With over 95% of Fortune 1000 companies making use of Active Directory services to organize their business, and around 73% of devices using the Windows operating system, Windows devices are comfortably equipped with the clear-cut option of going for Mircrosoft’s Active Directory services to manage user accounts and their access. But what happens when a macOS device is introduced in the enterprise?
As an IT admin, you might have asked – is it possible to integrate a Mac with Microsoft’s Active Directory services? The answer is, yes.
In this blog, we’ll cover the essentials of macOS Active Directory binding, learn how to troubleshoot binding issues, and understand how you can use a UEM solution to remotely bind Macs to the AD domain.
Bind your Macs to Active Directory with Hexnode UEM
What is macOS Active Directory binding?
macOS Active Directory binding is the term associated with binding a macOS device to the Active Directory domain. So how does this process work? To find out, let’s look at it through a series of simple steps.
- Step – 1: The entire process begins with your Mac, requesting to join the Active Directory domain.
- Step – 2: Once this joining request is received, the Active Diectory server verifies the user credentials that were used to join the AD database.
- Step – 3: Once the credentials have been successfully verified, the Active Directory server (also called, domain controller) gets the macOS device to communicate with the Active Directory database.
- Step – 3: Once this process is completed, the Active Directory users can login to the Mac using their AD credentials, and access their data stored within the AD database, straight from the macOS device itself.
What is Active Directory?
Active Directory is a directory service developed by Microsoft, that’s used to maintain and manage a database containing all the information about your company’s users and devices.
In Active Directory, data is stored as objects, which include users, groups, applications, and devices, and these objects are categorized according to their name and attributes.
What is Active Directory domain controller?
Active Directory domain controller is a server that responds to authentication requests on the network and validates users on the company network. In basic terms, its purpose is to manage access privileges for all the users within the Active Directory domain.
What is the purpose of macOS Active Directory binding?
The primary purpose of macOS Active Directory binding is to equip network users with the ability to login to a connected Mac, and access the data stored in the Active Directory right from the macOS device itself. What’s more, with the help of Active Directory, you can also control their access privileges within the company network. In other words, Active Directory services enable you to authorize the network users to access just the data and resources they’re permitted to use, and grants them access only after successful authentication.
Active Directory domain services – Hierarchical structure explained
Alright so let’s talk a bit about Active Directory’s hierarchical structure. Essentially, the hierarchical structure of an AD is comprised of forests, trees, domains, and organizational units (OUs). Now, how are these units related to each other? Let’s take a look.
Domain
A domain is the fundamental unit for managing and maintaining objects in Active Directory. In basic terms, it is a collection of objects within the AD network. These objects can be users, groups, applications, or devices, and they are categorized within the AD domain based on their names and attributes. Usually, domains may represent departments within a company, or the geographical location of a company.
Take, for example, a company called ‘Example’. Then, the root domain of this company would be registered as, exampleUS.com, and their sub-domains would be marketing.exampleUS.com, and sales.exampleUS.com.
It is important to always create the top-level domains (root domains) of a company first, before moving on to create any other sub-domains.
Organizational unit (OU)
In many cases, a domain may have too many objects to manage all together in one group. This is where Active Directory enables you to create one or more organizational units (OUs) within a domain. OUs let you organize and separate objects within a domain, thereby eliminating the need to create additional domains for these objects.
Another reason to create OUs would be to assign administrative privileges to OU users in a domain. Then, the users within this OU can perform tasks such as creating new user accounts or resetting passwords.
For example, suppose you require assigning a set of users within the domain sales.exampleUS.com with authority to create new users. Then, rather than creating a new domain for these users, you can create an organizational unit called TrialTeam within the domain, and assign it with access to create new user accounts.
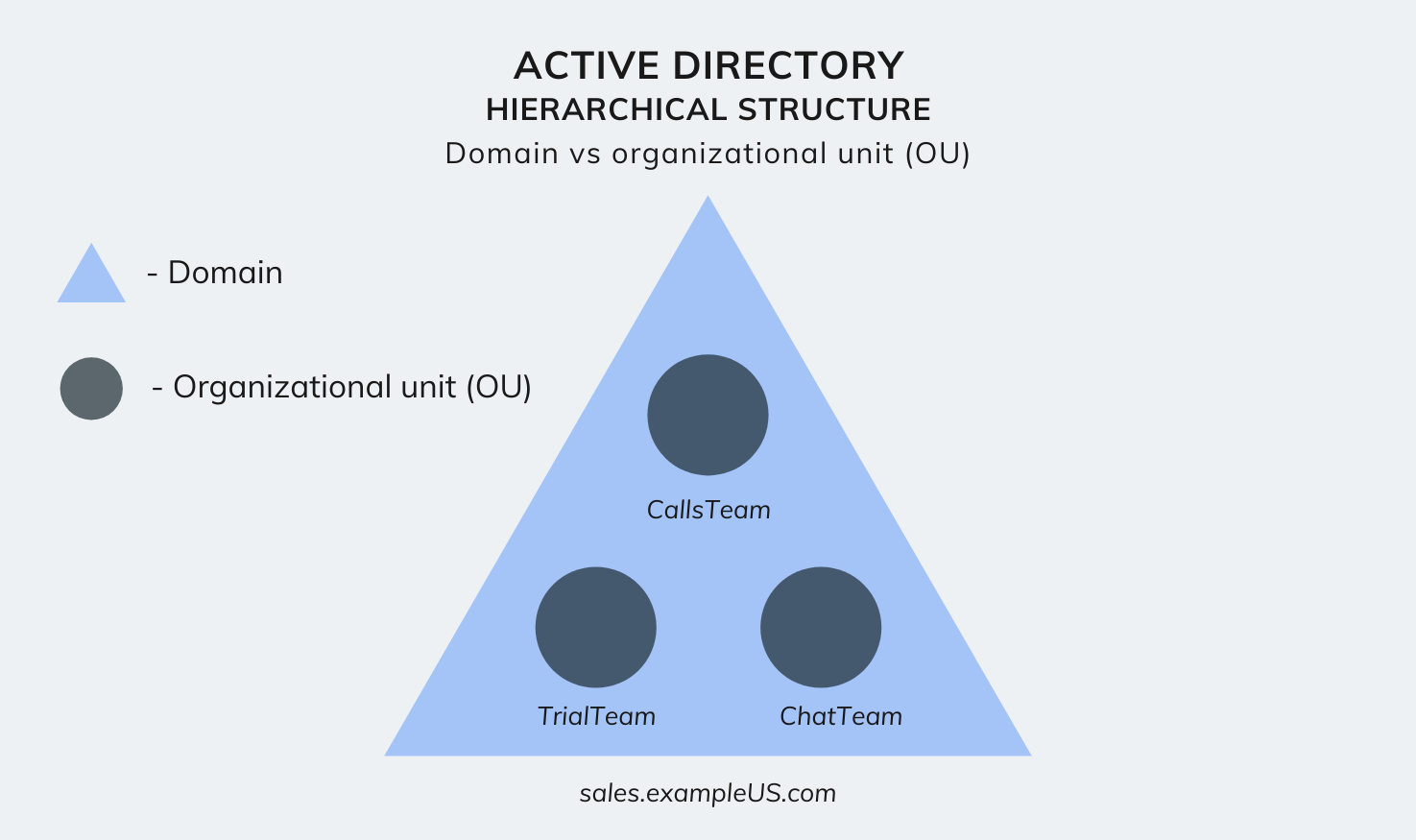 Active Directory hierarchical structure – Domain vs OU
Active Directory hierarchical structure – Domain vs OU
Tree
A tree is a collection of domains that share the same namespace, grouped together in a hierarchical structure. This collection of domains includes the root domain and its corresponding sub-domains. For example, consider the root domain, exampleUS.com, and its sub-domains, marketing.exampleUS.com, and sales.exampleUS.com. Together, these three domains that share the same namespace, form a tree.
Now, another different tree within the AD network could be, exampleUK.com, with its sub domains marketing.exampleUK.com, and sales.exampleUK.com, sharing the same namespace.
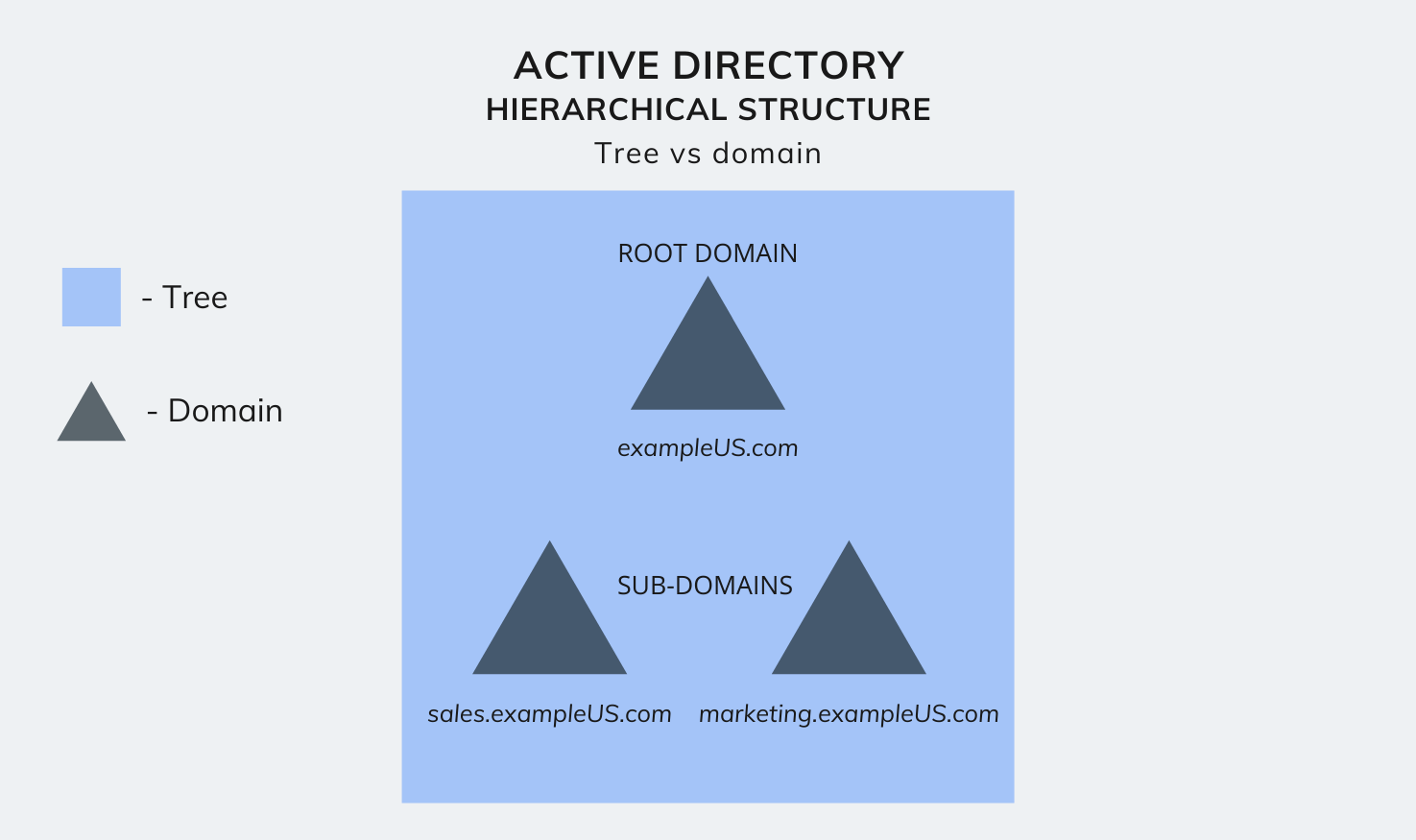 Active Directory hierarchical structure – Tree vs domain
Active Directory hierarchical structure – Tree vs domain
Forest
A forest is the highest level of hierarchy within an AD. It is a complete instance of Active Directory and consists of all the groups of trees. It forms a sort of super-directory, which contains information about all the objects in a forest, regardless of its domain.
By default, information in the Active Directory is shared only within the forest. This way, the forest is a security boundary for the information contained in that instance of Active Directory.
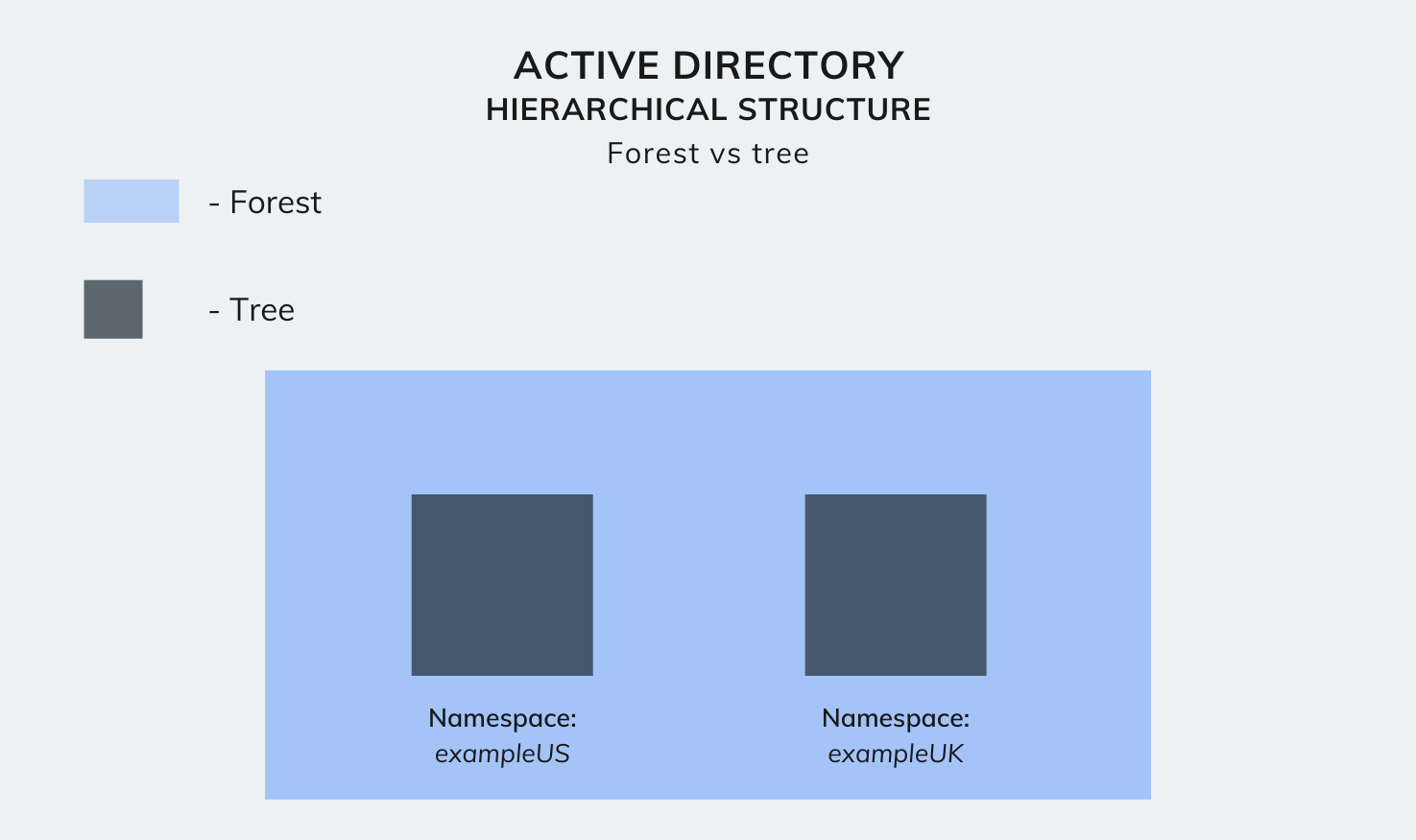 Active Directory hierarchical structure – Forest vs tree
Active Directory hierarchical structure – Forest vs tree
Some Active Directory terms you should know
 Binding Macs to Active Directory
Binding Macs to Active Directory
GID (Group ID) and UID (Unique ID)
The Active Directory database can store around 2 billion objects. Among these objects, there may be multiple users or devices with the same name, or similar attributes. So how do you uniquely identify each of these objects? You got it. This is where unique identification numbers come in.
The Unique ID (UID), user GID, and group GID, are unique identification numbers used to identify the objects in an Active Directory database. Moreover, assigning these unique IDs to each object helps manage the object’s access to company resources.
Active Directory mobile accounts
An Active Directory mobile account enables you to remotely access the data stored in your Active Directory database, even when you’re not connected to the network. Once your Directory Utility’s Active Directory connector sets up your mobile user account, you can use your Active Directory credentials to log in to the AD account on your Mac.
AFP (Apple File Protocol) and SMB (Server Message Block) protocols
Both AFP and SMB are file-sharing protocols that define the commands for opening, reading, writing and closing files across your connected networks/directory services. In addition, it allows devices within the same network to obtain shared access to server-based printers, serial ports, and more.
The primary difference here is, Apple Filing Protocol (AFP) is a macOS network protocol used for sharing files among servers and clients. In contrast, Server Message Block (SMB) is a network protocol used by Windows-based computers.
However, this does not mean only Windows devices can utilize SBM and vice versa. macOS and Windows devices both support AFP and SBM protocols. But that being said, both platforms work best with their native file sharing protocols.
DNS (Domain Name system) and DDNS (Dynamic Domain Name system)
As humans, it’s pretty difficult for us to remember random number combinations. Domain name service (DNS) servers eliminate the need for humans to memorize complex IP addresses (such as 192.168.1.1), by converting them into a hostname (such as www.example.com), whereas, DNS resolution involves converting hostnames to computer-friendly IP addresses, so that web browsers can load the specified internet resources.
However, today, the rapid growth of the internet devices with web access has now created a shortage of available IP addresses. As a result, ISPs change their web services’ IP addresses quite frequently. This is where the need for a DDNS comes in.
Dynamic DNS (DDNS) is a service that keeps the web services’ DNS records updated with the correct IP address, even when the IP address is frequently being updated by ISPs.
How to bind a macOS device to Active Directory
Okay, now that we know a little bit about the Active Directory, I think it’s time we begin binding our Mac to the Active Directory database.
Minimum requirements for macOS Active Directory binding
- Server hardware running Windows Server 2000 or above
- Active Directory Domain Services (AD DS) set up and configured
- Access to a domain account with privileges to create AD users
- A Mac device running macOS 10.5 or above
Integrating Macs to the AD domain is quite an easy process – Since directory services operate pretty much the same across Windows and macOS systems.
To enforce macOS Active Directory binding, follow these steps.
Configure the basic settings
Open System preferences, and navigate to Users and groups > Login options > Network account server, and click on Join. A pop-up will open, asking you to enter the server name.
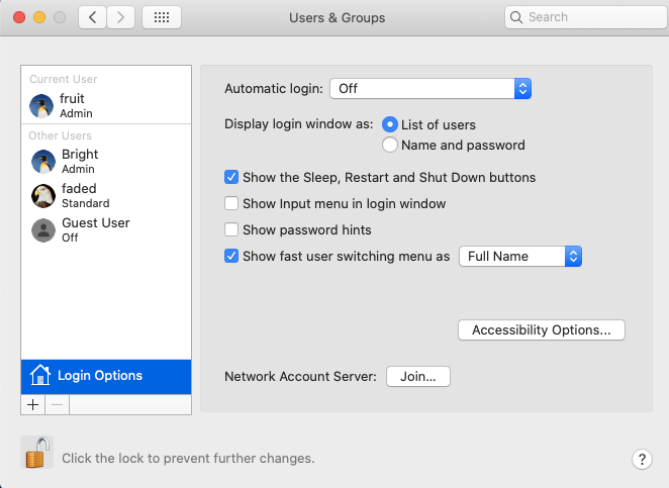 Login options
Login options
Once you enter the server name, macOS automatically detects the AD server. Next, enter the computer ID, username and password of an Active Directory user who has authorization to create user accounts within the specified AD domain.
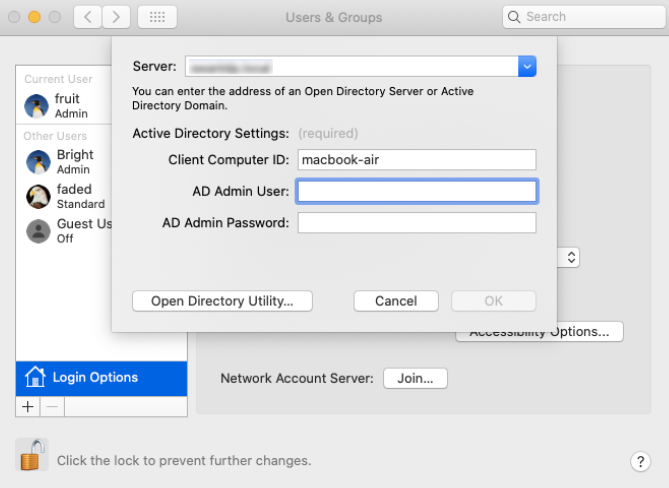 Join network account server
Join network account server
Now, click on OK. Upon successful binding, a green dot will appear next to the ‘network account server’ button.
Modify directory service settings
To ensure the best possible level of reliability between the macOS device and the network resources within the Active Directory server, you must make specific changes to the Active Directory settings using the Directory Utility.
- Open System preferences, and navigate to Users and groups > Login options > Network account server, and click on the Edit button. Then, click ‘Open Directory Utility’.
- Now, double click on ‘Active Directory’ to edit its configurations. Click on ‘show advanced options’. Here, you are presented with three tabs to configure according to your requirements.
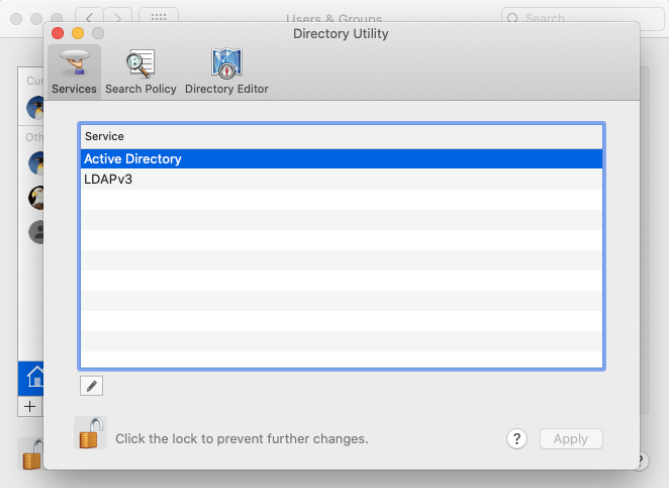 Modify directory service settings
Modify directory service settings
We shall explain each of the settings within these three tabs in detail.
User experience
- Create mobile account at login
Check this option to enable users to log in to their macOS device with their AD credentials even when they are not connected to the AD server. If checked, the user’s data is stored locally on the Mac device.
- Require confirmation before creating mobile account
Check this option to require the Active Directory users to confirm the creation of a mobile account on the macOS device.
- Force local home directory on start-up disk
This option forces the local home directory to be created on the start-up disk of the Mac, thereby enabling the AD users to access their network user accounts remotely.
- Use UNC path from Active Directory to derive network home location
When selecting SMB, a user’s Windows network home folder is mounted as the macOS home folder when the user logs in. When selecting AFP, the AD user is given a local macOS home folder on the start-up disk. What’s more, the user’s network home folder is also mounted as an additional share point. This enables the user to copy files between their network volume and the local home folder.
- Default user shell (default: bin/bash)
A shell is a computer program that provides you with an interface to the device’s operating system. It gathers input from you and executes operations (and displays the output) based on the input. macOS supports Bourne Again SHell (bash) as the default user shell.
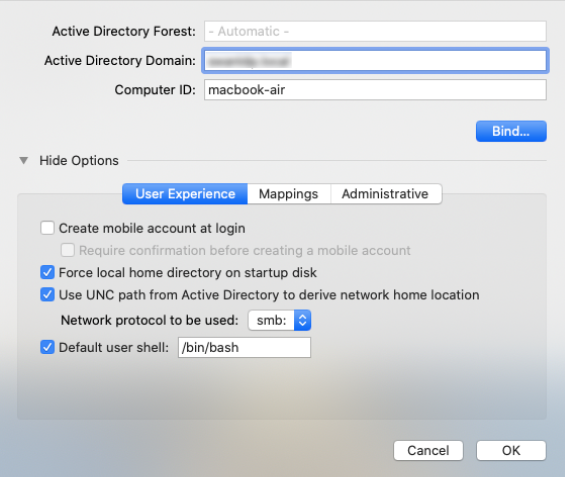 Modify directory service settings – User experience
Modify directory service settings – User experience
Mappings
You can specify AD attributes to map to the group ID, primary/user group ID, and unique user ID (UID) attributes in macOS. However, by default, these are derived from the domain server. It is also important to note that, if you change these attributes later, your users might lose access to their previously created files.
- Map UID to attribute: (eg: uniqueID)
- Map GID to attribute: (eg: primaryGroupID)
- Map group GID to attribute: (eg: gidNumber)
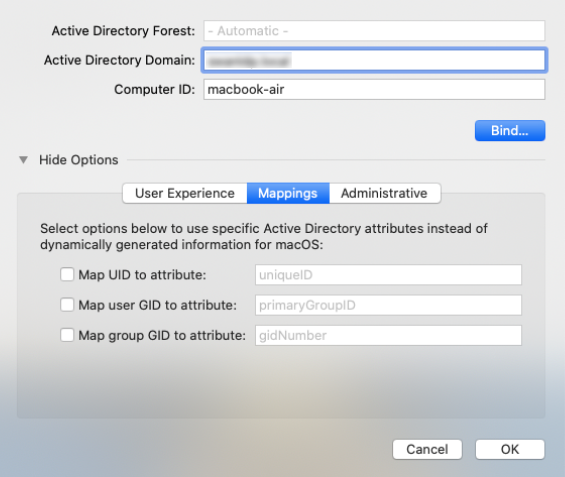 Modify directory service settings – Mappings
Modify directory service settings – Mappings
Administrative
- Prefer this domain server
A domain controller (domain server) refers to a server that manages authentication and security within a network, effectively functioning as the gatekeeper within a domain. It is used to authenticate user identities that attempt to access the Active Directory network and its resources. You can specify a domain controller for authentication here. If none is specified, macOS uses site information and domain controller responsiveness to determine which domain controller to use.
Check this option and add groups to the list. Members listed in the AD groups you specify here are granted administrative privileges on the macOS device. You should also specify the display name of the required security groups. However, if If Allow Administration by is enabled and on AD groups are specified, all the domain and enterprise admins are granted administrative privileges by default.
- Allow authentication from any domain in the forest
By default, after you’ve entered the DNS name of the AD domain, macOS permits users within the Active Directory forest to authenticate from all domains. By unchecking this option, you can restrict authentication to users from just the specified domains.
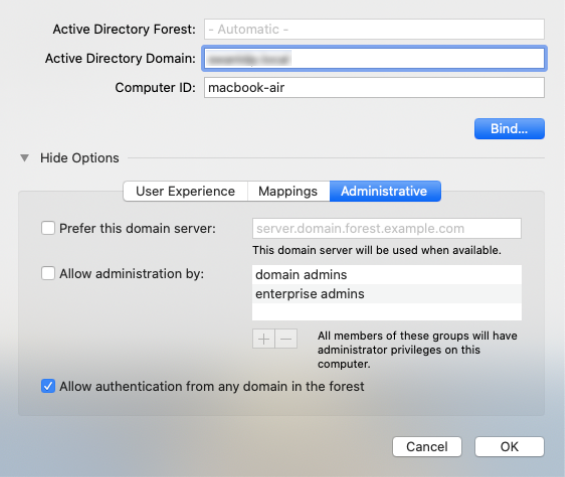 Modify directory service settings – Administrative
Modify directory service settings – Administrative
MacOS Active Directory binding – Troubleshooting tips
- Check if the credentials of the specified domain account are valid. If not, the configuration may fail to take effect.
- The domain account you have provided on configuration must have the rights to manage objects within the organizational unit (OU). Otherwise, the policy will fail.
- If there is a firewall configured, you will need to ensure that the required ports on the Domain Controller are accessible (open) by the macOS system.
Mac AD asset binding with Hexnode UEM
So now you know how to bind your Macs to your organization’s Active Directory server. That’s great! However, before the celebrations begin, there’s just one more small hurdle to clear. Especially if you’re the IT administrator of a company that uses hundreds of macOS devices.
I think you might’ve grasped the issue by now, but here it is. Binding hundreds of Macs to your organization’s AD server one-by-one just takes too much time to be considered feasible. This is where UEM solution like Hexnode can help you.
The absolute guide to Unified Endpoint Management (UEM) in enterprise
With Hexnode’s AD asset binding policy, all you have to do is configure the settings once. You can then streamline the process of binding your corporate Macs to the company’s Active Directory server, and save yourselves lots of precious time.
Hexnode UEM - macOS AD asset binding policy
Basic settings:
- Active Directory domain: Enter IP address or the domain name of the server.
- Username: Enter the username of the account used to authenticate and bind the device to the AD domain.
- Password: Enter the password of the above mentioned account account.
- Organizational Unit: Enter the name of the organizational unit to which the joining computer is to be added.
Advanced settings:
- Create mobile account at login: If checked, the user’s data will be stored locally and automatically logged into the mobile account.
- Require confirmation before creating mobile account: Send a confirmation message to the end user on creating a mobile account.
- Force local home directory creation on startup disk: Forces the local home directory to be created on the startup disk of the Mac. (This option remains checked and cannot be changed if ‘Create mobile account at login’ is enabled.)
- Use UNC Path specified in the Active Directory to derive the network home location: Use the AD standard attribute to set up the home folder location. If unchecked, uses the macOS attribute to set up home folder location.
- Use the Network Home Protocol: Choose either afp or smb protocol for accessing the home folder. (by default, afp is set.)
- Any domain in the forest can authenticate: macOS automatically searches all domains for user authentication. If unchecked, only the domains to which the device is bound to will be allowed to authenticate. on the macOS device
- Default user shell after device log in: “/bin/bash” is used by default.
- Map UID to attribute: Map an AD attribute to the unique user ID
- Map user GID to attribute: Map an AD attribute to the user group ID in user account
- Map group GID to attribute: Map an AD attribute to the GID in group account
- Prefer this Domain Server: Specify the name of the preferred domain server for authentication. If a domain controller specified here is unavailable, Mac returns to its default behaviour.
- Allow administration by: Add groups to this list. All members of the specified group will have administrative privileges on their Mac. (if enables and no groups are specified, all the domain and enterprise admins are granted administrative privileges by default.)
- Namespace:
- Domain: If Domain is selected users have to enter their domain name to login.
- Forest: If forest is selected, user can login with the format, username\password. (if multiple domains in the same forest contain several users with the same user name, users can log in with the domain’s name followed by the login name (domain\login name).
- Packet Signing: Allows you to choose how to ensure data security.
- Allow/Disable
- Require: If enabled, the LDAP connection required to communicate with the AD must be signed by the Open Directory client.
- Packet Encryption: Choose how to encrypt the data.
- Allow/Disable
- Require: If enabled, the LDAP connection must be encrypted by the Open Directory client.
- Restrict DDNS: Specify which interface to use when updating Dynamic Domain Name system.
- Password trust interval: specify how often the computer trust password is to be changed. If you require to have this password never changed, set the value to zero.
The final note
Although Macs can be bound to the Active Directory domain using the above-mentioned policies and configurations, it is important to note that Microsoft’s AD services do not provide the same level of desktop management capabilities that they provide to their native Windows devices.
Corporate Macs cannot be managed by Active Directory domain services (AD DS) using their group policy objects (GPOs). This could turn out to be a pretty big dealbreaker for many businesses.
However, if you require to monitor and manage your corporate macOS devices, you can make use of a UEM solution like Hexnode to streamline Mac management in the enterprise.
Wanna learn how you can manage your corporate Macs with Hexnode?
Read all about it here!







