Zero-trust access built on device trust with Hexnode IdP

Built for modern enterprises to ensure real-time access
Workforce access, secured
Ensure only the right people on compliant devices access your company data.
Verified BYOD access
Protect company resources by allowing access only from verified personal devices.
Compliance at every login
Stay audit-ready by aligning access rules with regulatory and compliance requirements.
User Lifecycle Automation
Make user access changes automated through SCIM-based lifecycle management.
Federated Identity
Integrate with existing identity providers like Microsoft Entra ID and Google Workspace.
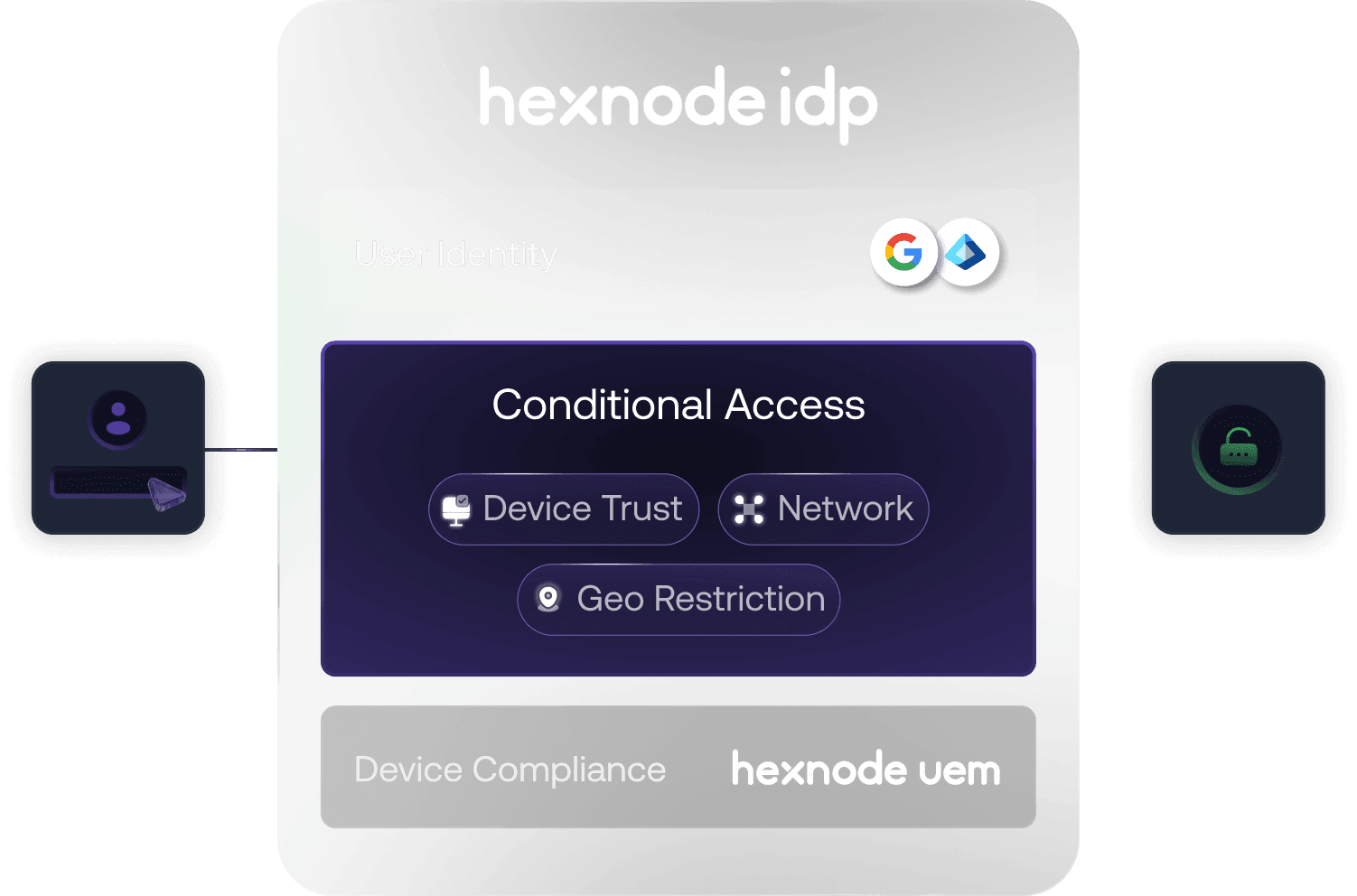
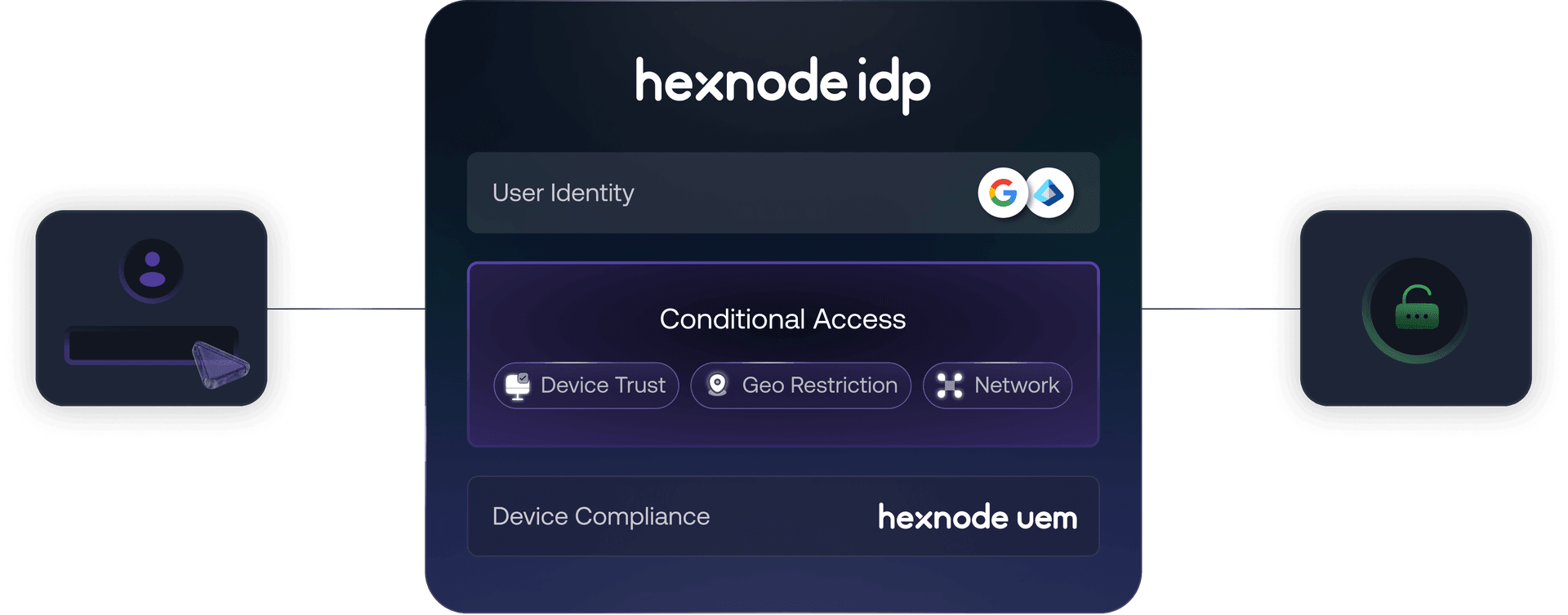
The building blocks to protect every sign-in
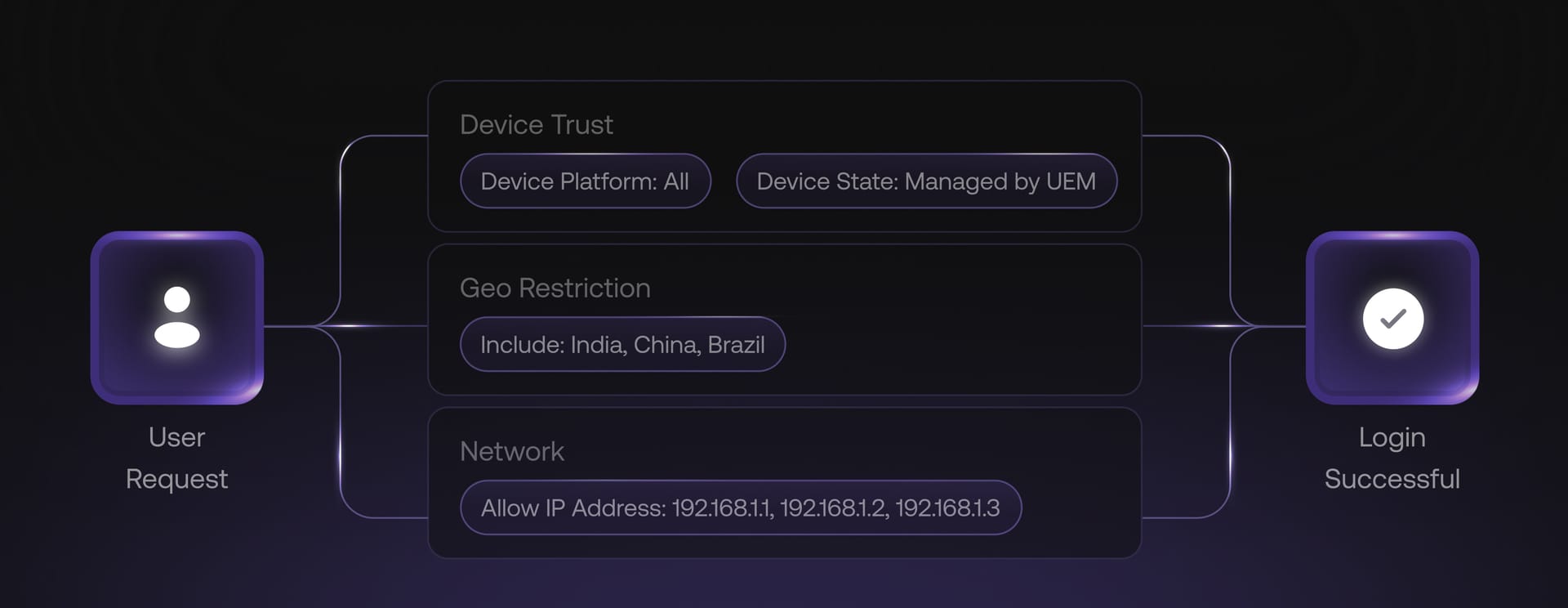
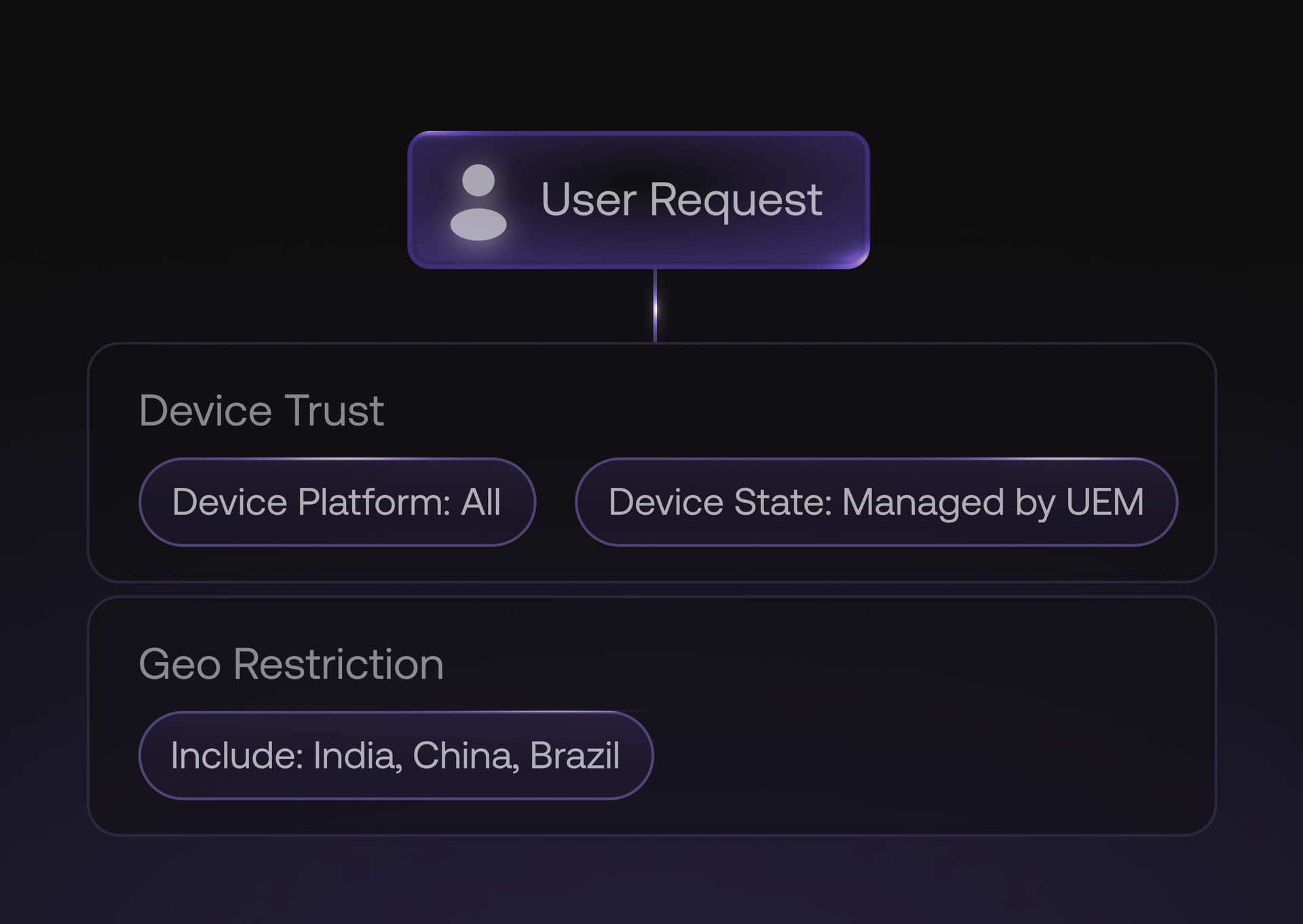
Conditional access
Enforce access rules based on user identity, device compliance, and security context to reduce risk and prevent unauthorized access.
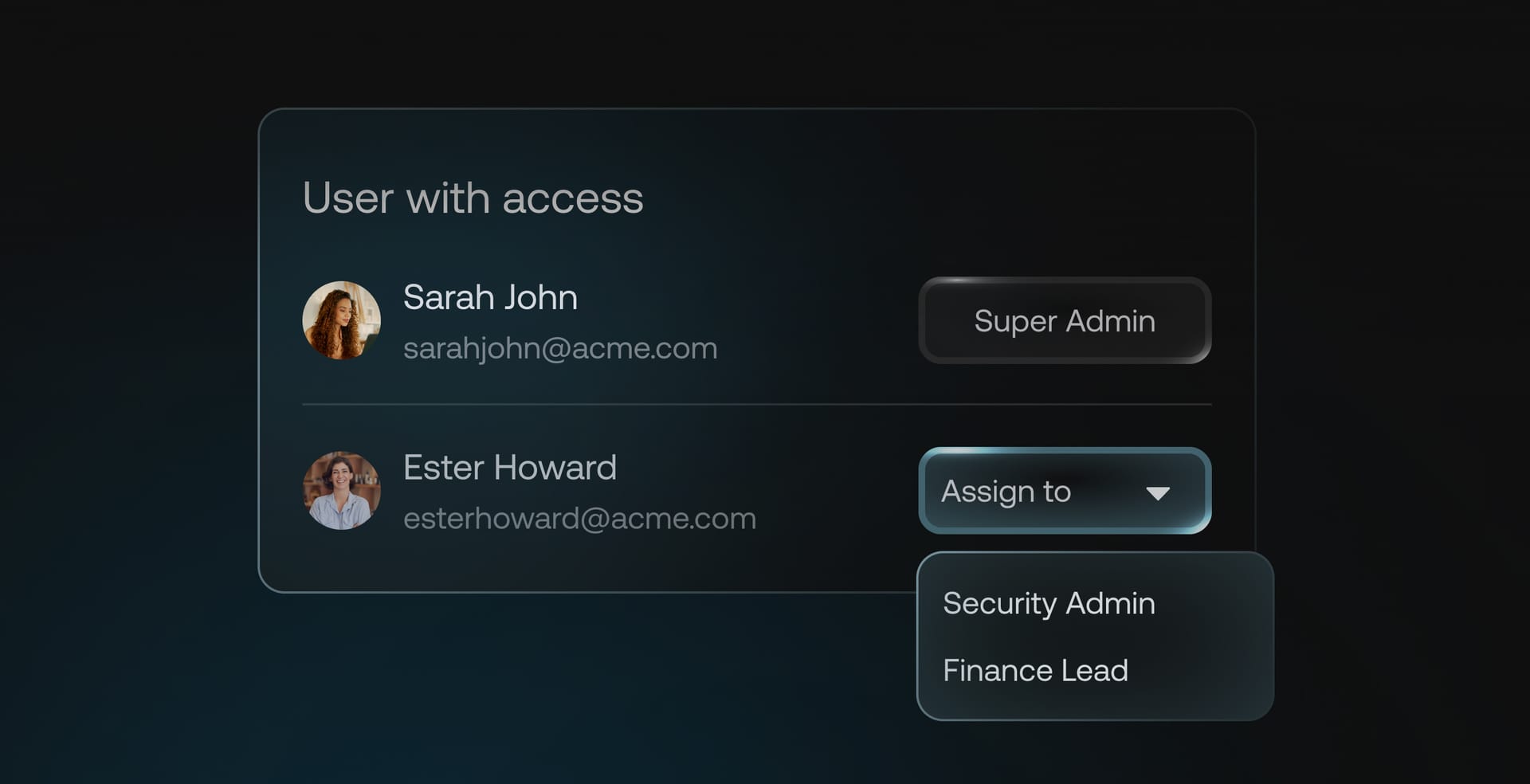
Role based access control
Manage access rights and permissions based on the user's defined role or function.
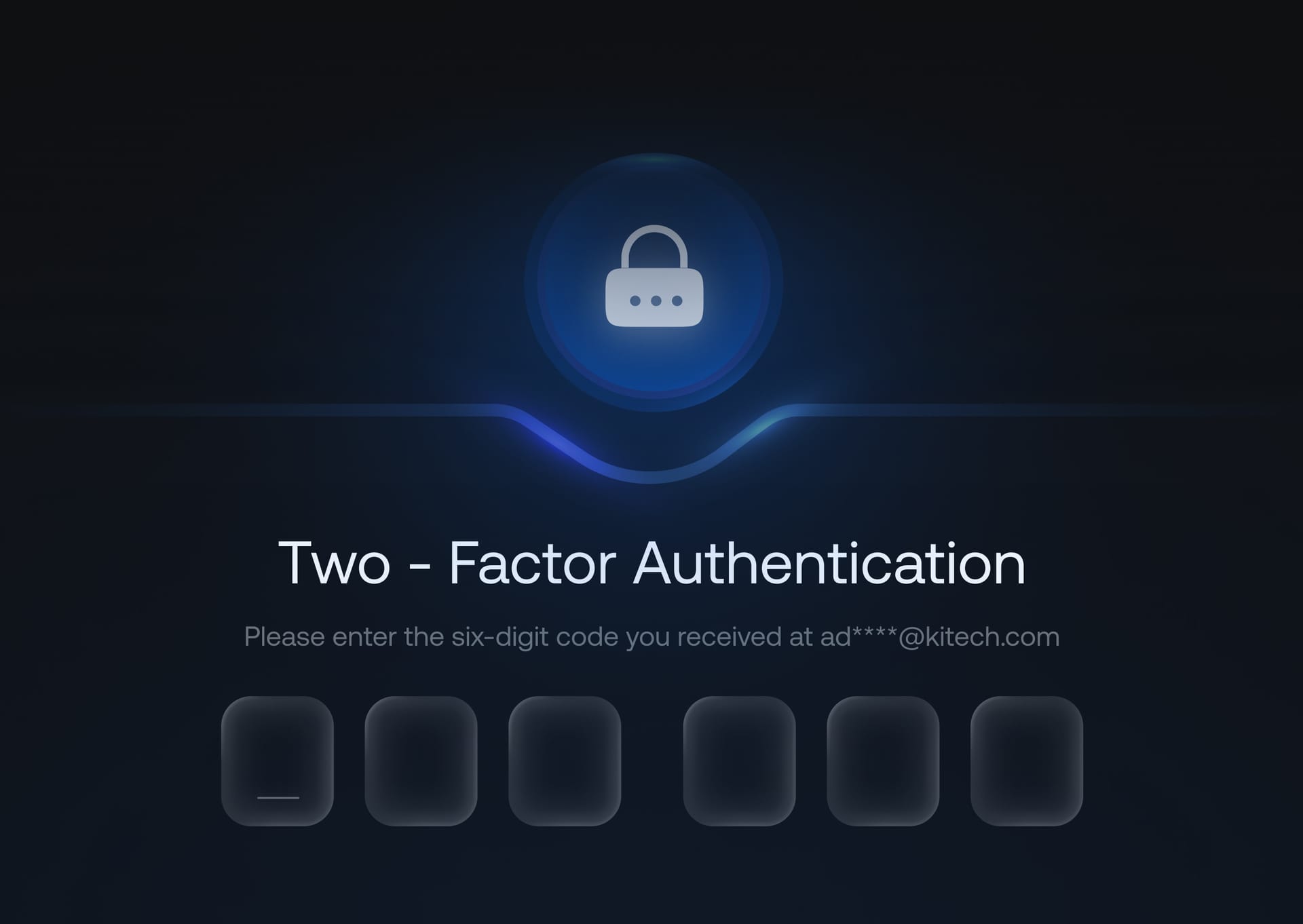
Contextual authentication
Step-up authentication with two-factor MFA to enforce an extra layer of security for high-risk actions.
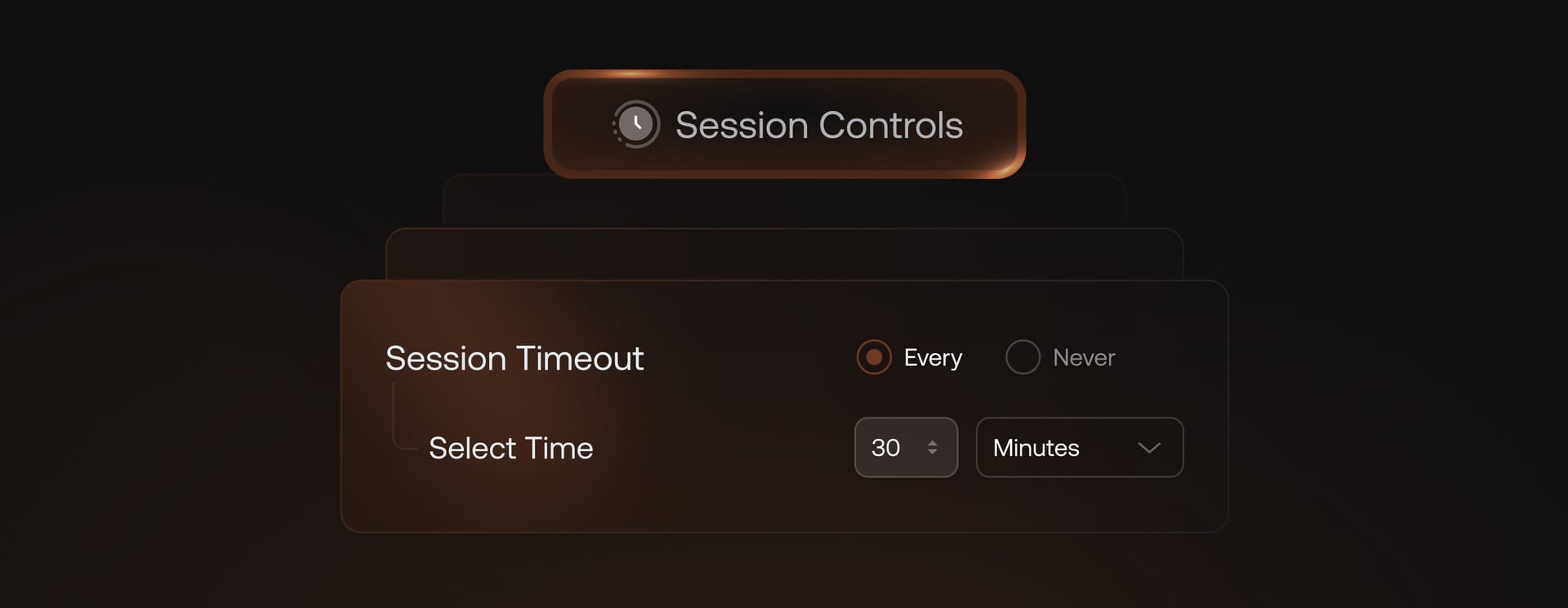
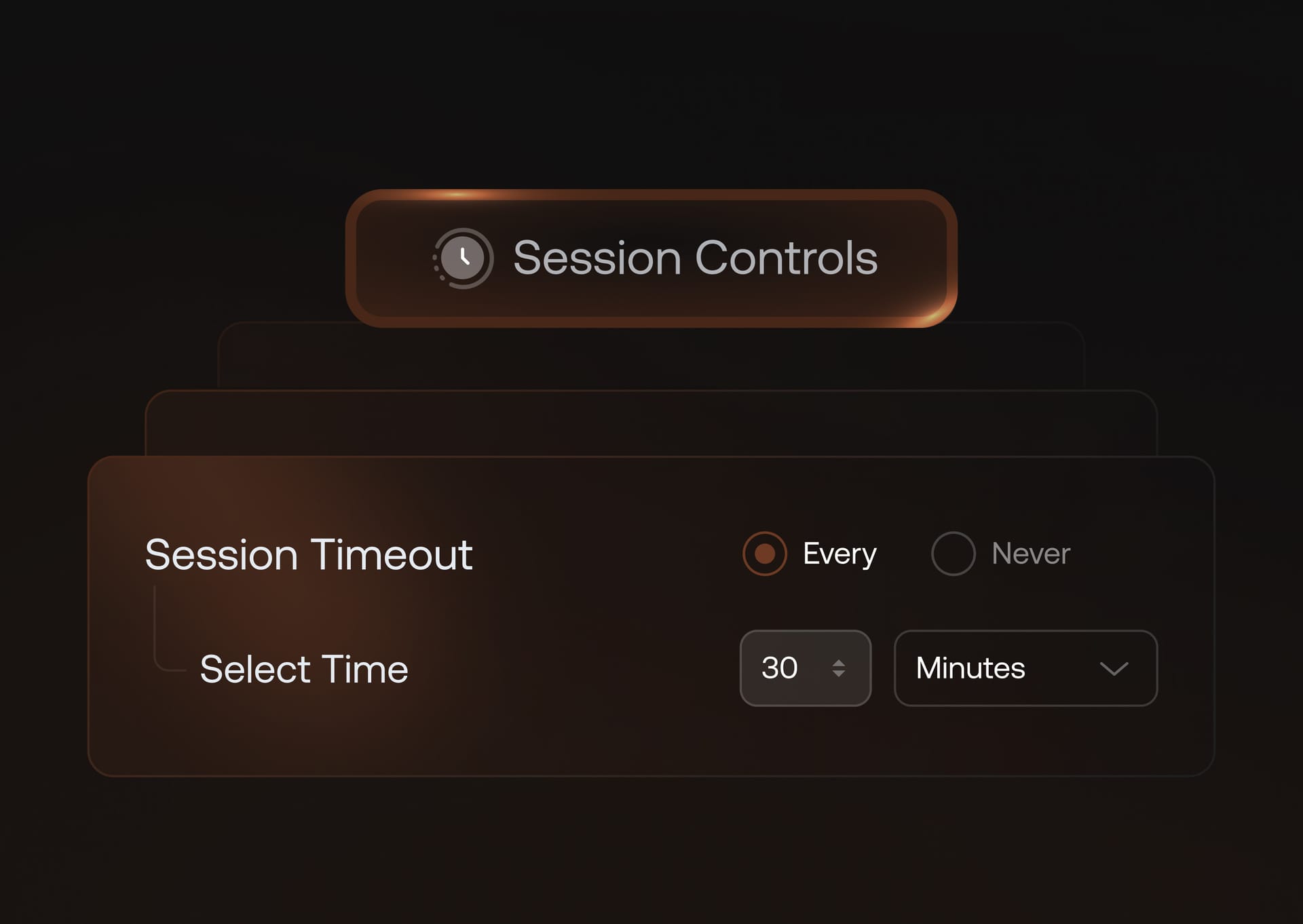
Session management
Control user access duration by defining policies for session inactivity, reducing exposure from unattended sessions.
Application access
Provide secure, policy-controlled access to all approved web, mobile, and SaaS applications.
Activity reports
Access centralized reports covering sign-in logs, provisioning and authentication history across users and applications.
Resources worth exploring

14 day free trial
No credit card