- What is a custom configuration profile?
- What can be done using custom configuration profiles?
- Steps to deploy custom profiles to Apple devices
- How can you deploy custom configuration profiles to an Apple device through Hexnode
- The benefits of deploying custom profiles through Hexnode
- Featured Resource
- Apple Device Management: For the robust security of the digital workspace
- Sign up for a free trial!
What is a custom configuration profile?
Custom configuration profiles are files that help IT admins distribute configuration information to Apple devices. These custom profiles prove themselves useful for IT admins in cases like configuring passcode settings or DNS proxy settings for several devices over a short period of time. Custom profiles can be a .xml, .mobileconfig or a .plist file. Using configuration profiles, instructions to modify device settings, like Wi-Fi settings, VPN settings, email server settings, etc., can also be sent to devices.
When there is a need to configure several devices or set up email or network on several devices, configuration profiles prove themselves to be an easy way to execute it. For creating a custom profile, you need 2 things: one, a MacBook, and two, Apple Configurator 2. Custom profiles created using the Apple Configurator 2 are usually saved as a .mobileconfig file. Along with this .xml and .plist files created using other profile creation apps can also be used to configure Apple devices.
What can be done using custom configuration profiles?
Custom profiles are a very powerful tool and it is very easy to mess up devices if not used properly. These configuration profiles can be used for a huge set of functionalities. From device settings like Wi-Fi settings and VPN settings to Active Directory settings like LDAP server settings, custom profiles can manage almost everything in Apple devices.
Custom profiles can be made non-removable from devices, but there is a small problem with this feature. Only profiles that are pushed through UEMs are truly non-removable. Manually installed profiles (those which are not installed over the air) can be removed using an account with administrative authority even if they are made non-removable.
Steps to deploy custom profiles to Apple devices
The process to deploy and install profiles on Apple devices are pretty straightforward. First, a configuration profile has to be created using the Apple Configurator 2, then it has to be stored as a .mobileconfig/.xml/.plist file and then it can be deployed, either manually or over the air. Apple lets you sign profiles with certificates to let devices know that the profiles are sent from a trusted source and it is safe to install the profile on the device.
Step 1: Custom profile creation
Open Apple Configurator 2 and create a new profile. In the new window that pops up, give a name for the profile and also a unique profile identifier.
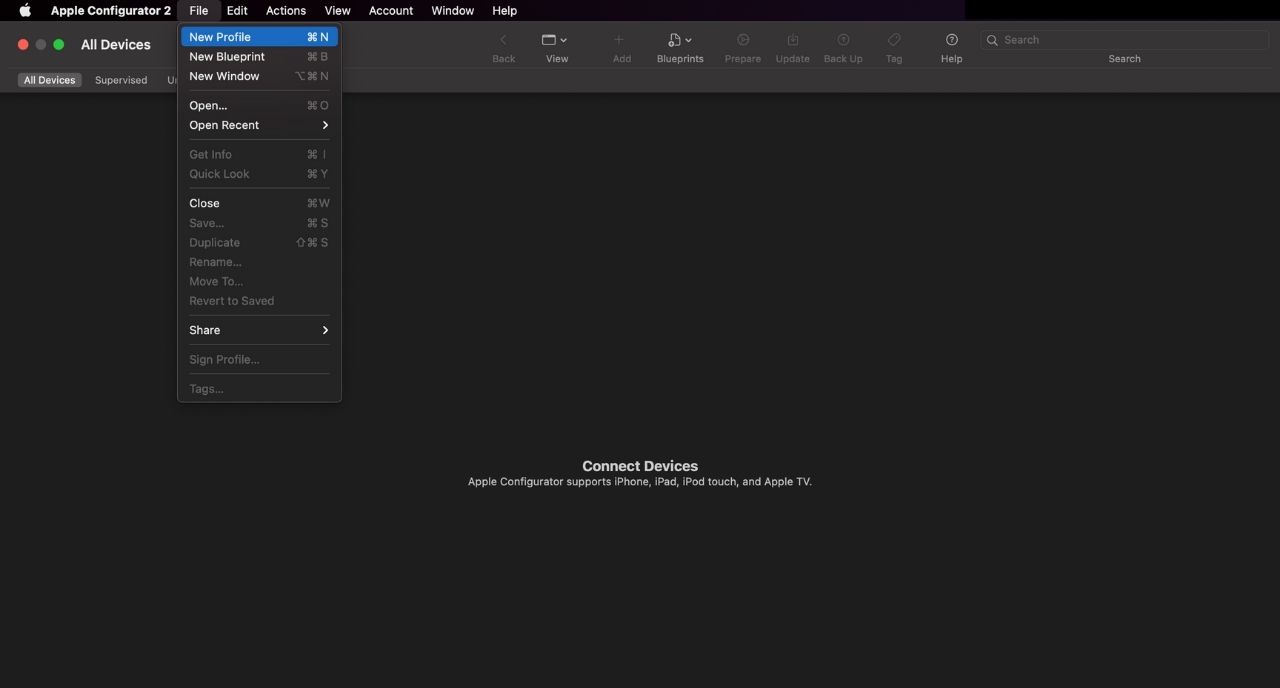
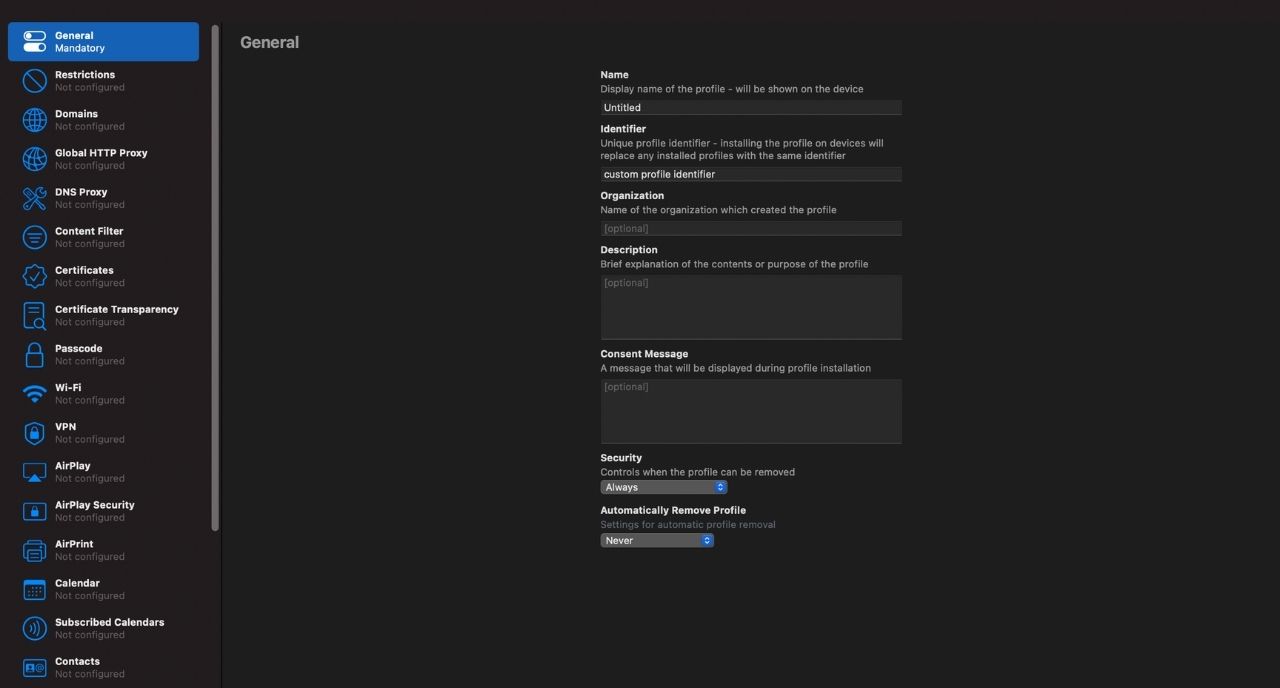
Step 2: Configuration of settings
In the Apple Configurator 2, on the left-hand side, there is a tab providing all the settings that can be configured using custom profiles. When a function is clicked a window pops up asking you to configure. Clicking on the configure button takes you to all the features that can be configured. Let’s see an example.
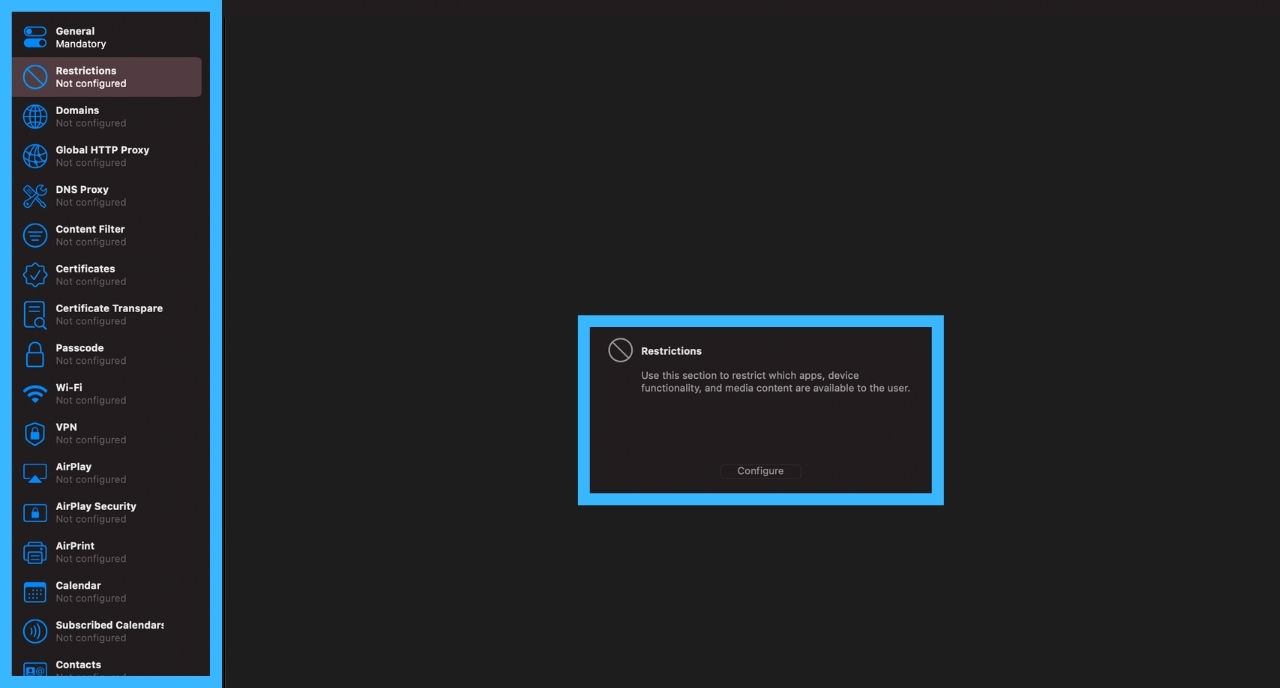
When clicked on the restrictions, a configure window pops up. Clicking on the configure button takes you to the next page.
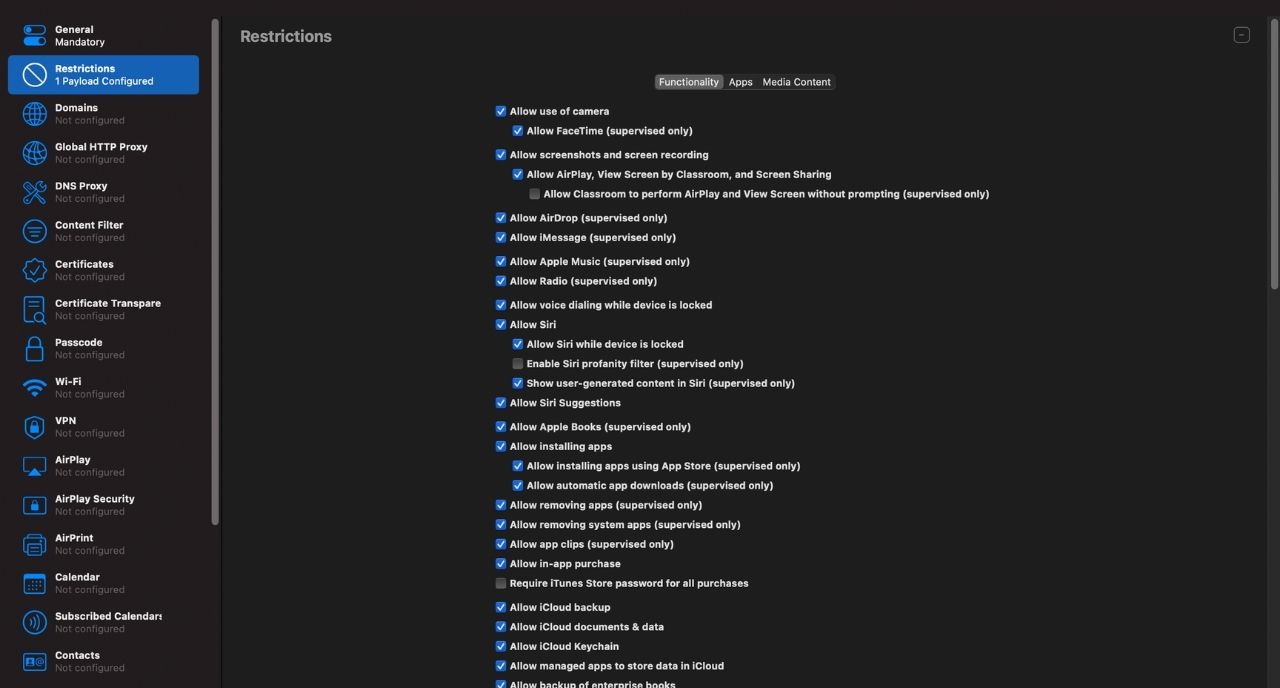
Here you are offered the functions that can be restricted using custom profiles. Similarly, other settings also let you configure other device functionalities.
Step 3: Signing and saving the profile
After all the settings are configured, the profile has to be saved. Apple Configurator 2 gives the option of signing the profile with a certificate before saving the profile. By signing the profile, you can let the devices know that the profile has been created from a trusted source and it is safe to install the profile on the device. For signing a profile, you have to go to File –> Sign Profile. A window pops up asking you to select a signing identity.
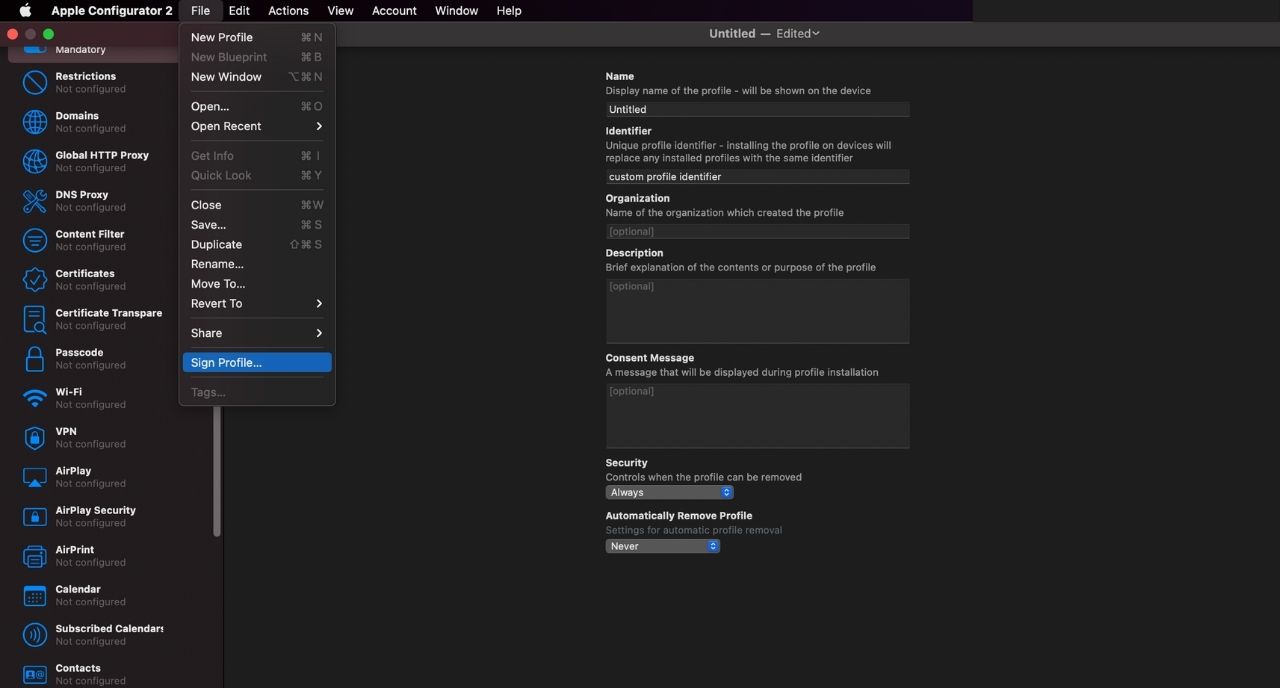
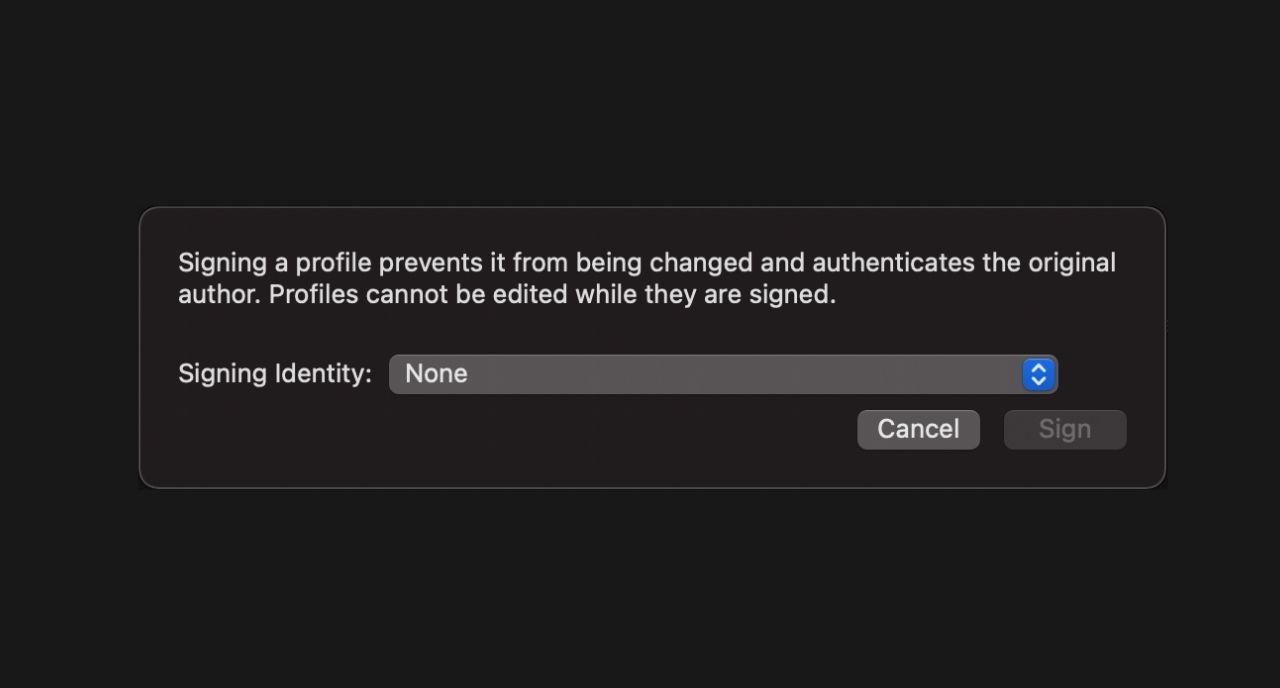
After you have signed the profile, you have to save the profile. Go to File –> Save and in the pop-up, give a name for the profile. The file is saved as a .mobileconfig file by default but you can also use files saved as .xml or .plist.
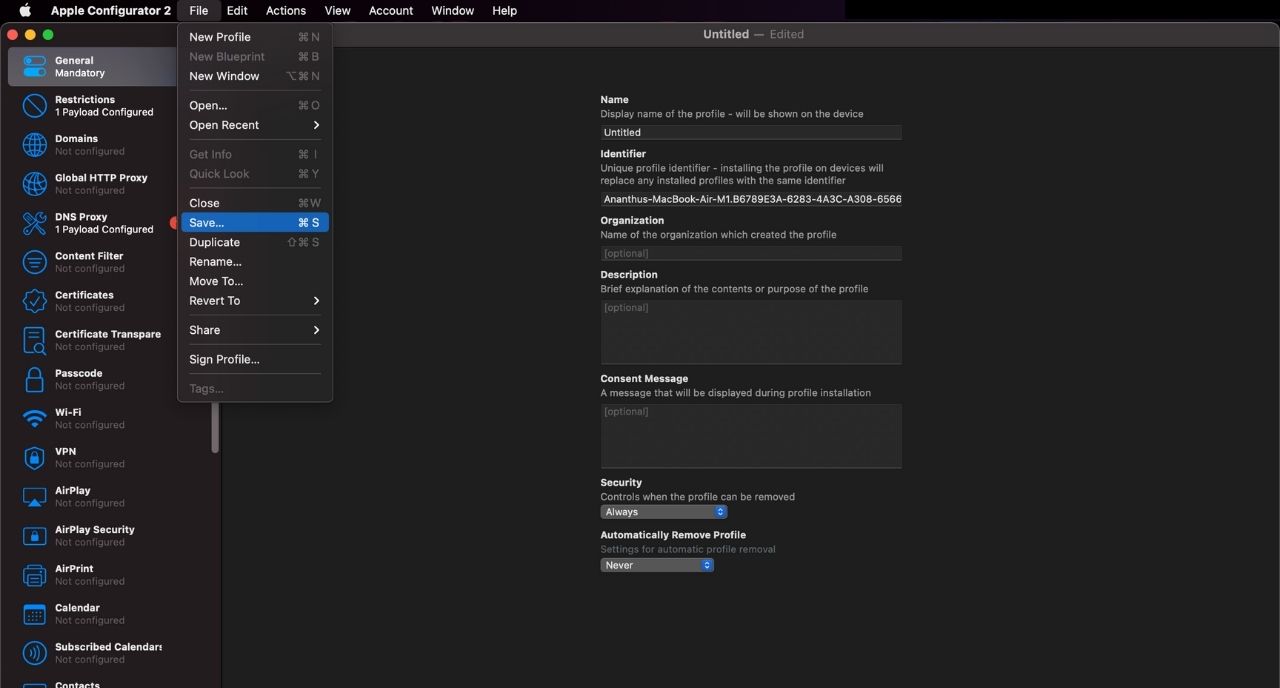
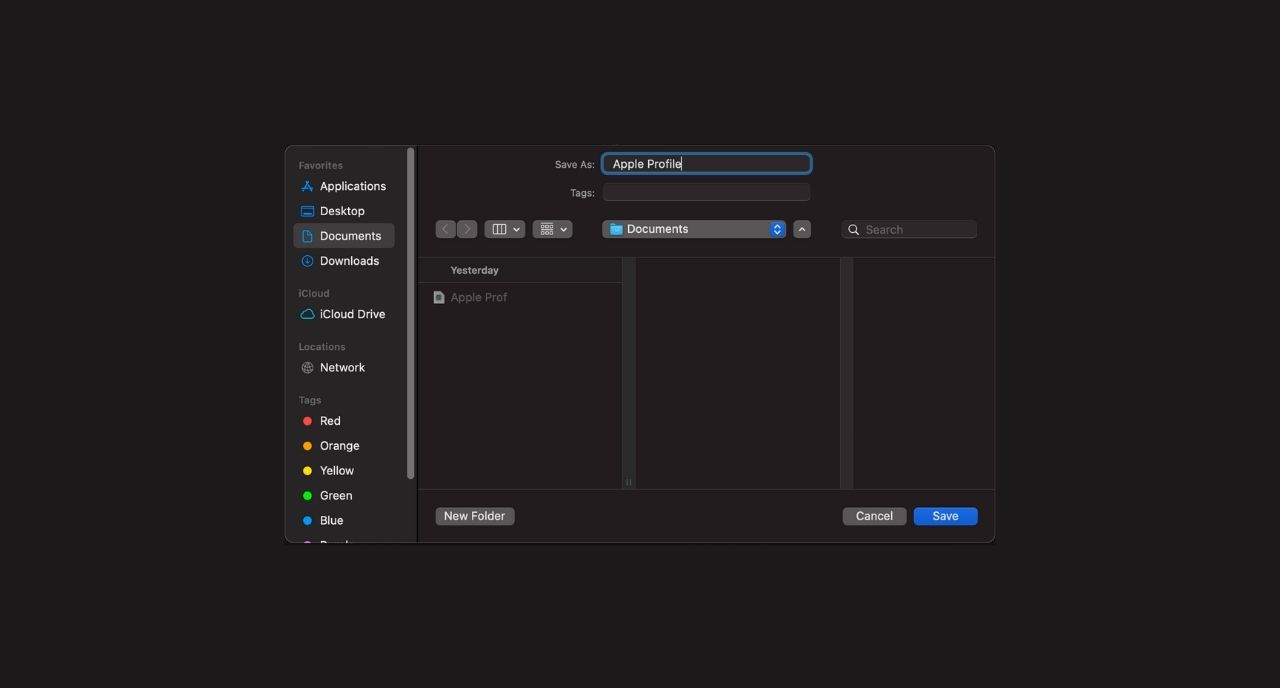
Step 4: Deployment of the custom profile
After the profile is created and signed, it has to be deployed to devices. There are multiple ways of deploying the profiles to devices:
- Using Apple Configurator 2
- Through an email
- Through a webpage
- Over-the-Air Profile Delivery and Configuration: a method provided by Apple itself
- Over the air using an MDM or UEM
Only profiles that are deployed through MDMs can be made truly non-removable. If a profile is made non-removable and deployed using an MDM, it can be removed only using the MDM itself. All the other profiles can be removed using an account having admin authority. This is one of the reasons why it is recommended to deploy profiles using an MDM server.
How can you deploy custom configuration profiles to an Apple device through Hexnode
Hexnode now offers the capability to remotely deploy custom configuration profiles to Apple devices (iOS devices, macOS devices and tvOS devices). Custom profiles created using Apple Configurator 2 can be pushed to devices through the Hexnode portal. In the policy section, it is possible to upload profiles for each Apple platform, namely iOS, macOS and tvOS. Once the profiles are uploaded, the policy should be associated with the required device or group of devices.
The benefits of deploying custom profiles through Hexnode
With Hexnode, it is possible to deploy custom profiles to a huge number of devices using a few simple steps. Hexnode lets you associate custom profiles to a single device, a group of devices, devices used by a user or even a set of devices used by a group of users. Contextual association of profiles to devices is possible through the use of dynamic device grouping feature provided by Hexnode. Using custom profile deployment, features like Apple TV remote management and macOS server account settings, that aren’t currently supported by Hexnode can be configured and pushed to the managed devices.

Featured Resource
Apple Device Management: For the robust security of the digital workspace
Efficient management strategies are a must for managing the wide range of Apple devices in enterprises. Check out how you can effectively manage all your Apple devices with Hexnode’s Unified Endpoint Management solution.
Download White paperUsing Hexnode it is possible to associate profiles to a particular Apple platform. This implies that when a platform-specific profile is pushed, it is installed only on devices running that particular OS (like if a profile for iOS is pushed to a group of devices, the profile is deployed only on iOS devices). This is a huge advantage because, if profiles meant for one platform get associated with another platform the result could be disastrous. However, even if you associate a profile meant for one platform, say iOS, with another one, say macOS, the profile won’t get installed. In such a case, even if the policy might show a success status the profile won’t get applied.
Sign up for a free trial!
Sign up for a 14-day free trial with Hexnode and explore the Apple device management features with Hexnode.
Sign up
Share your thoughts