O.MG cable and remote attacks: Here’s how UEM can help you stay safe
An O.MG cable contains a small network access point which is a powerful tool for cyber attackers.

Get fresh insights, pro tips, and thought starters–only the best of posts for you.
Aiden Ramirez
Jan 25, 2023
8 min read
A man in a black hoodie enters the bank. He approaches the front desk and starts talking to the staff member.
Staff member : Can I help you?
Hacker (man in the black hoodie) : Yeah, I just need to check my account balance real quick.
Staff member : Sure, just let me know if you need help.
The staff member turns to their computer, and the hacker takes advantage of the moment and quickly plugs the USB drive into the staff’s computer while still pretending to be typing something on another computer next to the staff.
Cut to the next scene in the hacker’s lair, where the hacker is sitting in front of a computer with multiple screens, and a stream of confidential information from the bank is being transferred to his computer.
You might have seen similar hacking scenes a dozen times in different movies. The moment you realize that all it takes is one rogue USB drive or accessory plugged into your system for your data to be compromised might have hit you hard. Apple has introduced the accessory security feature as a means of retaliation against the evolving range of such threats. In this blog, we will be looking at how this feature can help you keep your Macs safe from malicious accessories and how you can configure its settings in your Mac.
The new accessory security feature, also known as USB restricted mode, is a security feature that helps protect your Mac against any potentially malicious external Thunderbolt and USB devices. Accessory security puts up a gate whenever you connect an external device to the system. Hence, the device will require the end-user’s permission for communicating with the operating system.
On portable Mac computers with Apple silicon, new USB and Thunderbolt accessories require user approval before the accessory can communicate with macOS for connections wired directly to the USB-C port.
Previously, you could simply attach an external device to your Mac to transfer data or charge it. Mac automatically detects the accessories and gives them access to your computer’s data upon requirement. However, this also paves the way for malicious USB and Thunderbolt devices to damage your system quickly. The latest security addition is guaranteed to provide valuable protection against such hardware exploits.
No matter how secure you think your tech environment is, there will always be vulnerabilities that a cyber-terrorist might take advantage of. According to recent studies, executives of military, aerospace, journalism, energy, and political sectors are the ones who majorly fall victim to these crimes. Although cyberterrorists aim for high-value targets, that might not always be the case. Another side of this that even security professionals fail to notice is commercial espionage. Administrative personnel, engineers, and even frontline workers can be possible targets for obtaining valuable company information.
Situations like these are more than enough for someone with malicious intent to exploit the hardware. Even if the device is locked or in sleep mode, hackers can use methods like cold boot attacks and DMA attacks to boot up the computer and carry out the attack.
Attackers even come up with techniques such as USB drop and Juice jacking, which tempt the end-user themselves to plug the malicious drive into their systems. An interesting study conducted in 2016 showed that 45% of people plugged in a USB stick that they found lying around in the street. Although the study is a few years old, one can claim that the numbers may not have changed a lot.
The working of the accessory security feature is rather straight-forward. When you connect an accessory to your Mac, it will ask for permission to connect the USB accessory. The device can only communicate with your Mac if you click Allow. However, accessories plugged in but not approved can still be charged.
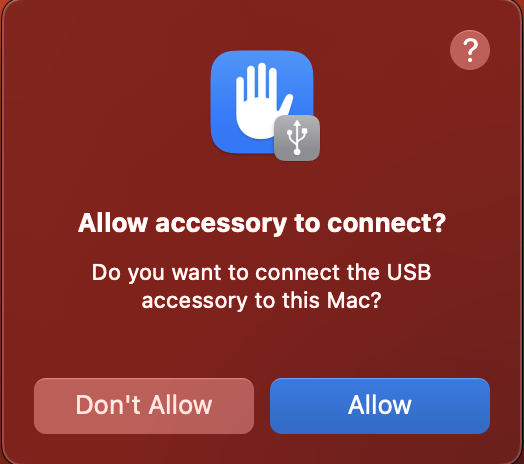
If your Mac is locked when you plug in the accessory, you must unlock it first and grant permission. All accessories connected are automatically allowed while upgrading macOS to Ventura. However, it might not be remembered once you restart your device. Therefore, you might have to grant permission again after unlocking.
The accessory security feature is turned on by default in Macs running macOS Ventura. However, some users might feel their environment is safe and find it annoying to have accessories asking permission whenever they connect an accessory. In such cases, you can disable or change the security settings to suit your preference.
To configure the accessory security settings, follow these steps;
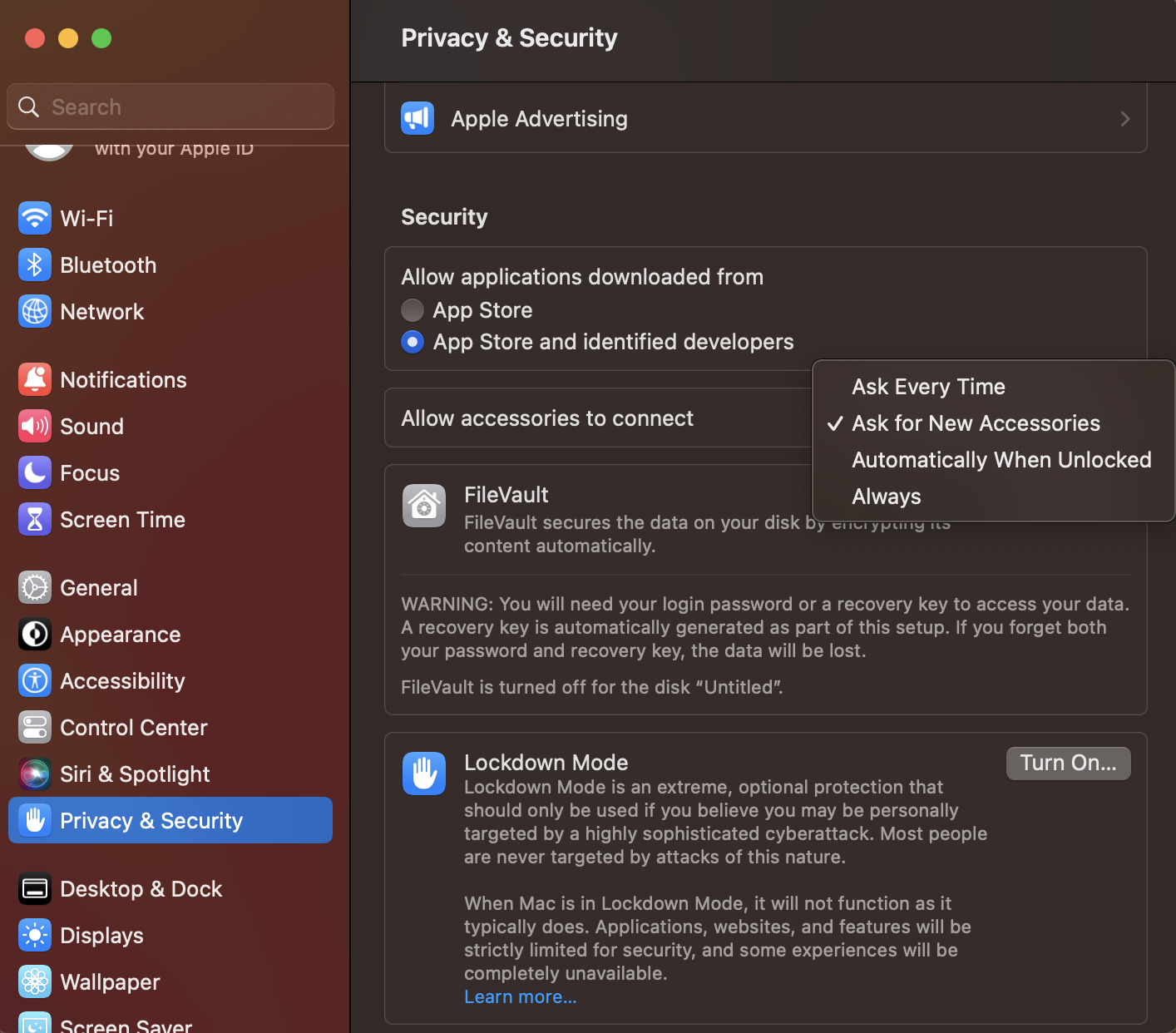
There are four options available for you to manage your accessory connections;
In conclusion, the accessory security feature is a game-changer in protecting your Macs from unauthorized data transfer. It gives you control over what data is being transferred and by whom. However, it is always better to fortify your defenses than be exposed to unwanted threats. You can take advantage of third-party antivirus software and devices such as USB data blockers to ensure the accessories you use are safe.
Another way to safeguard your macOS devices is to couple them with a UEM solution such as Hexnode. As the saying goes, a chain is only as strong as its weakest link. Hexnode can help you ensure you have complete control over your devices in terms of both security and management. Hexnode follows a zero-trust approach encompassing multi-level threat monitoring, detection and protection.
Get started with Hexnode’s Mac Management solution to save your time and the associated IT operational costs of managing your Mac devices.
Featured resource
Hexnode Mac management
You can enhance the security of your Macs by enforcing passwords, user access control, and web-content filtering policies. You can even manage FileVault with Hexnode, which lets you easily encrypt and decrypt your device data. This is just the tip of the iceberg. There are still plenty of features available to build a multi-faceted security infrastructure around your device fleet. So, get started and upgrade your security framework right away with Hexnode.
Sign up for a 14-day free trial to secure your digital environment with the power of Hexnode.
SIGN UP NOW
Share your thoughts