your curiosity fuels our passion, and we can’t wait to have you join us in the upcoming sessions. Until then, keep the enthusiasm alive, and let’s continue this learning adventure together!
The easier way to manage your Mac devices
Scale up your device management strategies by bringing onboard a UEM solution. Try Hexnode free for 14 days.
Sign up now!





