Hexnode UEM + Quokka: Closing the Mobile App Security Gap
Hexnode’s integration with Quokka delivers real-time mobile app risk insights - detecting threats without disrupting users.

Get fresh insights, pro tips, and thought starters–only the best of posts for you.

In today’s hyper-connected digital landscape, an endpoint is no longer just a desktop computer in an office cubicle. It encompasses laptops, mobile phones, servers, cloud workloads, and even IoT devices – any device that connects to a network and can exchange data.
With the rise of remote work, BYOD (Bring Your Own Device) policies, and distributed teams, the number of endpoints in an organization has exploded, dramatically expanding the attack surface.
In Q3 2024 alone, organizations faced an average of 1,876 cyberattacks per week, marking a 75% increase compared to the same period in 2023. This surge reflects the growing sophistication of threats targeting endpoints, from ransomware and phishing to fileless malware and credential theft.
Legacy antivirus solutions, once the cornerstone of endpoint protection, are now struggling to keep up. These tools rely heavily on signature-based detection, which is ineffective against zero-day threats and fileless attacks that don’t leave behind traditional malware footprints. As attackers evolve, so must our defenses.
This shift underscores the urgent need for a proactive, intelligent, and adaptive security solution – one that doesn’t just detect threats but responds to them in real time. Enter Endpoint Detection and Response (EDR), a modern approach designed to meet the challenges of today’s threat landscape head-on.
Imagine securing your home with a basic burglar alarm – it might beep when someone opens a door, but it won’t tell you who entered, what they did, or how they got in. Now compare that to a modern security system with motion sensors, surveillance cameras, and a rapid response team. That’s the difference between traditional antivirus and Endpoint Detection and Response (EDR).
EDR is a cybersecurity solution designed to monitor, detect, investigate, and respond to suspicious activities on endpoints – the devices that connect to your network. Unlike legacy antivirus tools that rely on known malware signatures, EDR takes a proactive approach, using behavioral analysis, threat intelligence, and automation to identify and contain threats in real time.
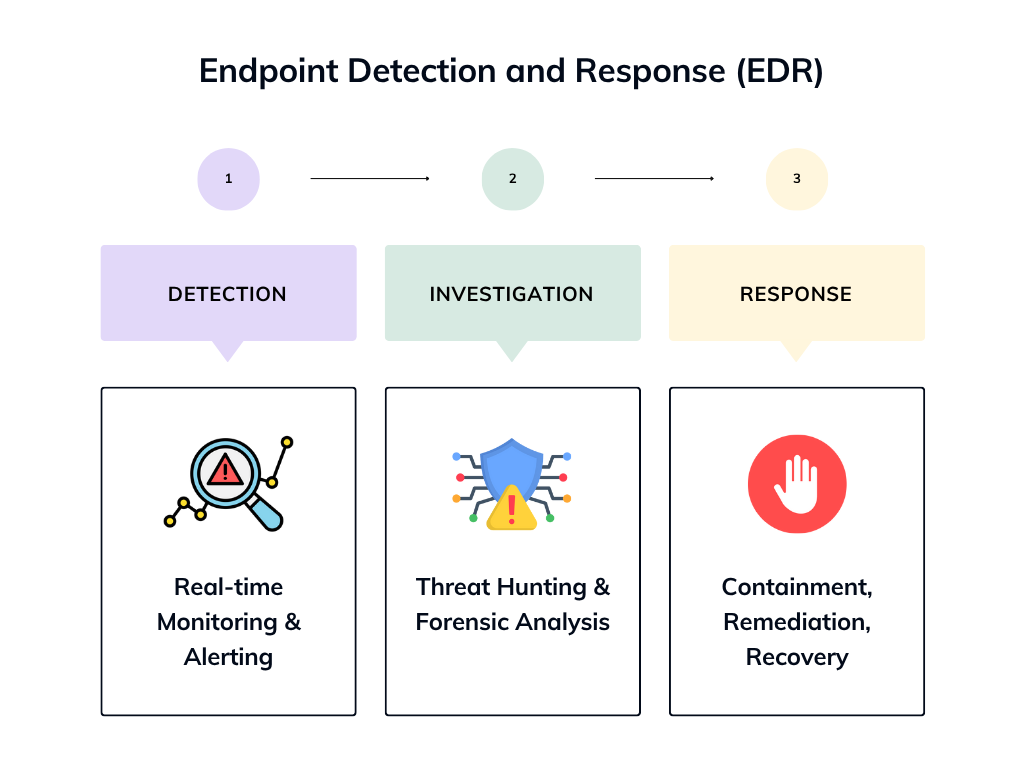
At its core, EDR is built on three foundational pillars:
1. Detection
EDR continuously monitors endpoint activity to identify anomalies, suspicious behaviors, and indicators of compromise (IOCs). It uses advanced analytics and machine learning to spot threats that traditional tools might miss – such as fileless malware, lateral movement, or privilege escalation.
2. Investigation
Once a threat is detected, EDR provides deep visibility into the attack chain. Security teams can trace the origin, understand the scope, and analyze how the threat propagated across systems. This forensic capability is crucial for root cause analysis and incident response planning.
3. Response
EDR enables rapid containment and remediation. Whether it’s isolating an infected device, killing malicious processes, or rolling back changes, EDR empowers security teams to act swiftly – often before damage is done.
Cybersecurity has come a long way from the days of simple antivirus software. As threats have evolved, so too have the tools designed to combat them. Understanding this evolution helps clarify why Endpoint Detection and Response (EDR) is now a cornerstone of modern security strategies.
Antivirus (AV): Initially focused on detecting known malware using signature-based methods. Effective for its time but limited in scope.
Endpoint Protection Platforms (EPP): Introduced a suite of preventive tools – firewalls, device control, and anti-malware – to strengthen endpoint defenses.
Endpoint Detection and Response (EDR): Emerged to fill the gap left by AV and EPP, offering real-time detection, investigation, and response to advanced threats.
Legacy tools are reactive by nature. They rely on known threat signatures and predefined rules, which makes them ineffective against zero-day exploits, fileless malware, and living-off-the-land attacks. These threats are designed to bypass traditional defenses and operate stealthily within systems.
APTs represent a new breed of cyberattack – stealthy, targeted, and long-lasting. They often begin with a compromised endpoint and escalate through lateral movement and privilege escalation. Detecting and stopping APTs requires deep visibility, behavioral analytics, and rapid response capabilities – all of which are core strengths of EDR.
While Endpoint Detection and Response (EDR) may sound complex, its core functions are built around a simple goal: to detect threats early, understand them deeply, and respond swiftly. Let’s break down how EDR works under the hood, focusing on its key capabilities that make it indispensable in modern cybersecurity.
At the heart of every EDR solution is a lightweight agent installed on endpoints. This agent continuously collects telemetry data – a rich stream of information that includes:
This granular visibility allows EDR to build a behavioral baseline for each endpoint, making it easier to spot anomalies that could indicate malicious activity.
Once data is collected, EDR platforms use real-time analytics to detect threats. This involves:
This layered approach ensures that even fileless attacks, zero-day exploits, and living-off-the-land techniques don’t go unnoticed.
Speed is critical in cybersecurity. EDR solutions are designed to automatically respond to threats as soon as they’re detected. Common automated actions include:
This automation reduces dwell time and limits the impact of attacks, especially in large environments where manual response isn’t scalable.
Beyond automation, EDR empowers security analysts with tools for deep investigation and proactive threat hunting. Analysts can:
This capability transforms EDR from a reactive tool into a strategic asset, enabling organizations to stay ahead of adversaries.
The cybersecurity landscape is filled with acronyms, and it’s easy to get lost in the alphabet soup. Understanding how Endpoint Detection and Response (EDR) compares to other security technologies is essential for making informed decisions. Here’s a breakdown of how EDR stacks up against AV, EPP, XDR, and MDR – and how they complement each other.
Antivirus (AV) is the most basic form of endpoint protection. It relies on signature-based detection to identify known malware and prevent it from executing. While AV is effective against well-documented threats, it struggles with zero-day attacks, fileless malware, and advanced persistent threats (APTs).
EDR, on the other hand, uses behavioral analysis, machine learning, and real-time monitoring to detect suspicious activity – even if the threat is previously unknown. It doesn’t just block; it investigates and responds.
Endpoint Protection Platforms (EPP) are the evolution of AV. They typically include a suite of tools such as firewall, device control, anti-malware, and web filtering. EPP focuses on preventing threats from reaching the endpoint.
EDR complements EPP by adding detection and response capabilities. Many modern solutions combine EPP and EDR into a unified platform, offering both preventive and reactive security.
Extended Detection and Response (XDR) builds on EDR by expanding visibility beyond endpoints. It integrates data from network traffic, cloud workloads, email systems, and more to provide a holistic view of threats across the entire environment.
While EDR focuses on endpoint-level threats, XDR correlates signals across multiple domains, improving detection accuracy and reducing response time.
Managed Detection and Response (MDR) is a service, not a technology. MDR providers use tools like EDR to monitor, detect, and respond to threats on behalf of organizations. What sets MDR apart is the human expertise – security analysts who manage alerts, investigate incidents, and provide actionable guidance 24/7.
MDR is ideal for organizations that lack in-house security teams or want to augment their capabilities with external experts.
Understanding these distinctions helps organizations choose the right mix of tools and services based on their security maturity, resource availability, and risk profile. EDR is a foundational technology – but when paired with EPP, XDR, or MDR, it becomes part of a robust, layered defense strategy.
Deploying an Endpoint Detection and Response (EDR) solution is a strategic move – but its success depends on thoughtful planning and execution. Here are four best practices to ensure your implementation delivers maximum value:
Planning and Scoping
Start by clearly defining your goals. Are you focused on reducing dwell time, improving threat visibility, or meeting compliance requirements? Map out which endpoints will be covered, what data will be collected, and how alerts will be managed. A well-scoped deployment avoids unnecessary complexity and ensures alignment with business priorities.
Integration with Existing Security Stack
EDR works best when it’s part of a broader security ecosystem. Ensure your solution integrates smoothly with tools like SIEM, SOAR, UEM, and identity platforms. This enables centralized visibility, automated workflows, and faster incident resolution.
Training and Change Management
Even the most advanced EDR solution is only as effective as the team using it. Invest in training for your security analysts and IT staff. Provide clear documentation, run simulations, and establish response playbooks. Change management is key – ensure stakeholders understand the value and impact of EDR.
Continuous Monitoring and Optimization
EDR is not a “set it and forget it” tool. Regularly review detection rules, response workflows, and alert thresholds. Use insights from past incidents to fine-tune your configuration. Continuous monitoring and optimization ensure your EDR adapts to evolving threats and remains aligned with your security goals.
For business leaders, the value of Endpoint Detection and Response (EDR) goes far beyond technical capabilities. It’s about reducing risk, improving operational efficiency, and protecting the bottom line. Here are five key benefits that make EDR a strategic investment:
1. Massive Improvement in Visibility: You can’t protect what you can’t see. EDR provides a granular, real-time view into all activity happening on your endpoints, eliminating blind spots.
2. Drastically Faster Incident Response: EDR reduces the “dwell time” – the critical period between initial compromise and detection. By automating containment, EDR can stop a minor incident from becoming a catastrophic breach.
3. Effective Defense Against Advanced Threats: EDR is specifically designed to catch the threats that AV misses, including ransomware, zero-day exploits, and fileless malware.
4. Streamlined Forensic Investigation: In the event of an incident, EDR provides security teams with all the data they need to quickly understand the root cause and full scope of the attack, simplifying remediation and reporting.
5. Reduced Analyst Burnout: By automating the response to common threats and providing high-fidelity alerts, EDR allows your security team to focus their valuable time on the most critical investigations.

Cyberattacks are rising - learn how to build a resilient defense. This blueprint helps you choose the right cybersecurity strategy tailored to your business.
Download White paperImplementing Endpoint Detection and Response (EDR) can deliver transformative security benefits – but it’s not without its challenges. Here are some common obstacles organizations face, and how to overcome them:
EDR platforms can generate a high volume of alerts, especially in the early stages of deployment. This can overwhelm security teams and lead to missed threats.
Solution: Fine-tune alert thresholds, prioritize high-fidelity alerts, and leverage automation to filter noise. Integrating EDR with a SIEM or SOAR platform can also help streamline alert management.
Behavior-based detection can sometimes flag legitimate activity as suspicious, leading to unnecessary investigations and user disruption.
Solution: Continuously refine detection rules and whitelist known safe behaviors. Use feedback loops from investigations to improve accuracy over time.
Inconsistent deployment across devices – especially remote or unmanaged endpoints – can leave blind spots in your security posture.
Solution: Conduct regular audits to ensure full coverage. Choose an EDR solution that supports remote deployment and offline protection to secure endpoints regardless of location.
Smaller teams may struggle to manage and respond to EDR alerts effectively, especially without dedicated security analysts.
Solution: Consider partnering with a Managed Detection and Response (MDR) provider. MDR services offer 24/7 monitoring and expert support, allowing organizations to benefit from EDR without overextending internal resources.
Choosing the right Endpoint Detection and Response (EDR) solution can be a game-changer for your organization’s security posture. As you evaluate vendors, here are the key features and considerations to keep in mind:
Cloud-Native Platform: A cloud-based solution ensures easy deployment, scalability, and access for your security team from anywhere.
Integration Capabilities: Ensure the EDR can integrate with your other security tools, such as your UEM (Unified Endpoint Management) and SIEM (Security Information and Event Management) platform, for a more cohesive security posture.
Threat Hunting Tools: A strong EDR solution provides an intuitive interface that allows your team to easily query data and proactively hunt for threats.
MITRE ATT&CK® Framework Alignment: Look for vendors that map their detections to this globally recognized framework of adversary tactics and techniques. This ensures the solution is focused on real-world attack behaviors.
Before committing, request proof of concept (POC) or trial. This allows your team to test the solution in your environment, evaluate usability, and validate its detection and response capabilities.
While the core capabilities of Endpoint Detection and Response (EDR) remain consistent, its impact varies across industries based on unique threat profiles, compliance requirements, and operational environments. Here’s how EDR is making a difference across key sectors:
Healthcare
Healthcare organizations face constant threats from ransomware and data breaches targeting patient records. EDR helps by:
Finance
Financial institutions are prime targets for fraud, phishing, and insider threats. EDR provides:
Retail
Retailers manage large volumes of customer data and payment systems, often across distributed locations. EDR helps:
Remote Workforce Protection
With remote work now a norm, endpoints outside the corporate perimeter are vulnerable. EDR ensures:
As cyber threats continue to evolve, so does the technology designed to combat them. Endpoint Detection and Response (EDR) is rapidly advancing, driven by innovation in AI, automation, and integrated security ecosystems. Here’s a look at the key trends shaping the future of EDR:
AI and Automation
Artificial intelligence is transforming EDR from reactive to predictive. Machine learning models are becoming more accurate at identifying anomalies, reducing false positives, and automating complex response actions. Expect to see AI-driven playbooks and self-healing endpoints become standard features.
Predictive Threat Modeling
EDR platforms are beginning to incorporate predictive analytics to anticipate threats before they occur. By analyzing historical data and behavioral patterns, these systems can forecast potential attack vectors and proactively strengthen defenses – moving from detection to prevention by prediction.
Unified Security Platforms
The future of EDR lies in convergence. Vendors are increasingly integrating EDR with SIEM, SOAR, UEM, and identity platforms to create unified security operations. This consolidation improves visibility, reduces complexity, and enables faster, more coordinated responses across the entire attack surface.
Role of EDR in Zero Trust Architecture
EDR plays a critical role in Zero Trust strategies by continuously validating endpoint behavior and enforcing strict access controls. It ensures that every device is monitored, every action is verified, and no trust is assumed – making it a foundational component of modern Zero Trust implementations.
Understanding the terminology around Endpoint Detection and Response (EDR) is essential for navigating the cybersecurity landscape. Here’s a quick glossary of commonly used terms and acronyms:
Can EDR replace all of my existing security tools, like my firewall?
No, EDR is a critical component of a modern security strategy, but it’s not meant to be a standalone solution. It’s designed to work with other tools like firewalls and Endpoint Protection Platforms (EPP) to create a more comprehensive defense. EDR is the essential second line of defense against threats that get past your initial prevention tools.
My business is small and doesn’t have a large IT team. Is EDR too complex for us to manage?
While EDR provides powerful features, it can be a lot to manage without a dedicated team. For smaller businesses, a Managed Detection and Response (MDR) service is an excellent option. An MDR provider manages your EDR solution for you 24/7, offering their expert security analysts as a service.
If a device is disconnected from the internet, can EDR still protect it?
Yes, many modern EDR solutions continue to monitor and protect endpoints even when they are offline or disconnected from the network. While they may not be able to send real-time alerts to the central platform, they can often perform automated response actions locally to contain a threat.
Will an EDR agent slow down my employees’ computers?
This is a common concern, but modern EDR agents are designed to be lightweight and have a minimal impact on device performance. Because the heavy data processing and analysis happens in the cloud, the agent running on the endpoint remains efficient and doesn’t typically interfere with user productivity.
In today’s threat landscape, endpoints are the frontline – and the most vulnerable. Traditional antivirus solutions, while still useful, are no longer sufficient to defend against the sophisticated, fast-moving threats organizations face daily.
Endpoint Detection and Response (EDR) offers the visibility, intelligence, and speed needed to detect, investigate, and neutralize threats before they cause serious harm. It’s not just a tool – it’s a critical step toward a more resilient and mature cybersecurity posture.
If your organization is serious about reducing risk and staying ahead of attackers, now is the time to explore EDR. The next move is yours.
Discover seamless endpoint management and real-time threat response in one platform.
Get Started Today