How to implement a successful BYOD policy amid Covid-19
Learn how to set up a successful BYOD policy for your enterprise, in the wake of the COVID-19 pandemic.

Get fresh insights, pro tips, and thought starters–only the best of posts for you.
Eugene Raynor
Apr 5, 2021
12 min read

A year has passed since the COVID-19 pandemic swept across the world like a terrifying wave, crashing into our corporate culture and causing absolute chaos. Since then, we’ve noticed a shift in the way companies do business. Today, enterprises have moved from their closed office spaces and boldly transitioned into new business models in the digital realm. More and more companies are transitioning into the clouds and the trend of remote work seems like it will stay for a very long time. With all these innovations in business strategies, it is safe to assume that our IT management model is evolving into one that is boundless and everywhere. The people at Gartner have coined this as the ‘Everywhere Enterprise’ model of IT management.
So, what exactly is this Everywhere Enterprise? Well, the two keywords, ‘Everywhere’ and ‘Enterprise,’ pretty much tell you half the story.
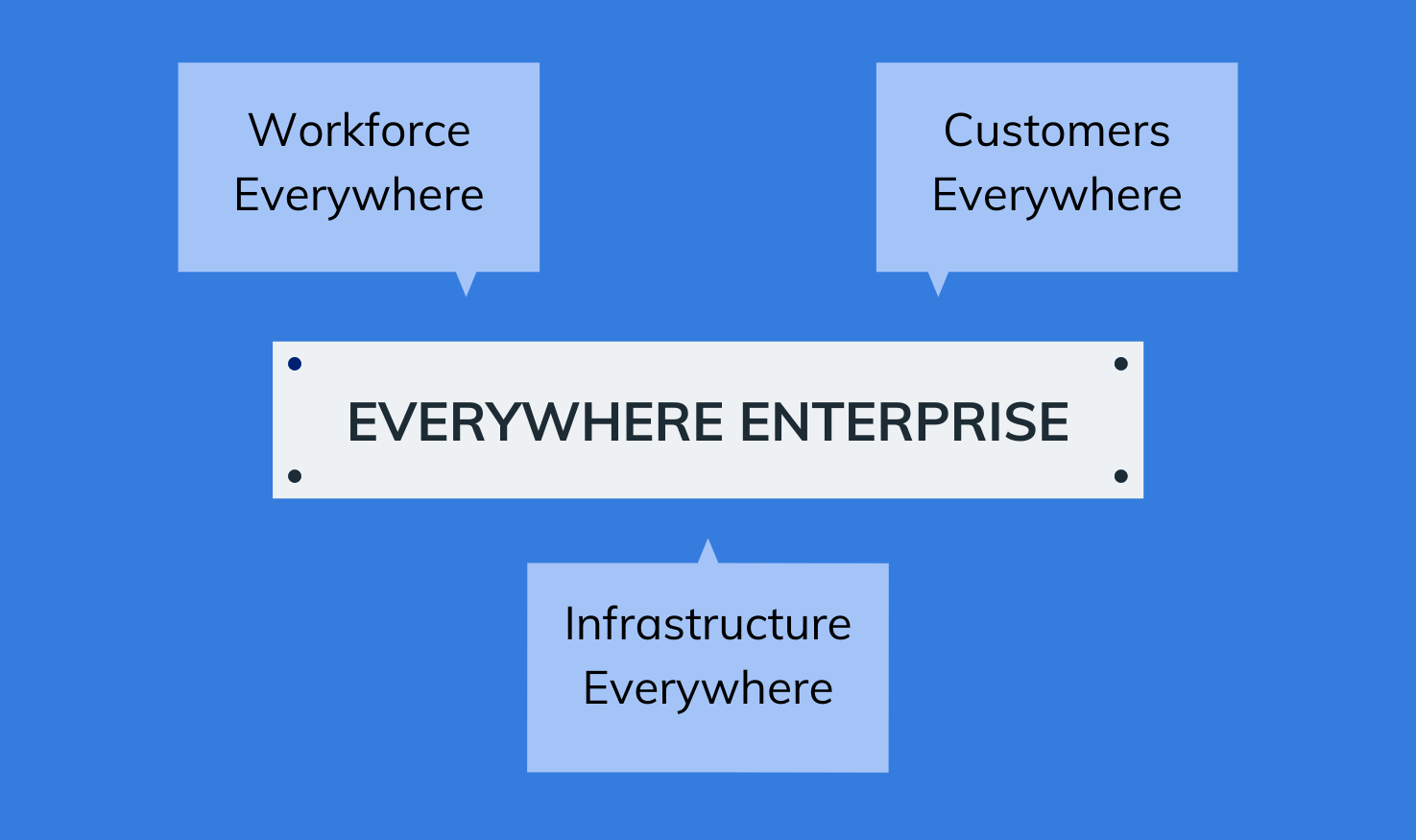
What this means is that any organization that has
Although the concept of Everywhere Enterprise has been around for a while, the rise of the COVID-19 pandemic accelerated the business transitions into this IT model. The changes in work-life culture, the increasing popularity of SaaS services, and the idea of broader customers online, have all played a part in the rise of Everywhere Enterprise.

Shifting to remote work is not an easy task by any means. Companies will have to face problems ranging from securing their devices and infrastructure outside the office to ensuring a productive environment on workers’ remote devices.
Definitely, there will be issues pertaining to enterprise security when shifting to a remote workforce. Phishing, Spoofing and other social engineering attacks will be significant threats to employees working from home. The device you use to access corporate data and the Wi-Fi network you are connected to poses the two primary gates of access to enterprise security. These are the two channels that cybercriminals will try the most to crack into, and your organization must be ready with a proper solution before adopting remote work. Utilizing a UEM solution like Hexnode equips businesses with a host of strategies to secure corporate endpoints and manage the networks they connect to.
Any organization shifting to remote work must equip their employees with the tools and services necessary to perform work, even from their home’s comfort. Companies can expect fewer person-to-person interactions, and they will need to set up remote-collaboration services to assist employees with teamwork.

Bring Your Own Device (BYOD) models are now commonplace in today’s Enterprise Mobility strategies. Allowing your employees to use their personal devices for corporate work enables them to increase working hours and improve overall productivity. Businesses can also harness this solution to reduce their overhead costs and maintenance charges.
However, without a proper management strategy, BYOD policies can be a double-edged sword. The employees’ personal devices may not possess the security measures required to effectively separate and protect corporate data, resulting in confusion between personal and work environments on your employees’ devices. This is where Hexnode comes in with its effective BYOD management strategies to containerize, secure and manage corporate BYOD devices.
The chances for insider threats are real. Especially when companies employ a remote workforce, the threat of an uncertain future fuelled by the pandemic, coupled with the privacy of being unnoticed when working from home, can bring malicious ideas to your employees’ minds. Your organization must be ready with measures to monitor and manage their remote workforce and set up policies to prevent data leaks and attacks, both intentional and unintentional.
In an environment where employees are dispersed everywhere around the world, on-premises software won’t cut it. Businesses will have to move to the cloud to set up remote collaboration tools. Popular cloud services for remote collaboration include
In the Everywhere Enterprise IT model, there is no such thing as an enterprise network. Instead, the entire world is your network.
Now, this presents a host of challenges for your IT. The traditional methods of securing your business may prove ineffective when managing a remote workforce. From protecting your enterprise infrastructure to managing endpoints, all of this has to be done remotely.

Businesses can make use of a UEM solution – such as Hexnode – to ensure effective endpoint security and device management strategies for their remote workforce. Depending on your business needs, Hexnode offers both cloud and on-premises management solutions to fulfill your business goals.
Now, this is a sketchy subject. Maximizing your workforce productivity is essential, yes. But so is securing your enterprise infrastructure. You must follow a fine line to secure your business from threats and attacks that might occur on running a remote workforce, without making it difficult for employees to access corporate facilities. Effective Identity and Access Management strategies can help achieve this feat.
So, in a work-from-anywhere environment, without an Enterprise network to manage and secure your devices, how do you achieve enterprise security? Now, although passwords and VPNs can do the work to some extent, to provide a streamlined and permanent solution to the issue at hand, you need more creative methods of authentication. Meet, Biometrics, MFA and Zero Trust Security.
When operating a dispersed workforce, provisions must be put in place to configure and deploy devices to employees working remotely. These devices must be configured such that it requires minimal effort to set up from the end-user. Android Zero-Touch, Apple Business Manager, Apple School Manager, Microsoft SCCM are platforms that organizations use to set up devices out-of-the-box. With the help of the cloud, organizations can also set up Virtual Desktop Infrastructure (VDIs), to assist remote workers in their operations. Device-as-a-service is another method that has gained traction during the pandemic, where the devices are outsourced from Managed Service Providers (MSPs) with pre-configured software and services, reducing the load on IT.
Utilizing a Unified Endpoint Management software like Hexnode enables businesses to secure their endpoints and enterprise infrastructure from cyberattacks. With Hexnode, you can create a secure environment for your remote workforce, by making use of the following features.
With Hexnode, businesses can configure Work Profile for Android Enterprise devices and Business Container for iOS devices, to set up separate workspaces to access corporate data. This draws a fine line between employees’ work and personal apps and data, while also securing corporate data.
Hexnode is integrated with Android Zero-Touch, Apple’s Automated Device Enrollment Program, Samsung Knox Mobile Enrollment, and supports Microsoft SCCM. This enables your organization to remotely configure and deploy corporate devices to their remote workers and allow out-of-the-box enrollment of these devices to the Hexnode portal.
When setting up corporate devices for your remote workforce, the Wi-Fi network employees use to connect to corporate services may not have the required level of security. In cases like this, you can use Hexnode to push VPN configurations for Android, macOS and iOS devices in bulk, to remote employees. This enables employees to secure their network connections. With Hexnode, you can also disable devices from connecting to unprotected Wi-Fi networks.
With Hexnode, your organization can set up location tracking policies to monitor your remote employees’ devices and manage device policies according to the location with the help of geofencing policies.
Every organization has its bunch of absent-minded employees, and losing devices with sensitive information can be a pain, especially in a work-from-home situation. With Hexnode’s lost mode and wipe device actions, your organization can protect the devices’ corporate data from falling into the wrong hands.
Pushing Apps to your remote employees becomes easy as pie with Hexnode. With just a few clicks, you can remotely deploy Store and Enterprise apps, and set up app configurations for your managed devices. You can also blacklist harmful and unproductive apps for iOS, Android, macOS and Windowsdevices, and set up app catalogs, all from a central console.
With Hexnode UEM, businesses can securely manage and transfer content to their corporate devices. You can also specify the content location on the device and delete content remotely from the Hexnode portal.
Hexnode lets your organization enforce strong password policies to secure corporate data on managed devices. You can set up restrictions on password length, complexity, age, history and device auto-lock time. You can also configure and push device encryption policies in bulk to corporate devices, to encrypt business hard drives.
With the help of Hexnode’s Remote Access tools, businesses can easily troubleshoot device issues in real-time, enabling your remote workforce to put in more productive hours.
With the Hexnode Messenger app, organizations can broadcast messages to remote devices, and assist your remote workers in device troubleshooting.
In the post-Covid age, it is a fair judgment that Everywhere Enterprise will be the new normal for organizations setting up their business strategies. Employees get to work from their preferred locales, and businesses get to cut costs in accommodating their workers. It’s a win-win strategy for both sides.
Everywhere enterprise is here to stay, and Hexnode’s UEM solution empowers your business to secure and manage all your remote devices.
Try out Hexnode free of cost for 14 days and experience simplified device management firsthand.Need to secure and manage your remote workforce?