IT Admin’s Guide to Patch Management with Hexnode
All you need to know on patch management with Hexnode—set policies, automate updates, monitor and manage OS and app patches with complete visibility.

Get fresh insights, pro tips, and thought starters–only the best of posts for you.

Cyber threats continue to grow in complexity and frequency, putting immense pressure on IT teams to secure their infrastructure. One critical line of defense is effective patch management, ensuring that systems remain updated and protected against known vulnerabilities. This article helps you understand the intricacies of patch management, focusing on the challenges faced by the tech industry, and the compelling need for a well-structured patch management strategy.
Patch management is the proactive process of identifying, deploying, and managing software updates, or patches, to rectify vulnerabilities, enhance performance, and boost security. It is a systematic approach to maintain the health and functionality of the endpoints by regularly applying software updates or patches. These patches are released by Microsoft (for Windows devices) and Apple (for Mac and other Apple devices) to address various issues, including security vulnerabilities, software bugs, and performance enhancements. Managing updates across this spectrum requires a nuanced understanding of the operating system’s architecture and the specific challenges posed by various hardware configurations.
Patch management serves as a defense against security threats, safeguarding sensitive data and strengthening the security posture of managed devices. It ensures that known vulnerabilities are promptly addressed, reducing the attack surface and enhancing overall resilience.
Swift and automated deployment of patches minimizes device downtime, ensuring seamless operations and productivity. This is especially critical in business-critical environments where even short periods of disruption can have significant financial implications.
Meeting regulatory standards is imperative for organizations. Patch management aids in compliance by keeping systems up-to-date and secure, providing evidence of due diligence in maintaining a secure computing environment.
From device lifecycle management to repair expenses, a proactive patch management strategy can yield cost savings. Timely updates reduce the likelihood of security incidents that might result in costly data breaches or system failures.
Patching not only addresses vulnerabilities but also enhances the overall functionality of the devices. Performance optimizations, feature updates, and bug fixes contribute to a smoother and more efficient user experience.
Efficient patch management simplifies the tech support landscape, reducing the burden on IT teams. With fewer issues stemming from unpatched vulnerabilities, tech support can focus on strategic initiatives and higher-value tasks.
To understand the situation better, imagine a finance team rushing to close the fiscal year on 40 Windows systems. The IT admin identifies a critical patch and requests a 3–4-hour downtime. Due to tight deadlines, the team postpones it to next week. A few days later, all 40 systems are hit by ransomware. Sensitive financial data is at risk, and the organization faces chaos as the ransom surpasses the entire year’s budget projections.
This situation could’ve been avoided with an efficient patch management strategy—one that includes risk-based prioritization, communication between teams, and the ability to schedule updates during non-peak hours or automate patching with minimal disruption. Proactive planning and the right tools can make the difference between a minor delay and a major disaster.
A well-defined patch management strategy is crucial for maintaining a secure and resilient IT infrastructure. It efficiently coordinates timely updates, addressing new features, performance improvements, and security vulnerabilities. It ensures regular, non-disruptive patching tailored to the systems, preventing clashes with employees’ productive hours. Furthermore, a patch management strategy, in adherence to regulatory standards like HIPAA and GDPR, plays a crucial role in ensuring compliance. This compliance not only shields against audits but also fosters trust by consistently improving products and services with secure functionality.

Simultaneously, the strategy mitigates risks through methodical testing and deployment of updates, reducing the likelihood of security incidents. Furthermore, it facilitates strategic planning by outlining patching frequency, prioritizing critical updates, and establishing efficient communication protocols, ensuring optimal resource allocation.
Patch management covers a range of updates, each designed to address different aspects of software performance and security. One of the most critical among them is security patches, which fix known vulnerabilities that could be exploited by attackers. These are often released urgently and prioritized to reduce the risk of breaches.
Bug fixes are another essential type, targeting issues that affect functionality or performance without adding new features. In contrast, feature updates or OS upgrades introduce new capabilities, interface changes, and performance improvements, often on a scheduled release cycle.
Some updates are more urgent in nature. Hotfixes are released outside regular patch cycles to resolve specific, high-impact issues quickly. While less common today, service packs used to bundle multiple fixes and updates into a single package for easier deployment.
Other useful categories include cumulative updates, which consolidate all prior patches, and rollup updates, which target a specific set of issues. Driver and firmware updates improve hardware stability and performance, while third-party patches—from vendors like Zoom or Adobe—are vital for securing the broader software ecosystem. Zero-day patches stand out for their urgency, addressing vulnerabilities already under active exploitation. A clear understanding of different types of patches helps IT teams prioritize updates effectively and maintain a secure, stable IT environment.

Selecting the right patch management solution is more than just ticking boxes – it’s about aligning the tool with your organization’s unique needs and IT infrastructure. Here are a few key factors to consider when evaluating patch management software:
1. Platform compatibility
Ensure the software supports all operating systems and devices in your environment – Windows, macOS, Linux, mobile platforms, and even third-party applications. A cross-platform solution simplifies patch deployment across diverse endpoints.
2. Automation capabilities
Look for tools that offer automated patch scanning, scheduling, deployment, and rollback. Automation reduces manual effort, minimizes human error, and ensures timely updates without disrupting productivity.
3. Customization and control
The ability to customize patch policies – such as setting approval workflows, defining maintenance windows, and excluding specific updates – is crucial for maintaining operational flexibility.
4. Reporting and compliance
Robust reporting features help track patch status, identify vulnerabilities, and demonstrate compliance with industry standards and regulations. Real-time dashboards and audit logs are a big plus.
5. Integration with existing tools
Choose a solution that integrates seamlessly with your existing IT management stack – whether it’s endpoint management, or SIEM systems. This ensures smoother workflows and better visibility.
6. Scalability and support
As your organization grows, your patch management tool should scale with it. Check for vendor support, documentation, and community resources to ensure long-term reliability.
Effective patch management is more than just deploying updates—it’s a structured, continuous process that ensures systems remain secure, stable, and compliant. The lifecycle typically follows a series of stages, each playing a critical role in minimizing risks and maximizing uptime.
 Steps in Patch Management
Steps in Patch ManagementThe process begins by monitoring for new patches released by vendors. This includes OS updates, application fixes, and security advisories.
Each identified patch is evaluated based on severity, relevance, and potential impact. Critical vulnerabilities and high-risk systems are prioritized for faster deployment.
Before rolling out patches across the organization, they’re tested in a controlled environment to avoid compatibility issues or disruptions in business-critical applications.
Once tested, patches are deployed to target systems using automation tools or manual processes—depending on urgency and environment complexity.
Post-deployment, IT teams verify successful installation and system stability to ensure that updates have not introduced any new issues.
Detailed logs are maintained to track patching activities, compliance status, and system health—helping with audits, future planning, and continuous improvement.
A well-defined patch management lifecycle ensures every update is delivered with precision. This results in minimizing downtime, maximizing compliance, and reinforcing security posture. By treating patching as a continuous process rather than a one-off task, organizations can stay ahead of vulnerabilities while maintaining operational efficiency.
Patch management has evolved from rigid, manual processes to more adaptive and user-friendly methods. Traditional patching typically focuses on deploying specific fixes for known bugs or vulnerabilities. It’s common in legacy systems like older Windows and macOS applications, where updates are discrete and non-cumulative. The process often involves blocking user access, testing on pilot devices, and then deploying patches in controlled batches.
Modern patching, on the other hand, is more streamlined. Updates are cumulative, often combining security fixes with feature enhancements. Found mostly in modern OS ecosystems like Apple’s, this approach supports user-defined deadlines and admin-imposed maintenance windows. Tools like Hexnode enable granular control over patch deployment—allowing IT admins to schedule updates intelligently without disrupting end users.
The shift toward modern patching reflects a broader focus on flexibility, automation, and end-user experience, something that legacy methods often lacked.
In today’s threat landscape, patch management isn’t just a routine IT task – it’s a frontline defense against costly breaches, ransomware, and compliance failures. Yet, many organizations still struggle with delayed patching, manual workflows, and limited visibility. Here are some eye-opening facts that highlight why patching – and automating it – is critical for every organization.
Key Stats That Speak Volumes

Patch management doesn’t happen in a vacuum. From rapidly evolving threats to the sheer diversity of devices and software, maintaining a secure ecosystem poses significant hurdles.
Despite its importance, patch management comes with a set of challenges.
Coordinating and deploying patches in a timely manner can be challenging, especially in large and complex environments. Delays in patch deployment leave systems exposed to potential exploits.
Patches may inadvertently introduce compatibility issues with existing software or configurations. Thorough testing is crucial to identify and address these issues before widespread deployment.
In environments where end-users have control over their devices, resistance to updates can pose challenges. Educating users about the importance of patches and implementing user-friendly update processes are key strategies.
Despite thorough testing, issues may arise post-patch deployment. Having robust rollback plans and mechanisms is essential to mitigate the impact of unforeseen complications.
Automation in patch management simplifies the entire workflow—from identifying patches to deploying them efficiently. Automation is no longer a luxury—it’s essential to keep pace with the scale and complexity of modern IT environments. The need for automation arises from the increasing volume and frequency of patches, the complexity of IT environments, and the imperative to reduce manual intervention.
A Patch Management software automates the entire patching lifecycle, covering identification, deployment, monitoring, and reporting. This boosts efficiency, strengthens security, minimizes manual errors, and enables organizations to adeptly address evolving software vulnerabilities.
Let’s walk through a simple example to understand how patch management works in a real-world scenario.
Scenario:
A mid-sized enterprise uses Windows and macOS devices across departments, along with third-party applications like Zoom, Adobe Reader, and Chrome. The IT team wants to ensure all systems are up to date and secure.
Step-by-step patch management process:
Asset discovery: The IT team uses an endpoint management tool to scan and list all devices and installed applications.
Patch assessment: The tool identifies missing patches, including a critical security update for Windows and a vulnerability fix for Adobe Reader.
Testing: Before deployment, patches are tested on a small group of devices to ensure compatibility and avoid disruptions.
Deployment: After successful testing, patches are rolled out in phases – starting with high-risk systems and gradually expanding to the rest.
Monitoring and reporting: The team monitors patch status through dashboards and generates compliance reports for auditing purposes.
Rollback (if needed): If any issues arise post-deployment, the IT team uses rollback features to revert the patch and troubleshoot.
This structured approach helps the organization stay secure, reduce downtime, and maintain compliance – all without overwhelming the IT team.
Hexnode’s patch management capabilities are designed to simplify, automate, and scale the update process across diverse device fleets. Whether you’re managing Windows, macOS, or third-party applications, Hexnode offers a unified, policy-driven approach that empowers IT teams with precision, visibility, and control.
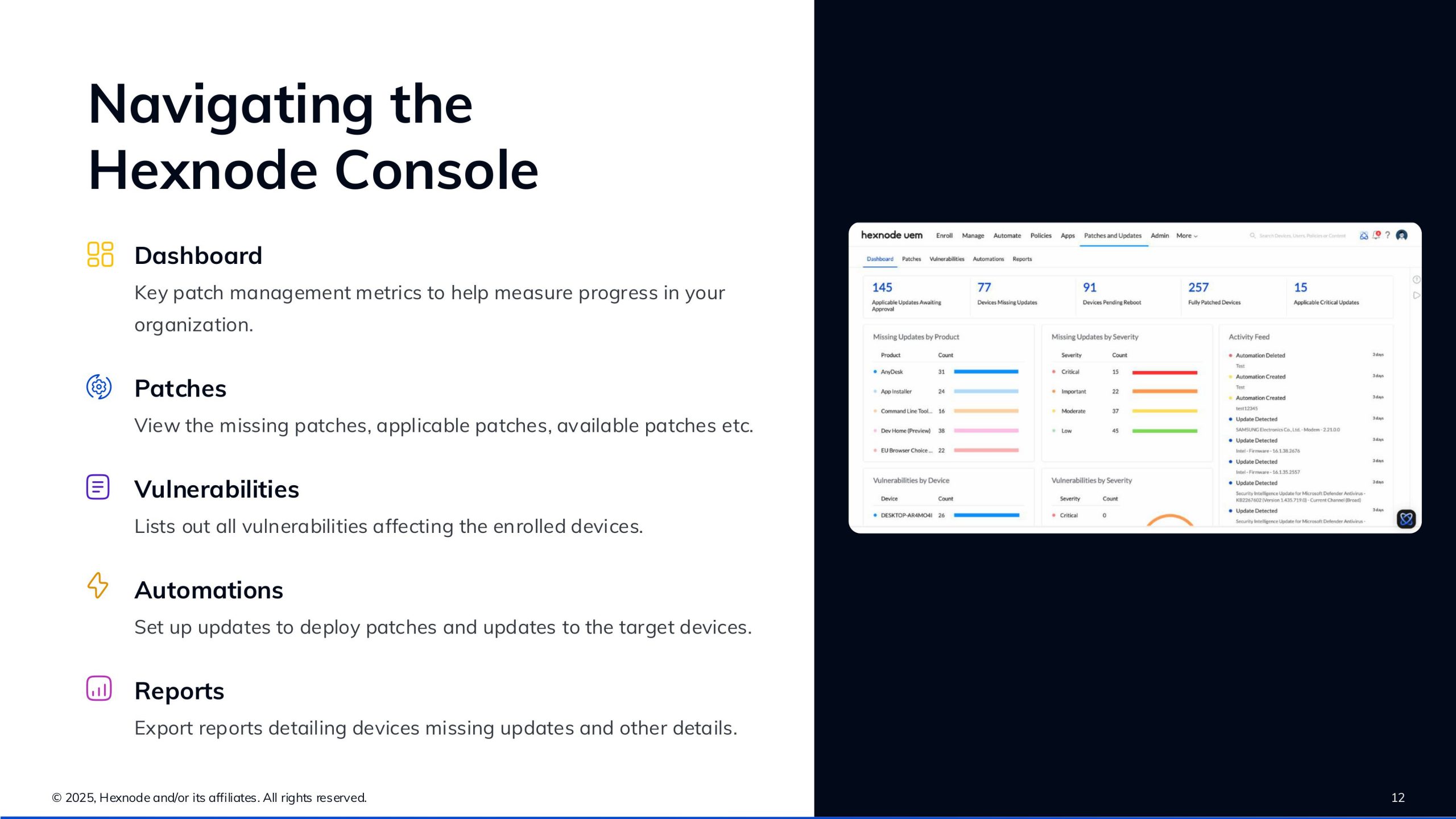
1. Unified Patch Management Console
Hexnode integrates patching into its Unified Endpoint Management (UEM) platform, allowing IT teams to manage OS and app updates from a single pane of glass. This eliminates the need for separate tools and streamlines workflows.
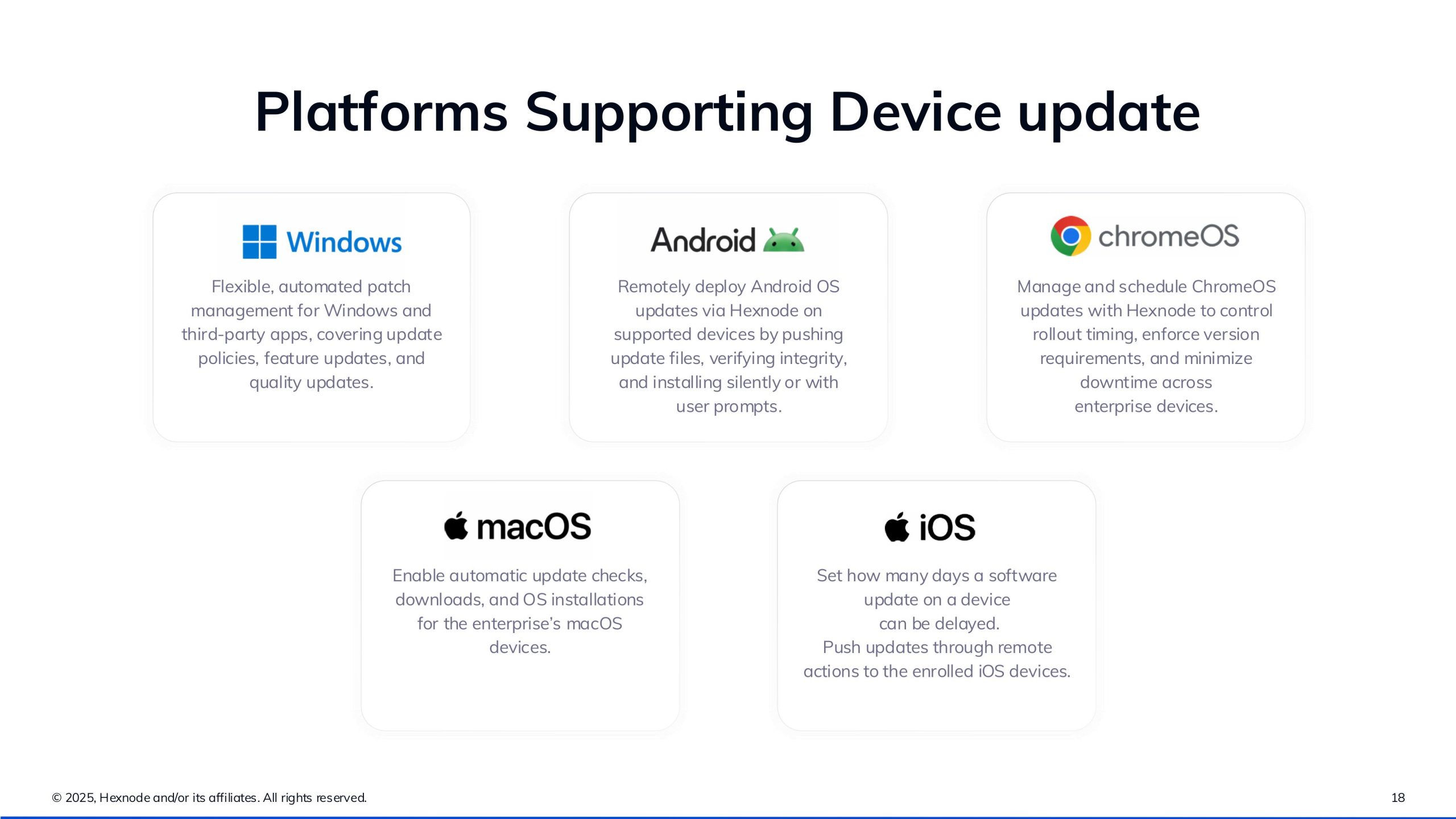
2. Support for Multiple Platforms
Patch management is available for Windows, macOS, and third-party applications. Hexnode also announced extended support for Linux devices, making it a cross-platform solution for modern enterprises.
3. Manual and Automated Deployment Options
Admins can choose between:

Deploy patches based on:
5. Maintenance Window Scheduling
Updates can be scheduled during off-peak hours or designated maintenance windows to avoid interrupting business operations.
6. Reboot and Rollback Controls
Admins can configure reboot behavior, allow user deferrals, and even roll back failed patches on Windows devices to maintain system integrity.
7. Real-Time Monitoring and Reporting
Hexnode provides:
Admins can:
9. WSUS Integration for Windows
Hexnode supports WSUS-specific configurations, enabling organizations to align patching with internal infrastructure and policies.
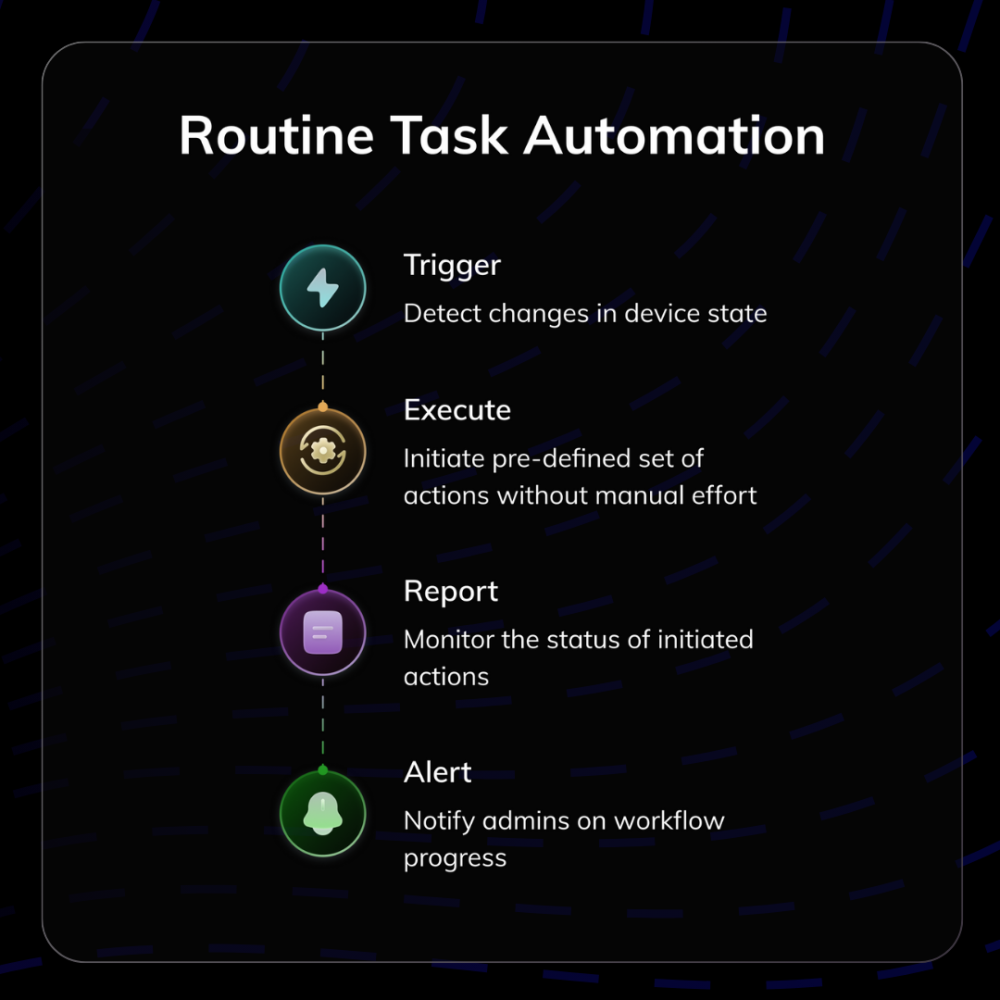
10. Automation via Hexnode Automate
With Hexnode Automate, IT teams can:
We’ve put together a short introductory video that gives you a glimpse into the features and its role within the Hexnode UEM platform.
Patch management can be handled through a variety of tools, each suited to different environments, device types, and administrative needs. From native OS utilities to full-scale enterprise platforms, organizations have a range of options to ensure systems remain secure and up to date.
Most operating systems come with built-in patching tools—like Windows Update or macOS Software Update. These are ideal for unmanaged or personal devices but lack the centralized control and visibility required in enterprise environments.
Windows Server Update Services (WSUS) and Microsoft System Center Configuration Manager (SCCM) are long-standing tools for managing Windows patches. WSUS allows IT admins to approve and deploy updates within a network, while SCCM offers broader configuration management and deeper integration with Microsoft ecosystems.

Simplify patching with Hexnode - automate updates, track compliance, and secure endpoints with zero manual effort.
Download the datasheetLinux environments typically rely on package managers like APT (for Debian-based systems) or YUM/DNF (for Red Hat-based systems). These tools retrieve patches from official repositories and can be scripted or automated for larger environments.
Mobile Device Management (MDM) and Enterprise Mobility Management (EMM) solutions extend patching capabilities across diverse endpoints. These platforms integrate update management into broader device policy frameworks, supporting mobile devices, desktops, and more.
In cloud and hybrid environments, tools like AWS Systems Manager Patch Manager automate patch deployment across virtual machines and cloud instances. These are useful for dynamic infrastructures requiring scalable and automated solutions. However, their scope is typically limited to assets hosted within that specific cloud environment, making them less suitable for organizations managing multi-cloud or hybrid setups that require centralized visibility and control.
Tools like Ansible, Puppet, and Chef are commonly used in DevOps to automate system configuration, including patch deployment. These solutions offer flexibility and scalability in complex IT ecosystems. However, for organizations with simpler infrastructure or smaller teams, these tools may be overkill, as they require significant setup and expertise, potentially adding unnecessary complexity.
Many organizations pair patching with vulnerability management tools like Qualys or Tenable. These tools identify security gaps and help prioritize patches based on risk severity. While highly effective in identifying and managing vulnerabilities, these tools may not be suitable for smaller businesses or those without dedicated security teams, as they can be costly and require significant resources to properly integrate and maintain.
To simplify patching across operating systems and application types, organizations often adopt unified solutions that combine visibility, automation, and cross-platform support—leading into modern tools like Hexnode. These enable centralized patch management across a wide range of endpoints—mobile devices, desktops, and laptops. These tools integrate update workflows into broader device policies, offering automation, policy-based control, and cross-platform support. Unified solutions help IT teams reduce operational overhead while maintaining security compliance. Platforms like Hexnode bring all these capabilities together under a single pane of glass, streamlining patching in diverse IT environments.
Navigating the complexities of patch management requires a strategic approach.
Regular audits:
Automated patching:
Rollback plans:
User education:
Patch testing:
Leverage expert tools:
What is third-party patch management?
Third-party patch management refers to the process of identifying, deploying, and managing updates for software applications that are not developed by the operating system vendor. These include widely used tools like Adobe Reader, Google Chrome, Zoom, and others. Since these apps often fall outside of native OS update mechanisms, they can become easy targets for attackers if left unpatched. A robust third-party patching strategy ensures these applications are regularly updated, reducing security risks, and maintaining compliance with industry standards.
What is the difference between patch management and vulnerability management?
While both aim to reduce security risks, patch management and vulnerability management serve different purposes. Patch management focuses on applying software updates to fix known issues – it’s a reactive process triggered by vendor-released patches. Vulnerability management, on the other hand, is a broader, proactive discipline that continuously scans for, assesses, and prioritizes all types of security weaknesses, whether or not a patch exists. In essence, patching is one of the many tools used within a vulnerability management strategy.
How often should patches be applied?
The frequency of patching depends on the severity of the vulnerability and the criticality of the system. Critical patches should be applied as soon as possible – often within 24 to 72 hours – while less urgent updates can be scheduled during regular maintenance windows. Many organizations follow a monthly patch cycle, supplemented by emergency patching when needed.
Can patching break applications or systems?
Yes, it’s possible. That’s why testing patches in a controlled environment before deployment is a best practice. Some patches may introduce compatibility issues or unintended side effects. A rollback plan and phased deployment strategy can help mitigate these risks.
Is automation necessary in patch management?
While not mandatory, automation significantly enhances the efficiency and reliability of patch management. Automated tools can scan for missing patches, schedule deployments, and generate compliance reports – reducing manual effort and minimizing human error. This is especially valuable in large or distributed environments.
Effective patch management is essential for maintaining security, stability, and compliance across any IT environment. From understanding the different types of patches to selecting the right tools and aligning them with broader IT operations like configuration or vulnerability management, every step plays a crucial role. While the process can be complex—especially in large or hybrid environments—the right strategy and tools can greatly simplify patch deployment and monitoring. Whether you’re relying on native OS tools, configuration managers, or unified solutions, a well-structured patch management plan ensures your systems remain resilient in the face of evolving threats and technology changes.
Give Hexnode UEM a go to effectively manage and deploy patches for your devices.
Start your free trial