Missed out on Day 1 @HexCon22?
We've got you covered. Check out this blog to catch up on everything you missed at Day 1.

Get fresh insights, pro tips, and thought starters–only the best of posts for you.
The second day of HexCon22 has come to an end. With a host of incredible sessions on cybersecurity, incident response, data privacy, and more, we’ve got some great highlights lined-up for you.
Read more to catch up on the talks, interviews, and discussions you may have missed at HexCon22.
Day 2 officially kicked off with Joe Tidy, BBC’s first cyber security correspondent, sharing his insights and knowledge in an interview session with Sarika Abraham, Media and Public Relations Manager at Hexnode.
Joe talked about many of his interesting stories from his days of investigative journalism, where he met and interviewed many famous cybercriminals, from the notorious hacker group called ‘Lizard squad’, who hacked the networks of PlayStation and Xbox Live, to cybercriminals and malicious hackers from countries all around the world.
He answered questions including how it is when you contact these malicious actors, why they do what they do, the risks involved in meeting and interviewing these agents, and more.
In fact, here’s something that caught my eye.
“The one thing that almost always connects the cybercriminals and hackers, they always started off as gamers. There’s a real intersection between gaming and hacking.”
As a fellow gamer, this was certainly an eye-opener 🙂
Moving on, Joe shared his valuable insights on how to remain safe in the cyber world. He talked about,
With over 25 years of experience as an FBI agent, and over 5 years as a corporate security executive specializing in intellectual property protection, Frank Figliuzzi talked about protecting what matters most – Your company’s crown jewels.
He kicked off the session by establishing a simple but effective analogy between protecting the royal crown jewels of England, and protecting your company’s critical components.
Akin to protecting and preserving the crown jewels while at the same time putting them on display for the entire world, Frank talks about how businesses should identify their critical business information (CBI), understand, secure, and preserve them, even in the frenzied threat and business environment of today’s business world.
He talked about the 3 core questions executives must ask, to help build a plan, or review and adapt an existing plan into a mature model – What, where and who.
“If done correctly, this approach provides a laser-like focus on what really matters.”
– Frank Figliuzzi, @HexCon22
Moving on, he talked about how executives should go about answering the questions, what where and who.
With 29 years of experience in cybersecurity, information technology (IT) operations, audit & risk management, and incident response and investigations, Mike Saylor, CEO and Executive Leader at Black Swan Cyber Security, LLC, covered crucial aspects of incident response strategies, including,
Mike began the session by comparing a data breach to a typical train wreck.

He talked about what it takes to prepare for a cyber incident, and the difference in response time to a breach when an organization is prepared, and unprepared.
To be prepared, businesses must,
Moving on, Mike shows a basic timeline of ransomware response activities businesses should follow depending how much time has elapsed, from hour 1, 12 – 72 hours, to 1 – 48 months.
He provides an in-depth checklist for companies to be prepared with an incident response plan, including questions like,
Mike gave detailed instructions on how to perform a table top exercise, by laying out all the steps involved.
Planning and designing:
Training day:
Remediation:
Mike concluded the session by talking about his war stories, where he assisted a variety of public and privately-held companies, as well as government, not-for-profit and educational institutions, and gave recommendations for being more effective in their incident response capabilities.
With nearly 40 years of experience working in all aspects of computer, network, and information security, Jeffery Mann, Information Security Consultant at Online Business Systems, shared his insights on what used to be known as information security and is now referred to as cybersecurity.
Jeff began the session by contemplating on the first lesson he learnt in data security, during his tenure as an intern in a DoD research facility – the importance of layered security in data protection.
He talked about the differences and similarities between cyber security and information security.
Jeff says, when it comes to protecting data, the processes splits up into 3 categories – Confidentiality, Integrity, and Availability – The CIA triad.
He moves on to give a very simplistic depiction of how to calculate the values of risk, called ‘the risk equation’, marking the overall goal as to reduce or decrease the risk that a business is experiencing.
The risk equation: risk = vulnerabilities + threats – countermeasures
Where,
Moving on, he talked about the 3 elements of information security – People, processes, and technology.
However, Jeff says,
“If you don’t have some sort of understanding on why you’re doing, what the purpose is, you’re gonna spend a lot of needless time and money, and may miss the point of securing your environment.”
With that, Jeff brings up a fourth ‘new’ element of information security, the ‘Purpose’. He moves on to explain how and where these elements fit into the risk equation, and introduces the ‘risk-based security model’, which fulfils a more commercial context.
Risk-based security model: risk = (vulnerabilities + threats – countermeasures) * value of data
Mike Crandall, founder and CEO at Digital Beachhead, talked about the relations and interdependencies between security and compliance, and how companies can bridge the gap between the two.
Mike kicked off the session by giving a brief definition on ‘what is cybersecurity’. He introduced the different definitions associated with cybersecurity, and talked about the ‘myths’ of cybersecurity and compliance.
He talks about the differences between compliance and security, where,
Moving on, Mike offered real-world examples of compliance ‘fails’, including some of which he encountered during his time at Digital Beachhead.
He talked about how compliance can be expensive to maintain, and stressed the importance of focusing on ‘reliable’ security mechanisms to meet compliance requirements.
Mike reiterates how compliance does not always guarantee security, and that as cyber professionals, executives must focus on enforcing and maintaining cybersecurity, and go beyond simply meeting regulatory compliance requirements.
Mike moves on to talk about how cyber risk management is an ever-evolving cycle with no end-goals, and with it comes the need to always evolve and change with the risks that pop up.
“Knowing what risks are still out there, and deciding on what risks you’re willing to accept is a key part of cyber risk management.”
– Mike Crandall @HexCon22
Tina Gravel, CEO of Pinecone Hill, LLC, talked about the importance of zero-trust in cyber security, and elaborates on practical ideas around what can be done to protect public or private firms by implementing Zero Trust.
Tina began the session by talking about how the cloud, SaaS adoption, and distributed computing on the public internet has led to increased threats including intrusion, fraud, ransomware, phishing, and viruses.
In such a scenario, the workplace perimeter is no longer static. Rather, it is dynamic. Moreover, exponential data growth has led to increased privacy requirements.

Tina talks about the history and definition of Zero-Trust, and how it is not simply one single software or product.
“Zero-Trust is a cybersecurity strategy premised on the idea that no user or asset is to be implicitly trusted.”
She moves on to talk about the NIST framework for a successful zero-trust strategy, and how to navigate through the complexity and noise of zero-trust. Tina talks about the need for zero-trust and provides valuable insights and resources to help organizations put a zero-trust strategy in place.
Ben Owen, Co-Director of Fortalice Solutions, talked about the rise in social engineering attacks targeting individuals and businesses, and the tools used by social engineers to target individuals.
Ben showcased a live case study to enlighten us about the ways social engineers use to scrape out the personal data of individuals. He talks about the kind of information these attackers look for, including,
The end goal of these attackers? – To use social engineering to scrape out personal data and create a believable attack strategy to target individuals.
Ben showcased some of the tools used by these social engineers, including,
Many organizations are facing cybersecurity concerns as they strive to speed up their digital transformation. Cyber security and GRC Architect Brett Osborne explained the need to modernize the security goals to keep up with this transformation. He kicked off the session by explaining the traditional security goals.
Although these are the fundamental objectives, they don’t touch all domains of cybersecurity. Brett proposed three more security goals to further strengthen the security infrastructure.
Brett concluded the session by mentioning that security objectives need to be updated as data security is always evolving.
Is security something that can be left isolated to a specific team in the final stages of development? Or should it be integrated as a shared responsibility throughout the entire IT lifecycle? Cybersecurity experts Sam Sehgal, Chris Kirschke, and Kapil Bareja talked about the need to integrate security into the “Software Development Lifecycle” in the panel discussion with Amith Manoj, the Lead Brand Strategist at Hexnode.
The session began with the experts talking about the important security considerations for a DevOps team. According to Chris Kirschke, security is to be integrated into DevOps to speed up delivery without compromising security. This is essential to reduce risks in the lifecycle.
“You can’t have security for DevOps until you have a DevOps for security.”
-Kapil Bareja, @HexCon22
Sam Sehgal explained that security belongs in every stage of a software development lifecycle, starting from the requirement to deployment. The cost of fixing a security bug will always be cheaper in the early stages.
The session ended by addressing the biggest challenges teams face while adopting DevSecOps. According to Kapil, the abundance of security tools available today makes it difficult for organizations to decide on the most suitable one for their organization. Sam added that it is essential to have proper instrumentation to periodically track the success or failure rates of the security policies.
Making mistakes is an essential aspect of the human experience; it is how we learn and evolve. However, human errors are much too often neglected in cyber security. Christopher Crummey, Director of Executive and Board Cyber Services at Sygnia, talked about the human factor of cybersecurity through real events of cybersecurity breaches in the previous decades. He also mentions the steps taken by mature companies to mitigate human errors.
Christopher began the session by talking about the typical causes of data breaches, including,
He went on to point out that all these cyberattack vectors have a human element beneath them. He then explained how threat actors use the concept called “perception blindness” to get what they want from the employees.

This concept uses creative ways of catching people off-guard. The threat actors also leverage human emotions such as fear, greed, curiosity, and urgency to make them distracted.
Mature companies have come up with strategies to reduce the risks of security breaches, which include,
IT admins often find it difficult to keep track of IT devices. These devices can remain in the field for many years indefinitely. Hence, setting clear compliance standards for these devices is crucial to achieving consistent security. Zhanwei Chan, IoT Lead of CheckPoint Software Technologies Ltd explained how global organizations are securing their OT, IoT, and unmanaged devices.
Zhanwei Chan starts by saying that IoT devices are involved in so many sectors such as;
There have been numerous cyber threats in the past in non-IT organizations also. Some of them include Honda, Loop, Polycom, and KNX. This makes it evident that you can’t use traditional cybersecurity as it is. You need specialized technology which needs to be thought of very well.
The root causes for these threats can be summarized as:
The solution to all these threats starts with generating visibility for these devices. This includes discovering the device and identifying its connection profile. Then comes the step of enforcing network segmentation and virtual patching.
Zhanwei Chan concluded the session by mentioning that the first step in making sure your IoT devices are compliant is to identify them.
“You can’t protect what you can’t see”
Environmental, Social, Governance (ESG) criteria is widely used by investors to assess the social responsibility effort of companies. This framework is designed to be integrated into an organization’s strategy to enhance the enterprise’s value. Dr. Valerie Lyons, who is the COO of BH Consulting, talks about why companies should entrench privacy along with the ESG criteria.
ESG simply means using Environmental, Social, and Governance factors to evaluate companies on how far they are advanced with sustainability. It focuses on qualifying and quantifying a company’s impact on the environment and the control it has in place to ensure ethical operations.
Some of the policies that are included in each of these criteria are:
Environment
Social
Governance
The objective of Privacy as an ESG or ES(p)G is to gain market advantage by focusing on privacy initiatives that align with customer values. Organizations undertaking this program understand the profile of their customers and the factors that lead to trust.
The three key ESG strategies or privacy include:
What are cloud identity and access management? How can we prevent our cloud identities from being compromised? Dwayne Natwick, the Senior Product Manager at Cloudreach answered these questions through his five recommendations to secure cloud identities.
In simpler terms, cloud identity and access management enable the right individuals to access the right resources at the right time. Identity providers such as Google and Microsoft control the permissions and access for users.
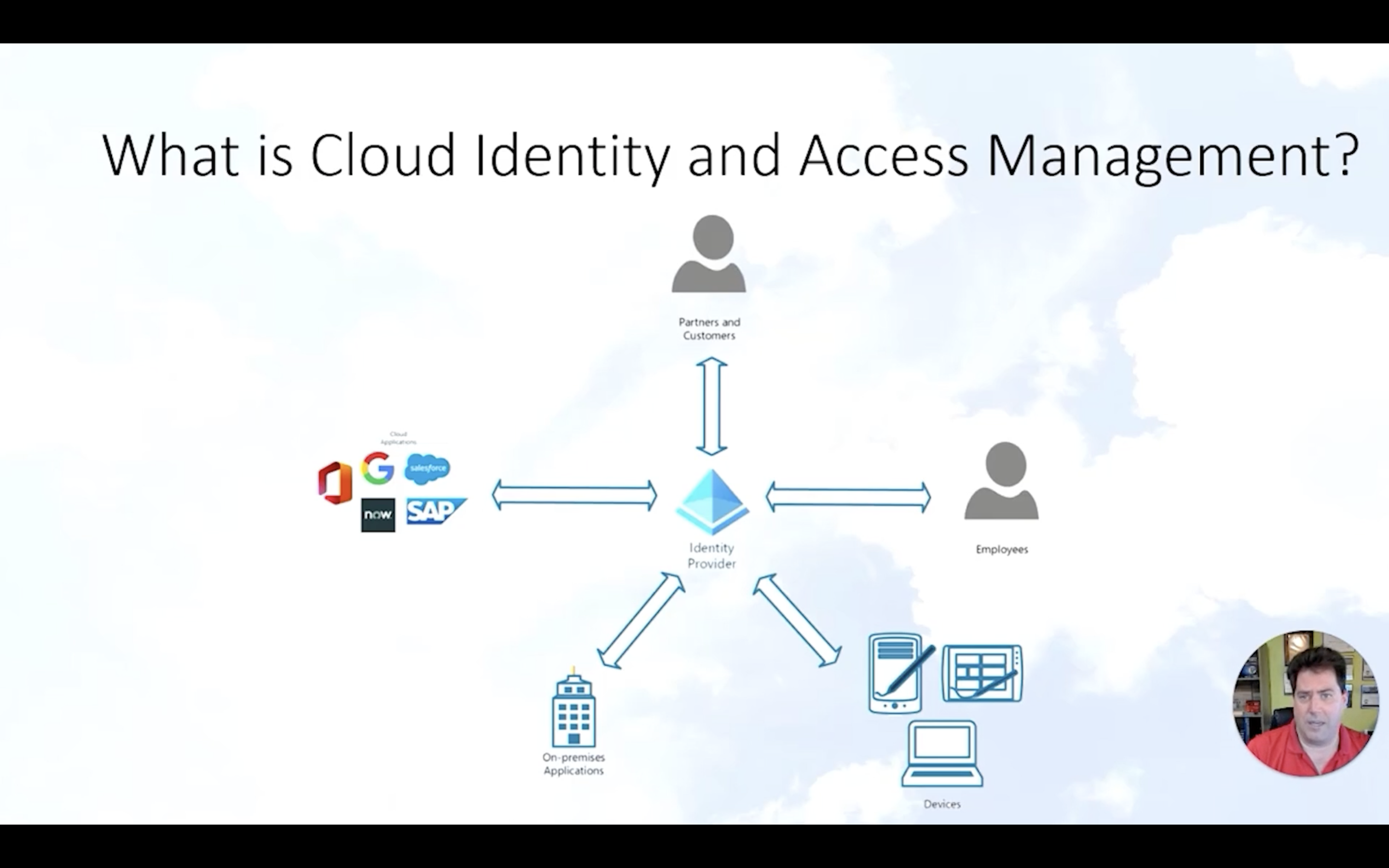
Dwayne Natwick also put forward five recommendations to secure cloud identities.
Lastly, Dwayne concluded the session by stating that implementing these elements and not affecting the user experience comes down to planning the communication. A proper communication plan where all the elements work together will ensure a secure identity infrastructure across cloud applications.
Sharon Knowles, Founder of Da Vinci CyberSecurity takes a look at data breach response measures from a different perspective. She states that having effective leadership is as equally important as having appropriate technical remedial measures to make sure your organization comes out of a data breach unscathed.
Sharon started the session by taking us through an interesting thought experiment: “If you discovered right now that your organization has a data breach, would you know what to do?” Companies adopt different response plans of action in the event of a cyber-attack. Sharon talked about three essential steps that the management should take to mitigate the risks.
The first step would be to make sure that the person who is responsible for initiating the response measures has a well-rehearsed and effective cyber resilience plan. There should be proper classification of cyber security incidents. This is essential in making sure incidents are handled correctly with appropriate measures.
Another major role of management is to understand what people need from the management and by responding to it. Staying focused on external communications and providing a timely response is critical.
Well, that’s it for Day 2. All the insightful sessions, interviews, and discussions made for an exciting day no doubt.
Stay tuned for Day 3 where there’ll be more exciting sessions in store!
Share your thoughts