Zero Trust and Cybersecurity with Hexnode MDM
Learn how to enforce and maintain zero-trust network access in your enterprise with Hexnode UEM

Get fresh insights, pro tips, and thought starters–only the best of posts for you.
Eugene Raynor
Jun 21, 2021
8 min read
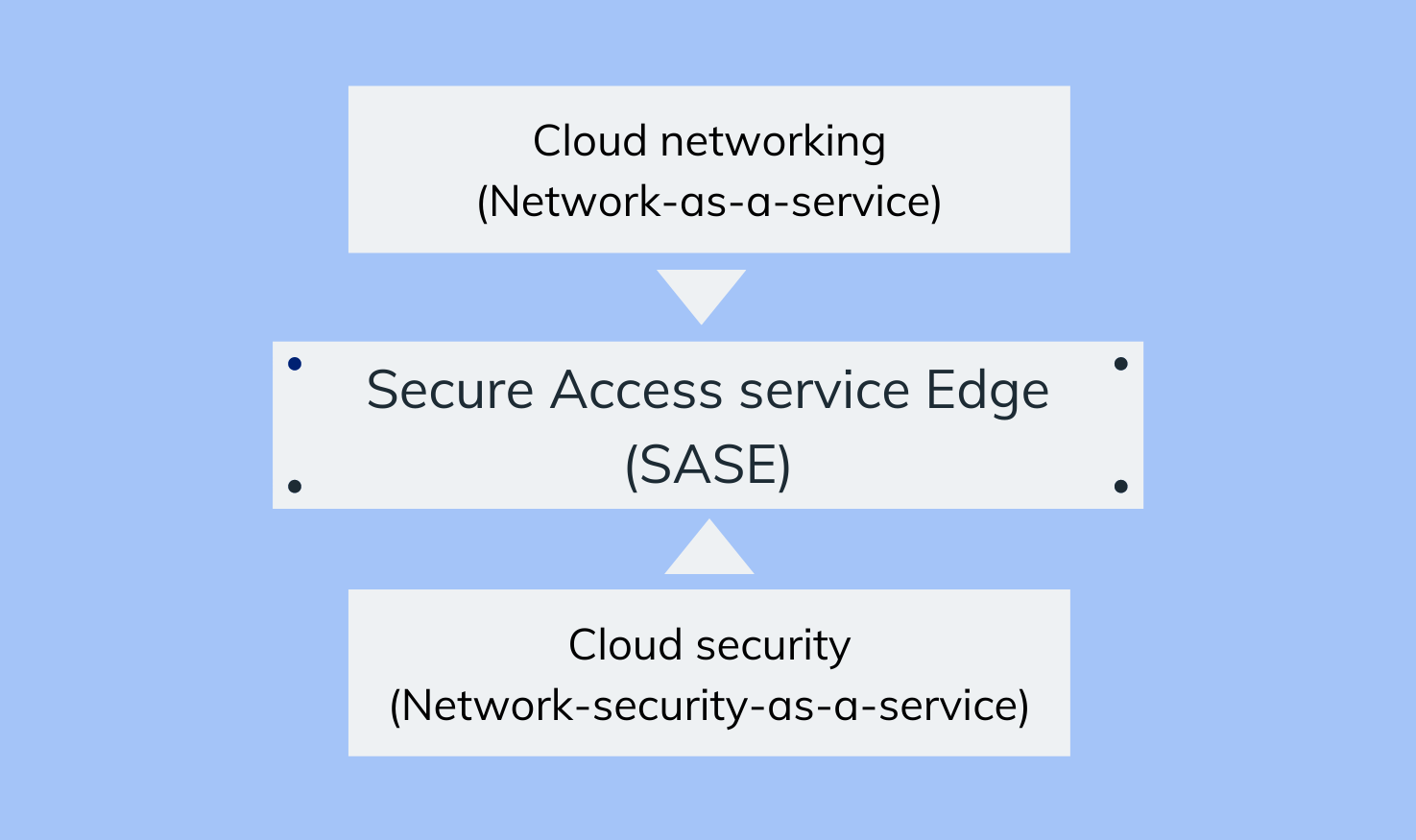
Secure Access Service Edge (SASE) is a network model that integrates both cloud networking (Network-as-a-service) and cloud network security (Network-security-as-a-service) technologies into a single framework, to ensure a simplified cloud structure for your enterprise. In simple terms, SASE combines the edge capabilities of the cloud along with its security offerings and delivers them together as a single service.
Back in the early days, the vast majority of enterprise infrastructure (including software, apps and services) were housed entirely inside corporate data centers located on-premise (usually at the organization headquarters). In this kind of corporate environment, the company’s security services would also be located at the data center itself.
Hence, employees could securely access enterprise infrastructure by connecting to the corporate VPN and crossing the company firewall. And although there was some form of traffic online, it wasn’t significant enough to cause latency issues or reduce the productivity of the employees.
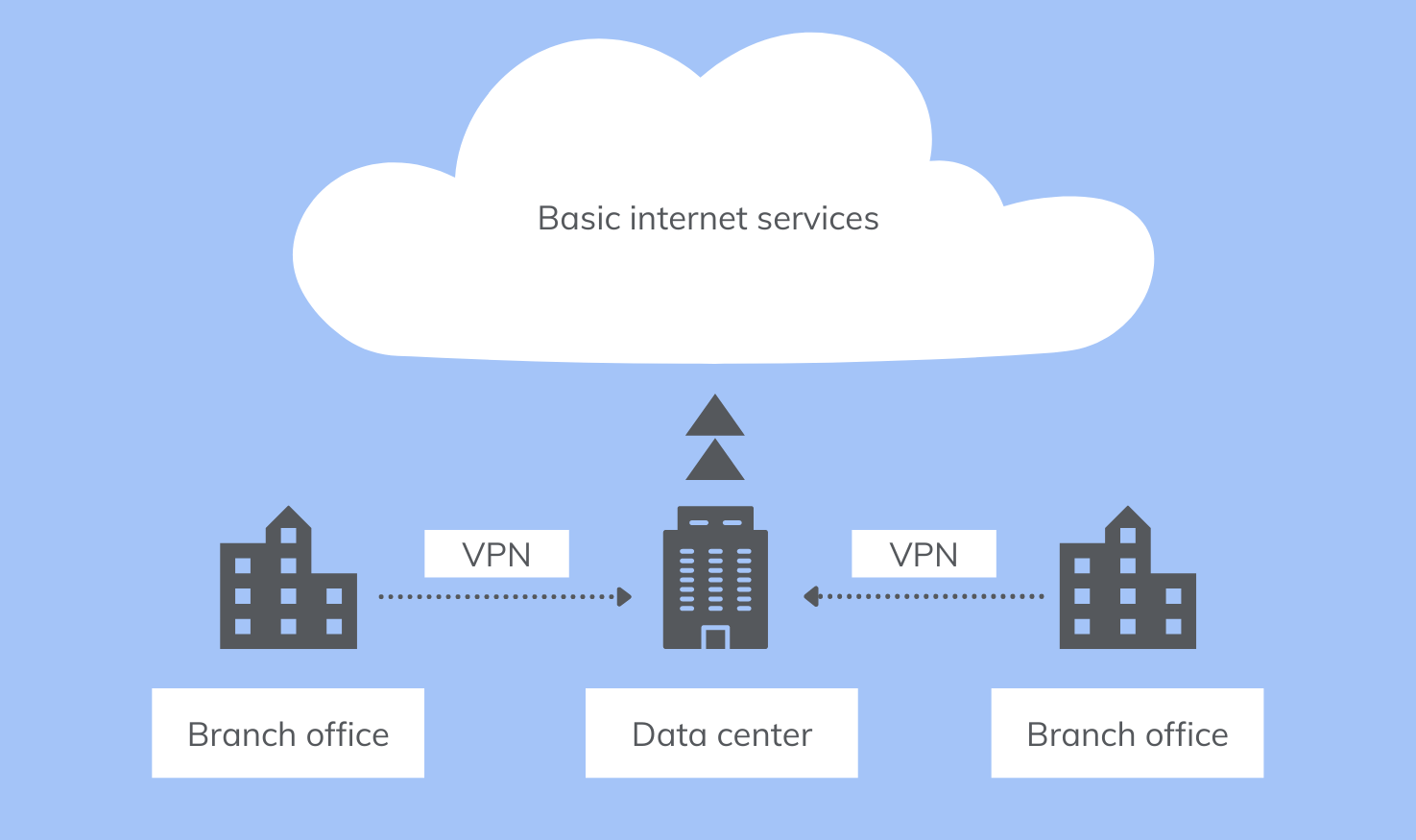
In short, there was a well-defined perimeter that you could easily secure, by utilizing the services hosted at the on-prem data center.
But today, things are different. Today, the increased reliability towards cloud services has led to a need for a transformation in the methods of securing employee traffic.
With the changing business landscape, the traditional methods of securing enterprises must change too. With so much infrastructure in the cloud, and users working from a diverse set of locations, it is inefficient to secure employee traffic by routing it to the data center and then to the web. Especially traffic that’s meant to reach the web anyways. Doing so would reduce the performance of the network while increasing the costs and maintenance involved. So instead, businesses needed to find a more efficient way to secure their online traffic. They accomplished this by decentralizing the enterprise network, and shifting security and verification to the edge of the cloud.
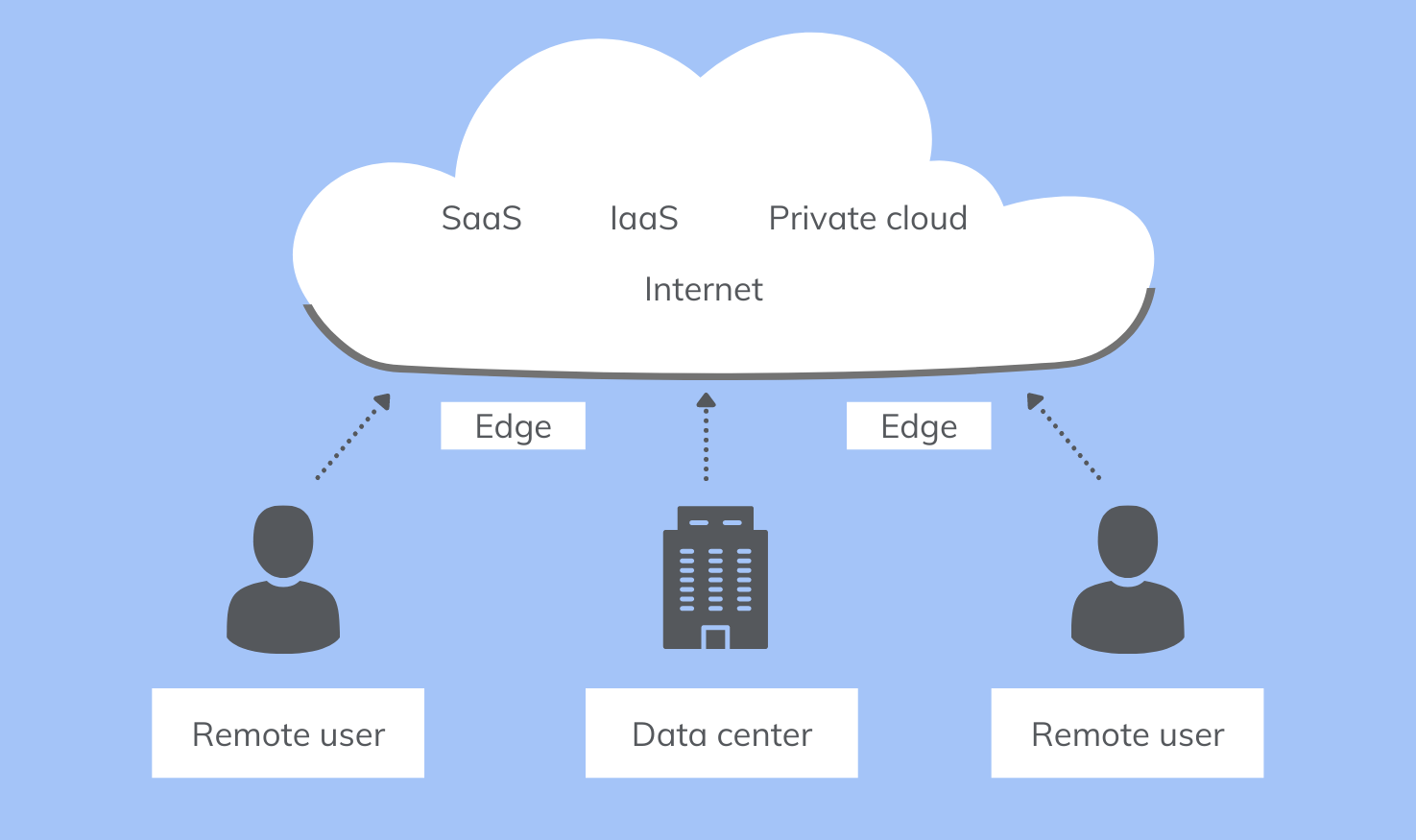
This modern approach of ‘direct internet access’, ensures that traffic is routed directly to the internet, and then secured at the edge.
Now, when shifting your infrastructure to the cloud, users may not go through the usual verification processes involved (including VPN and firewall) for connecting to the corporate network. Instead, they go through the security processes that are offered by cloud services.
However, employing separate tools for maintaining the cloud network and enforcing security near the edge (while also regularly updating these tools as new threats come out), can be a bothersome process, as organizations may have to resort to different cloud vendors to achieve their results. Instead, it is more efficient to subscribe to a multi-functional cloud-delivered method that provides both these offerings together as a single service, from a single vendor. This is the idea that SASE intends to fulfill.
Rather than layering cloud services that require separate configurations and management strategies, a SASE framework combines the services needed at the edge, and provides users with fast and secure access to your company’s cloud infrastructure.
SASE unifies networking capabilities, along with security elements and identity and access solutions, to ensure that users go through a speedy verification process on the edge.
Enterprises use NaaS models to host networking functionalities in the edge – by leasing SD-WANs from cloud service providers – to connect their users housed in different locations, to the corporate network.
A secure web gateway (SWG) is a software/hardware-based gateway that can either run on-prem or as a SaaS application. It enforces company security policies, block or filter out harmful content on the web, and restrict users from performing unauthorized actions on the network. SWGs usually consists of the following technologies
A CASB is a company or a security vendor that offers a vast suite of services to help secure cloud infrastructure from cyber-attacks and data breaches. They offer services including exposing shadow IT, access control, and data loss prevention. According to Garter, the four pillars of a CASB are visibility, data security, threat protection and compliance.
Firewall-as-a-service refers to a cloud-based firewall model. Unlike on-prem firewalls, FWaaS is hosted in the cloud and provides security capabilities similar to traditional firewalls. The only difference being; they protect your cloud infrastructure, rather than how traditional firewalls protect your local internal network.
Zero trust network access is an IT security model that is based on the phrase ‘trust nobody’. It means that no device, user or application attempting access to your infrastructure – inside or outside your network – can be considered secure, until they are verified and granted access. The zero-trust architecture operates on five pillars.
By minimizing the number of cloud service providers that IT has to depend on, it becomes easy for you to maintain and manage your cloud configurations and strategies and helps you set up simplified network controls at the edge.
In addition to reducing complexity, sticking to a single cloud service provider for all your cloud management needs can also reduce the setup costs and expenses by a significant amount.
The ability to scale enterprise infrastructure according to the company requirements is a huge advantage the cloud service providers can deliver over their on-prem counterparts. Along with its flexibility of providing a vast suite of security services ranging from URL filtering, malware detection and blocking, data loss prevention, firewall policies, and more, a SASE strategy acts as a comprehensive solution to secure and manage your enterprise infrastructure.
Any significant increase in latency can be an issue for enterprises that require high-speed services, including video streaming, conferencing, and customer support operations. Adopting a SASE strategy for your enterprise ensures that user traffic is optimized and transferred via the fastest network path possible.
With SASE’s zero-trust approach to managing identity access, along with SWG, CASB and FWaaS services, users are provided with secure access, even outside the corporate network. At the same time, enterprises are protected against any kind of potential attacks that may occur on their network – be it from inside or outside.

SASE is still a relatively new concept that is slowly gaining traction around business circles. Although it will still take time for this model to be implemented in large numbers, Gartner predicts that,
By 2024, 40% of enterprises will have adopted the SASE model of cloud networking.
Share your thoughts