Single Sign On (SSO) and its relevance
Single Sign On is a service where user signs in once and utilize a single set of login information for various applications.

Get fresh insights, pro tips, and thought starters–only the best of posts for you.
Brendon Baxter
Mar 31, 2022
7 min read
Would you believe it if I said that an average employee has to manage close to around 190+ passwords? Well, a study conducted by LastPass confirms this number. When a person has these many passwords to handle, there is a high chance that he might forget some.
Forgetting passwords is a hassle not only for the employee but also for the IT team. If an employee forgets their device password, only the IT team would be able to reset it. When it comes to safety and security, a poor password habit is extremely dangerous. And this is where tools like federated authentication and Single Sign-On (SSO) come into play.
More and more companies are starting to understand the significance of issues related to bad password management habits. This is why features like Single Sign-On and Federated authentication gained more popularity.
Both these systems use one set of credentials to log in to multiple apps and services. In this way, a user has fewer passwords to remember and thus minimizes the problems caused due to bad password habits.
Single Sign-On is a concept that allows users to create accounts and access tools, apps, or resources within a service, using the same set of credentials from another service in the same domain. It’s like logging into your Google account to access different services offered by Google.
Single Sign-On can be a great addition to your business as it can help in so many ways, from increasing the productivity of employees to tightening security.
Federated authentication is also a technology that allows users to access multiple tools, apps, and domains with only one set of credentials. Once the user gets into a system using his log-in credentials, he/she is authenticated by the system and can access multiple resources in the organization without using any other credentials.
Generally what employees would have to do is, they would have to type in different log-in credentials to access different tools in an organization. With Federated authentication, organizations can eliminate this hectic process.
Federated authentication works on the basic principle of trust between identity providers and service providers. An organization using this authentication should make sure that the IdP they plan on using works for all the tools they use.
As mentioned earlier both SSO and Federated authentication allow users to access multiple tools and resources using a single set of credentials. This might make a person think that both of these are the same things and might use the terms interchangeably.
This couldn’t be further from the truth. Federated authentication and SSO have one significant difference, that is, SSO allows access to tools and resources within a single domain or organization, whereas Federated authentication allows access to resources and tools across a federated group. The collection of domains to which Federated authentication allows access is normally called the Federated group.
Every Single Sign-On can be called an instance of Federated authentication, but not all Federated authentication can be termed Single Sign-On. SSO is commonly used by individuals and organizations that make use of a lot of tools provided by a single entity.
Federated authentication commonly finds its use in organizations where the employees are required to use a lot of tools provided by different vendors.
Federated authentication mainly consists of 2 systems: Identity Provider or IdP and Service Provider or SP. IdP is the one that validates or authenticates users based on the credentials entered by them, whereas the SP refers to the website, tool, or app the user is trying to access.
The working of Federated authentication is very easy to understand. Initially, the users would be asked to log in to the IdP or Identity provider’s server with their credentials. Once the IdP authenticates the user, a secure token or an XML file is created based on the type of protocol used by the IdP.
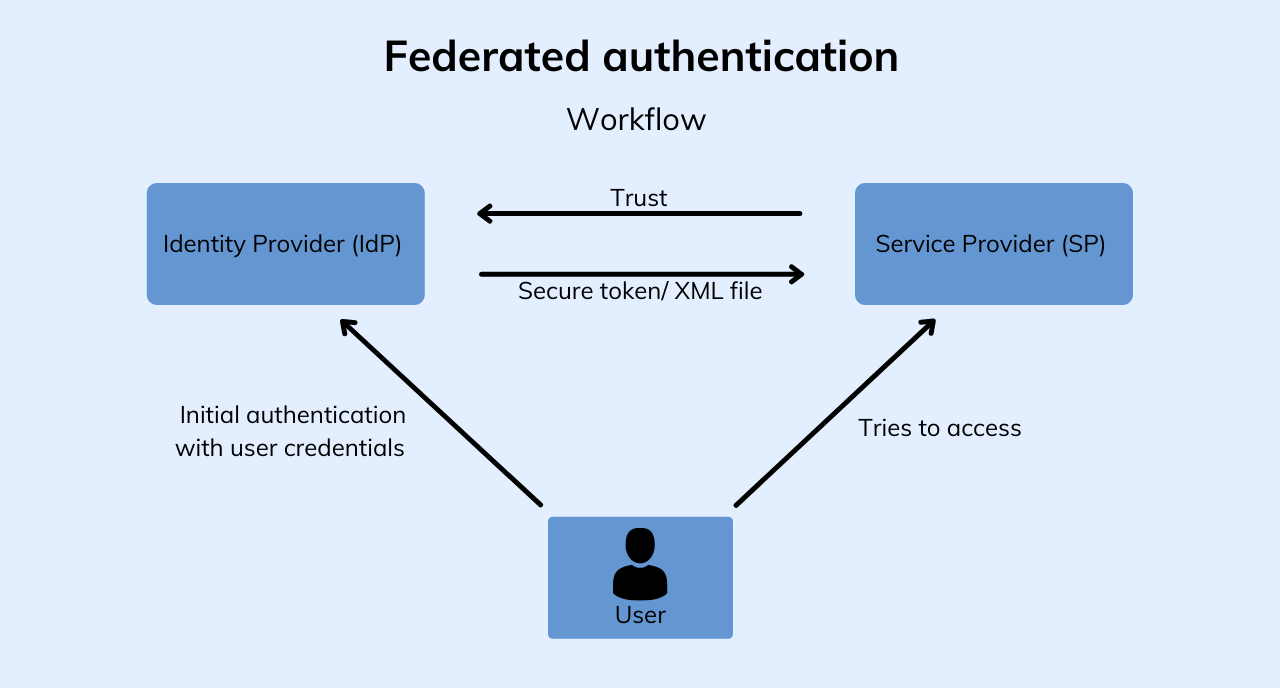
The communication made between the IdP and service providers is always encrypted and the encryption keys are used by the SPs to ensure that the attempt was made by an authenticated IdP itself.
SAML, OAuth, and OpenID are the three most commonly used protocols.
SAML is the abbreviation for Security Assertion Markup Language. SAML is an open-source authentication system that provides a secure method for transferring authentication details and data from the IdP to the service providers.
SAML makes use of XML files to communicate the authentication data between the IdP and the SPs. This is ideal for authentication of anything web-based, but not effective in the authentication of apps and software that are not web-based.
This protocol makes use of a token-based authorization. OAuth 2.0 can give users restricted access to resources and apps without revealing the authorization credentials. This protocol can eliminate the process of creating an account to access OAuth-enabled apps and tools.
OAuth differs from the other protocols in such a way that it is much more of an authorization protocol than an authentication protocol. The difference is authentication simply verifies a user but authorization verifies what all tools, apps, and resources a user can access.
OpenID Connect is more of an extension to OAuth 2.0 and it allows organizations to verify users using an authorization server. Although the OpenID connect uses an authorization server it mainly deals with the authentication of the user rather than the authorization.
Even though OpenID can perform most of the functions of OAuth 2.0, it is a bit different from it. OpenID connect is more API-friendly, so it can be used for web-based tools as well as apps. Also, OpenID provides more secure encryption to the authentication token.
Federated authentication is used when users link Apple School Manager or Apple Business Manager with Microsoft Azure Active Directory. With this integration, users can use their Azure AD credentials (username and password) as Managed Apple ID credentials.
The authentication makes use of the SAML protocol. The main highlight of this integration is that users can now use one set of credentials to log in to both Apple and Microsoft devices as well as the services offered by both.
There are many advantages of using Federated authentication, but a few of the most notable ones are:
IT administrators can utilize Hexnode UEM's IAM solution to handle access restrictions and permissions for individual network users.
Download DatasheetThe use of Federated authentication can not only benefit the IT team, but also the users and the entire organization. Even though implementing Federated authentication is a time taking process, the result would be a better, secure, and automated identity management which would save much more time down the road.
Sign up for a free trial and explore the Identity and Access Management features offered by Hexnode.
Sign up
Share your thoughts