Category filter
Password policy for Windows devices
Password protects your computer from unauthorized access and ensures device security for the critical data in it. With Hexnode UEM, admins can enforce strong password rules on Windows devices, thereby ensuring the security of the organization’s data. This feature enables you to configure the level of complexity enforced on device passwords. When a password policy is pushed to a device, the user is asked to set a password that complies with the criteria defined. There are different scenarios for setting up a password policy for Windows:
- If the device does not have a password: A message will be displayed asking the user to set a device password based on the password rules pushed to the device via policy.
- If the device has a password and it complies with the set password rules: The change password pop-up shows up on the device when a user logs in for the first time after the password policy is associated. The pop-up will be shown even if the device already has a password that meets the constraints mentioned in the policy.
- If the device has a password but it does not comply with the set password rules: A message reading ‘The user’s password must be changed before signing in’ will be displayed.
Configure password settings from the UEM console
To configure password rule for the users and make the password mandatory on the devices
- Login to your Hexnode UEM portal > Navigate to the Policies tab > Click on New policy to create a new one or click on any policy to edit an existing one > Enter the policy name and description in the provided fields.
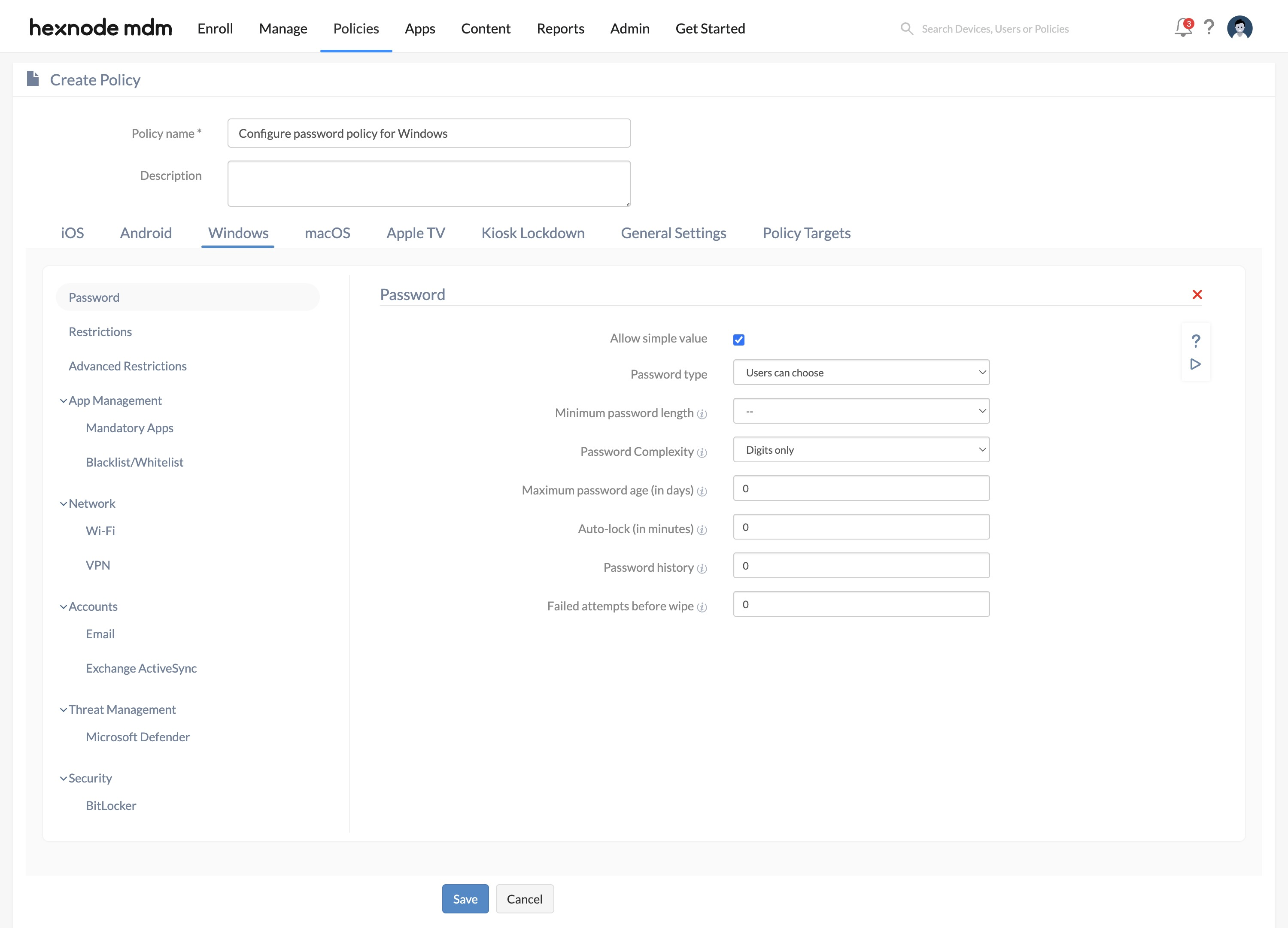
- Navigate to Windows > Password > Click on Configure.
- Configure password settings. Password settings
Password settings Supported Windows OS Description Allow simple value ✓10
✓11 Select this option to enable users to set simple passwords (without special characters or numbers) on their devices. Password type ✓10
✓11 Select the type of password that the users can set on their Windows devices. Alphanumeric password: Enforce users to set an alphanumeric password.
Numeric password: Enforce users to set a numeric password.
Users can choose (default): Select this option to allow users to set a password according to their desire.
Minimum password length ✓10
✓11 The minimum password length setting allows administrators to define the minimum number of characters required for a Windows device password. It could be any integer between 4 and 16. For instance, if the minimum passcode length is set to 7, users will be blocked from setting a password with 6 or fewer characters. Password Complexity ✓10
✓11 Select the minimum number of complex characters that the password should have. You can choose any value from,
- Digits only (default)
- Digits and lowercase letters
- Digits, lowercase and uppercase letters
Maximum password age (in days) ✓10
✓11 Select the maximum number of days before which the password needs to be changed. You can set any value in the range of 0 – 730 days.
Auto-lock (in minutes) ✓10
✓11 Set the maximum duration of device inactivity after which the device gets locked automatically. You can set any value in the range of 0 – 999 minutes. Once the device auto-locks itself after the specified duration of device inactivity, the user has to enter the password to unlock the screen. Note that the auto-lock time will also depend on the Screensaver policy configured, if any. The shortest among the values configured for the Auto-Lock setting (in the Password policy) and the Start screensaver after setting (in the Screensaver policy) will be applied as the auto-lock time. It determines when to auto-lock or activate the screensaver.
Password history ✓10
✓11 Password history is set to block the users from reusing the password for a specified number of times. You can set any value in the range 0 and 24.
Failed attempt before wipe ✓10
✓11 The number of wrong password attempts after which the device will be automatically reset to factory default settings and all user data (contacts, files, calendars, etc.) will be lost. You can set any value in the range 4 – 16.
- Finally, go to Policy Targets > + Add Devices > Select the required device(s) to which the policy needs to be associated > Click OK.
- Click Save.
Associate policy with Windows devices
To associate the policy with target devices, navigate to the Policies tab.
- When the policy is not yet saved,
- Go to Policy Targets.
- Click on Devices > + Add Devices, select the required devices and click Ok to associate the policy with the target devices.
- When the policy has already been saved,
- Select the appropriate policy.
- Then click on Manage > Associate Targets > choose the target devices and click on Associate to associate the policy with the target devices.