In the modern BYOD environment, employees are expected to be productive around the clock with anywhere anytime access to work resources whether they are at the office, home, or any remote locations. The trend has brought more flexible devices like smartphones, tablets, wearables, and even IoT gadgets to work apart from the traditional work laptops and desktops keeping the mobility landscape in constant flux. Thus, digitization and ever-evolving device technologies have overburdened enterprise IT with challenges that they have never encountered before. This urged enterprises to look for new management options to accommodate the disparate number of endpoints, device models, and OS platforms which brought a new level of complexity to IT functions and concerns.
How to develop a successful enterprise mobility strategy
Learn how to establish a successful mobility strategy for your business
Any successful management strategy for IT involves formally defining the acceptable device use etiquette, management practices, and security policies along with employee and employer rights and responsibilities. Employees, in general, are aware of the trade-off between BYOD and the corporate’s authority over such work devices. So, they are ready to accept stringent enterprise policies in exchange for the convenience to work from their own devices. What they expect from organizations in return is that the organizations respect the employees’ privacy and maintain the so-called digital trust while enforcing compliance or data protection measures. There should be an implicit agreement between the organization and the user to keep the management friction minimum and output maximum.
The key to boosting the employee-employer rapport is clearly communicating the organization’s mobile device policy with the users and the users taking on the responsibility to abide by whatever is recommended by the organization. To avoid vulnerabilities there should be provisions to check whether any conditions or rules are being violated. In this guide, we’ll be discussing the prime considerations to go a step further in creating a successful mobile device policy for any organization. This article serves as a reference and provides the best practices for the development and implementation of policies and procedures. You can modify the pointers discussed here to cater to your needs.
Components of a solid mobile device policy
 Components of a mobile device policy
Components of a mobile device policy
A mobile device policy typically comprises concrete actions to sustain enterprise mobility. Right from the moment an employee boots up the device for the first time, the enterprise IT should get remote authority over the device and the data residing in it and the enterprise should make it clear to the employees what is and what is not collected from the device, whether it be corporate-owned or personal. It is impossible to deliver on these promises without a well-planned mobile device policy and a robust management platform. IT should decide on the policy prior to procuring any management technologies.

As the diversity of endpoints being used increases, so does the importance of having systematic platform-based management rules, continuous monitoring, and automatic remediation in place. Both the employee and employer needs should be addressed, and the participation of representatives from all lines of business should be ensured in the policy creation process. User and organization rights and responsibilities should be clearly enumerated. The immediate business goals and growth path should be taken into consideration. There is no one right policy to cover all areas but there should be an optimum balance between user privacy and corporate security. Both from the perspective of employee and employer, there are some important considerations to be noted by any organization.
User rights and responsibilities
 User rights and responsibilities
User rights and responsibilities
When a user enrolls a device to the corporate network, management measures get activated on the device to protect against the risk factors. Employees knowingly take on some burden of responsibility of never violating corporate standards in return to the seamless access to the business resources from the endpoints of their choosing. While mixing their personal and professional lives on a device, employees should also enjoy the confidence that their employers are never careless with any personal data that are collected from those devices.
The user should also keep in mind the various situations that might pose a threat to corporate security due to their negligence including:
- Unauthorized use or distribution of data.
- Unwittingly exposing confidential data to malicious intruders.
- Accessing apps and data from unapproved sources.
- Misplacing and losing devices.
- Copying and pasting sensitive data to unprotected systems.
Enterprise not only want their users to be productive but also want them to be secure for which they define and implement strict security measures.
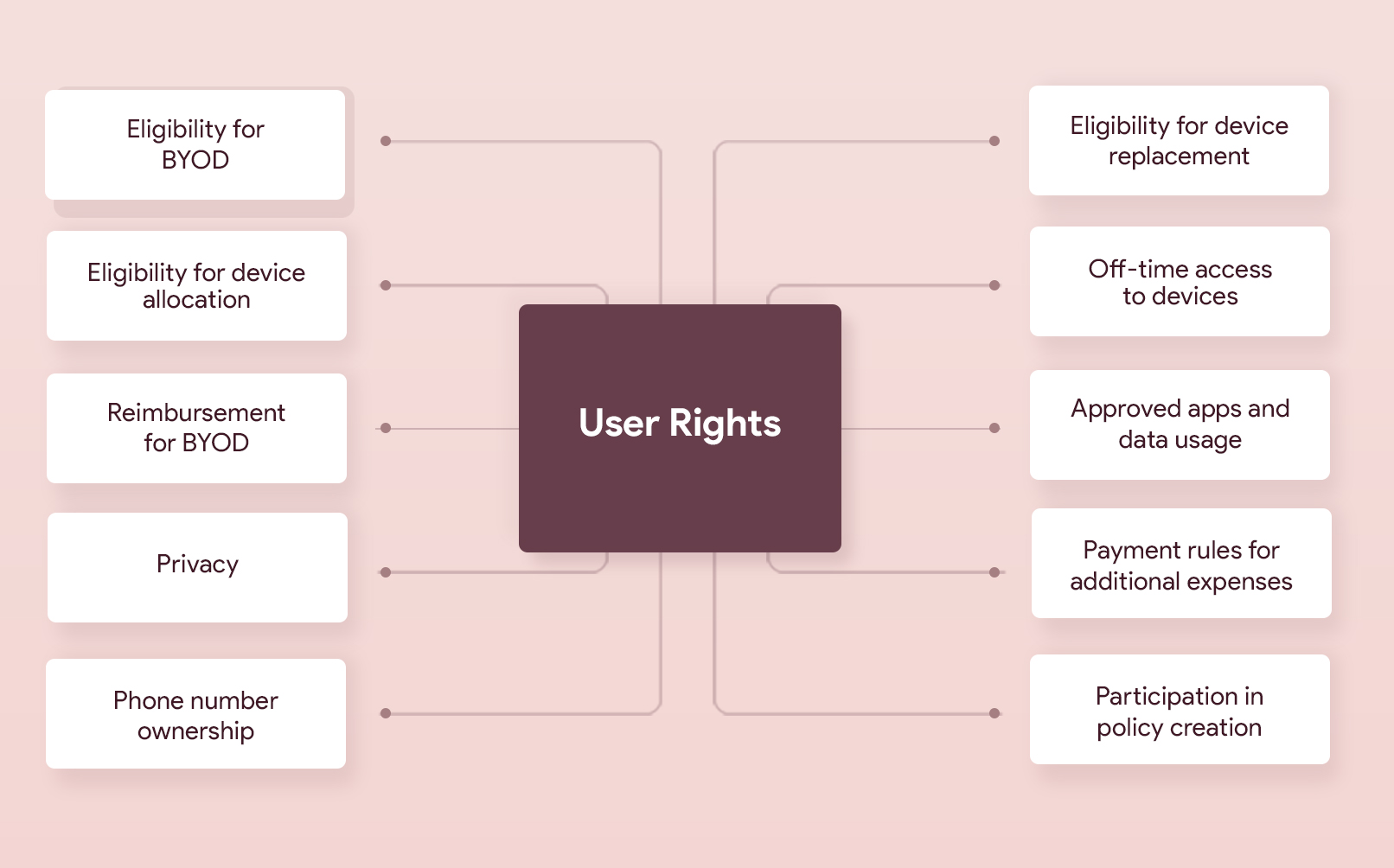
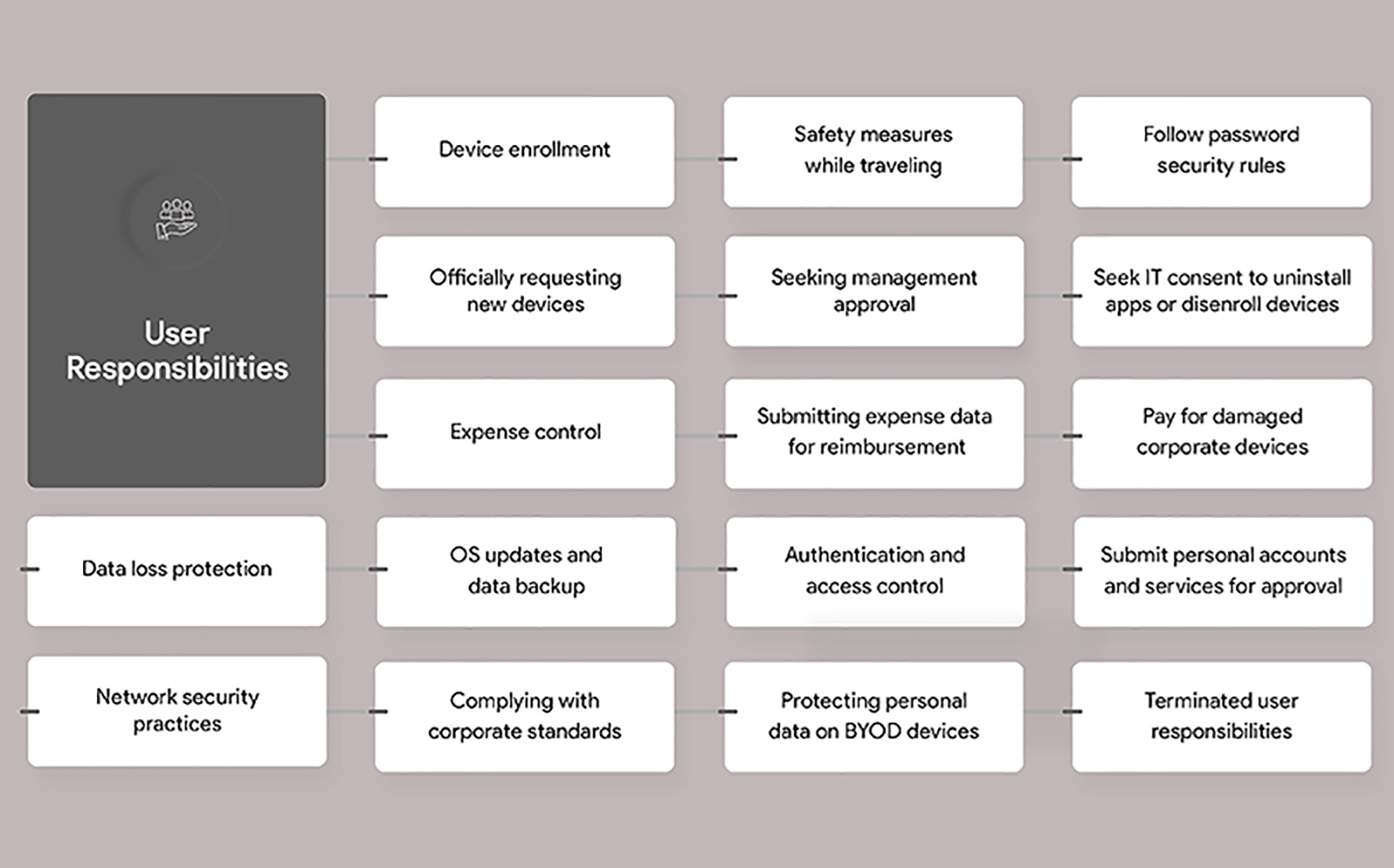 Here are the key user rights, terms, and responsibilities to be addressed in an organization’s mobile device policy.
Here are the key user rights, terms, and responsibilities to be addressed in an organization’s mobile device policy.
- Conditions for allotting devices to users
- The eligibility of an enterprise user to have an enterprise-issued device or personal device to access work data will be assessed and the decision to allocate a device or allow BYOD is made by the enterprise IT.
- Users should officially request for the IT to grant them corporate endpoints.
- BYOD will be allowed in genuine cases if granted by the IT and device’s hardware and software specifications are compliant to the pre-defined organization standards.
- Corporate-issued devices or devices funded by the corporate are always the properties of the enterprise and employees under no condition are allowed to violate the security standards defined by the organization.
- Employees can use corporate-issued devices only for work purposes and whenever needed for personal purposes should have special consent from the management.
- Employees are not allowed to burrow unapproved devices to the enterprise network without permission from the management.
- All the corporate-owned devices should be returned when an employee is terminated from service.
- The number of devices that can be enrolled by a user at a specific time has some limitations as defined by the organization.
- Users should maintain all the devices issued to them in proper working condition.
- In BYOD, users are responsible to keep the devices compatible with the technical specifications defined by the organization.
- Device user responsibilities
- Device users are responsible to authorize the device enrollment and make sure that the device is always locked with MDM management. Users should not tamper with any management or security software installed on the device.
- Maintaining the physical security of the device is the user’s responsibility.
- Don’t make any unapproved modifications to the device.
- Users are responsible for the security of enterprise data within the device.
- Backing up of work and personal data falls under the responsibility of the users. Device users must use secure means to back up the data and the backed-up data should be properly encrypted.
- Users should return the devices to the organization if they demand so under any circumstances.
- During selective enterprise wipes, users are assumed to back up personal data.
- Users assume full responsibility to remove any harmful gadgets from the enterprise network.
- Device users are fully responsible for stolen, lost, or damaged personal devices.
- It is the user’s duty to take all the necessary precautions to prevent data loss and cyber-attacks.
- Users are supposed to depend only on corporate-approved services while handling sensitive work data.
- Best practices for accessing sensitive corporate data from work devices
- Users should be aware of the confidentiality of the data they are dealing with which makes risk assessment easy.
- Ensure that the data is backed up properly.
- Make sure that the hard drives and external drives used for data sharing are properly encrypted.
- Employees should follow all the network security practices which are defined by the organization and consider the sensitive data they are handling as their personal responsibility.
- Users must use strong passwords for all their accounts and strictly follow the password security practices.
- Best practices for accessing devices, peripherals, and apps for work purposes
- Make sure that the management approves all the applications, devices, and connected things before they can be used.
- Ensure that all the software used is legally obtained.
- The license agreement for any software shouldn’t be violated under any circumstance.
- Get IT consent to uninstall any app or disconnect any endpoint from the enterprise network if they are no longer needed.
- Request for reimbursement for any purchases related to enterprise approved applications.
- Rules on lost devices
- Employees have the whole responsibility of safeguarding the device and data from loss, theft, or damage. The organization won’t be paying for any such losses.
- Employees will have to pay for loss or damage to corporate-issued devices (as the organization demands) if it is found that it happened due to misappropriation or carelessness from the user.
- Employees should report the loss or theft immediately to the authorities for the organization’s assistance to recover the device.
- Employees should be precautious in implementing authentication and access control measures on all their devices to address such situations.
- Employees should cancel all the individual services associated with the device on loss or theft.
- Expense control rules
- Limit excessive use of enterprise devices for personal uses particularly during work hours.
- Ensure that the data usage doesn’t exceed the plan limits.
- Device usage rules
- Users are not allowed to root, jailbreak, or make alterations to built-in functionalities of work devices.
- Users must protect the device from unauthorized access. Users are not allowed to share their credentials with anyone unless asked by the enterprise to do so.
- Users need special permission to access features like camera or Bluetooth on devices at restricted areas where the usage of these features is explicitly prohibited.
- Users are responsible to keep the work devices up to date.
- Application usage rules
- Use only apps that are approved by the organization.
- Work apps will be either provided by the organization or can be downloaded from the enterprise app store.
- Use only the organization accounts with App stores. Users don’t have the right to make an app purchase using their personal credentials.
- All the apps and software running on the device should comply with the organization’s security policy.
- Users should formally submit the unapproved applications for the organization’s consent.
- Users can use apps from public app stores (Google Play Store, Apple’s App Store, or Microsoft Store) provided the app is not included in the blacklist of apps restricted by the organization.
- Only approved credit cards can be used for app purchases.
- No copies of the organization’s licensed software can be made by the user.
- Rules on data back up and sharing
- During a device wipe, users are responsible for protecting their personal data.
- Use organization approved means to back up data.
- Use only approved platforms for file sharing.
- Users are not allowed to use personal email accounts to transfer corporate data.
- Users should act in compliance with the data copyright regulations.
- Users are responsible for the data on hard disk drives and data backed up to any systems.
- All the changes made to the enterprise data while not connected to the enterprise network should be synced once reconnected.
- User safety rules
- While using devices during driving, users should comply with local regulations.
- Users can use Bluetooth devices if approved by the organization.
- Users should avoid practices like emailing, messaging, or calling while driving.
- It is better to avoid programming navigation apps while driving.
- User privacy rules
- Users should be aware that the organization collects private information such as contacts, call logs, and geographical locations from their devices.
- Users should know what all actions that the organization can and cannot perform on their devices and make sure that the corporate policy addresses their privacy concerns.
- Rules on penalties
- Users should be aware of the extent of penalties that will be incurred upon them for violating the rules set by the organization. The penalty can extend up to termination of employment.
- Users should be more cautious in their actions if they are warned by authorities before enforcing any penalty.
- Security guidelines
- Avoid downloading unfamiliar files off the internet.
- Make sure that only personal devices complying with the security criteria are added to the corporate network.
- Users should keep the OS, software patches, application software, anti-virus software, and other security tools updated. Updates can be delayed only if informed by IT.
- Avoid leaving systems unattended. Log out of all the accounts whenever you step away from the devices.
- Store sensitive data only according to the information classification policy defined by the organization.
- Be sure to always maintain redundant power supply for the device.
- Use a web browser (preferably with the sandboxing capability) approved by the organization for internet surfing.
- Follow the online security practices like clearing browsing history after each session logouts.
- Use only secure Wi-Fi for network access and always use the corporate VPN.
- Disable functionalities like Bluetooth and NFC whenever they are not needed.
BYOD security: An exhaustive approach with UEM
Download
- Device enrollment options
- Users should in some cases enroll the devices by themselves as per the instructions provided by the organization to help them get up and running.
- Users must enroll the devices to the UEM for complete management if they are required to do so.
- Personal devices are required to enroll with the UEM partially under management options like Android Enterprise work profile or iOS user enrollment.
- Sometimes users are asked to enroll only with a MAM solution where the enterprise has little authority over the device but significant control over the apps and data.
- Rules on ownership of mobile phone numbers
- Users who are willing to use their personal contact number for business purposes can do so agreeing to the terms of usage. The user’s personal number remains a corporate asset during the specified period of time. Upon termination, employees are required to remove all the business-related contacts from their personal devices and agree to not maintain any relations with the clients depending on the conditions under which they are leaving.
- If the users don’t want to use their personal number for business needs, they are required to mask their number by directing all the business calls through the organization’s internal telephony system.
- Expense reimbursement rules for BYOD
- Users should comply with the reimbursement policy and submit the expense data with documentation of proof before the authorities.
- Users should be aware that the organization won’t pay for any purchases where the user fails to submit proper documentation.
- Users should be aware that the organization won’t pay for any personal purchases made on the work device.
- Rules for terminated employees
- Employees have to return all the company assets upon termination of employment.
- Employees should take care of their personal data as the organization will perform an enterprise wipe in the case of BYOD and the organization won’t be responsible for personal data.
- Employees should agree to delete all backed-up enterprise data as they won’t be having any right for accessing the data upon termination.
- Rules on off-time access to work devices
- Users may be prohibited from accessing a certain portion of the device after work hours.
- Users are not allowed to access work email and other sensitive data when they are out of work.
- Users may be sometimes allowed to access some services during weekends and day-offs under special permission from the management.
Organization rights and responsibilities
 Organization rights and responsibilitiesOrganizations have a vital role in improving productivity and collaboration by granting freedom of choice for the employees regarding the type of device they use at work. It is the duty of the organization to ensure that effective mobility management policies are in place and privacy, security, and risk management concerns are properly addressed. All rights and duties of organizations should also be officially declared, documented, and implemented to empower mobility in the right manner.
Organization rights and responsibilitiesOrganizations have a vital role in improving productivity and collaboration by granting freedom of choice for the employees regarding the type of device they use at work. It is the duty of the organization to ensure that effective mobility management policies are in place and privacy, security, and risk management concerns are properly addressed. All rights and duties of organizations should also be officially declared, documented, and implemented to empower mobility in the right manner.
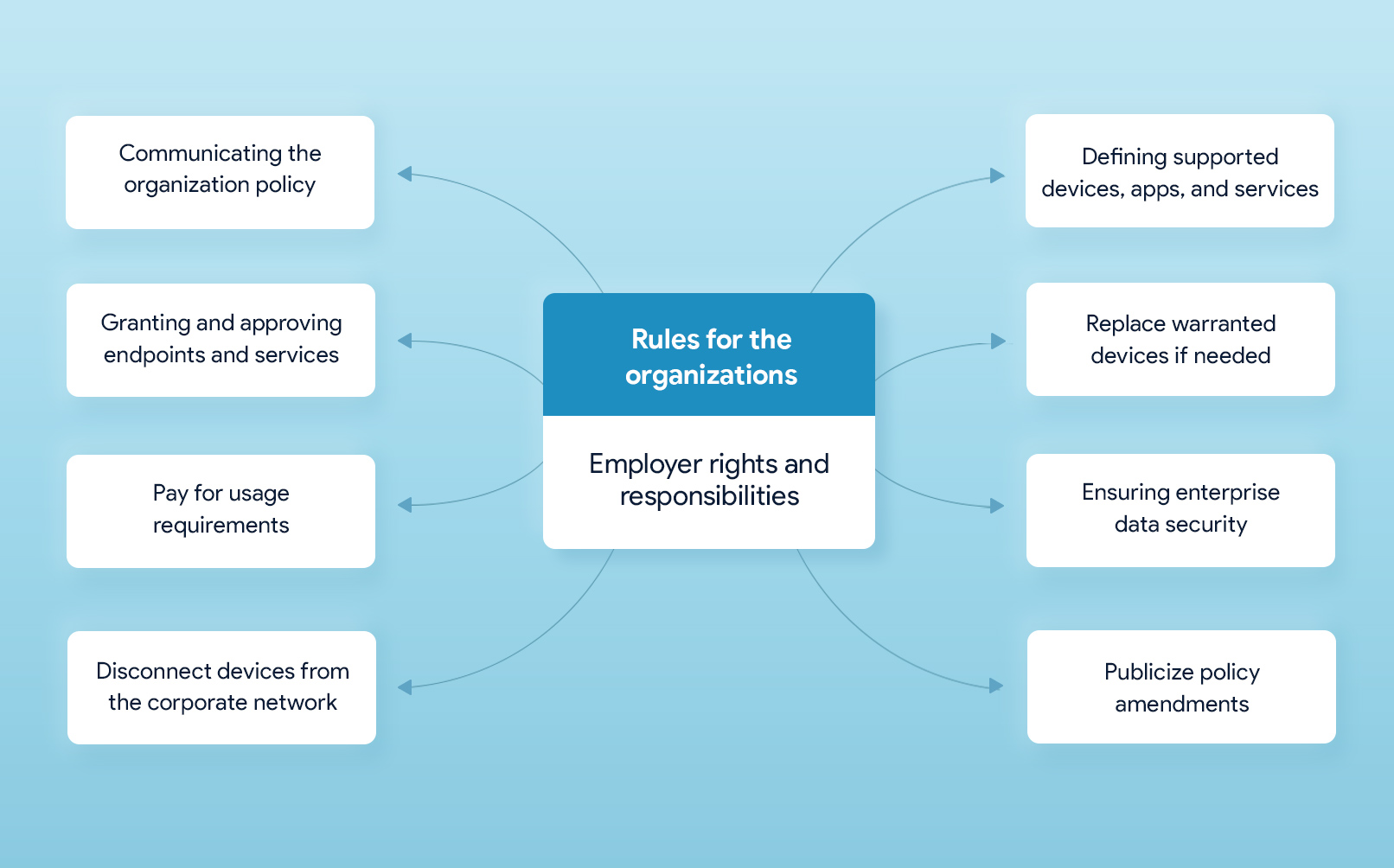 Here are the guiding principles for defining organization rights and duties towards a complete mobile device policy.
Here are the guiding principles for defining organization rights and duties towards a complete mobile device policy.
- Organization responsibilities
- The organization is responsible for communicating the organization policy with the employees and make sure that all elements of the organization’s mobility strategy are properly implemented.
- The organization is responsible for taking care of additional management requirements brought by mobility in the workplace including technical help desk, data privacy policies, new provisioning options, regulatory compliance, and more.
- Make sure that the enterprise’s mobile device policy adheres to all government and local regulations.
- The organization is responsible for providing any stipends or reimbursements for essential cases.
- The IT security department is responsible for approving devices to be added to the corporate network.
- Organizations can remove any modified software or app from corporate-issued devices or deny access to enterprise data from personal devices whenever required.
- The organization is responsible to pay for any previously reported extended usage requirements.
- The organization has the right to enforce security policy on any work device irrespective of the ownership.
- The organization is responsible for performing an enterprise wipe on a device that is lost, stolen, or misplaced and vulnerable to threats.
- The organization is responsible for making users aware of any changes made to the work procedures.
- The organization has the right to disable or disconnect any device from the corporate network without any prior notification.
- Best practices for policy development
- Organizations should incorporate opinions from work councils and trade unions within the policy to ensure that user privacy and rights are respected.
- Organization policy requires the acceptance of all departments as well as the users.
- Involve all departments in the policy development process.
- The organization is responsible to review and amend the mobile device policy periodically to make it compliant with the new regulations and security standards and address all the future enterprise needs.
- Publicize any amendments made to the organization policies and submit them for approval from all.
- Best practices for handling enterprise data
- The IT security department should educate employees on the precautions and best security practices.
- Organizations should define general rules for data encryption, storage of sensitive data, and publish a list of data backup methods.
- Be sure to keep data duplication to a minimum.
- Analyze and approve the secure means by which enterprise data can be transferred.
- Secure on-demand delivery of enterprise data with the help of monitoring and tracking.
- Defining supported device models and platforms
- The enterprise should define the device models that can be added to the enterprise network including smartphones, tablets, laptops, wearables, and IoT devices.
- The enterprise should clearly list the OS platforms that are supported including iOS, Android, Windows, macOS, tvOS, ChromeOS, etc.
- Replacement rules for damaged devices
- The help desk is responsible to replace or repair any device within the warranty period if the device user officially requests a replacement.
- The organization won’t be responsible for the replacement of any lost or stolen personal device.
- The IT department is responsible for checking the warranty of the device and decide the eligibility for device replacement.
- Out-of-model or discontinued devices may be replaced with new devices if needed.
- A loaner device will be provided if a device is given for repair until the device is returned after the repair.
Towards a sustainable mobile device policy
 Towards a sustainable mobile device policy
Towards a sustainable mobile device policy
No organization has excessive time on hand to plan on the development and implementation of a mobile device management policy for them. There are certain security regulations which should be adhered to when using endpoints for work purposes. Each organization will be having its own ensuing policy decisions to obtain a balance between device security and enterprise productivity. There is nothing like a single fit for all, but a carefully crafted policy can equip the organization as well as users to efficiently handle their endpoints with confidence. Use the guidelines mentioned in this article to optimize your organization’s mobility strategy to its full potential. The overall result is increased employee satisfaction and productivity accompanying security and administrative control.









Share your thoughts