macOS Active Directory binding explained
Learn how to enforce macOS Active Directory binding and see how IT can use a UEM to remotely bind Macs to the AD domain.

Get fresh insights, pro tips, and thought starters–only the best of posts for you.
Aiden Ramirez
Nov 17, 2022
10 min read

We at Hexnode very often dive deep into technical topics that can help make your life easier if you are an IT administrator, an entrepreneur or just someone trying to make the most out of your personal devices. In today’s episode of one of those ‘deep dives’, we will understand what Windows Active Directory asset binding is. Not to brag, but Hexnode makes this task effortless. We’ll get to that part a bit later.
The throne, for the most widely used operating system, is still occupied by Windows and will probably stay the same for a while. One of the reasons for this is the ease of managing user accounts, which becomes especially relevant in a corporate environment. Speaking of user management, there is also the need to keep the corporate network secure. IT admins use Microsoft’s Active Directory (AD) services to make this happen for Windows devices. In fact, the use of AD for this purpose is so common that over 46,000 companies worldwide use it currently.
AD asset binding is the term associated with binding a device with the Active Directory domain. That is, joining an Active Directory domain with your Windows devices allows you to bind user accounts with each device. This will enable users to seamlessly log in to their devices using their Active Directory credentials without creating separate user accounts for each device.
If you are already familiar with Active Directory and its services, save yourself some time and jump into the next section. Else, please stick around😄.
First things first- what is Active Directory? Active Directory is a directory service developed by Microsoft for Windows domain networks. Initially introduced in Windows 2000, it is included with most Windows server operating systems as Directory and identity management service.
Active Directory contains a variety of directory services. Let’s take a quick look at them.
ADDS is the main service in Active Directory as it stores all directory information and handles user interaction with the domain. Active Directory checks the username and password entered by the user when they log into a Windows domain computer member to determine whether they are a system administrator or regular user. Then, it controls access to each resource and group policies for each user.
Lightweight Directory Services is a subset of AD DS, providing almost the same functionalities. However, it doesn’t require the creation of new domains or domain controllers. Also, it allows running multiple AD LDS instances on the same server.
It is used to generate, manage and share certificates. A personal key will be used to encrypt these certificates, to enable the secure exchange of information through the internet.
This solution is used for sharing identity and access management information across the organization using Single Sign-On (SSO).
AD RMS is a set of tools that controls and manages information rights. It provides users access permission to corporate resources based on a minimum access policy.
Active Directory stores information about users in a hierarchical manner consisting of domains, trees, and forests.
A domain represents a group of objects which share the same AD database. These objects can be users, groups, or devices. Domains are organized by Domain Name System (DNS) and will have a DNS name such as yourcompany.com.
A tree is formed by one or more domains grouped together. A contiguous namespace is used in a tree structure to gather the domains in a logical hierarchy (for instance, marketing.yourcompany.com, accounting.yourcompany.com, etc.). The domains thus gathered can be considered to have a trusted relationship in which the involved domains share a secure connection.
A forest is a collection of multiple trees. It consists of a common schema, global catalog, and domain configurations shared between trees as a trusted relationship. The schema defines an object’s class and attributes, while global catalog servers keep track of all the objects in a forest. In simpler terms, forests are like the security fence of Active Directory.
OUs are objects grouped into separate units to simplify their management. These organizational units can be created to match the functional or business structure of the organization. However, each user or object in a domain must be unique, so OUs cannot have separate namespaces.
These are similar to OUs, but Group Policy Objects (GPOs) can’t be linked to an Active Directory container.
So now you have a pretty good understanding of Active Directory and its features. However, if you are still somewhat confused, head to Eugene’s blog, where he has gone the extra mile to elucidate this topic.
We have already established that Active Directory is a powerful tool for storing information in a logical hierarchy. Now let’s look at how these AD capabilities can benefit your business.
You can add your Windows device to an Active Directory domain in multiple ways. It can be done through the Settings app, from System properties or using PowerShell. We’ll look at the more straightforward method among the three, that is, through the Settings app.
1. Open the Settings app either from the Start menu or by pressing Windows key + I.
2. Navigate to Accounts -> Access work or school. Click on the Connect button.
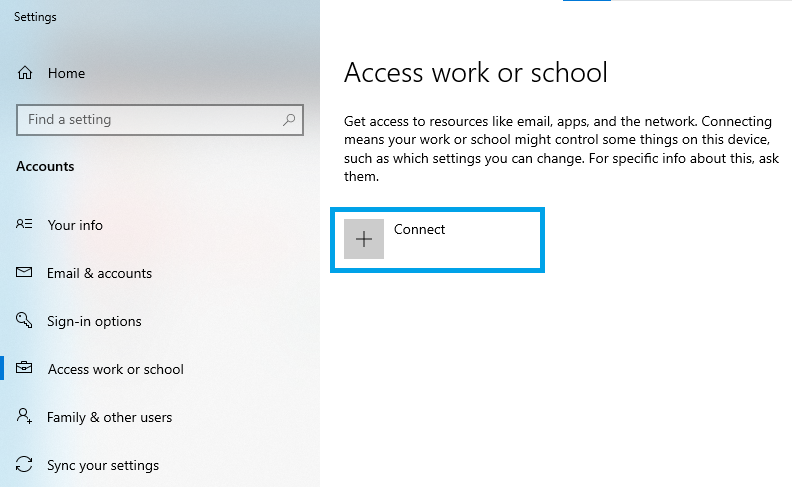
3. In the pop-up window that appears, click on the “Join this device to a local Active Directory domain” option.
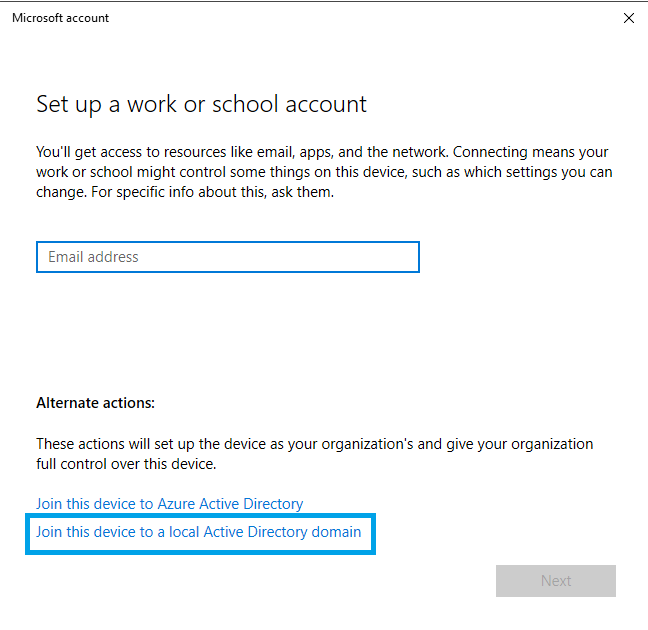
4. Enter your Active Directory domain name and click Next.

5. Type in the username and password for your domain account and click Ok.
6. Finally, restart your computer, and you can sign in to the Windows device with your domain account.
Your device is now linked with your Active Directory domain. That wasn’t so hard. This process was easy since we just had one device to bind to the AD domain. What if you had 10 or 100 such devices? Or what if you had to do it remotely? Not so easy now, is it?
Binding your assets to Active Directory can be time-consuming if you do it manually. Not to mention the effort of IT admins required to physically get to each device to do so. This is what I was talking about in the beginning- Hexnode makes this task painless. Let’s see how to do this.
Hexnode eliminates the trouble of having to bind each of your enterprise devices one by one. You can simply link your devices to the Active Directory domain from the Hexnode portal. Hence, you don’t have to create separate user accounts for each device, and users can seamlessly log in to their devices using their Active Directory credentials.
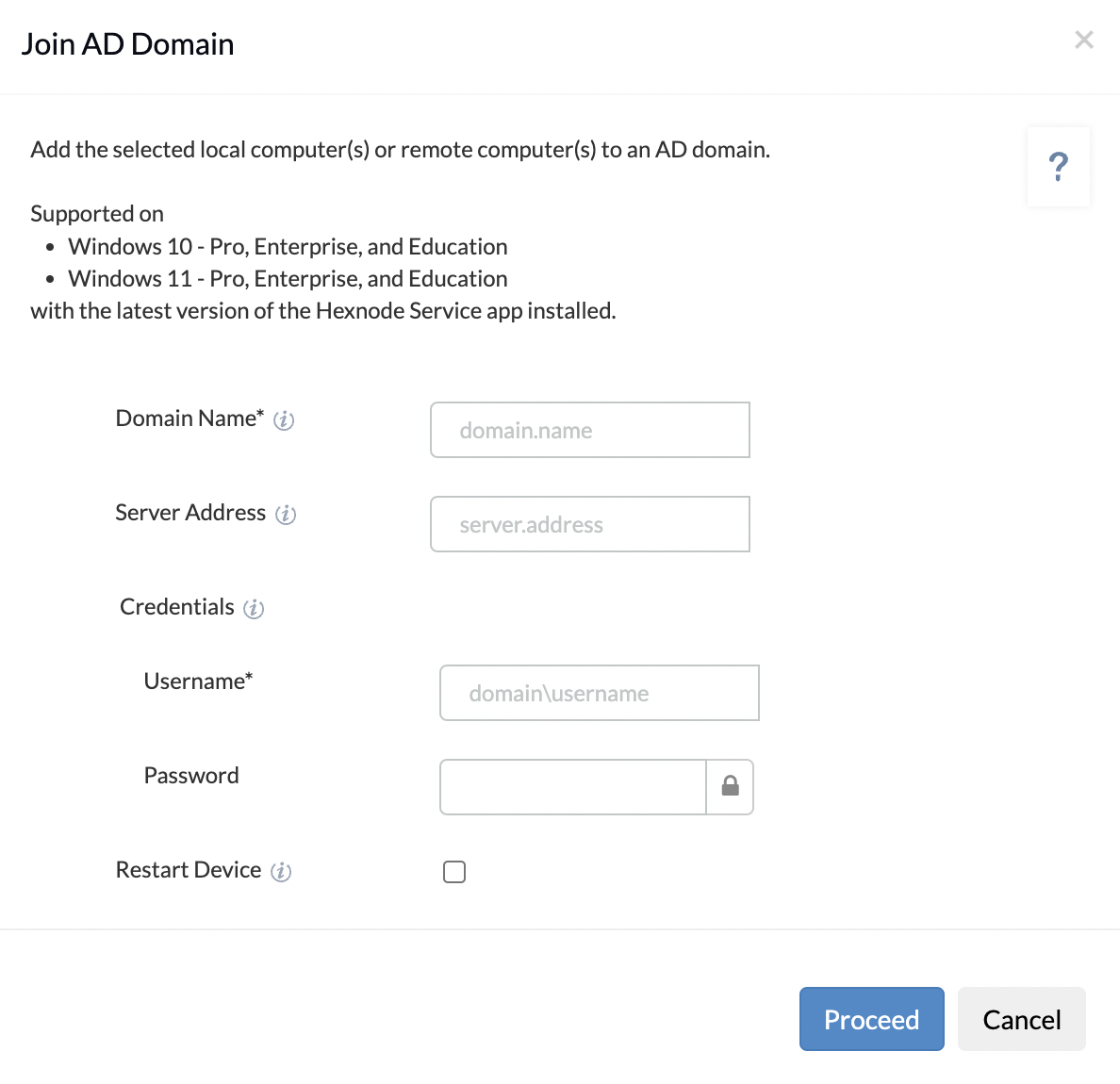
Your devices are linked to the AD domain, just like that. If you want to check the domain join status, select the required device from the Manage tab and go to Device Summary. You can see the AD join status in the domain joined field. You can also see the domain or workgroup to which the device has been added just below.
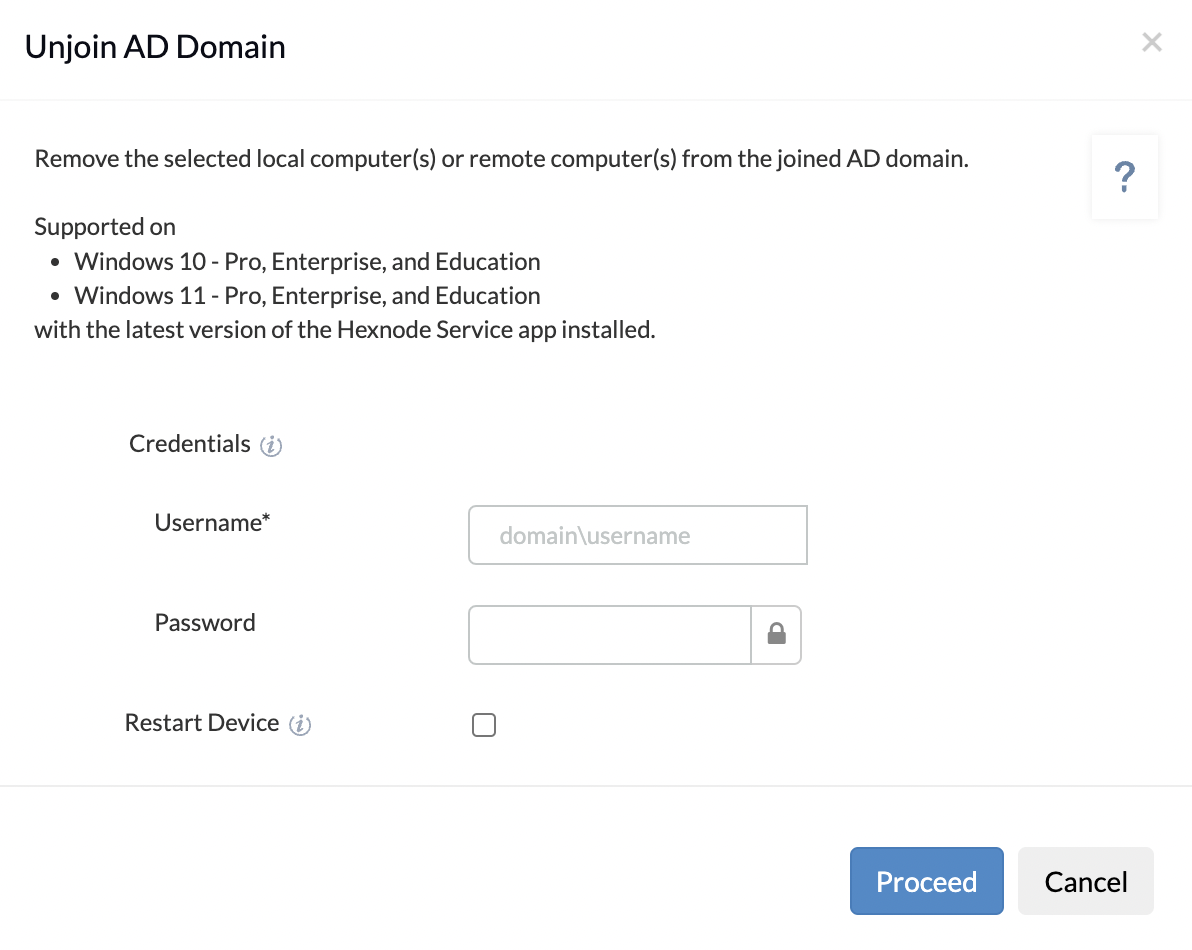
You can also remotely unjoin from the AD domain from the Hexnode portal.
Active Directory is a beneficial tool for controlling user access and privileges without hassle. It holds the keys to authentication (making sure the users are who they claim they are) and authorization (allowing access to only the data they are allowed to use) within the organizational network.
Get started with Hexnode’s Windows Management solution to improve efficiency, increase productivity, save time and overhead costs of managing your corporate devices.
AD can organize your organization’s entire hierarchy, meaning it can control which network your PC is connected to and even change your login credentials. In addition, it provides an easy way to ensure files can be accessed by only those who need them. These are a few reasons why AD is widely used on an enterprise level and why you should use it if you are not doing it already, no matter the organization’s size. The final piece of the puzzle is connecting the required devices to Active Directory, which takes a bit more time and effort. However, having a tool such as Hexnode, which can significantly help reduce the burden of manually binding your assets, might just be what you need to ensure maximum productivity.
Featured resource
Hexnode Windows Management Solution
Hexnode offers you much more management capabilities than just being able to bind your assets to AD remotely. Hexnode contains comprehensive app management, security management, and device restriction capabilities for Windows devices, as well as having functionalities in other platforms such as iOS, macOS, tvOS, and Android.
Start your 14-day free trial to get started with AD asset binding and a whole lot of other features.
SIGN UP NOW