Unattended access for Windows devices made easy with Hexnode
Need hands-off remote control? See how Hexnode simplifies Windows troubleshooting at scale.

Get fresh insights, pro tips, and thought starters–only the best of posts for you.
Oct 22, 2025
21 min read

Modern IT management starts with the assumption that devices will be everywhere. IT teams are now expected to jump in and fix problems, push updates, or lock down devices instantly, whether those devices are in the same building or on the other side of the world. That’s only possible if you’ve got the right way to reach them – securely, reliably, and without wasting time.
And that’s where remote access protocols come in. Think of them as the rulebooks that decide how two devices talk to each other over a network. Whether it’s opening a full desktop session on a remote Windows PC, sharing the screen of a macOS device, or running secure terminal commands on a Linux server, the protocol in use decides how smooth, secure, and compatible that experience will be.
Let’s break down the nuts and bolts of the most common remote access protocols—how they work, their strengths, and where they might fall short. From there, it’s easier to see how a platform like Hexnode doesn’t just support these protocols, but wraps them in enterprise-grade security, policy control, and unified device management.
Remote access is essential for any IT team managing distributed devices. From pushing patches and verifying compliance to restarting stuck apps or assisting users in real time, the ability to intervene remotely saves time, reduces costs, and keeps operations running smoothly, no matter where the devices are located.
It’s not just about convenience either. With more devices outside the office than inside, remote access has become critical infrastructure. If something breaks, there’s no walking over to fix it. And when you’re managing fleets of machines across different networks, remote access is the only way to maintain control.
But that control comes with a security trade-off. Exposing devices for remote access – even through common protocols like RDP or VNC—can be risky if you’re not careful. Weak encryption, poor authentication, or leaving services open to the internet can make things easier not just for admins, but for attackers too. There’s also the performance angle. Some protocols handle low bandwidth or high latency better than others. And depending on what you’re trying to do, run CLI commands, share a screen, control a full desktop – the protocol has to match the use case. And let’s be real, you’re managing Windows, macOS, Linux, Android, maybe more. So cross-platform support isn’t optional; it’s expected.
Remote access only works if it’s secure, responsive, and flexible.
Anything less becomes a liability.
Remote access isn’t a one-size-fits-all setup. Depending on the device type, the OS it’s running, the use case, and your organization’s security posture, the protocol you pick can make or break the experience—for both the admin and the end user. Some protocols are lightweight and command-line only; others offer full desktop control with encryption and graphical support built in.
At their core, remote access protocols define the rules and structure for how two devices connect and communicate over a network. They govern everything from how a session is initiated, how the connection is authenticated, how data is transmitted, and how that session is secured. Whether it’s a text-based shell or a full desktop interface, the protocol determines what kind of access is possible—and how smooth, secure, and responsive that access will be.
This section breaks down the most commonly used remote access protocols you’ll run into. We’ll cover what they’re built for, how they work, what kind of security they offer, and where they tend to hit limits. Think of it as a technical teardown, so you know exactly what you’re working with—and what to look out for.
Each protocol will be broken down across the same key criteria:
This technical overview sets the foundation for understanding how platforms like Hexnode implement and extend these protocols, and why that matters when you’re working across multiple device types at scale.
RDP is Microsoft’s go-to protocol for remote desktop access on Windows systems—and chances are, if you’ve ever remoted into a Windows machine, you’ve used it. Built deep into the OS, RDP allows full GUI access to another system over the network, making it a solid choice for remote troubleshooting, configuration, and administrative tasks.
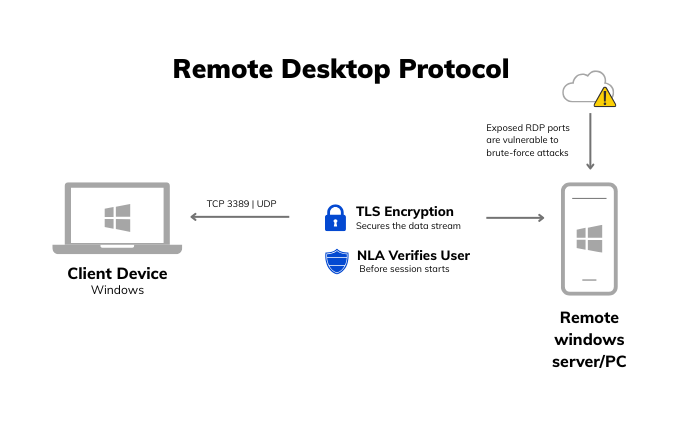
By default, RDP runs over TCP port 3389, with optional UDP support baked in to improve responsiveness over less stable connections. It supports TLS encryption and leverages Network Level Authentication (NLA) to verify users before a full connection is established – an important layer that helps block unauthenticated sessions early.
That said, RDP has its weak spots. When exposed directly to the internet without additional protections like VPN or a secure gateway, it becomes a magnet for brute-force attacks and credential spraying. There’s a long history of RDP-based exploits, many of which target misconfigurations or outdated Windows versions.
Full control over Windows systems, especially in environments already built around Microsoft infrastructure.
Public-facing scenarios or mixed-OS environments where security hardening and cross-platform support are non-negotiable.
VNC is one of the older, more flexible remote access protocols still in use today. It’s built around the Remote Frame Buffer (RFB) protocol, which transmits screen data from the host device to the client and relays keyboard and mouse input back. It’s a simple mechanism that works across platforms, making VNC a go-to for basic GUI-based access, especially in mixed-OS environments.
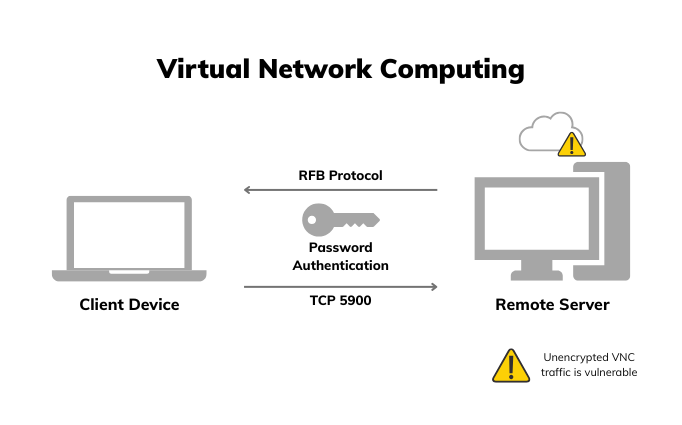
By default, VNC uses TCP port 5900, and while it supports password-based authentication, encryption isn’t always enabled by default—it depends on the VNC variant or implementation in use. Some modern versions (like TigerVNC or RealVNC) layer in encryption, but legacy or stripped-down versions may still send data unencrypted unless configured otherwise.
What makes VNC useful is its platform agnosticism and relatively lightweight setup—you can use it to view and interact with almost any graphical desktop without much overhead. But that simplicity comes with trade-offs. Performance tends to degrade over low-bandwidth connections, and without native encryption, it needs extra hardening (like tunneling through SSH or VPN) before it’s safe for production use over untrusted networks.
Cross-platform environments, quick graphical access to remote desktops, and simple use cases with low security requirements.
Environments needing strong out-of-the-box encryption, high performance over poor networks, or enterprise-level control.
SSH is the gold standard when it comes to secure, remote command-line access—especially in Linux and Unix-based environments. It’s built for remote administration, configuration, and scripting, and it’s what most sysadmins reach for when they need lightweight, encrypted access to servers without any GUI* overhead.
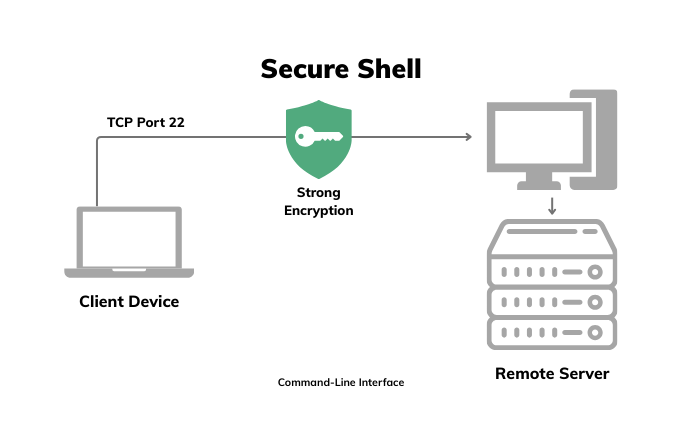
Operating over TCP port 22, SSH establishes an encrypted tunnel between the client and server, using strong cryptographic algorithms to secure both authentication and data transmission. Most setups rely on key-based authentication (public/private key pairs), which is far more secure than passwords alone—especially when paired with passphrases and access control lists.
SSH is fast, reliable, and hardened by decades of use. Its CLI* focus makes it ideal for scripting, automation, and low-bandwidth environments. But it’s not built for GUI interactions. If you need to remotely control a graphical interface, you’ll need to tunnel VNC, RDP, or another protocol through SSH—which adds complexity and isn’t ideal for day-to-day helpdesk scenarios.
Secure server management, automation, headless device control, and remote shell access across Linux/macOS systems.
GUI-based workflows, remote desktop support, or environments where non-technical users need access.
While traditional protocols like RDP, VNC, and SSH require some degree of setup or system-level integration, tools like TeamViewer, AnyDesk, and LogMeIn come packaged with their own proprietary protocols—offering an all-in-one solution that “just works,” especially for users who don’t want to mess with port forwarding or firewall tweaks.
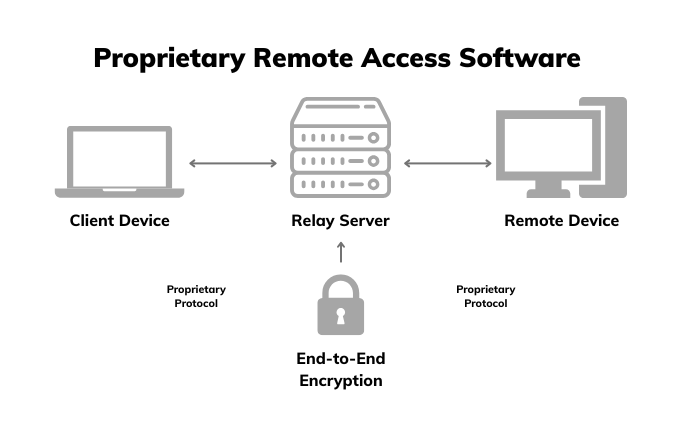
These tools typically operate through relay servers* that handle NAT traversal*—allowing remote sessions even if the client and host are both behind routers or firewalls. That’s one of the key selling points: you can initiate a session quickly without needing to reconfigure the network.
Security-wise, most of these tools offer their own end-to-end encryption and authentication layers, though the details vary between vendors and aren’t always open for scrutiny. Since they’re proprietary, you’re relying on the vegndor to maintain both security and uptime.
The convenience is hard to ignore—cross-platform support, minimal setup, and solid performance in most environments. But that comes at a cost. You’re dependent on third-party servers, which introduces external risk and potential points of failure. And while some versions are free for personal use, licensing for business environments often adds up fast.
Quick remote support, mixed OS environments, and scenarios where ease-of-use outweighs deep control.
High-security environments, offline scenarios, or enterprises that need auditability, self-hosted control, or tight compliance.
If Telnet shows us where remote access started, WebRTC shows us how far it’s come. While older protocols were built for basic connectivity, WebRTC is designed for secure, real-time communication—and it’s become the backbone for many of today’s modern remote access platforms.
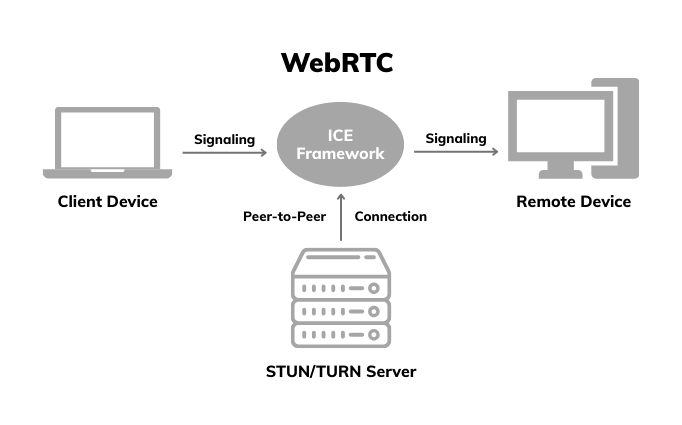
Originally developed for video and voice in browsers, WebRTC has evolved into a go-to solution for low-latency, peer-to-peer connections that work across networks without requiring heavy configuration. That makes it ideal for modern IT environments where speed, security, and cross-platform support are non-negotiable.
Here’s what sets WebRTC apart:
WebRTC delivers the kind of performance and flexibility that legacy protocols weren’t designed for – real-time communication, encrypted by default, and accessible straight from a browser. It’s why more modern remote access tools are shifting toward it: less setup, tighter security, and smoother control across platforms, all without sacrificing usability
Outside the mainstream protocols like RDP, VNC, and SSH, there are a few others you might encounter—either in legacy systems or as part of specific remote access setups.
Since VNC is based on the Remote Frame Buffer (RFB) protocol, there are multiple forks and implementations floating around – some optimized for speed, others for encryption or platform-specific use. Tools like TigerVNC or UltraVNC extend RFB with added capabilities, but the underlying communication model stays the same: streaming screen data and input events over the network.
Once a common remote access protocol, Telnet has mostly been retired for one big reason – it transmits data, including passwords, in plain text. It’s still found in some embedded systems and networking hardware, but should be avoided entirely in favor of SSH wherever possible.
Some modern devices (especially routers, NAS systems, and embedded IoT gear) expose web-based dashboards over HTTPS for remote access. While they’re easy to use, their security is only as good as the device’s implementation – firmware vulnerabilities, default credentials, and poor certificate management are common attack vectors here.
These protocols are either too limited, outdated, or context-specific to serve as general-purpose remote access solutions, but they’re worth being aware of, especially if you’re working with older infrastructure or specialized hardware.
While not remote access protocols themselves, VPN tunneling protocols like PPTP, L2TP/IPSec, OpenVPN, and WireGuard play a critical role in enabling secure remote access across untrusted networks. Instead of exposing protocols like RDP or VNC directly to the internet, which is notoriously risky -many organizations route them through a VPN connection first.
This adds a security layer by:
VPNs can be used in combination with traditional remote access protocols, especially when additional layers of network-level segmentation or compliance are required.
Remote access in Hexnode isn’t an add-on, it’s tightly integrated, designed for secure, real-time control across platforms and backed by enterprise-grade protections.
Instead of relying on external agents or standalone tools, Hexnode delivers remote access that works out of the box -encrypted by default, resilient across networks, and frictionless for IT teams.
Remote access is tailored per platform without added complexity:
Security is built into every session:
And because remote access is built directly into the Hexnode UEM console, there’s no need for external tools, third-party agents, or manual setup. If a device is enrolled, it’s accessible—securely and instantly—whether you’re troubleshooting, applying policies, assisting a user live, or checking in for compliance.
MDM remote access: The essential tool for real-time troubleshooting
Most remote access tools stop at control—Hexnode goes further by building it into the entire device management workflow. It’s not just about reaching a device; it’s about doing it securely, in real-time, and with full context—all from the same console used to manage policies, apps, and compliance.

Get access to a datasheet, policy template, white paper, infographic, guides, and success stories to support your remote work strategy.
Download the kitRemote access opens up powerful possibilities—but it also expands your attack surface. Without the right safeguards in place, even the most useful protocol can become a liability. These best practices aren’t just recommendations—they’re baseline requirements if you want to keep your environment both accessible and secure.
?Can I still use RDP or VNC safely?
Yes—but only if properly secured. RDP and VNC should never be exposed directly to the internet. Always use them behind a VPN or through a secure gateway, enforce strong authentication, and ensure they’re up to date with the latest patches.
? What’s the difference between remote desktop and screen sharing?
Remote desktop (like RDP) gives you full control of a device’s desktop environment. Screen sharing (like VNC) mirrors the screen and may allow interaction, but it’s often less tightly integrated with the OS and can be slower or less secure depending on the implementation.
? Why is WebRTC better for modern remote access?
WebRTC enables real-time, encrypted, peer-to-peer connections without requiring open ports or complex setup. It’s ideal for browser-based tools and offers better performance and security out of the box—especially for cross-platform environments.
? What are the disadvantages of WebRTC?
While WebRTC is fast and secure, it depends on STUN/TURN servers for NAT traversal, which can introduce latency if peer-to-peer isn’t possible. It also requires modern browsers or compatible environments, and managing large-scale deployments may need additional infrastructure like TURN relay servers for fallback scenarios.
? Can I access devices without installing a separate remote tool?
Yes. With Hexnode, if the device is enrolled, it’s accessible. Remote access is built into the Hexnode console—no extra tools, plugins, or port configurations required.
? How do I ensure my remote access setup is secure?
Follow key best practices:
Choosing the right remote access protocol isn’t just a technical decision—it’s a strategic one. The tools and standards you rely on shape how quickly your team can respond, how securely they can operate, and how seamlessly your workflows scale across devices, platforms, and users.
Legacy protocols like RDP, VNC, and SSH still serve their purpose—but modern IT environments demand more than just access. They require visibility, control, auditability, and zero-friction integration.
That’s where Hexnode fits in. By embedding secure, WebRTC-powered remote access into a unified device management platform, Hexnode gives you the best of both worlds—real-time control, wrapped in enterprise-grade security, with none of the setup or overhead of standalone tools.