How to ensure privacy and security in business Macs
How important a role does a UEM play in ensuring security and privacy in your business Mac? Read this blog to find out.

Get fresh insights, pro tips, and thought starters–only the best of posts for you.
Aiden Ramirez
Jul 24, 2023
6 min read

What aspects come to mind when you think about Unified Endpoint Management (UEM)? Managing and controlling the endpoint devices will be one of the obvious answers. What else? Device security? Keeping corporate data secure is one of the main reasons why we have device management solutions in the first place. End-user experience is also a worthy contender in this list.
In today’s digital world, security of corporate devices is not just an IT concern but a top priority for enterprises. Protecting sensitive data and confidential information is especially vital for maintaining the integrity of a company’s operations. Endpoint management solutions keep security as the cornerstone for this reason. Consequently, each step towards attaining a better security infrastructure is of high value in the device management sphere.
In keeping with the emphasis on security, Hexnode’s newly launched Hexnode Access App has been thoughtfully crafted to enhance the login process for Macs and provide an added layer of security. In this blog, we will delve into how this app provides enhanced security during the login process on your Macs.
Hexnode Access will replace the default macOS login window with a customizable login window. It also brings some new features to the plate. Let’s have a glimpse at them.
The new feature allows admins to authenticate end-user credentials with cloud-based identity providers. This is in addition to the local account credentials, which the users will have to authenticate later on. With this dual-stage authentication process, the system can better ensure the identity of users and provide an extra layer of protection for sensitive data and information.
You can easily pre-configure your identity provider and provide the necessary information, such as Client ID, through the Hexnode portal. Once you’ve specified which users should have access, you can easily push the policy to the relevant devices. This makes the authentication process seamless for both administrators and end users while ensuring the security of your data.
IT administrators can enhance the login experience for users by incorporating custom wallpaper and logos by using Hexnode Access. Customizing the login screen is as easy as uploading a background image and logo into Hexnode portal. This not only enhances the overall user experience but also serves as an opportunity to reinforce the company’s brand identity through visual branding elements.
You can pre-configure Hexnode Access with your identity provider account. Firstly, the user is presented with the login window depending on the configuration you deployed. On successful authentication by the respective identity provider, the app will check if the cloud identity is linked to any local accounts. If yes, the user is presented with another window prompting for credentials of the local account connected with the cloud identity. On successful verification, the user can log in to his or her home window.
If the cloud identity is not linked to any local accounts, the user will be presented with a migration window where they can choose to connect to any of the free, unconnected local accounts or create a new user. Take a look at the graphic given below to quickly understand the login flow of the app.
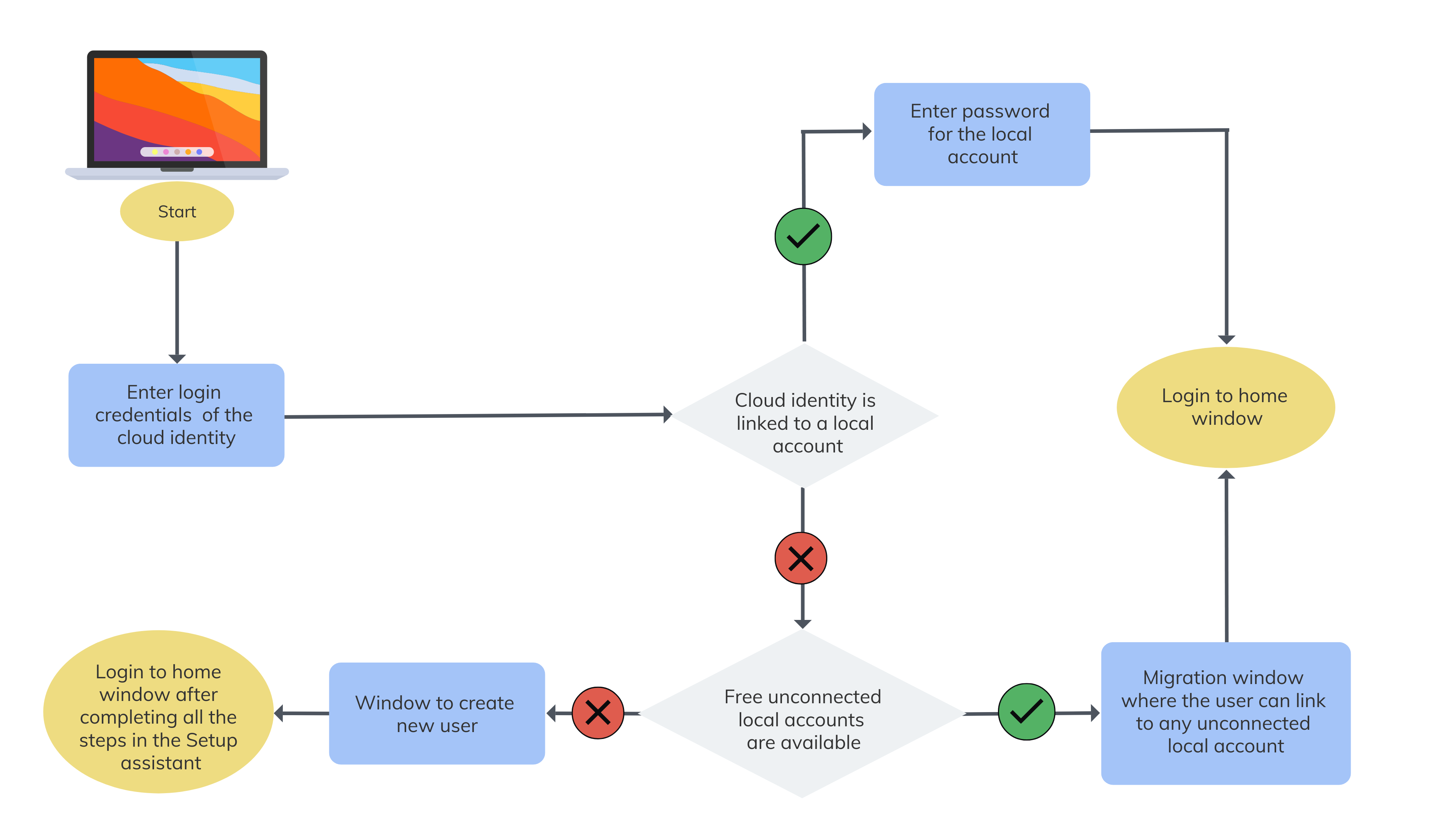
In addition to the cloud-based identity login, users can also opt for a local login by simply providing the username and password of their local account. Upon successful verification, the user can login to their home window.
We’ve uncovered all that Hexnode Access has to offer. Now it is time to answer the bigger question: what additional advantages does it bring to the equation? Let’s have a quick look at how this new addition can help your organization.
In addition to the Access app, we have a range of other security-focused features. You can remotely configure the in-built macOS security features such as Firewall and FileVault in your entire device fleet to protect your Mac from network breaches and to ensure the protection of your data. You can also set restrictions on the web content and media that end users can access in their work profiles. These are in addition to all the policies related to app management, network management, managing accounts, etc. at your disposal. In short, all these features work together to enhance the overall security of your device fleet and ensure that your data is always safe and secure.

Get this white paper to know more about Hexnode’s Mac management features to simplify device deployment, enhance security, deploy OS updates.
DOWNLOAD PDFI wasn’t kidding when I said we at Hexnode keep security as the cornerstone. You can even say that security is in our DNA😄. With Hexnode, you can rest easy knowing that we’re constantly working to stay one step ahead of potential security threats and to ensure you get maximum capabilities from your devices. So, whether you’re managing a handful of devices or a large fleet, we’ve got you covered!
Start your 14-day free trial to get a first hand experience on Hexnode's Mac management capabilities.
SIGN UP NOW